Usage of Wireless Network technologies
... knowledge base and storage area for everyone in customers business. They also provide users with easy access to McDonalds’ data, systems and email from their desktops. Because intranets are secure and easily accessible via the internet, this enables staff to do work from any location simply by using ...
... knowledge base and storage area for everyone in customers business. They also provide users with easy access to McDonalds’ data, systems and email from their desktops. Because intranets are secure and easily accessible via the internet, this enables staff to do work from any location simply by using ...
The Everyday ICT Glossary - UN
... significant value, or that has some technical maturity but still has relatively few users; also known as an "emerging technology." Current examples include artificial intelligence, biometrics, etags, grid computing and wearable computers. Adware: (ECOM) Advertising-supported software. A software pac ...
... significant value, or that has some technical maturity but still has relatively few users; also known as an "emerging technology." Current examples include artificial intelligence, biometrics, etags, grid computing and wearable computers. Adware: (ECOM) Advertising-supported software. A software pac ...
Using Udpcast to IP Multicast Data over Amateur
... audio and/or video data. Multicast Software for Amateur Packet Radio Networks As of July 2008, two software applications have been identified that were specifically developed to multicast data over amateur packet radio networks. They are RadioMirror and AltCast, and each are discussed in the followi ...
... audio and/or video data. Multicast Software for Amateur Packet Radio Networks As of July 2008, two software applications have been identified that were specifically developed to multicast data over amateur packet radio networks. They are RadioMirror and AltCast, and each are discussed in the followi ...
Access Control - FTP Directory Listing
... Multi-application gateway Web app firewall, including “deep” packet inspection” Web app access control Web services protection (for SOA) Automated learning of legitimate use patterns App layer Denial-of-Service protection Website cloaking: hiding from crawlers (but not Google...) ...
... Multi-application gateway Web app firewall, including “deep” packet inspection” Web app access control Web services protection (for SOA) Automated learning of legitimate use patterns App layer Denial-of-Service protection Website cloaking: hiding from crawlers (but not Google...) ...
CISCO Secure Intrusion Detection System
... externally. Adding host-based IDS further enhances protection from attack, especially from attacks that are generated from internal sources. ...
... externally. Adding host-based IDS further enhances protection from attack, especially from attacks that are generated from internal sources. ...
Voltage Enterprise Security for Big Data - HPE Security
... Security with Format-Preserving Encryption™ (FPE): Structured, semi-structured or unstructured data can be encrypted at source and protected throughout the data life-cycle, wherever it resides and however it is used. Protection travels with the data, eliminating security gaps in transmission into an ...
... Security with Format-Preserving Encryption™ (FPE): Structured, semi-structured or unstructured data can be encrypted at source and protected throughout the data life-cycle, wherever it resides and however it is used. Protection travels with the data, eliminating security gaps in transmission into an ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... unique security signature pattern maintained by respective wireless nodes using an encryption algorithm and this is made dynamic. The metrics includes latency, throughput, Scalability, Effects of data transfer operation on node processor and application data located in the processor Keywords: Wirele ...
... unique security signature pattern maintained by respective wireless nodes using an encryption algorithm and this is made dynamic. The metrics includes latency, throughput, Scalability, Effects of data transfer operation on node processor and application data located in the processor Keywords: Wirele ...
Red Hat enteRpRise Linux 6 seRveR: FeatuRes
... reduce the risk of privilege escalation. • New utilities and system libraries provide more control over process privileges for easily managing reduced capabilities. • Walk-up kiosks (as in banks, HR departments, etc.) gain additional protections to ensure secure public use. ...
... reduce the risk of privilege escalation. • New utilities and system libraries provide more control over process privileges for easily managing reduced capabilities. • Walk-up kiosks (as in banks, HR departments, etc.) gain additional protections to ensure secure public use. ...
5.Transport Layer
... Accessing TCP Services Access to the services provided by TCP can only be granted through transport service access points (TSAPs) known as ports. To use a port a socket must be created and bound to it. Each socket is addressed by a number made up of the machines IP address and a 16-bit port number l ...
... Accessing TCP Services Access to the services provided by TCP can only be granted through transport service access points (TSAPs) known as ports. To use a port a socket must be created and bound to it. Each socket is addressed by a number made up of the machines IP address and a 16-bit port number l ...
Cengage Learning 2013
... • State-of-the-art malicious code attack – Polymorphic (or multivector) worm – Uses several attack vectors to exploit variety of ...
... • State-of-the-art malicious code attack – Polymorphic (or multivector) worm – Uses several attack vectors to exploit variety of ...
0 - CIS Classes
... to choose from Geographical location is not an issue Shopping bots and other comparison shopping tools are available ...
... to choose from Geographical location is not an issue Shopping bots and other comparison shopping tools are available ...
Network security scanner and port scanner for vulnerability
... GFI LANguard ships with a complete and thorough vulnerability assessment database, which includes standards such as OVAL (2,000+ checks) and SANS Top 20. This database is regularly updated with information from BugTraq, SANS Corporation, OVAL, CVE and others. Through its auto-update system, GFI LANg ...
