GENIConnections
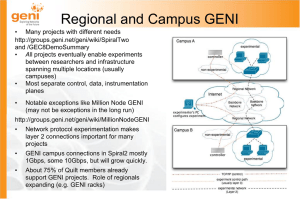
... • Many projects with different needs http://groups.geni.net/geni/wiki/SpiralTwo and /GEC8DemoSummary • All projects eventually enable experiments between researchers and infrastructure spanning multiple locations (usually campuses) • Most separate control, data, instrumentation planes ...
... • Many projects with different needs http://groups.geni.net/geni/wiki/SpiralTwo and /GEC8DemoSummary • All projects eventually enable experiments between researchers and infrastructure spanning multiple locations (usually campuses) • Most separate control, data, instrumentation planes ...
Chapter 4: Advanced Internetworking
... networks (they are usually called service provider networks, and they are operated by private companies rather than the government) Sites are connected to each other in arbitrary ways ...
... networks (they are usually called service provider networks, and they are operated by private companies rather than the government) Sites are connected to each other in arbitrary ways ...
Operational Risk and Probabilistic Networks – An
... The first step in the Bayesian process is construction of the operational loss model by identifying the key variables and their cause-effect relationship. The key BBN variables for a missed corporate action (CA) announcement are given below. These variables, in combination, determine operational los ...
... The first step in the Bayesian process is construction of the operational loss model by identifying the key variables and their cause-effect relationship. The key BBN variables for a missed corporate action (CA) announcement are given below. These variables, in combination, determine operational los ...
Chapter 4 - Elsevier
... networks (they are usually called service provider networks, and they are operated by private companies rather than the government) Sites are connected to each other in arbitrary ways ...
... networks (they are usually called service provider networks, and they are operated by private companies rather than the government) Sites are connected to each other in arbitrary ways ...
Video Source Traffic Modeling
... In statistical multiplexing, a VBR connection is allocated its “statistical” bandwidth (less than its peak but more than its average bit rate) The statistical bandwidth of a connection depends not only on its own stochastic behavior but also strongly on the characteristics of existing connections Ba ...
... In statistical multiplexing, a VBR connection is allocated its “statistical” bandwidth (less than its peak but more than its average bit rate) The statistical bandwidth of a connection depends not only on its own stochastic behavior but also strongly on the characteristics of existing connections Ba ...
Introduction to Classless Routing
... Note: Remember classful/classless routing protocols is different than classful/classless routing behavior. Classlful/classless routing protocols (RIPv1, RIPv2, IGRP, EIGRP, OSPF, etc.) has to do with how routes get into the routing table; how the routing table gets built. Classful/classless routing ...
... Note: Remember classful/classless routing protocols is different than classful/classless routing behavior. Classlful/classless routing protocols (RIPv1, RIPv2, IGRP, EIGRP, OSPF, etc.) has to do with how routes get into the routing table; how the routing table gets built. Classful/classless routing ...
Campus Fabric Design Guide - CVD - October 2016
... the VXLAN data plane. EID prefixes (IPv4 addresses with /32 “host” masks) are registered into the map server along with their associated RLOCs. When sending traffic to an EID, a source RLOC queries the mapping system in order to identify the destination RLOC for traffic encapsulation. Although a ful ...
... the VXLAN data plane. EID prefixes (IPv4 addresses with /32 “host” masks) are registered into the map server along with their associated RLOCs. When sending traffic to an EID, a source RLOC queries the mapping system in order to identify the destination RLOC for traffic encapsulation. Although a ful ...
投影片 1
... Packet scheduling policy in CFP 1) The PBS first scans the token buffers of voice sources according to the preset priority order. If a token is found, it removes one token from this token buffer and transmits a packet for this voice source. Then, the PBS generates next token for this voice source a ...
... Packet scheduling policy in CFP 1) The PBS first scans the token buffers of voice sources according to the preset priority order. If a token is found, it removes one token from this token buffer and transmits a packet for this voice source. Then, the PBS generates next token for this voice source a ...
