Vandelay Industries 1 Overview
... another individual, either deliberately or through failure to secure its access, is a violation of this policy. 3.2.2 You must maintain systemlevel and userlevel passwords in accordance with the Password Policy. 3.2.3 You are responsible for ensuring that proprietary information remains within ...
... another individual, either deliberately or through failure to secure its access, is a violation of this policy. 3.2.2 You must maintain systemlevel and userlevel passwords in accordance with the Password Policy. 3.2.3 You are responsible for ensuring that proprietary information remains within ...
full text pdf
... This Section explains the learning phase of the proposed neural network. In this phase, the neurons and connections are organized and trained in an unsupervised way according to the input text. At first, the input text is split into sentences and input to the neural network sentence by sentence. Bec ...
... This Section explains the learning phase of the proposed neural network. In this phase, the neurons and connections are organized and trained in an unsupervised way according to the input text. At first, the input text is split into sentences and input to the neural network sentence by sentence. Bec ...
IP in LANs
... DHCPREQUEST - Client broadcast to servers requesting offered parameters from one server and implicitly declining offers from all others. ...
... DHCPREQUEST - Client broadcast to servers requesting offered parameters from one server and implicitly declining offers from all others. ...
PPT
... • Very few LANs have close to 64K hosts • For electrical/LAN limitations, performance or administrative reasons ...
... • Very few LANs have close to 64K hosts • For electrical/LAN limitations, performance or administrative reasons ...
Wireless Electronic Notice Board
... ZigBee is targeted at applications that require a low data rate, long battery life, and secure networking. ZigBee has a defined rate of 250 kbit/s, best suited for periodic or intermittent data or a single signal transmission from a sensor or input device. Applications include wireless light switche ...
... ZigBee is targeted at applications that require a low data rate, long battery life, and secure networking. ZigBee has a defined rate of 250 kbit/s, best suited for periodic or intermittent data or a single signal transmission from a sensor or input device. Applications include wireless light switche ...
User Guide
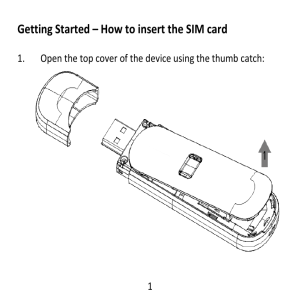
... antenna to connect to the mobile network. To get the best performance from your device do not cover or shield the device in any way as this will lead to increased output power. Always leave a clear space around the device to allow the transmit and receive signals to propagate. It is not intended to ...
... antenna to connect to the mobile network. To get the best performance from your device do not cover or shield the device in any way as this will lead to increased output power. Always leave a clear space around the device to allow the transmit and receive signals to propagate. It is not intended to ...
Network Routing Algorithms
... • With Distance Vector Routing reverse path forwarding is used. – When a router receives a packet for a multicast group for which it has no subscribers (hosts or other routers), the router sends a PRUNE message to the source router. ...
... • With Distance Vector Routing reverse path forwarding is used. – When a router receives a packet for a multicast group for which it has no subscribers (hosts or other routers), the router sends a PRUNE message to the source router. ...
ATM: Architecture
... reassembly of larger data sets into the ATM cells and to provide service specific mechanisms for the transport of different types of data. ...
... reassembly of larger data sets into the ATM cells and to provide service specific mechanisms for the transport of different types of data. ...
Network Routing Algorithms
... • With Distance Vector Routing reverse path forwarding is used. – When a router receives a packet for a multicast group for which it has no subscribers (hosts or other routers), the router sends a PRUNE message to the source router. ...
... • With Distance Vector Routing reverse path forwarding is used. – When a router receives a packet for a multicast group for which it has no subscribers (hosts or other routers), the router sends a PRUNE message to the source router. ...
WISPCON-Keeping It Up 2 - Home
... • 10Mbit ethernet’s default cost is 10 • Traffic from WPOP1 to WPOP2 will take the wireless PTP link if it’s available, else it will use T1s • Traffic from WPOP1 to Internet goes via the local T1, else via the wireless PTP link to WPOP2 and then via WPOP2’s T1 ...
... • 10Mbit ethernet’s default cost is 10 • Traffic from WPOP1 to WPOP2 will take the wireless PTP link if it’s available, else it will use T1s • Traffic from WPOP1 to Internet goes via the local T1, else via the wireless PTP link to WPOP2 and then via WPOP2’s T1 ...
Providing Guaranteed Services without Per Flow Management
... • If all flows were sending at their reserved rates, computing Re is trivial; just measure traffic throughput • Problem: what if flows do not send at their reserved rates? • Solution: Associate with each packet a virtual length - virtual length = r * (time now - transmit time of previous packet) • U ...
