Overlay Networks and Tunneling Reading: 4.5, 9.4 Mike Freedman
... – AcVng as intermediate nodes that forward traffic – Providing a service, such as access to files ...
... – AcVng as intermediate nodes that forward traffic – Providing a service, such as access to files ...
Chp. 4, Part II - comp
... • If any fragments do not arrive within a certain time, other received fragments in the datagram will be discarded. • Fragmentation could occur multiple times to an IP datagram. ...
... • If any fragments do not arrive within a certain time, other received fragments in the datagram will be discarded. • Fragmentation could occur multiple times to an IP datagram. ...
Chapter 1 - Introduction
... telephone systems – A physical pair of wires between two parties to form a dedicated circuit ...
... telephone systems – A physical pair of wires between two parties to form a dedicated circuit ...
Security as an App and Security as a Service: New Killer
... • Clouds are large, complicated, and dynamic • How do tenants deploy security devices/ func?ons? • Tenant can use some pre-‐installed fixed-‐loca?on security devices – Not able to keep up with the high dynam ...
... • Clouds are large, complicated, and dynamic • How do tenants deploy security devices/ func?ons? • Tenant can use some pre-‐installed fixed-‐loca?on security devices – Not able to keep up with the high dynam ...
Chapter 6 slides, Computer Networking, 3rd edition
... Mobility: Vocabulary home network: permanent “home” of mobile (e.g., 128.119.40/24) ...
... Mobility: Vocabulary home network: permanent “home” of mobile (e.g., 128.119.40/24) ...
Blueprint For Security Chapter 6
... Benchmark and monitor the status of key system files and detect when intruder creates, modifies, or deletes files Most HIDPSs work on the principle of configuration or change management Advantage over NIDPS: can usually be installed so that it can access encrypted information when traveling ov ...
... Benchmark and monitor the status of key system files and detect when intruder creates, modifies, or deletes files Most HIDPSs work on the principle of configuration or change management Advantage over NIDPS: can usually be installed so that it can access encrypted information when traveling ov ...
UNIT 3.ppt - E
... on top of any data-link layer technology (Ethernet, Fast Ethernet, ATM etc.). All these technologies can handle a different packet length. The network layer must be able to fragment transport layer PDUs into smaller units so that they can be transferred over various data-link layer technologies. ...
... on top of any data-link layer technology (Ethernet, Fast Ethernet, ATM etc.). All these technologies can handle a different packet length. The network layer must be able to fragment transport layer PDUs into smaller units so that they can be transferred over various data-link layer technologies. ...
Dedicated and Distributed Vulnerability Management
... more use to identify which subnets are always lagging behind in patches or have the most vulnerabilities. Later we will discuss correlation with intrusion detection systems. Some organizations have drawn parallels between poor security and the number of intrusions (which should be obvious), but they ...
... more use to identify which subnets are always lagging behind in patches or have the most vulnerabilities. Later we will discuss correlation with intrusion detection systems. Some organizations have drawn parallels between poor security and the number of intrusions (which should be obvious), but they ...
Chapter 37 Network Security
... document is encrypted using sender’s private key. Recipient can verify that document has not been tampered by using sender’s public key to recover the media digest and verifying that this value is the same as the one-way hash value calculated. ...
... document is encrypted using sender’s private key. Recipient can verify that document has not been tampered by using sender’s public key to recover the media digest and verifying that this value is the same as the one-way hash value calculated. ...
Interconnection Networks Enable Fine-Grain Dynamic
... task does not need to know where it is situated in the network and whether the tasks it communicates with are running in hardware or software. The RT-OS adapts the routing tables after an IP-block reconfiguration. Therefore, there is no need for complex run-time circuit re-routing as required in pre ...
... task does not need to know where it is situated in the network and whether the tasks it communicates with are running in hardware or software. The RT-OS adapts the routing tables after an IP-block reconfiguration. Therefore, there is no need for complex run-time circuit re-routing as required in pre ...
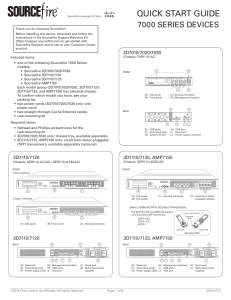
http://www.cisco.com/c/dam/en/us/td/docs/security/sourcefire/3d-system/53/quick-start-guides/QSG-3D7xxx-v53-3-20140311.pdf
... is connected to your trusted management network and the various network segments you want to monitor. In a simple deployment scenario, you connect the management interface on your device to your trusted management network using an Ethernet cable, then connect the sensing interfaces to the network se ...
... is connected to your trusted management network and the various network segments you want to monitor. In a simple deployment scenario, you connect the management interface on your device to your trusted management network using an Ethernet cable, then connect the sensing interfaces to the network se ...
PPT - ME Kabay
... Intelligence: can be addressed Requires protocol agreement Montreal Can select alternate routes Bridges becoming smarter – now called brouters ...
... Intelligence: can be addressed Requires protocol agreement Montreal Can select alternate routes Bridges becoming smarter – now called brouters ...
Network Layer - e-learning website
... 3. Examine all tentative nodes (not just adjacent nodes) and mark the node with the smallest labeled value as permanent. This node becomes the new working node. Reconstruct the path backwards from sink to source. Computer Networks: Routing ...