Presentation Title Here 24/28pt - Alcatel
... Increased bandwidth with cost decrease All Rights Reserved © Alcatel-Lucent 2010 ...
... Increased bandwidth with cost decrease All Rights Reserved © Alcatel-Lucent 2010 ...
Chapter 12 from Stalling`s book
... wherever there is telephone or some other means of network access. • This is changing how we play, work, communicate, teach, learn, and conduct business. • They provide both new opportunities and new challenges. • These challenges will slow the deployment of networks to a rush from what would otherw ...
... wherever there is telephone or some other means of network access. • This is changing how we play, work, communicate, teach, learn, and conduct business. • They provide both new opportunities and new challenges. • These challenges will slow the deployment of networks to a rush from what would otherw ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... quality of service. Various approaches are proposed in earlier to manage the mobility in wireless networks. In [1], the current state of the art for mobility management for next generation IP-based wireless systems with new wireless network architecture for mobility management were introduced. Towar ...
... quality of service. Various approaches are proposed in earlier to manage the mobility in wireless networks. In [1], the current state of the art for mobility management for next generation IP-based wireless systems with new wireless network architecture for mobility management were introduced. Towar ...
presentation source - University of Baltimore Home Page
... – Real-Time Streaming Protocol (RTSP) • Sets up virtual circuits for audio-video applications – Real-Time Transport Protocol (RTP) • Used after a virtual connection setup by RSVP or RTSP • Adds a sequence number and a timestamp for helping applications to synchronize delivery • Uses UDP (because of ...
... – Real-Time Streaming Protocol (RTSP) • Sets up virtual circuits for audio-video applications – Real-Time Transport Protocol (RTP) • Used after a virtual connection setup by RSVP or RTSP • Adds a sequence number and a timestamp for helping applications to synchronize delivery • Uses UDP (because of ...
Module 8
... • ICMP provides informational or control messages to hosts • Error messages result from Lost packets during packet transmission Error conditions which occur during packet transmission • Control messages are used to inform hosts of Conditions such as network congestion The existence of a better gatew ...
... • ICMP provides informational or control messages to hosts • Error messages result from Lost packets during packet transmission Error conditions which occur during packet transmission • Control messages are used to inform hosts of Conditions such as network congestion The existence of a better gatew ...
tia10e_ch12_pptM - Computer and Information Science
... Network Topologies Comparing Topologies (cont.) • Topologies can be combined within a single network – Topologies are often combined to benefit from the unique advantages of each – Known as a hybrid topology ...
... Network Topologies Comparing Topologies (cont.) • Topologies can be combined within a single network – Topologies are often combined to benefit from the unique advantages of each – Known as a hybrid topology ...
Assume a machine for which a char takes 1 byte, an int takes 4 bytes
... QUESTION 1: Weighting it Out (10 points) This question explores how to set the (configurable) link weights in link-state routing protocols like OSPF and IS-IS inside a single Autonomous System (AS) to achieve AS-wide goals. 1a) How should the network operators set the link weights if their goal is ...
... QUESTION 1: Weighting it Out (10 points) This question explores how to set the (configurable) link weights in link-state routing protocols like OSPF and IS-IS inside a single Autonomous System (AS) to achieve AS-wide goals. 1a) How should the network operators set the link weights if their goal is ...
Deep Learning: An Overview
... • Once an RBM is trained, another RBM is "stacked" atop it, taking its input from the final already-trained layer. • The new visible layer is initialized to a training vector, and values for the units in the already-trained layers are assigned using the current weights and biases. • The new RBM is t ...
