Spirent Journal of IEEE 802.3ba 40/100 GB Ethernet PASS
... How to use this Journal This provides test engineers with a battery of test cases for the Spirent Test Ecosystem. The journal is divided into sections by technology. Each test case has a unique Test Case ID that is universally unique across the ecosystem. Tester Requirements To determine the true ca ...
... How to use this Journal This provides test engineers with a battery of test cases for the Spirent Test Ecosystem. The journal is divided into sections by technology. Each test case has a unique Test Case ID that is universally unique across the ecosystem. Tester Requirements To determine the true ca ...
ppt
... • Priority queues: one-way sharing • high-priority traffic sources have impact on lower priority traffic only • has to be combined with admission control and traffic enforcement to avoid starvation of low-priority traffic ...
... • Priority queues: one-way sharing • high-priority traffic sources have impact on lower priority traffic only • has to be combined with admission control and traffic enforcement to avoid starvation of low-priority traffic ...
Slide 1
... increases, so too does the number of network routes. These IPv4 routes consume a great deal of memory and processor resources on Internet routers. ...
... increases, so too does the number of network routes. These IPv4 routes consume a great deal of memory and processor resources on Internet routers. ...
Cooper Bussmann 945U-E Wireless Ethernet Modem & Device Server User Manual
... connected to a suitable ground/earth and the aerial, aerial cable, serial cables and the module should be installed as recommended in the Installation Guide. 4. To avoid accidents during maintenance or adjustment of remotely controlled equipment, all equipment should be first disconnected from the ...
... connected to a suitable ground/earth and the aerial, aerial cable, serial cables and the module should be installed as recommended in the Installation Guide. 4. To avoid accidents during maintenance or adjustment of remotely controlled equipment, all equipment should be first disconnected from the ...
3. Centralized versus Distributed Mobility
... both the MN and the correspondent node (CN) are attached to the same MAG, and it is not applicable when the CN does not behave like an MN.) PS2: Divergence from other evolutionary trends in network architectures such as distribution of content delivery Mobile networks have generally been evolving to ...
... both the MN and the correspondent node (CN) are attached to the same MAG, and it is not applicable when the CN does not behave like an MN.) PS2: Divergence from other evolutionary trends in network architectures such as distribution of content delivery Mobile networks have generally been evolving to ...
24 Port Gigabit Ethernet PoE Switch User Manual
... • TP Port and Cable Installation In the switch, TP ports support MDI/MDI-X auto-crossover, so both types of cable, straight-through and crossed-over can be used. It means you do not have to tell from them, just plug it. Use Cat. 5 grade RJ-45 TP cable to connect to a TP port of the switch and the ot ...
... • TP Port and Cable Installation In the switch, TP ports support MDI/MDI-X auto-crossover, so both types of cable, straight-through and crossed-over can be used. It means you do not have to tell from them, just plug it. Use Cat. 5 grade RJ-45 TP cable to connect to a TP port of the switch and the ot ...
Multi-domain Diagnosis of End-to
... This paper introduces a distributed fault-localization technique [4,7], which increases the admissible network size by an order of magnitude by taking advantage of the domain semantics of communication systems. The technique divides the computational effort and system knowledge among hierarchically ...
... This paper introduces a distributed fault-localization technique [4,7], which increases the admissible network size by an order of magnitude by taking advantage of the domain semantics of communication systems. The technique divides the computational effort and system knowledge among hierarchically ...
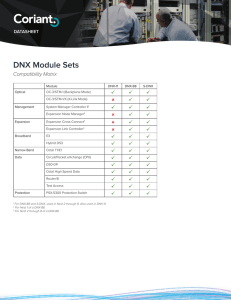
DNX Module Sets
... DS1s, 21 E1s, or a mixture of DS1s and E1s on the same DS3 link. The ability to mix DS1 and E1 on the same link complies with international standards and improves flexibility for global carriers. Diagnostic capabilities of the Hybrid DS3 include an unframed 215-1 T3 BERT that tests the whole pipe; a ...
... DS1s, 21 E1s, or a mixture of DS1s and E1s on the same DS3 link. The ability to mix DS1 and E1 on the same link complies with international standards and improves flexibility for global carriers. Diagnostic capabilities of the Hybrid DS3 include an unframed 215-1 T3 BERT that tests the whole pipe; a ...
Internet Big Bang Theory
... optically switched network and how such a network might evolve as each decimal order of magnitude of growth occurs. First we must consider the current size of Internet backbones. Global Crossings has been very open about their design [9]. It utilizes tens of backbone routers interconnected primarily ...
... optically switched network and how such a network might evolve as each decimal order of magnitude of growth occurs. First we must consider the current size of Internet backbones. Global Crossings has been very open about their design [9]. It utilizes tens of backbone routers interconnected primarily ...
