IPsec VPNs with Digital Certificates: The Most Secure and Scalable
... of shared networks, including the public Internet, privately managed internets, and commercial service provider backbones. The current excitement over VPNs stems from their ability to solve corporate communication problems while also providing significant cost savings. Interesting applications inclu ...
... of shared networks, including the public Internet, privately managed internets, and commercial service provider backbones. The current excitement over VPNs stems from their ability to solve corporate communication problems while also providing significant cost savings. Interesting applications inclu ...
Effectiveness of Proactive Reset for Mitigating
... • Their autonomy and interconnectedness increases their susceptibility to cyber attack as well as the magnitude of damage an attack could cause • Self-propagating malware can exploit vulnerabilities in hardware, software, or communication protocols to spread through and gain control over such networ ...
... • Their autonomy and interconnectedness increases their susceptibility to cyber attack as well as the magnitude of damage an attack could cause • Self-propagating malware can exploit vulnerabilities in hardware, software, or communication protocols to spread through and gain control over such networ ...
ppt
... 1/3 of network bandwidth consumed by BitTorrent Students: what are BitTorrent, Gnutella, Kazaa, … used for? ...
... 1/3 of network bandwidth consumed by BitTorrent Students: what are BitTorrent, Gnutella, Kazaa, … used for? ...
Not another Perimeter Presentation - ISSA
... Block spam, viruses, and probes Preserve bandwidth, for corporate business Preserve access to unauthenticated but authorized information (e.g. public web site) ...
... Block spam, viruses, and probes Preserve bandwidth, for corporate business Preserve access to unauthenticated but authorized information (e.g. public web site) ...
Information Fusion
... Service). • Note: Fusion is possible only if data can be correlated at both the sensor and intermediary nodes. ...
... Service). • Note: Fusion is possible only if data can be correlated at both the sensor and intermediary nodes. ...
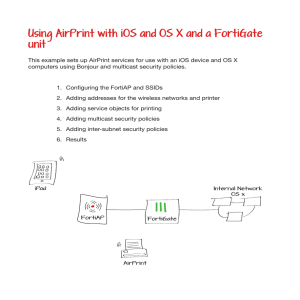
Using AirPrint with iOS and OS X and a FortiGate unit
... from WLAN1 and WLAN2 for iOS devices. For the first policy, set Incoming Interface to WLAN1, Source Address to the SSID1 IP, Outgoing Interface to WLAN2, and Destination Address to Bonjour. For the second policy, set Incoming Interface to WLAN2, Source Address to the SSID2 IP, Outgoing Interface to ...
... from WLAN1 and WLAN2 for iOS devices. For the first policy, set Incoming Interface to WLAN1, Source Address to the SSID1 IP, Outgoing Interface to WLAN2, and Destination Address to Bonjour. For the second policy, set Incoming Interface to WLAN2, Source Address to the SSID2 IP, Outgoing Interface to ...
Prime III: Where Usable Security and Electronic Voting Meet
... Learning Technologies, User Interfaces (Usability), Ethnocomputing (Culturally Relevant Computing) and Databases. He is also a Senior Member of the IEEE Computer Society, he serves on the IEEE Board of Governors and he is the Editor for the new Broadening Participation in Computing Series in Compute ...
... Learning Technologies, User Interfaces (Usability), Ethnocomputing (Culturally Relevant Computing) and Databases. He is also a Senior Member of the IEEE Computer Society, he serves on the IEEE Board of Governors and he is the Editor for the new Broadening Participation in Computing Series in Compute ...
University of Split University Department of Professional
... ICT stands for Information and Communication Technologies. ICT refers to technologies that provide access to information through telecommunications. It is similar to Information Technology (IT), but focuses primarily on communication technologies. This includes the Internet, wireless networks, cell ...
... ICT stands for Information and Communication Technologies. ICT refers to technologies that provide access to information through telecommunications. It is similar to Information Technology (IT), but focuses primarily on communication technologies. This includes the Internet, wireless networks, cell ...
Types of Management Information Systems
... – formal agreement that commits two or more companies to exchange or share their resources in order to produce and market a product ...
... – formal agreement that commits two or more companies to exchange or share their resources in order to produce and market a product ...
WRT600N Datasheet
... the wireless link are Wireless-N, the router can increase the throughput even more by using twice as much radio band, yielding speeds up to 12 times as fast as standard Wireless-G. But unlike other speed-enhanced technologies, Wireless-N can dynamically enable this double-speed mode for Wireless-N d ...
... the wireless link are Wireless-N, the router can increase the throughput even more by using twice as much radio band, yielding speeds up to 12 times as fast as standard Wireless-G. But unlike other speed-enhanced technologies, Wireless-N can dynamically enable this double-speed mode for Wireless-N d ...
Chapter 12 - Cisco Networking Academy
... • Digital certificates can be used to associate a user’s identity to a public key • An entity that issues digital certificates for others is known as a Certificate Authority (CA) • Types of certificates – Personal, server, and software publisher certificates ...