... • Once an RBM is trained, another RBM is "stacked" atop it, taking its input from the final already-trained layer. • The new visible layer is initialized to a training vector, and values for the units in the already-trained layers are assigned using the current weights and biases. • The new RBM is t ...
answers - Cs.princeton.edu
... QUESTION 1: Weighting it Out (10 points) This question explores how to set the (configurable) link weights in link-state routing protocols like OSPF and IS-IS inside a single Autonomous System (AS) to achieve AS-wide goals. 1a) How should the network operators set the link weights if their goal is ...
... QUESTION 1: Weighting it Out (10 points) This question explores how to set the (configurable) link weights in link-state routing protocols like OSPF and IS-IS inside a single Autonomous System (AS) to achieve AS-wide goals. 1a) How should the network operators set the link weights if their goal is ...
Effect of an industrial chemical waste on the uptake
... As shown in the ANN architecture depicted in Fig. 1, the network used for modelling in this work consisted of three layers of neurons. The layers described as input, hidden and output layers comprise i, j and k numbers of processing nodes, respectively. Each node in the input (hidden) layer is linke ...
... As shown in the ANN architecture depicted in Fig. 1, the network used for modelling in this work consisted of three layers of neurons. The layers described as input, hidden and output layers comprise i, j and k numbers of processing nodes, respectively. Each node in the input (hidden) layer is linke ...
Signaling and Network Control
... Such additional features are used to support noncircuitrelated signaling, which is mostly used to interact with databases (SCPs). It is also used to connect the radiorelated components in cellular networks and for inter-SSP communication supporting CLASS services. For example, in cellular networks, ...
... Such additional features are used to support noncircuitrelated signaling, which is mostly used to interact with databases (SCPs). It is also used to connect the radiorelated components in cellular networks and for inter-SSP communication supporting CLASS services. For example, in cellular networks, ...
Design and performance evaluation of an improved TCP congestion
... in the network pipe and maintain extra data between the lower threshold (α) and the upper threshold (β). ...
... in the network pipe and maintain extra data between the lower threshold (α) and the upper threshold (β). ...
Colorful Spring Flowers
... – Manages the assignment of both IP and application layer name space (domain names) • Both assigned at the same time and in groups • Manages some domains directly (e.g., .com, .org, .net) and • Authorizes private companies to become domain name registrars as well ...
... – Manages the assignment of both IP and application layer name space (domain names) • Both assigned at the same time and in groups • Manages some domains directly (e.g., .com, .org, .net) and • Authorizes private companies to become domain name registrars as well ...
SS7
... Such additional features are used to support noncircuitrelated signaling, which is mostly used to interact with databases (SCPs). It is also used to connect the radiorelated components in cellular networks and for inter-SSP communication supporting CLASS services. For example, in cellular networks, ...
... Such additional features are used to support noncircuitrelated signaling, which is mostly used to interact with databases (SCPs). It is also used to connect the radiorelated components in cellular networks and for inter-SSP communication supporting CLASS services. For example, in cellular networks, ...
Proceedings of USITS ’03: 4th USENIX Symposium on Internet Technologies and Systems
... long-distance link is successful. However as noted above in Section 3.1, some of these connections in fact are rejected because the intended target of the link is \saturated" with 2k incoming links. We account for this implementation detail by noting that provided k = O(1), the fraction of such reje ...
... long-distance link is successful. However as noted above in Section 3.1, some of these connections in fact are rejected because the intended target of the link is \saturated" with 2k incoming links. We account for this implementation detail by noting that provided k = O(1), the fraction of such reje ...
Brain networks - Personal website space for Aalto University
... • Geographical networks: nodes are located in 3D space and each node has specific function! • Hierarchically structured: with highly reproducible modules both at structural and functional level ! - Possibly arising from wiring economy Rivera-Alba, M.et al (2014). Wiring economy can account for ce ...
... • Geographical networks: nodes are located in 3D space and each node has specific function! • Hierarchically structured: with highly reproducible modules both at structural and functional level ! - Possibly arising from wiring economy Rivera-Alba, M.et al (2014). Wiring economy can account for ce ...