Integrate Services Digital Network (ISDN) and SS7
... Before 1970, only channel-associated signalling (CAS) was used. In CAS systems, signalling always occurs in-band (i.e. over voice channels). ...
... Before 1970, only channel-associated signalling (CAS) was used. In CAS systems, signalling always occurs in-band (i.e. over voice channels). ...
32501-900
... The E-UTRAN/EPC network including its OSS. IP network connectivity exists between the eNodeB and the OAM (sub) systems providing support for the self-configuration process. The eNodeB is physically installed and physically connected to an IP network. The field personnel start the self-configuration ...
... The E-UTRAN/EPC network including its OSS. IP network connectivity exists between the eNodeB and the OAM (sub) systems providing support for the self-configuration process. The eNodeB is physically installed and physically connected to an IP network. The field personnel start the self-configuration ...
Introduction - School of Computing and Information Sciences
... A metropolitan area network based on cable TV. CEN 4500, S. Masoud Sadjadi ...
... A metropolitan area network based on cable TV. CEN 4500, S. Masoud Sadjadi ...
Manual D-Link AirPlus DI-614+
... Under many circumstances, it may be desirable for mobile network devices to link to a conventional Ethernet LAN in order to use servers, printers or an Internet connection supplied through the wired LAN. A Wireless Access Point (AP) is a device used to provide this link. People use wireless LAN tech ...
... Under many circumstances, it may be desirable for mobile network devices to link to a conventional Ethernet LAN in order to use servers, printers or an Internet connection supplied through the wired LAN. A Wireless Access Point (AP) is a device used to provide this link. People use wireless LAN tech ...
IEEE Vehicular Technology Conference (VTC)
... increase over time, as will the load of Internet traffic per vehicle, which means there is a possibility of ever-increasing interference and congestion that reduces the achievable throughput. A variety of mechanisms including RTS/CTS and exponential back-off are intended to limit the damage of conge ...
... increase over time, as will the load of Internet traffic per vehicle, which means there is a possibility of ever-increasing interference and congestion that reduces the achievable throughput. A variety of mechanisms including RTS/CTS and exponential back-off are intended to limit the damage of conge ...
Benefits of an Implementation of H-P2PSIP
... of the hierarchy. Other issues related with hierarchical ring topologies are published in [17]. Additional improvements and algorithms that are more complex can be used if necessary. Cyclone [18] builds a hierarchical DHT overlay network in similar manner with respect to [16]. However, it assures th ...
... of the hierarchy. Other issues related with hierarchical ring topologies are published in [17]. Additional improvements and algorithms that are more complex can be used if necessary. Cyclone [18] builds a hierarchical DHT overlay network in similar manner with respect to [16]. However, it assures th ...
1-i
... C. Martínez, R. Beivide, J. Gutierrez and E. Gabidulin. "On the Perfect tDominating Set Problem in Circulant Graphs and Codes over Gaussian Integers". Accepted for presentation at ISIT’05, September, Australia. This paper also deals with perfect resource placement. Broadcasting in Dense Gaussian Net ...
... C. Martínez, R. Beivide, J. Gutierrez and E. Gabidulin. "On the Perfect tDominating Set Problem in Circulant Graphs and Codes over Gaussian Integers". Accepted for presentation at ISIT’05, September, Australia. This paper also deals with perfect resource placement. Broadcasting in Dense Gaussian Net ...
Measurement guide and report template
... maintain a DNS cache (on Windows the entries are valid for 24 hours). This cache can be displayed by issuing the command ipconfig /displaydns and deleted with ipconfig /flushdns. You have to ping five different target nodes. Each time you also have to capture and records the network traffic by the h ...
... maintain a DNS cache (on Windows the entries are valid for 24 hours). This cache can be displayed by issuing the command ipconfig /displaydns and deleted with ipconfig /flushdns. You have to ping five different target nodes. Each time you also have to capture and records the network traffic by the h ...
3rd Edition, Chapter 5
... A creates link-layer frame with R's MAC address as dest, frame contains A-to-B IP datagram This is a really important A’s NIC sends frame ...
... A creates link-layer frame with R's MAC address as dest, frame contains A-to-B IP datagram This is a really important A’s NIC sends frame ...
Network Service and Applications
... Excessive congestion: packet delay and loss - protocols needed for reliable data transfer, congestion control Q: How to provide circuit-like behavior? - bandwidth guarantees needed for audio/video apps - still an unsolved problem - Overprovisioning often used Mao W07 ...
... Excessive congestion: packet delay and loss - protocols needed for reliable data transfer, congestion control Q: How to provide circuit-like behavior? - bandwidth guarantees needed for audio/video apps - still an unsolved problem - Overprovisioning often used Mao W07 ...
GD-Aggregate: A WAN Virtual Topology Building Tool for
... throughputs (when link capacity is precious). GR-Aggregate does not talk about this situation. What will happen? ...
... throughputs (when link capacity is precious). GR-Aggregate does not talk about this situation. What will happen? ...