... • Digital certificates can be used to associate a user’s identity to a public key • An entity that issues digital certificates for others is known as a Certificate Authority (CA) • Types of certificates – Personal, server, and software publisher certificates ...
Web Security
... • part of javax.net • SSL (and thus HTTPS) permits encrypted traffic to be exchanged between the client and server. – After an SSL client initiates a conversation with an SSL server, the server sends an X.509 certificate back to the client for authentication. The client then checks the validity of t ...
... • part of javax.net • SSL (and thus HTTPS) permits encrypted traffic to be exchanged between the client and server. – After an SSL client initiates a conversation with an SSL server, the server sends an X.509 certificate back to the client for authentication. The client then checks the validity of t ...
GULP: A Unified Logging Architecture for Authentication Data ABSTRACT
... then be transferred and stored in a relational database (MySQL, in our case) [10]. For our project, we used logs from UNIX timeshare hosts (CUNIX and PINEX), web application log-in servers (WIND), secure web servers (WWWS), and webmail (CubMail), all of which we have described above. We chose the ti ...
... then be transferred and stored in a relational database (MySQL, in our case) [10]. For our project, we used logs from UNIX timeshare hosts (CUNIX and PINEX), web application log-in servers (WIND), secure web servers (WWWS), and webmail (CubMail), all of which we have described above. We chose the ti ...
Web Security
... • part of javax.net • SSL (and thus HTTPS) permits encrypted traffic to be exchanged between the client and server. – After an SSL client initiates a conversation with an SSL server, the server sends an X.509 certificate back to the client for authentication. The client then checks the validity of t ...
... • part of javax.net • SSL (and thus HTTPS) permits encrypted traffic to be exchanged between the client and server. – After an SSL client initiates a conversation with an SSL server, the server sends an X.509 certificate back to the client for authentication. The client then checks the validity of t ...
IT 141: Information Systems I - Tonga Institute of Higher Education
... Protocols for computers decide important ...
... Protocols for computers decide important ...
Protocol Overview
... much of the session and presentation layers using Distinguished Names (DN) Category: Authentication ...
... much of the session and presentation layers using Distinguished Names (DN) Category: Authentication ...
Mobile Health Communication Infrastructure
... • Performance, coverage, reliability, security WP2 system requirements needed • Derived from WP1 WP3 communication infrastructure requirements • Derived from WP1 and WP2 WP3 preliminary testing • ‘testdrive’ with plain IP E2E communication ...
... • Performance, coverage, reliability, security WP2 system requirements needed • Derived from WP1 WP3 communication infrastructure requirements • Derived from WP1 and WP2 WP3 preliminary testing • ‘testdrive’ with plain IP E2E communication ...
Chapter 01_02 - UniMAP Portal
... link on end-end path that constrains end-end throughput Introduction 1-12 ...
... link on end-end path that constrains end-end throughput Introduction 1-12 ...
Secure coprocessors - University of Pittsburgh
... versions to a network server Server may accept node’s configuration or confine node to restricted network that allows only updating node’s software Expected to become common in a few years ...
... versions to a network server Server may accept node’s configuration or confine node to restricted network that allows only updating node’s software Expected to become common in a few years ...
Lecture 3: Slides
... was introduced, with variable-length prefixes and aggregation of blocks [And2007] proposes an address structure where the subnet prefix is replaced with a self-certifying Autonomous Domain identifier (AD) and the suffix with a self-certifying Host Identifier (EID), adresses now being of form: AD:E ...
... was introduced, with variable-length prefixes and aggregation of blocks [And2007] proposes an address structure where the subnet prefix is replaced with a self-certifying Autonomous Domain identifier (AD) and the suffix with a self-certifying Host Identifier (EID), adresses now being of form: AD:E ...
CSIT560 Project Presentation
... multitude of information is obtained by analyzing networking parameters. ...
... multitude of information is obtained by analyzing networking parameters. ...
Issue - GiaSpace
... Recommendation: Disable or remove user accounts for users that have not logged in in 30 days. ...
... Recommendation: Disable or remove user accounts for users that have not logged in in 30 days. ...
Firewall Deployment for SCADA-PCN
... Unrestricted (but only authorized) access from the enterprise network to shared PCN/Enterprise servers Secured methods for authorized remote support of control system Secure connectivity for wireless devices Well defined rules outlining the type of traffic permitted Monitoring the traffic ...
... Unrestricted (but only authorized) access from the enterprise network to shared PCN/Enterprise servers Secured methods for authorized remote support of control system Secure connectivity for wireless devices Well defined rules outlining the type of traffic permitted Monitoring the traffic ...
NPTF - FINAL RATE SETTING
... Traffic volume/composition by immediate peers (attached commercial ISPs or R&E networks) Evaluate peering status - would it make sense to add/drop a particular peer? How much traffic would shift and in which direction Peer-to-peer, AS-to-AS traffic analysis Establish better peering and transit r ...
... Traffic volume/composition by immediate peers (attached commercial ISPs or R&E networks) Evaluate peering status - would it make sense to add/drop a particular peer? How much traffic would shift and in which direction Peer-to-peer, AS-to-AS traffic analysis Establish better peering and transit r ...