IEC 62591 Wireless Interface Instruction Manual Remote Automation Solutions
... Be sure that these instructions are carefully read and understood before any operation is attempted. Improper use of this device in some applications may result in damage or injury. The user is urged to keep this book filed in a convenient location for future reference. These instructions may not co ...
... Be sure that these instructions are carefully read and understood before any operation is attempted. Improper use of this device in some applications may result in damage or injury. The user is urged to keep this book filed in a convenient location for future reference. These instructions may not co ...
OSI layers
... communicate with each other, and use a star topology. Like a repeater, a hub regenerates the signal. Hubs have the same disadvantage as a repeater, anything it receives on one port, it FLOODS out all other ports. Wherever possible, hubs should be replace by switches. ...
... communicate with each other, and use a star topology. Like a repeater, a hub regenerates the signal. Hubs have the same disadvantage as a repeater, anything it receives on one port, it FLOODS out all other ports. Wherever possible, hubs should be replace by switches. ...
V100R001C04 - Huawei Enterprise
... The RP series products provide the static network address translation (NAT) function. If the number of terminals within the firewall is small, the terminals can traverse the firewall or a NAT device by configuring one-to-one mappings for public and private networks on the firewall. For one-to-one ma ...
... The RP series products provide the static network address translation (NAT) function. If the number of terminals within the firewall is small, the terminals can traverse the firewall or a NAT device by configuring one-to-one mappings for public and private networks on the firewall. For one-to-one ma ...
No Slide Title
... Usually happens when the interface is configured at bootstrap time. The interface uses gratuitous ARP to determine if there are other hosts using the same IP address. The sender’s IP and MAC address are broadcast, and other hosts will insert this mapping into their ARP tables. ...
... Usually happens when the interface is configured at bootstrap time. The interface uses gratuitous ARP to determine if there are other hosts using the same IP address. The sender’s IP and MAC address are broadcast, and other hosts will insert this mapping into their ARP tables. ...
Transcranial Alternating Current Stimulation Modulates Large
... Transcranial direct current stimulation (tDCS) has emerged as a potentially safe and effective brain stimulation modality that alters cortical excitability by passing a small, constant electric current through the scalp. tDCS creates an electric field that weakly modulates the membrane voltage of a ...
... Transcranial direct current stimulation (tDCS) has emerged as a potentially safe and effective brain stimulation modality that alters cortical excitability by passing a small, constant electric current through the scalp. tDCS creates an electric field that weakly modulates the membrane voltage of a ...
Internet Control Message Protocol
... Thanks to Philippe Biondi of Cartel Security for reporting this vulnerability. ...
... Thanks to Philippe Biondi of Cartel Security for reporting this vulnerability. ...
VLSM and CIDR 04/01/2008 Modified by Tony Chen – Chapter 6
... –Let us assume that router X has a specific route for 172.22.0.0/16 using Serial 0/0/1 and a summary route of 172.16.0.0/13 using Serial0/0/0. –Packets with the IP address of 172.22.n.n match both route entries. –These packets destined for 172.22.0.0 would be sent out the Serial0/0/1 interface becau ...
... –Let us assume that router X has a specific route for 172.22.0.0/16 using Serial 0/0/1 and a summary route of 172.16.0.0/13 using Serial0/0/0. –Packets with the IP address of 172.22.n.n match both route entries. –These packets destined for 172.22.0.0 would be sent out the Serial0/0/1 interface becau ...
In NGN - APNOMS
... request to achieve QoS guarantee – Relative QoS (e.g., diffserv’s CoS) is acceptable – Various message flow and protocols are defined, operators will choose ...
... request to achieve QoS guarantee – Relative QoS (e.g., diffserv’s CoS) is acceptable – Various message flow and protocols are defined, operators will choose ...
User Manual
... 4. To avoid accidents during maintenance or adjustment of remotely controlled equipment, all equipment should be first disconnected from the 245U-E module during these adjustments. Equipment should carry clear markings to indicate remote or automatic operation. For example, “This equipment is remot ...