Slide 0
... • But nearly half the RAC sites I visit are suffering from RAC performance issues related to this! • Still far too RAC experts among the general DBA population (although improving each & every day) • Really no simple, single button tools yet to make RAC “auto-magically” “fire on all cylinders” • Man ...
... • But nearly half the RAC sites I visit are suffering from RAC performance issues related to this! • Still far too RAC experts among the general DBA population (although improving each & every day) • Really no simple, single button tools yet to make RAC “auto-magically” “fire on all cylinders” • Man ...
Workgroup Systems
... As an ENERGY STAR® Partner, Canon U.S.A., Inc. has determined that these products meet the ENERGY STAR guidelines for energy efficiency. ENERGY STAR and the ENERGY STAR mark are registered U.S. marks. Windows and Windows NT are registered trademarks of Microsoft Corporation in the United States and/ ...
... As an ENERGY STAR® Partner, Canon U.S.A., Inc. has determined that these products meet the ENERGY STAR guidelines for energy efficiency. ENERGY STAR and the ENERGY STAR mark are registered U.S. marks. Windows and Windows NT are registered trademarks of Microsoft Corporation in the United States and/ ...
Simple Network Management Protocol (SNMP) Primer
... Read-Only: When the Community String is set to Read-Only, the information in the MIB can only be read and not modified. A client is only allowed to issue getRequest and getNextRequest commands with the Read-Only community name. Read-Write: A Read-Write setting allows the value of the MIB object to b ...
... Read-Only: When the Community String is set to Read-Only, the information in the MIB can only be read and not modified. A client is only allowed to issue getRequest and getNextRequest commands with the Read-Only community name. Read-Write: A Read-Write setting allows the value of the MIB object to b ...
ppt - DePaul University
... Hides underlying technologies from end user Facilitate communicate between autonomous domains Able to move packets between any host on the internetwork ...
... Hides underlying technologies from end user Facilitate communicate between autonomous domains Able to move packets between any host on the internetwork ...
ppt
... Stream Editor (SED) - two parallel engines - modify outgoing packets (e.g., checksum, TTL, …) - configurable, but not programmable ...
... Stream Editor (SED) - two parallel engines - modify outgoing packets (e.g., checksum, TTL, …) - configurable, but not programmable ...
An Overview of Embedded Sensor Networks
... Examples of in-network processing are duplicate suppression, data aggregation, and statistical filtering. When data is generated from multiple sensors, in-network processing can merge this data near those sites rather than sending all data out, thus greatly reducing energy consumption. (This approac ...
... Examples of in-network processing are duplicate suppression, data aggregation, and statistical filtering. When data is generated from multiple sensors, in-network processing can merge this data near those sites rather than sending all data out, thus greatly reducing energy consumption. (This approac ...
C Spire Wireless
... Help Menu ................................................................................................................................ 36 About ..................................................................................................................................... 36 User Guide .... ...
... Help Menu ................................................................................................................................ 36 About ..................................................................................................................................... 36 User Guide .... ...
Optimizing Multiple Distributed Stream Queries Using Hierarchical Network Partitions
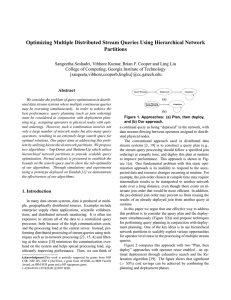
... the number of possible plan and deployment combinations can grow exponentially. The cost of considering all possibilities exhaustively is prohibitive. Consider Figure 2. With a network of 64 nodes, combining query plans and plan deployments simultaneously required us to examine 2.88 × 109 plans for ...
... the number of possible plan and deployment combinations can grow exponentially. The cost of considering all possibilities exhaustively is prohibitive. Consider Figure 2. With a network of 64 nodes, combining query plans and plan deployments simultaneously required us to examine 2.88 × 109 plans for ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... between nodes are capable of changing on a continual basis. MANETs are self-configuring; there is no central management system with configuration responsibilities. All the mobile nodes can communicate each other directly, if they are in other’s wireless links radio range. In order to enable data tra ...
... between nodes are capable of changing on a continual basis. MANETs are self-configuring; there is no central management system with configuration responsibilities. All the mobile nodes can communicate each other directly, if they are in other’s wireless links radio range. In order to enable data tra ...
IntelliServ™ Product Catalog
... IntelliServ has developed DataSwivels for the following Top Drive models. ...
... IntelliServ has developed DataSwivels for the following Top Drive models. ...
Chapter 6 slides, Computer Networking, 3rd edition
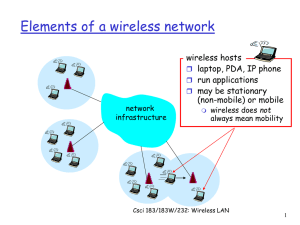
... infrastructure mode base station connects mobiles into wired network handoff: mobile changes base station ...
... infrastructure mode base station connects mobiles into wired network handoff: mobile changes base station ...