COEN 252 Computer Forensics
... Copies network traffic from one switch port to another Only copy valid ethernet packets. Do not duplicate all error information. Copying process has lower priority and some packets might not be mirrored. Misses out on traffic on the local link. ...
... Copies network traffic from one switch port to another Only copy valid ethernet packets. Do not duplicate all error information. Copying process has lower priority and some packets might not be mirrored. Misses out on traffic on the local link. ...
ATM
... Currently mostly used for traffic engineering and network management. » LSPs can be thought of as “programmable links” that can be set up under software control » on top of a simple, static hardware infrastructure ...
... Currently mostly used for traffic engineering and network management. » LSPs can be thought of as “programmable links” that can be set up under software control » on top of a simple, static hardware infrastructure ...
Network Protocols Pre.
... Copies network traffic from one switch port to another Only copy valid ethernet packets. Do not duplicate all error information. Copying process has lower priority and some packets might not be mirrored. Misses out on traffic on the local link. ...
... Copies network traffic from one switch port to another Only copy valid ethernet packets. Do not duplicate all error information. Copying process has lower priority and some packets might not be mirrored. Misses out on traffic on the local link. ...
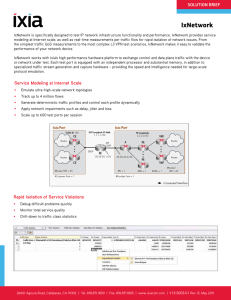
IxNetwork
... IxNetwork is specifically designed to test IP network infrastructure functionality and performance. IxNetwork provides service modeling at Internet scale, as well as real-time measurements per traffic flow for rapid isolation of network issues. From the simplest traffic QoS measurements to the most ...
... IxNetwork is specifically designed to test IP network infrastructure functionality and performance. IxNetwork provides service modeling at Internet scale, as well as real-time measurements per traffic flow for rapid isolation of network issues. From the simplest traffic QoS measurements to the most ...
router
... errors caused by signal attenuation, noise. receiver detects presence of errors: • signals sender for retransmission or drops frame ...
... errors caused by signal attenuation, noise. receiver detects presence of errors: • signals sender for retransmission or drops frame ...
PDF - This Chapter (262.0 KB)
... SNMP is an application-layer communication protocol that allows ONS 15600 network devices to exchange management information among these systems and with other devices outside the network. Through SNMP, network administrators can manage network performance, find and solve network problems, and plan ...
... SNMP is an application-layer communication protocol that allows ONS 15600 network devices to exchange management information among these systems and with other devices outside the network. Through SNMP, network administrators can manage network performance, find and solve network problems, and plan ...
DFL-M510 A3_Manual V1.02 - D-Link
... Mechanic & ID Design Front LED indicators ............................................................ 141 Physical Environment ............................................................................................... 142 ...
... Mechanic & ID Design Front LED indicators ............................................................ 141 Physical Environment ............................................................................................... 142 ...
Case Studies on IP-based Interconnection for Voice Services
... interest, operators will migrate from TDMvIC to IPvIC on a voluntary basis. However, in other cases regulatory intervention may be necessary. From a regulatory perspective, during the migration phase at least two crucial aspects have to be considered. Firstly, there are several different solutions w ...
... interest, operators will migrate from TDMvIC to IPvIC on a voluntary basis. However, in other cases regulatory intervention may be necessary. From a regulatory perspective, during the migration phase at least two crucial aspects have to be considered. Firstly, there are several different solutions w ...
Ethernet - ECE Users Pages
... Each interface must wait until there is no signal on the channel, then it can begin transmitting. If some other interface is transmitting there will be a signal on the channel, which is called carrier. All other interfaces must wait until carrier ceases before trying to transmit, and this process is ...
... Each interface must wait until there is no signal on the channel, then it can begin transmitting. If some other interface is transmitting there will be a signal on the channel, which is called carrier. All other interfaces must wait until carrier ceases before trying to transmit, and this process is ...
投影片 1
... net.link.ether.bridge_cfg: ed2:1,rl0:1 Set of interfaces for which bridging is enabled, and cluster they belong to net.link.ether.bridge: 0 Enable bridging net.link.ether.bridge_ipfw: 0 Enable ipfw for bridging ...
... net.link.ether.bridge_cfg: ed2:1,rl0:1 Set of interfaces for which bridging is enabled, and cluster they belong to net.link.ether.bridge: 0 Enable bridging net.link.ether.bridge_ipfw: 0 Enable ipfw for bridging ...
GPSR: Greedy Perimeter Stateless Routing for Wireless Networks
... state for a one-hop radius about a router is the minimum required to do any routing; no useful forwarding decision can be made without knowledge of the topology one or more hops away. This beaconing mechanism does represent pro-active routing protocol traffic, avoided by DSR and AODV. To minimize th ...
... state for a one-hop radius about a router is the minimum required to do any routing; no useful forwarding decision can be made without knowledge of the topology one or more hops away. This beaconing mechanism does represent pro-active routing protocol traffic, avoided by DSR and AODV. To minimize th ...