... 4. To avoid accidents during maintenance or adjustment of remotely controlled equipment, all equipment should be first disconnected from the 245U-E module during these adjustments. Equipment should carry clear markings to indicate remote or automatic operation. For example, “This equipment is remot ...
Powerpoint
... • Transit - carrying network traffic across a network, usually for a fee • Peering - exchanging routing information and traffic – your customers and your peers customers network information only ...
... • Transit - carrying network traffic across a network, usually for a fee • Peering - exchanging routing information and traffic – your customers and your peers customers network information only ...
vRealize Operations Management Pack for Storage Devices 6.0.1
... NOTE Any adapter credentials you add are shared with other adapter administrators and vRealize Operations Manager collector hosts. Other administrators might use these credentials to configure a new adapter instance or to move an adapter instance to a new host. Prerequisites Verify that the followin ...
... NOTE Any adapter credentials you add are shared with other adapter administrators and vRealize Operations Manager collector hosts. Other administrators might use these credentials to configure a new adapter instance or to move an adapter instance to a new host. Prerequisites Verify that the followin ...
Martin Herzog, Technical University Berlin
... TDM traffic with a high level of quality of service (QoS). Similar to Ethernet, RPR provides advantages of low equipment cost and simplicity, and exhibits an improved bandwidth utilization due to statistical multiplexing. The bandwidth utilization is further increased by means of spatial reuse. In R ...
... TDM traffic with a high level of quality of service (QoS). Similar to Ethernet, RPR provides advantages of low equipment cost and simplicity, and exhibits an improved bandwidth utilization due to statistical multiplexing. The bandwidth utilization is further increased by means of spatial reuse. In R ...
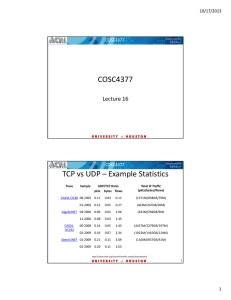
COSC4377 TCP vs UDP – Example Statistics
... minimal (if any) configuration of routers, and no additional servers. The stateless mechanism allows a host to generate its own addresses using a combination of locally available information and information advertised by routers. Routers advertise prefixes that identify the subnet(s) associated w ...
... minimal (if any) configuration of routers, and no additional servers. The stateless mechanism allows a host to generate its own addresses using a combination of locally available information and information advertised by routers. Routers advertise prefixes that identify the subnet(s) associated w ...
update on NLR
... circuits, (b) stable transport to sustain control and streaming operations, and (c) middleware and application software to support data transfers, visualization, steering and control. • Infrastructure - WaveNet circuit ...
... circuits, (b) stable transport to sustain control and streaming operations, and (c) middleware and application software to support data transfers, visualization, steering and control. • Infrastructure - WaveNet circuit ...
QoS Requirement of Network Applicationson the Internet.pdf
... applications), are bonded in a single-service platform through Internet technology. Media are transmitted on a network by bit streams. Each bit stream is represented by a flow of bits of 1s and 0s through the network. Although all media are transmitted in the same digital form, each application gene ...
... applications), are bonded in a single-service platform through Internet technology. Media are transmitted on a network by bit streams. Each bit stream is represented by a flow of bits of 1s and 0s through the network. Although all media are transmitted in the same digital form, each application gene ...
Topic 16: Routing in IP over ATM networks
... The packet encapsulation has been defined in RFC1483 ([9], now obsoleted by [10]), which also takes into account the saving of virtual connections by multiplexing different protocols into a single VC. The LLC/SNAP encapsulation defined in RFC1483 is the most common encapsulation in IP over ATM netwo ...
... The packet encapsulation has been defined in RFC1483 ([9], now obsoleted by [10]), which also takes into account the saving of virtual connections by multiplexing different protocols into a single VC. The LLC/SNAP encapsulation defined in RFC1483 is the most common encapsulation in IP over ATM netwo ...
