Network Architectures - Computing Sciences
... • Firewall: HW device or SW program that inspects packets going into or out of a network or computer, and then discards/forwards them based on rules – Protects against outside attempts to access unauthorized resources, and against malicious network packets intended to disable or cripple a corporate ...
... • Firewall: HW device or SW program that inspects packets going into or out of a network or computer, and then discards/forwards them based on rules – Protects against outside attempts to access unauthorized resources, and against malicious network packets intended to disable or cripple a corporate ...
Cyber - Security and Investigations Ingrid Beierly August 18, 2008
... Vendor - Supplied Default Settings and Passwords Mitigation Strategy • Change default or blank settings and passwords prior to deployment. This includes operating systems, firewall devices, routers, wireless access points, etc. ...
... Vendor - Supplied Default Settings and Passwords Mitigation Strategy • Change default or blank settings and passwords prior to deployment. This includes operating systems, firewall devices, routers, wireless access points, etc. ...
Cutting Edge VoIP Security Issues Color
... Voice SPAM refers to bulk, automatically generated, unsolicited phone calls Similar to telemarketing, but occurring at the frequency of email SPAM Not an issue yet, but will become prevalent when: ...
... Voice SPAM refers to bulk, automatically generated, unsolicited phone calls Similar to telemarketing, but occurring at the frequency of email SPAM Not an issue yet, but will become prevalent when: ...
XML: Part - RoboSoft
... • Prior to VPNs, organizations were forced to lease expensive data connections from private carriers so employees could remotely connect to the organization’s network ...
... • Prior to VPNs, organizations were forced to lease expensive data connections from private carriers so employees could remotely connect to the organization’s network ...
Glossary terms section 1 - Department of Learning Technologies
... extranet is a private network utilizing Internet protocols that can be shared with interested parties such as suppliers or customers. Facebook – Also see MySpace. A social networking site where users can create web pages with personal information and connect and communicate with other users. Freewar ...
... extranet is a private network utilizing Internet protocols that can be shared with interested parties such as suppliers or customers. Facebook – Also see MySpace. A social networking site where users can create web pages with personal information and connect and communicate with other users. Freewar ...
module 3 Cyberpatriot Powerpoint
... • Information gathering: assessing targets to plan attacks • Denial of Service (DoS): degrading or preventing communication through or across specific network(s) • Other exploitation/interception: – Disinformation: fooling users or network components/services – Man-in-the-middle: getting between com ...
... • Information gathering: assessing targets to plan attacks • Denial of Service (DoS): degrading or preventing communication through or across specific network(s) • Other exploitation/interception: – Disinformation: fooling users or network components/services – Man-in-the-middle: getting between com ...
Welcome (and overview of NSF CISE)
... Research in smart and autonomous systems lies at interstices of NRI and CPS NRI: “co-robots” – robots that work alongside, cooperatively with people CPS: deeply integrating computation, communication, control into physical systems ...
... Research in smart and autonomous systems lies at interstices of NRI and CPS NRI: “co-robots” – robots that work alongside, cooperatively with people CPS: deeply integrating computation, communication, control into physical systems ...
Linux OS Concepts
... or from a private network. Firewalls can be implemented in both hardware and software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. All messages entering or leaving the ...
... or from a private network. Firewalls can be implemented in both hardware and software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. All messages entering or leaving the ...
HP Enterprise and IoT Connectivity
... services, if the originating devices and transportation mechanisms aren’t trusted. Doing so threatens all of the devices, processes, applications, and business decisions built on the untrusted data. The solution is to build trust where it doesn’t exist today, and that is the objective of HP Enterpri ...
... services, if the originating devices and transportation mechanisms aren’t trusted. Doing so threatens all of the devices, processes, applications, and business decisions built on the untrusted data. The solution is to build trust where it doesn’t exist today, and that is the objective of HP Enterpri ...
Document
... network planning: managing the noise floor, cell breathing. Books Recommended: 1. Wireless Communications ...
... network planning: managing the noise floor, cell breathing. Books Recommended: 1. Wireless Communications ...
slides
... WAN: wide area network (long haul network) Most commonly, we’re interested in the seamless integration of all these levels (as in the Internet). Note: Different levels use very different technologies. ...
... WAN: wide area network (long haul network) Most commonly, we’re interested in the seamless integration of all these levels (as in the Internet). Note: Different levels use very different technologies. ...
Guidelines at a Glance - American Bankers Association
... systems to authorized persons only. 2. Access restrictions at physical locations, such as buildings and computer facilities, to permit access to authorized persons only. 3. Encryption of electronically transmitted and stored customer data. 4. Procedures to ensure that systems modifications are consi ...
... systems to authorized persons only. 2. Access restrictions at physical locations, such as buildings and computer facilities, to permit access to authorized persons only. 3. Encryption of electronically transmitted and stored customer data. 4. Procedures to ensure that systems modifications are consi ...
Making the Most Out of Substation IEDs in a Secure, NERC Compliant Manner
... defined as being cyber-assets that are directly or indirectly accessible via routable protocols (networks) or via dial-up mechanisms (modems). Many, if not most, of the new IEDs now being installed must be considered critical cyber-assets. CIP-003-1 Security Management Controls – Utilities must have ...
... defined as being cyber-assets that are directly or indirectly accessible via routable protocols (networks) or via dial-up mechanisms (modems). Many, if not most, of the new IEDs now being installed must be considered critical cyber-assets. CIP-003-1 Security Management Controls – Utilities must have ...
www.cs.hofstra.edu
... 1. Try default passwords used with standard accounts shipped with the system 2. Exhaustive try of all short passwords 3. Try words in system’s dictionary or list of likely passwords (hacker bulletin boards) 4. Collect information about users (full names, names of spouses and children, pictures and b ...