... 3. Examine all tentative nodes (not just adjacent nodes) and mark the node with the smallest labeled value as permanent. This node becomes the new working node. Reconstruct the path backwards from sink to source. Computer Networks: Routing ...
Aalborg Universitet Time Calculus
... and protocols currently used. Ethernet is currently widely used in a broad range of applications, however in safety-critical networks its applicability is still under question. As in-car networks are used for communication of critical date, e.g. wheel sensor information, there is a need of verifying ...
... and protocols currently used. Ethernet is currently widely used in a broad range of applications, however in safety-critical networks its applicability is still under question. As in-car networks are used for communication of critical date, e.g. wheel sensor information, there is a need of verifying ...
ppt - NOISE
... • Reliable Delivery: Guarantee to deliver the frame to the other end of the link without error. • Flow Control: The link layer can provide mechanisms to avoid overflowing the buffer • Error Correction: Determining where errors have occurred and then correcting those errors. ...
... • Reliable Delivery: Guarantee to deliver the frame to the other end of the link without error. • Flow Control: The link layer can provide mechanisms to avoid overflowing the buffer • Error Correction: Determining where errors have occurred and then correcting those errors. ...
Annex 1D Equipment to Trade-In
... 3.1 Ports Line card shall be based either on RJ45, SFP+, QSFP, QSFP28/CPAK/CFP4 form factors for their respective port speed. 3.2 The respective line cards shall also support 1GBase-SX, 1GBaseLX, 10GBase-SR, 10GBase-LR, 10GBase-ER, 40GBase-LR4, 100GBase-LR4, DWDM and Bi-Directional optics. PC is to ...
... 3.1 Ports Line card shall be based either on RJ45, SFP+, QSFP, QSFP28/CPAK/CFP4 form factors for their respective port speed. 3.2 The respective line cards shall also support 1GBase-SX, 1GBaseLX, 10GBase-SR, 10GBase-LR, 10GBase-ER, 40GBase-LR4, 100GBase-LR4, DWDM and Bi-Directional optics. PC is to ...
Innovation in Backhaul Antenna Technology to
... network traffic lost and gained could be determined explicitly from the data. Alternatively, the microwave backhaul network could be redesigned with Sentinel, allowing the C/I benefit to enable the use of smaller antennas. To get the same or better link throughput as Class 3, the Class 4 antennas co ...
... network traffic lost and gained could be determined explicitly from the data. Alternatively, the microwave backhaul network could be redesigned with Sentinel, allowing the C/I benefit to enable the use of smaller antennas. To get the same or better link throughput as Class 3, the Class 4 antennas co ...
Data Link Layer
... • Transfer data from the network layer of one machine to the network layer of another machine. • Convert the raw bit stream of the physical layer into groups of bits (“frames”). • Perform flow control between sender and receiver. Network ...
... • Transfer data from the network layer of one machine to the network layer of another machine. • Convert the raw bit stream of the physical layer into groups of bits (“frames”). • Perform flow control between sender and receiver. Network ...
DumpsReview
... C. Create a filter and apply it to an interface. D. Create a filter and apply it to the VPN policy. Answer: AD NO.4 Which three can a proxy-based firewall do? (Choose three.) A. hide addresses on the internal network B. track each connection across all interfaces C. inspect encrypted traffic at the ...
... C. Create a filter and apply it to an interface. D. Create a filter and apply it to the VPN policy. Answer: AD NO.4 Which three can a proxy-based firewall do? (Choose three.) A. hide addresses on the internal network B. track each connection across all interfaces C. inspect encrypted traffic at the ...
VANET Simulation in Diffrent Indian City Scenario
... implementing such a system in real world, most research in VANET relies on simulations for evaluation. This paper presents a comparative test of various mobility scenarios of Vehicular Ad-hoc Network in three well-known Indian Metros. The AODV routing protocol have been used for the simulation. In o ...
... implementing such a system in real world, most research in VANET relies on simulations for evaluation. This paper presents a comparative test of various mobility scenarios of Vehicular Ad-hoc Network in three well-known Indian Metros. The AODV routing protocol have been used for the simulation. In o ...
TW-522 802.11ac Dual Radio Wallplate Specification Sheet
... provide high-speed Wi-Fi services and more in the largest campus-style environments quickly, easily and cost-effectively with the TW-522. An integral component in the Zebra T5 system, the TW-522 delivers high performance Wi-Fi access over your existing in-room telephone line — no CAT5 cabling requir ...
... provide high-speed Wi-Fi services and more in the largest campus-style environments quickly, easily and cost-effectively with the TW-522. An integral component in the Zebra T5 system, the TW-522 delivers high performance Wi-Fi access over your existing in-room telephone line — no CAT5 cabling requir ...
Brochure
... airPoint XO2 provides traffic statistics. This helps the WISP to observe the behavior of network devices, traffic load fluctuations and other events, making it much easier to troubleshoot any problems, which might occur. The information available helps the WISP to optimize bandwidth utilization. WIS ...
... airPoint XO2 provides traffic statistics. This helps the WISP to observe the behavior of network devices, traffic load fluctuations and other events, making it much easier to troubleshoot any problems, which might occur. The information available helps the WISP to optimize bandwidth utilization. WIS ...