... GFI LANguard ships with a complete and thorough vulnerability assessment database, which includes standards such as OVAL (2,000+ checks) and SANS Top 20. This database is regularly updated with information from BugTraq, SANS Corporation, OVAL, CVE and others. Through its auto-update system, GFI LANg ...
What is SAN:Storage area network is a dedicated centrally managed
... banking, stock exchange, government record etc. This has generated an explosive demand for data storage and this demand can be addressed by deploying SAN. The activity to share a single large storage device across many server or application has made SAN an attractive option in today’s market place. ...
... banking, stock exchange, government record etc. This has generated an explosive demand for data storage and this demand can be addressed by deploying SAN. The activity to share a single large storage device across many server or application has made SAN an attractive option in today’s market place. ...
FAKEM RAT: Malware Disguised as Windows Messenger and
... The perpetrators of targeted attacks aim to maintain persistent presence in a target network in order to extract sensitive data when needed. To maintain persistent presence, attackers seek to blend in with normal network traffic and use ports that are typically allowed by firewalls. As a result, man ...
... The perpetrators of targeted attacks aim to maintain persistent presence in a target network in order to extract sensitive data when needed. To maintain persistent presence, attackers seek to blend in with normal network traffic and use ports that are typically allowed by firewalls. As a result, man ...
Reasons for segmentation.
... An example of segmentation for security is using honeynets. Honeynets are network segments that are created with the sole purpose of attracting any network attacks through the implementation of multiple honeypots. Honeypots are systems that are configured to be attractive to network attackers, helpi ...
... An example of segmentation for security is using honeynets. Honeynets are network segments that are created with the sole purpose of attracting any network attacks through the implementation of multiple honeypots. Honeypots are systems that are configured to be attractive to network attackers, helpi ...
Past Paper - Holy Cross High School
... Natural language processing is one area of artificial intelligence that will enable many more people to use computers. (a) Ambiguity of meaning and similar sounding words both cause problems to developers of natural language processing. (i) Name one other type of problem, generated by everyday langu ...
... Natural language processing is one area of artificial intelligence that will enable many more people to use computers. (a) Ambiguity of meaning and similar sounding words both cause problems to developers of natural language processing. (i) Name one other type of problem, generated by everyday langu ...
Co-authors Point of View
... 3) Service Platform level: How to suite the information towards a customer/Service Provider business? ...
... 3) Service Platform level: How to suite the information towards a customer/Service Provider business? ...
www.ijecs.in International Journal Of Engineering And Computer Science ISSN: 2319-7242
... [email protected] Department of Electronics and Communication, RIET, Ropar [email protected] Abstract: Security is often vital in knowledge networks; however it's significantly crucial in wireless networks like LTE. One in all the distinctive challenges of fourth-generation technology ...
... [email protected] Department of Electronics and Communication, RIET, Ropar [email protected] Abstract: Security is often vital in knowledge networks; however it's significantly crucial in wireless networks like LTE. One in all the distinctive challenges of fourth-generation technology ...
A Security Pattern for a Virtual Private Network
... remotely. They need a secure connection to their company network. We need to develop a secure architecture so that confidential work can be performed. Many companies have offices distributed all over the globe. The employees of such companies need to communicate securely. Secure Systems Research Gro ...
... remotely. They need a secure connection to their company network. We need to develop a secure architecture so that confidential work can be performed. Many companies have offices distributed all over the globe. The employees of such companies need to communicate securely. Secure Systems Research Gro ...
Chapter 07 - Computer Science
... TCP/IP is the Internet protocol hierarchy, composed of five layers: physical, data link, network, transport, and application ...
... TCP/IP is the Internet protocol hierarchy, composed of five layers: physical, data link, network, transport, and application ...
Ch6-a Presentation
... Source – device that sends the message Destination – device that receives the message Handshaking – router establishes the connection between the source and the destination ...
... Source – device that sends the message Destination – device that receives the message Handshaking – router establishes the connection between the source and the destination ...
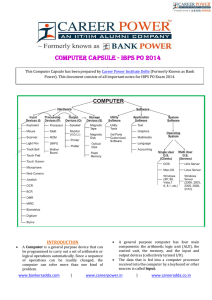
COMPUTER CAPSULE - IBPS PO 2014 . INTRODUCTION
... computer that typically fills a room and may cost many hundreds or thousands of times as much as a personal computer. They are designed to perform large numbers of calculations for governments and large enterprises. Read-only memory (ROM) is a storage medium used in computers and other electronic de ...
... computer that typically fills a room and may cost many hundreds or thousands of times as much as a personal computer. They are designed to perform large numbers of calculations for governments and large enterprises. Read-only memory (ROM) is a storage medium used in computers and other electronic de ...
PPT file - University of Central Florida
... C code for a process node Copyright © 2003 OPNET Technologies, Inc. Confidential, not for distribution to third parties. ...
... C code for a process node Copyright © 2003 OPNET Technologies, Inc. Confidential, not for distribution to third parties. ...