Why Network Computers?
... The function of a hub is to direct information around the network, facilitating communication between all connected devices. However in new installations switches should be used instead of hubs as they are more effective and provide better performance. Switches Switches are the more recent technolo ...
... The function of a hub is to direct information around the network, facilitating communication between all connected devices. However in new installations switches should be used instead of hubs as they are more effective and provide better performance. Switches Switches are the more recent technolo ...
Chapter 11
... Must be unique on the network Must not be chosen at random Must be assigned by a network administrator ...
... Must be unique on the network Must not be chosen at random Must be assigned by a network administrator ...
Andrew Knotts` presentation on Distributed DOS attacks
... Flow data can be useful for analyzing the behavior characteristics of traffic. In order for flow data to be useful for detecting attacks, it must be processed fast enough to respond. Munz and Carle [2] propose a system and framework to handle the real-time analysis of this flow data. ...
... Flow data can be useful for analyzing the behavior characteristics of traffic. In order for flow data to be useful for detecting attacks, it must be processed fast enough to respond. Munz and Carle [2] propose a system and framework to handle the real-time analysis of this flow data. ...
Introduction - Petra Christian University
... • Nodes: PC, special-purpose hardware… – hosts – switches ...
... • Nodes: PC, special-purpose hardware… – hosts – switches ...
TCP/IP Protocol Architecture
... functions across multiple networks for systems attached to different networks using IP protocol implemented in end systems and routers routers connect two networks and relays data between them ...
... functions across multiple networks for systems attached to different networks using IP protocol implemented in end systems and routers routers connect two networks and relays data between them ...
Protocol Architecture, TCP/IP, and Internet
... attached network • concerned with issues like : – destination address provision – invoking specific services like priority – access to & routing data across a network link between two attached systems ...
... attached network • concerned with issues like : – destination address provision – invoking specific services like priority – access to & routing data across a network link between two attached systems ...
lecture9 - Academic Csuohio
... Example services for a flow of datagrams: • In-order datagram delivery • Guaranteed minimum bandwidth to flow • Restrictions on changes in inter-packet spacing • No guarantee whatsoever ...
... Example services for a flow of datagrams: • In-order datagram delivery • Guaranteed minimum bandwidth to flow • Restrictions on changes in inter-packet spacing • No guarantee whatsoever ...
An Introduction to Computer Networks
... Options are rarely used in today except for ‘loose’ and ‘strict’ source routing parameters. ‘loose’ and ‘strict’ source option sometimes, is used for IP encapsulation in another IP or ...
... Options are rarely used in today except for ‘loose’ and ‘strict’ source routing parameters. ‘loose’ and ‘strict’ source option sometimes, is used for IP encapsulation in another IP or ...
PPT Version
... not adequate for needs of MBWA and Next-Gen multi-access wide-area networks • Need for a localized MM protocol – Optimized for handover performance of different application classes, client power-management states and IP reachability ...
... not adequate for needs of MBWA and Next-Gen multi-access wide-area networks • Need for a localized MM protocol – Optimized for handover performance of different application classes, client power-management states and IP reachability ...
Cellular IP Modems
... The OnCell G3100 comes bundled with Real COM drivers for Windows 98, ME, NT, 2000, XP, 2003, and Vista systems. In Real COM mode, the bundled drivers are able to establish a transparent connection between a host and a serial device by mapping the serial port on the OnCell G3100 to a local COM port o ...
... The OnCell G3100 comes bundled with Real COM drivers for Windows 98, ME, NT, 2000, XP, 2003, and Vista systems. In Real COM mode, the bundled drivers are able to establish a transparent connection between a host and a serial device by mapping the serial port on the OnCell G3100 to a local COM port o ...
Pass4sure 640
... A. A CSU/DSU terminates a digital local loop. B. A router is commonly considered a DCE device. C. A modem terminates an analog local loop. D. A router is commonly considered a DTE device. E. A modem terminates a digital local loop. F. A CSU/DSU terminates an analog local loop. G. A modem is used to ...
... A. A CSU/DSU terminates a digital local loop. B. A router is commonly considered a DCE device. C. A modem terminates an analog local loop. D. A router is commonly considered a DTE device. E. A modem terminates a digital local loop. F. A CSU/DSU terminates an analog local loop. G. A modem is used to ...
Terminal Bridge Extension Over Distributed Architecture
... Extension provides very flexible architecture to use distributed services in changing wireless environment • Using very different wireless technologies together provides new possibilities for creating and using services ...
... Extension provides very flexible architecture to use distributed services in changing wireless environment • Using very different wireless technologies together provides new possibilities for creating and using services ...
SANS Top 5 Essential Log Reports
... it has traversed routers on the network. While it is possible routing errors can cause these packets, they are usually an indication that someone is probing the network with a tracing tool such as traceroute, Firewalk, TCPTraceroute, or similar. The latter two tools are the hardest to protect agains ...
