Wireless TCP(September 20)
... TCP aware provide better performance than a link level protocols that are not TCP aware. TCP-aware link-layer protocols with selective acknowledgements had the best performance. The split-connection approach shields sender from wireless loss but sender often stalls due to timeouts on the wireles ...
... TCP aware provide better performance than a link level protocols that are not TCP aware. TCP-aware link-layer protocols with selective acknowledgements had the best performance. The split-connection approach shields sender from wireless loss but sender often stalls due to timeouts on the wireles ...
High Speed Communication Protocols
... It can convey only how much data can be buffered, rather than how fast the transmission should be It ties flow control and error control together Go-back-N type of control degrades throughput severely and add unnecessary network congestion Flow control should be independent of error control ECE 677, ...
... It can convey only how much data can be buffered, rather than how fast the transmission should be It ties flow control and error control together Go-back-N type of control degrades throughput severely and add unnecessary network congestion Flow control should be independent of error control ECE 677, ...
2017_Gopi_Deepthi_Thesis
... I would like to express my deep profound gratitude to Dr. Daisaku Ikeda, my mentor for always providing me consistent and unfailing support, guidance, inspiration, and encouragement to accomplish my goals and ambitions with firm determination, unshakable conviction and indomitable “Never Give Up” s ...
... I would like to express my deep profound gratitude to Dr. Daisaku Ikeda, my mentor for always providing me consistent and unfailing support, guidance, inspiration, and encouragement to accomplish my goals and ambitions with firm determination, unshakable conviction and indomitable “Never Give Up” s ...
Hardware Manual for the Model CG814WG Wireless Cable Modem
... The NETGEAR CG814WG Wireless Cable Modem Gateway connects directly to the wide area network (WAN) using its built-in cable modem. It has multiple options to connect to your local area network (LAN), including a 4-port 10/100 Mbps Ethernet switch, a USB port and an 802.11g wireless Access Point. The ...
... The NETGEAR CG814WG Wireless Cable Modem Gateway connects directly to the wide area network (WAN) using its built-in cable modem. It has multiple options to connect to your local area network (LAN), including a 4-port 10/100 Mbps Ethernet switch, a USB port and an 802.11g wireless Access Point. The ...
MF10 3G Wireless Router
... Connecting the external power ................................................................................... 14 Switching on your device............................................................................................ 14 Power supply................................................... ...
... Connecting the external power ................................................................................... 14 Switching on your device............................................................................................ 14 Power supply................................................... ...
Link state Routing - 寬頻網路實驗室
... When topology of network changes or failure, the network knowledge base must also change. The knowledge needs to reflect an accurate, consistent view of the new topology. This view is called convergence. When all routers in an inter-network are operating with the same knowledge, the inter-networ ...
... When topology of network changes or failure, the network knowledge base must also change. The knowledge needs to reflect an accurate, consistent view of the new topology. This view is called convergence. When all routers in an inter-network are operating with the same knowledge, the inter-networ ...
View PDF - Allied Telesis
... Netscape Communications Corporation. All other product names, company names, logos or other designations mentioned herein are trademarks or registered trademarks of their respective owners. Allied Telesis, Inc. reserves the right to make changes in specifications and other information contained in t ...
... Netscape Communications Corporation. All other product names, company names, logos or other designations mentioned herein are trademarks or registered trademarks of their respective owners. Allied Telesis, Inc. reserves the right to make changes in specifications and other information contained in t ...
(IP) dan Subnet Mask
... • In an IPv4 network, the hosts can communicate one of three different ways: – Unicast - the process of sending a packet from one host to an individual host – Broadcast - the process of sending a packet from one host to all hosts in the network – Multicast - the process of sending a packet from one ...
... • In an IPv4 network, the hosts can communicate one of three different ways: – Unicast - the process of sending a packet from one host to an individual host – Broadcast - the process of sending a packet from one host to all hosts in the network – Multicast - the process of sending a packet from one ...
CISCO Modes of Operations
... There are many different routing protocols, and they all use different variables, known as "metrics," to decide upon appropriate routes. A router needs to be running the same routing protocols as its neighbors do. Many routers can, however, run multiple protocols. Many protocols are designed to be a ...
... There are many different routing protocols, and they all use different variables, known as "metrics," to decide upon appropriate routes. A router needs to be running the same routing protocols as its neighbors do. Many routers can, however, run multiple protocols. Many protocols are designed to be a ...
Network and Service Discovery in Distributed Environments
... • others are forwarded to greater than “minimum distance-routing” links • (optical buffer may still be used here) • source-destination pair routes are no longer fixed, i.e. different routes possible as in IP • parameters that affect performance of deflection routing • network diameter (max. # of hop ...
... • others are forwarded to greater than “minimum distance-routing” links • (optical buffer may still be used here) • source-destination pair routes are no longer fixed, i.e. different routes possible as in IP • parameters that affect performance of deflection routing • network diameter (max. # of hop ...
isd5.2_prnt
... fabric, arbitrated loop and point-to-point. • Point-to-point defines a bi-directional connection between two devices. • Arbitrated loop defines a unidirectional ring in which only two devices can ever exchange data with one another at any one time. • Fabric defines a network in which several devices ...
... fabric, arbitrated loop and point-to-point. • Point-to-point defines a bi-directional connection between two devices. • Arbitrated loop defines a unidirectional ring in which only two devices can ever exchange data with one another at any one time. • Fabric defines a network in which several devices ...