... 1. Try default passwords used with standard accounts shipped with the system 2. Exhaustive try of all short passwords 3. Try words in system’s dictionary or list of likely passwords (hacker bulletin boards) 4. Collect information about users (full names, names of spouses and children, pictures and b ...
Information Technology A25590 - Beaufort County Community
... Information Technology A25590 A25590 The Information Systems curriculum is designed to prepare graduates for employment with organizations that use computers to process, manage, and communicate information. This is a flexible program, designed to meet community information system’s needs. Course wor ...
... Information Technology A25590 A25590 The Information Systems curriculum is designed to prepare graduates for employment with organizations that use computers to process, manage, and communicate information. This is a flexible program, designed to meet community information system’s needs. Course wor ...
PowerPoint Presentation - Securing a Wireless 802.11b Network
... Access. Choose Password and enter a password between 8 and 63 characters. Wireless client computers using WPA or WPA2 can join the network. ...
... Access. Choose Password and enter a password between 8 and 63 characters. Wireless client computers using WPA or WPA2 can join the network. ...
Tcp/ip
... • The highest level is closer to the user – processes are usually handled by either the operating system or application software • The lower levels are handled using a combination of hardware and software including the physical or wireless connections between devices • It’s called a stack because of ...
... • The highest level is closer to the user – processes are usually handled by either the operating system or application software • The lower levels are handled using a combination of hardware and software including the physical or wireless connections between devices • It’s called a stack because of ...
11 Secure electronic communication
... Preventative system maintenance undertaken regularly Software updates and patches applied as soon as they become available Secure messaging system (involving encryption) used for the electronic transfer of confidential information Safe and secure use of email, internet and the practice website polic ...
... Preventative system maintenance undertaken regularly Software updates and patches applied as soon as they become available Secure messaging system (involving encryption) used for the electronic transfer of confidential information Safe and secure use of email, internet and the practice website polic ...
ICA An acronym for Citrix`s Independent
... (e.g., name, address, social security number or other identifying number or code, telephone number, email address, etc.) or (ii) by which an agency intends to identify specific individuals in conjunction with other data elements, i.e., indirect identification. (These data elements may include a comb ...
... (e.g., name, address, social security number or other identifying number or code, telephone number, email address, etc.) or (ii) by which an agency intends to identify specific individuals in conjunction with other data elements, i.e., indirect identification. (These data elements may include a comb ...
Using two ISPs for redundant Internet connections
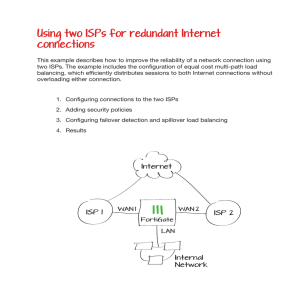
... Using two ISPs for redundant Internet connections This example describes how to improve the reliability of a network connection using two ISPs. The example includes the configuration of equal cost multi-path load balancing, which efficiently distributes sessions to both Internet connections without ...
... Using two ISPs for redundant Internet connections This example describes how to improve the reliability of a network connection using two ISPs. The example includes the configuration of equal cost multi-path load balancing, which efficiently distributes sessions to both Internet connections without ...
TCP/IP
... • The Open Systems Interconnection (OSI) model is a reference model for networked data communications • OSI describes 7 layers – Application, Presentation, Session, Transport, Network, Data Link, Physical – Data is processed sequentially from the user interfaces at the Application layer to the trans ...
... • The Open Systems Interconnection (OSI) model is a reference model for networked data communications • OSI describes 7 layers – Application, Presentation, Session, Transport, Network, Data Link, Physical – Data is processed sequentially from the user interfaces at the Application layer to the trans ...
ACCESS CONTROL OPTIONS FOR WIRED NETWORKS
... profiling efforts have been solely focused on wireless access. This has led to wired access controls being overshadowed or not configured at all, leading to security gaps in many organizations. And as IT Security experts are well aware, networks are only as strong as their weakest link. As the moder ...
... profiling efforts have been solely focused on wireless access. This has led to wired access controls being overshadowed or not configured at all, leading to security gaps in many organizations. And as IT Security experts are well aware, networks are only as strong as their weakest link. As the moder ...
GW2412271231
... can be handled: first by selecting a hash function that is more and more collision resistant, second by putting the processing in an environment to minimize the chance of collisions and third by resolving when the collision really takes place. The choice of a hash function, its implementation and it ...
... can be handled: first by selecting a hash function that is more and more collision resistant, second by putting the processing in an environment to minimize the chance of collisions and third by resolving when the collision really takes place. The choice of a hash function, its implementation and it ...
Slide 1
... of isn’t the operating system depends on used very frequently, might not need system ifofreasonable the OS could providing parts of the SK … Few OS’s come with part the TCB at definition all, ifbiometric the TCB By any of theis whether or not the security architecture to be continuously memory resid ...
... of isn’t the operating system depends on used very frequently, might not need system ifofreasonable the OS could providing parts of the SK … Few OS’s come with part the TCB at definition all, ifbiometric the TCB By any of theis whether or not the security architecture to be continuously memory resid ...
CS244a: An Introduction to Computer Networks
... Ensure packets received from Internet belong to an ...
... Ensure packets received from Internet belong to an ...