... • If all flows were sending at their reserved rates, computing Re is trivial; just measure traffic throughput • Problem: what if flows do not send at their reserved rates? • Solution: Associate with each packet a virtual length - virtual length = r * (time now - transmit time of previous packet) • U ...
2 - Networking
... node to node, and each node has a designated time at which it can remove the token and either add a message or take a message from it. ...
... node to node, and each node has a designated time at which it can remove the token and either add a message or take a message from it. ...
Introduction
... Each router builds an identical link-state database Allows router to build shortest path tree with router as root OSPF typically converges faster than RIP when there is a failure in the network ...
... Each router builds an identical link-state database Allows router to build shortest path tree with router as root OSPF typically converges faster than RIP when there is a failure in the network ...
20060420_OnLinkScalability_rev1
... • For neighboring routers, reachability means that packets sent by a node's IP layer are delivered to the router's IP layer, and the router is indeed forwarding packets (i.e., it is configured as a router, not a host) • For hosts, reachability means that packets sent by a node's IP layer are delive ...
... • For neighboring routers, reachability means that packets sent by a node's IP layer are delivered to the router's IP layer, and the router is indeed forwarding packets (i.e., it is configured as a router, not a host) • For hosts, reachability means that packets sent by a node's IP layer are delive ...
Reflections on the Development of A/P Nets
... – Arrange hash tables so these are handled in one or two accesses ...
... – Arrange hash tables so these are handled in one or two accesses ...
Guide to Firewalls and Network Security with Intrusion
... routing or IP forwarding Take out hardware features you won’t use Do not disable any dependency services Each time a service is stopped, test the system Document every single change you make ...
... routing or IP forwarding Take out hardware features you won’t use Do not disable any dependency services Each time a service is stopped, test the system Document every single change you make ...
Part II
... • Multiple routers on same LAN • Master performs packet routing • Fail-over by migration of ’virtual’ MAC address Virtual Router NE 1 HUB 1 ...
... • Multiple routers on same LAN • Master performs packet routing • Fail-over by migration of ’virtual’ MAC address Virtual Router NE 1 HUB 1 ...
9781305105430_PPT_ch03
... brought around from the last device back to the first device to form a ring ...
... brought around from the last device back to the first device to form a ring ...
non-cooperative forwarding in ad-hoc networks
... aggressive mobiles, which is in the spirit of a well established design approach for promoting cooperation in Ad-hoc networks, carried on in many previous works [3], [7]. In all these references, the well known “TIT-FOR-TAT” (TFT) strategy was proposed. This is a strategy in which when a misbehaving ...
... aggressive mobiles, which is in the spirit of a well established design approach for promoting cooperation in Ad-hoc networks, carried on in many previous works [3], [7]. In all these references, the well known “TIT-FOR-TAT” (TFT) strategy was proposed. This is a strategy in which when a misbehaving ...
Layer 2 Data Link Frame
... What does a router do with a packet received from one network and destined for another network? 1. Decapsulates the Layer 3 packet by removing the Layer 2 frame header and trailer 2. Examines the destination IP address of the IP packet to find the best path in the ...
... What does a router do with a packet received from one network and destined for another network? 1. Decapsulates the Layer 3 packet by removing the Layer 2 frame header and trailer 2. Examines the destination IP address of the IP packet to find the best path in the ...
Cisco TrustSec 3.0 How-To Guide: Introduction to MACSec and NDAC Guide
... from end to end. However, QoS cannot be provided when a packet’s contents are not visible: It wasn’t possible to ensure security while encrypting both good and bad traffic across the network. The way to provide wireless equivalency - and a viable alternative to end-to-end IPSec - was to layer on the ...
... from end to end. However, QoS cannot be provided when a packet’s contents are not visible: It wasn’t possible to ensure security while encrypting both good and bad traffic across the network. The way to provide wireless equivalency - and a viable alternative to end-to-end IPSec - was to layer on the ...
TDC 463-98-501/502, Summer II 2002 2-1
... Unlike Ethernet, there is a fixed limit on how long a station must wait to transmit frame. b) Eight data priority levels ensure that important data get sent first. ...
... Unlike Ethernet, there is a fixed limit on how long a station must wait to transmit frame. b) Eight data priority levels ensure that important data get sent first. ...
An Overview on Ad Hoc Networks
... But the reactive schemes have smaller Route discovery overheads, because they don’t have to save all possible routes in the networks. Destination Sequenced Distance Vector (DSDV) is an example of proactive scheme. Ad Hoc On Demand Distance Vector (AODV) and Dynamic Source Routing are examples of rea ...
... But the reactive schemes have smaller Route discovery overheads, because they don’t have to save all possible routes in the networks. Destination Sequenced Distance Vector (DSDV) is an example of proactive scheme. Ad Hoc On Demand Distance Vector (AODV) and Dynamic Source Routing are examples of rea ...