IPv6 Land Speed Record
... R=C*(RTT**2)/2*MSS (where C is the link capacity and MSS is the max segment size). This is not a real problem for standard traffic on a shared link, but a serious penalty for long distance transfers of large amount of data. The TCP stack was designed a long time ago and for much slower networks: fro ...
... R=C*(RTT**2)/2*MSS (where C is the link capacity and MSS is the max segment size). This is not a real problem for standard traffic on a shared link, but a serious penalty for long distance transfers of large amount of data. The TCP stack was designed a long time ago and for much slower networks: fro ...
for TCP
... – Karn proposed not to update RTT on any retransmitted segment. – Instead RTT is doubled on each failure until segments get through. ...
... – Karn proposed not to update RTT on any retransmitted segment. – Instead RTT is doubled on each failure until segments get through. ...
PDF
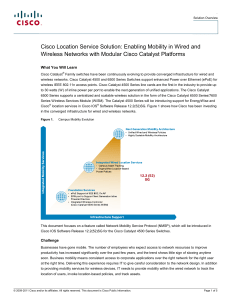
... network infrastructures. Those services typically provide high-level service capabilities such as location tracking. The Cisco 3300 Series MSE tracks the location of wired and wireless devices continuously. It can do this by having the wired and wireless network infrastructure devices (controllers a ...
... network infrastructures. Those services typically provide high-level service capabilities such as location tracking. The Cisco 3300 Series MSE tracks the location of wired and wireless devices continuously. It can do this by having the wired and wireless network infrastructure devices (controllers a ...
Chap 11 Routing
... Link-state advertisements (LSAs) A topological database The SPF algorithm; the SPF tree A routing table of paths and ports to each network ...
... Link-state advertisements (LSAs) A topological database The SPF algorithm; the SPF tree A routing table of paths and ports to each network ...
6LoWPAN adaptation layer (cont.)
... DYMO-low uses 16-bit link layer short address or IEEE 64-bit extended address (EUI-64). All of the features that discussed in LOAD above are used in DYMO-low except that the 16-bits sequence numbers are used in DYMO-low to ...
... DYMO-low uses 16-bit link layer short address or IEEE 64-bit extended address (EUI-64). All of the features that discussed in LOAD above are used in DYMO-low except that the 16-bits sequence numbers are used in DYMO-low to ...
ppt
... • Solution: in-network support for overlays – End-hosts establish reflection points in routers • Reduces strain on bottleneck links • Reduces packet duplication in application-layer multicast (next lecture) ...
... • Solution: in-network support for overlays – End-hosts establish reflection points in routers • Reduces strain on bottleneck links • Reduces packet duplication in application-layer multicast (next lecture) ...
PHD Proposal Draft
... Trunking, defined in IEEE 802.3ad [3]. It is a method of combining multiple physical network links between two devices into a single logical link for increased bandwidth. The upper layer applications or protocols, such as a MAC client, can treat the link aggregation group as if it were a single link ...
... Trunking, defined in IEEE 802.3ad [3]. It is a method of combining multiple physical network links between two devices into a single logical link for increased bandwidth. The upper layer applications or protocols, such as a MAC client, can treat the link aggregation group as if it were a single link ...
A Combined Routing+Queueing Approach to Improving
... wired sensor networks, or example Ethernet and ATM-based video surveillance network (VSN) using intelligent cameras, are a prime example. The Dallas-Fort Worth International Airport has deployed a VSN [1] that produces high-resolution, full-motion, broadcast-quality color images and audio in place o ...
... wired sensor networks, or example Ethernet and ATM-based video surveillance network (VSN) using intelligent cameras, are a prime example. The Dallas-Fort Worth International Airport has deployed a VSN [1] that produces high-resolution, full-motion, broadcast-quality color images and audio in place o ...
Best Practices: Installation and Setup of Crestron RF Products
... planning compared to hard-wired networks. Many additional factors affecting the strength and reliability of RF signals must be taken into consideration, including walls, furniture, other electronic equipment, and even people. Many common household electronic devices emit electromagnetic energy, whic ...
... planning compared to hard-wired networks. Many additional factors affecting the strength and reliability of RF signals must be taken into consideration, including walls, furniture, other electronic equipment, and even people. Many common household electronic devices emit electromagnetic energy, whic ...
4 Measuring Network Delay
... jitter is significantly reduced. The synchronization accuracy depends on the precision with which the source and destination hosts are able to synchronize their internal clock to the GPS signal. This method provides the accuracy of a few microseconds [15]. However, GPS has also several drawbacks. In ...
... jitter is significantly reduced. The synchronization accuracy depends on the precision with which the source and destination hosts are able to synchronize their internal clock to the GPS signal. This method provides the accuracy of a few microseconds [15]. However, GPS has also several drawbacks. In ...
... “Taking Turns” MAC protocols channel partitioning MAC protocols: share channel efficiently and fairly at high load inefficient at low load: delay in channel access, 1/N bandwidth allocated even if only 1 active node! random access MAC protocols efficient at low load: single node can fully uti ...
MTP SCCP message
... Essential for circuit-switching related signalling Not only ISDN (can be generally used in PSTN) ...
... Essential for circuit-switching related signalling Not only ISDN (can be generally used in PSTN) ...