... it has traversed routers on the network. While it is possible routing errors can cause these packets, they are usually an indication that someone is probing the network with a tracing tool such as traceroute, Firewalk, TCPTraceroute, or similar. The latter two tools are the hardest to protect agains ...
Fundamentals of Computer Networks
... • IEEE 802.3, popularly called Ethernet is a bus-based broadcast network. • Computers on an Ethernet can transmit whenever they want to; if two or more packets collide, each computer just waits a random time and tries again later. ...
... • IEEE 802.3, popularly called Ethernet is a bus-based broadcast network. • Computers on an Ethernet can transmit whenever they want to; if two or more packets collide, each computer just waits a random time and tries again later. ...
Introduction
... Layer 3: Network layer provides the functional and procedural means of transferring variable length data sequences from a source to a destination via one or more networks while maintaining the quality of service requested by the Transport layer performs network routing functions, and might al ...
... Layer 3: Network layer provides the functional and procedural means of transferring variable length data sequences from a source to a destination via one or more networks while maintaining the quality of service requested by the Transport layer performs network routing functions, and might al ...
Virtual Private Networks - Mathematics and Computer Science
... “A virtual private network (VPN) is the extension of a private network that encompasses links across shared or public networks like the Internet.” (Microsoft, 2001) ► It ...
... “A virtual private network (VPN) is the extension of a private network that encompasses links across shared or public networks like the Internet.” (Microsoft, 2001) ► It ...
OSA journals template (MSWORD)
... system requires bidirectional propagation inside each fiber segment. Second, standard telecommunication networks use optical to electrical conversion of data signal in all nodes and regenerators, whereas RS dissemination has to be purely optical from end to end. Therefore most of the network equipme ...
... system requires bidirectional propagation inside each fiber segment. Second, standard telecommunication networks use optical to electrical conversion of data signal in all nodes and regenerators, whereas RS dissemination has to be purely optical from end to end. Therefore most of the network equipme ...
presentation
... – High scalability with no performance loss – SIP and XML-based interfaces don’t lock you into a proprietary architecture ...
... – High scalability with no performance loss – SIP and XML-based interfaces don’t lock you into a proprietary architecture ...
NFN Gateway
... NOTIFIER® is a Honeywell company. This document is not intended to be used for installation purposes. We try to keep our product information up-to-date and accurate. We cannot cover all specific applications or anticipate all requirements. All specifications are subject to change without notice. For ...
... NOTIFIER® is a Honeywell company. This document is not intended to be used for installation purposes. We try to keep our product information up-to-date and accurate. We cannot cover all specific applications or anticipate all requirements. All specifications are subject to change without notice. For ...
Enactment of dynamic programming tactic Formation of
... experimentation and testing of new innovations and new protocols, which can also be solved by the virtual network infrastructure. [1,2,3] ...
... experimentation and testing of new innovations and new protocols, which can also be solved by the virtual network infrastructure. [1,2,3] ...
Introduction - Faculty of Computer Science
... We’re making these slides freely available to all (faculty, students, readers). They’re in powerpoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in powerpoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the ...
lecture20
... On both surrounding hillsides are blue armies. The white army is larger than either of the blue armies alone, but together the blue armies are larger than the white army. If either blue army attacks by itself, it will be defeated, but if the two blue armies attack simultaneously, they will be victor ...
... On both surrounding hillsides are blue armies. The white army is larger than either of the blue armies alone, but together the blue armies are larger than the white army. If either blue army attacks by itself, it will be defeated, but if the two blue armies attack simultaneously, they will be victor ...
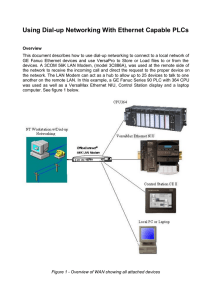
Using Dial-up Networking With Ethernet Capable PLCs
... installed on the PC you will need to install it now before proceeding. Once installed, create a new entry in the phone book using your PC’s modem as the dial-out device. Specify a user name and password for authentication. Dial-up server type is PPP, network protocol is TCP/IP. Next, configure the L ...
... installed on the PC you will need to install it now before proceeding. Once installed, create a new entry in the phone book using your PC’s modem as the dial-out device. Specify a user name and password for authentication. Dial-up server type is PPP, network protocol is TCP/IP. Next, configure the L ...
Information Technology and Protection Considerations for E
... In Wi-Fi networking, the wireless access point or router typically broadcasts the network name (SSID) over the air at regular intervals. This feature was designed for businesses and mobile hotspots where Wi-Fi clients may roam in and out of range. In the home, this roaming feature is unnecessary, an ...
... In Wi-Fi networking, the wireless access point or router typically broadcasts the network name (SSID) over the air at regular intervals. This feature was designed for businesses and mobile hotspots where Wi-Fi clients may roam in and out of range. In the home, this roaming feature is unnecessary, an ...