router - DAINF
... D = Data protected by error checking, may include header fields • Error detection not 100% reliable! • protocol may miss some errors, but rarely • larger EDC field yields better detection and correction ...
... D = Data protected by error checking, may include header fields • Error detection not 100% reliable! • protocol may miss some errors, but rarely • larger EDC field yields better detection and correction ...
12.[2014-286](제정). - TTA표준화 위원회
... which, through reference in this text, constitute provisions of this Recommendation. At the time of publication, the editions indicated were valid. All Recommendations and other references are subject to revision; users of this Recommendation are therefore encouraged to investigate the possibility o ...
... which, through reference in this text, constitute provisions of this Recommendation. At the time of publication, the editions indicated were valid. All Recommendations and other references are subject to revision; users of this Recommendation are therefore encouraged to investigate the possibility o ...
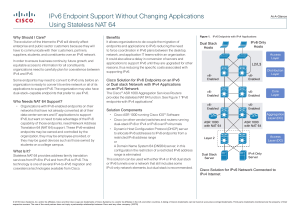
IPv6 Endpoint Support Without Changing Applications Using Stateless NAT 64
... Internet. One important restriction of this solution is that it requires each host in the IPv6 network that needs to communicate with the IPv4 Internet to have a routable IPv4 address at the Cisco ASR 1000, so it does not currently solve the address exhaustion problem. This solution is useful for cu ...
... Internet. One important restriction of this solution is that it requires each host in the IPv6 network that needs to communicate with the IPv4 Internet to have a routable IPv4 address at the Cisco ASR 1000, so it does not currently solve the address exhaustion problem. This solution is useful for cu ...
Brief - Electronic Privacy Information Center
... right in law to communicate privately across computer networks. The Electronic Communications Privacy Act of 1986 (“ECPA”) ensures the privacy of these communications, and its protections should not be interpreted in an unfair and inconsistent way. The fact that sophisticated parties may be able to ...
... right in law to communicate privately across computer networks. The Electronic Communications Privacy Act of 1986 (“ECPA”) ensures the privacy of these communications, and its protections should not be interpreted in an unfair and inconsistent way. The fact that sophisticated parties may be able to ...
Power over Ethernet (PoE)
... • VTP Transparent mode allows the creation or deletion of VLAN’s of local significance only. VLAN information is stored in switch memory. Will pass VTP information to other switches within the same domain. ...
... • VTP Transparent mode allows the creation or deletion of VLAN’s of local significance only. VLAN information is stored in switch memory. Will pass VTP information to other switches within the same domain. ...
PDF
... The snmp-server enable traps command is used in conjunction with the snmp-server host command. Use the snmp-server host command to specify which host or hosts receive SNMP notifications. To send notifications, you must configure at least one snmp-server host command. For a host to receive a notifica ...
... The snmp-server enable traps command is used in conjunction with the snmp-server host command. Use the snmp-server host command to specify which host or hosts receive SNMP notifications. To send notifications, you must configure at least one snmp-server host command. For a host to receive a notifica ...
VERTICAL HORIZON VH-2402-L3 FAST ETHERNET SWITCH
... 5. Develop a security scheme. Some subnets on the network need more security or should be isolated from the other subnets. IP or MAC filtering can be used. Also, one or more VLANs on the Layer 3 switch can be configured without an IP subnet – in which case, these VLANs will function as a layer 2 VLA ...
... 5. Develop a security scheme. Some subnets on the network need more security or should be isolated from the other subnets. IP or MAC filtering can be used. Also, one or more VLANs on the Layer 3 switch can be configured without an IP subnet – in which case, these VLANs will function as a layer 2 VLA ...
lecture-03-thu-fri-routing-isis
... topology; only know direction (shortest path) to networks in other areas. Area Border routers “summarize” distances to networks in the area and advertise them to other Area Border routers. Backbone routers: run an OSPF routing algorithm limited to the backbone. Boundary routers: connect to oth ...
... topology; only know direction (shortest path) to networks in other areas. Area Border routers “summarize” distances to networks in the area and advertise them to other Area Border routers. Backbone routers: run an OSPF routing algorithm limited to the backbone. Boundary routers: connect to oth ...
1 - Southern California Edison
... Home area network (HAN) (e.g. Z-Wave, Zigbee, Bluetooth) Interface to distributed generation Interface to transmission and distribution automation systems Interface to peripheral devices or expansion modules such as displays or switch panels. ...
... Home area network (HAN) (e.g. Z-Wave, Zigbee, Bluetooth) Interface to distributed generation Interface to transmission and distribution automation systems Interface to peripheral devices or expansion modules such as displays or switch panels. ...
Advanced SCSI Programming Interface over Internet Protocol
... manner subject to recent commercial and scientific research. While most existing solutions relate to the SCSI (Small Computers System Interface) standard, resulting in a high degree of universality, from an end-user’s point of view there is, however, a lack of dedicated support for remote optical st ...
... manner subject to recent commercial and scientific research. While most existing solutions relate to the SCSI (Small Computers System Interface) standard, resulting in a high degree of universality, from an end-user’s point of view there is, however, a lack of dedicated support for remote optical st ...
Taxonomy of IP Traceback - College of Engineering and Computing
... overwrites its source address on the outgoing packet headers and also applies some packet transformation to conceal the true origin. Most of the traceback schemes are capable of tracing only till the stepping stone. The stepping stones can be identified using specialized techniques only that looks f ...