LS 131 109
... understanding of the SIGTRAN architectural and technology. SIGTRAN (Signaling Transport) over IP is a working group within the IETF standard organization and it was developed to allow an interworking between SS7 network elements and IP based elements. Its primary purpose is to address the transport ...
... understanding of the SIGTRAN architectural and technology. SIGTRAN (Signaling Transport) over IP is a working group within the IETF standard organization and it was developed to allow an interworking between SS7 network elements and IP based elements. Its primary purpose is to address the transport ...
PRESENTATION TITLE/SIZE 30
... Create TCL policy scripts to program the Catalyst 6500 – When detect event X, then do action Y • Generic On-Line Diagnostics (GOLD) supports pro-active diagnosis of faults before they become a problem… © 2005 Cisco Systems, Inc. All rights reserved. ...
... Create TCL policy scripts to program the Catalyst 6500 – When detect event X, then do action Y • Generic On-Line Diagnostics (GOLD) supports pro-active diagnosis of faults before they become a problem… © 2005 Cisco Systems, Inc. All rights reserved. ...
SNAMP: Secure Namespace Mapping to Scale NDN Forwarding
... – objective of retrieving – specifics of how to do it ...
... – objective of retrieving – specifics of how to do it ...
Introduction and Overview
... CCS systems are packet-based, transferring over 200 bytes in a single SS7 packet, as opposed to a few bits allocated to act as indicators in digital CAS. The signaling information is transferred by means of messages, which is a block of information that is divided into fields that define a certain p ...
... CCS systems are packet-based, transferring over 200 bytes in a single SS7 packet, as opposed to a few bits allocated to act as indicators in digital CAS. The signaling information is transferred by means of messages, which is a block of information that is divided into fields that define a certain p ...
Network Loss Inference with Second Order Statistics
... throughout the measurement period. • T.2 No route fluttering: There is no pair of paths Pi and Pi′ that share two links ej and ej ′ without also sharing all the links located in between ej and ej ′ . That is, the two paths never meet at one link, diverge, and meet again further away at another link. ...
... throughout the measurement period. • T.2 No route fluttering: There is no pair of paths Pi and Pi′ that share two links ej and ej ′ without also sharing all the links located in between ej and ej ′ . That is, the two paths never meet at one link, diverge, and meet again further away at another link. ...
PowerPoint Presentation - requirements for delivering MPLS
... • Will add application scenarios based on comments • Stitching LSPs • CE-PE: C-TE LSPs • PE-PE: non-TE LSPs (LDP) • PE-CE: C-TE LSPs ...
... • Will add application scenarios based on comments • Stitching LSPs • CE-PE: C-TE LSPs • PE-PE: non-TE LSPs (LDP) • PE-CE: C-TE LSPs ...
Document
... header. This simplifies and speeds up the routing process because most of the options do not need to be checked by routers. ...
... header. This simplifies and speeds up the routing process because most of the options do not need to be checked by routers. ...
network - Victoria College
... • The definition of classless inter-domain routing (CIDR): – Allocation of one or more blocks of Class C network numbers to each network service provider – Organizations using the network service provider for Internet connectivity are allocated bitmask-oriented subsets of the provider’s address spac ...
... • The definition of classless inter-domain routing (CIDR): – Allocation of one or more blocks of Class C network numbers to each network service provider – Organizations using the network service provider for Internet connectivity are allocated bitmask-oriented subsets of the provider’s address spac ...
Tapestry: A Resilient Global-scale Overlay for Service Deployment
... durability, and performance. One technique for achieving these properties is to adapt to failures or changes in load through migration and replication of data and services. Unfortunately, the ability to place replicas or the frequency with which they may be moved is limited by underlying infrastruct ...
... durability, and performance. One technique for achieving these properties is to adapt to failures or changes in load through migration and replication of data and services. Unfortunately, the ability to place replicas or the frequency with which they may be moved is limited by underlying infrastruct ...