... overwrites its source address on the outgoing packet headers and also applies some packet transformation to conceal the true origin. Most of the traceback schemes are capable of tracing only till the stepping stone. The stepping stones can be identified using specialized techniques only that looks f ...
Potential IP Solutions for Networking Selected FAA Weather
... converters would communicate via IP routers that would form an IP cloud). The test was set up to emulate the connection of an ADAS port to two ASOSs. Three protocol converters were used where one converter was connected to the ADAS port and the other two were each connected to the two ASOSs using th ...
... converters would communicate via IP routers that would form an IP cloud). The test was set up to emulate the connection of an ADAS port to two ASOSs. Three protocol converters were used where one converter was connected to the ADAS port and the other two were each connected to the two ASOSs using th ...
Microsoft Word - PRISMA 2009 Checklist
... respectively. There was no obvious bias in each group (P > 0.05 was considered as no publication bias). Begg's funnel plots were shown in the Supporting Information (S1-S3 Figs). In addition, we performed sensitivity analysis of 22 trials for stroke prevention, in which one study was removed at a ti ...
... respectively. There was no obvious bias in each group (P > 0.05 was considered as no publication bias). Begg's funnel plots were shown in the Supporting Information (S1-S3 Figs). In addition, we performed sensitivity analysis of 22 trials for stroke prevention, in which one study was removed at a ti ...
Linux+ Guide to Linux Certification
... two or more BSS networks that are connected through a common distribution system • An Independent Basic Service Set (IBSS) is a wireless network that does not use an access point • Frames are used by both wireless NICs and access points for communication and for managing and controlling the wireless ...
... two or more BSS networks that are connected through a common distribution system • An Independent Basic Service Set (IBSS) is a wireless network that does not use an access point • Frames are used by both wireless NICs and access points for communication and for managing and controlling the wireless ...
No Slide Title
... Regular routing updates: Every 30 seconds, send all or part of the routing tables to every neighbor. Triggered Updates: Whenever the metric for a route changes, send data that has changed. ...
... Regular routing updates: Every 30 seconds, send all or part of the routing tables to every neighbor. Triggered Updates: Whenever the metric for a route changes, send data that has changed. ...
Quality of Service
... How to Diagnose with Ping 1. to localhost (127.0.0.1), 2. ping to gateway (use route or traceroute (tracert on Windows) to find gateway), 3. ping to well known host 4. & to relevant remote host – Use IP address to avoid nameserver problems – Look for connectivity, loss, RTT, jitter, dups – May need ...
... How to Diagnose with Ping 1. to localhost (127.0.0.1), 2. ping to gateway (use route or traceroute (tracert on Windows) to find gateway), 3. ping to well known host 4. & to relevant remote host – Use IP address to avoid nameserver problems – Look for connectivity, loss, RTT, jitter, dups – May need ...
The Tenet Architecture for Tiered Sensor Networks
... view of sensor networking, the principle constrains the processing of data received from multiple sensors to be placed at the master tier, regardless of whether that processing is specific to an application or can be expressed as a generic fusion service. (It might, for example, be possible to cast ...
... view of sensor networking, the principle constrains the processing of data received from multiple sensors to be placed at the master tier, regardless of whether that processing is specific to an application or can be expressed as a generic fusion service. (It might, for example, be possible to cast ...
Network Performance Definitions - Network Startup Resource Center
... Can be confusing at first Consider this example: Two 100 Mbps circuits - 1 km of optic fiber - Via satellite with a distance of 30 km between the base and the satellite ...
... Can be confusing at first Consider this example: Two 100 Mbps circuits - 1 km of optic fiber - Via satellite with a distance of 30 km between the base and the satellite ...
23.22
... The contents of the present document are subject to continuing work within the TSG and may change following formal TSG approval. Should the TSG modify the contents of the present document, it will be re-released by the TSG with an identifying change of release date and an increase in version number ...
... The contents of the present document are subject to continuing work within the TSG and may change following formal TSG approval. Should the TSG modify the contents of the present document, it will be re-released by the TSG with an identifying change of release date and an increase in version number ...
2920 Switch Series PDF
... This Basic Layer 3 switch series supports modular stacking, 10GbE, PoE+, static and RIP routing, Access OSPF routing, Tunneled Node, ACLs, sFlow, and IPv6. The 2920 delivers a consistent wired/wireless user experience with advanced security and network management tools with Aruba ClearPass Policy Ma ...
... This Basic Layer 3 switch series supports modular stacking, 10GbE, PoE+, static and RIP routing, Access OSPF routing, Tunneled Node, ACLs, sFlow, and IPv6. The 2920 delivers a consistent wired/wireless user experience with advanced security and network management tools with Aruba ClearPass Policy Ma ...
20111011-DYNES_USATLAS - Indico
... – DYNES will be operated, tested, integrated and optimized at scale, transitioning to routine operations and maintenance as soon as this ...
... – DYNES will be operated, tested, integrated and optimized at scale, transitioning to routine operations and maintenance as soon as this ...
OSPF - Treca
... Uses Dijkstra Algorithm Supports multiple equal cost routes to the destination Consists of areas ...
... Uses Dijkstra Algorithm Supports multiple equal cost routes to the destination Consists of areas ...
Part2.3Internetworki..
... Send ARP request message to T Receive reply with T’s hardware address ...
... Send ARP request message to T Receive reply with T’s hardware address ...
. - TTA표준화 위원회](http://s1.studyres.com/store/data/004568034_1-cea0cb43984c16e12bdd271f5f03676e-300x300.png)