Maintenance ST - Common Criteria
... 7750 SR and SRc service routers as well as 7450 ESS Ethernet services switches. Refer to Table 2 on page 7 for additional information. An Access Control List (ACL) is filter policy applied on ingress or egress to a service SAP on an interface to control the traffic access. SAR-series routers and SAS ...
... 7750 SR and SRc service routers as well as 7450 ESS Ethernet services switches. Refer to Table 2 on page 7 for additional information. An Access Control List (ACL) is filter policy applied on ingress or egress to a service SAP on an interface to control the traffic access. SAR-series routers and SAS ...
Virtual Private Network (VPN)
... Two types of encryption systems Symmetric key encryption Public key encryption These two types of encryption will be discussed more in depth in BA483 ...
... Two types of encryption systems Symmetric key encryption Public key encryption These two types of encryption will be discussed more in depth in BA483 ...
Slide 1
... spent and value of resources protected WSN seems to be an environment where probabilistic approach to security fits better Protocols should be tolerant to partial compromise Automated approaches are welcome due to diversity of usage scenarios ● network topology, hardware characteristics, compr ...
... spent and value of resources protected WSN seems to be an environment where probabilistic approach to security fits better Protocols should be tolerant to partial compromise Automated approaches are welcome due to diversity of usage scenarios ● network topology, hardware characteristics, compr ...
Oracle AQADM Privilege Elevation Vulnerability
... Oracle is a widely deployed DBMS that contains various built-in packages. The DBMS_AQADM package provides procedures to manage Oracle Streams Advanced Queuing (AQ) configuration and administration information. DBMS_AQADM_SYS is a package used internally by DBMS_AQADM to implement some of its functio ...
... Oracle is a widely deployed DBMS that contains various built-in packages. The DBMS_AQADM package provides procedures to manage Oracle Streams Advanced Queuing (AQ) configuration and administration information. DBMS_AQADM_SYS is a package used internally by DBMS_AQADM to implement some of its functio ...
CWNA Guide to Wireless LANs,Third Edition
... – Asset tracking of wireless equipment that has a high value or have been stolen or misplaced (called RealTime Location Services or RTLS) – Finding an emergency Voice Over Wi-Fi caller – Troubleshooting sources of wireless interference – Conducting a site survey – Determining a wireless user’s avail ...
... – Asset tracking of wireless equipment that has a high value or have been stolen or misplaced (called RealTime Location Services or RTLS) – Finding an emergency Voice Over Wi-Fi caller – Troubleshooting sources of wireless interference – Conducting a site survey – Determining a wireless user’s avail ...
Networking for Everyone
... As a recognized industry leader for over 30 years, SMC Networks has pioneered high-quality, standards-based connectivity and Internet access solutions. The company leverages its global manufacturing resources and strategic relationships with technology innovators to bring to market a growing range ...
... As a recognized industry leader for over 30 years, SMC Networks has pioneered high-quality, standards-based connectivity and Internet access solutions. The company leverages its global manufacturing resources and strategic relationships with technology innovators to bring to market a growing range ...
SERVICE DESCRIPTION WEB APPLICATION SECURITY SCANNING
... we are going to work with you to meet those requirements by deliver the service as per required (based on standard package fixed deliverables and scope of service work subscribed, as well as additional service that your may consider before, during and after based on the consulting session). It is ou ...
... we are going to work with you to meet those requirements by deliver the service as per required (based on standard package fixed deliverables and scope of service work subscribed, as well as additional service that your may consider before, during and after based on the consulting session). It is ou ...
chapter1
... original vision: “a group of mutually trusting users attached to a transparent network” Internet protocol designers playing “catch-up” Security considerations in all layers! ...
... original vision: “a group of mutually trusting users attached to a transparent network” Internet protocol designers playing “catch-up” Security considerations in all layers! ...
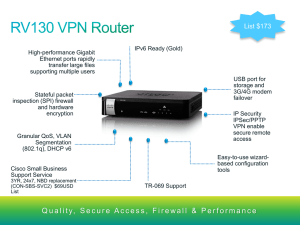
Cisco RV130/RV130W Product Overview
... Allows the business to control access to files and applications, as well as enabling secure guest access Intuitive, browser-based device manager with support for the Cisco FindIT Network Discovery Tool ...
... Allows the business to control access to files and applications, as well as enabling secure guest access Intuitive, browser-based device manager with support for the Cisco FindIT Network Discovery Tool ...
Report The Internet Infrastructure Foundation
... to a network or a network to another network, over insecure communication links – a technique generally referred to as Virtual Private Network, or VPN. The most common technology, with wide spread support in networking equipment, is IPsec. IPsec incorporates security directly on top of IP using the ...
... to a network or a network to another network, over insecure communication links – a technique generally referred to as Virtual Private Network, or VPN. The most common technology, with wide spread support in networking equipment, is IPsec. IPsec incorporates security directly on top of IP using the ...
bluetooth technology
... future. Imagine the current data equipped pay phones in airports being upgraded with Bluetooth modems. This would allow any mobile device equipped with Bluetooth technology to easily connect to the Internet while located within ten meters of that access point. These Access points support much higher ...
... future. Imagine the current data equipped pay phones in airports being upgraded with Bluetooth modems. This would allow any mobile device equipped with Bluetooth technology to easily connect to the Internet while located within ten meters of that access point. These Access points support much higher ...
MEDS – Sample Report - MIEL e
... This report is being supplied by us on the basis that it is for your benefit and information only and that, save as may be required by law or by a competent regulatory authority (in which case you shall inform us in advance), it shall not be copied, referred to or disclosed, in whole (save for your ...
... This report is being supplied by us on the basis that it is for your benefit and information only and that, save as may be required by law or by a competent regulatory authority (in which case you shall inform us in advance), it shall not be copied, referred to or disclosed, in whole (save for your ...
RPL (pronounced ripple) Routing Protocol for Low Power and Lossy
... The routing MUST be configured and managed using secure messages and protocols that prevent outsider attacks and limit insider attacks from field devices installed in insecure locations in the plant. ...
... The routing MUST be configured and managed using secure messages and protocols that prevent outsider attacks and limit insider attacks from field devices installed in insecure locations in the plant. ...
Active Worms - Computer Science and Engineering
... Instances of Active Worms (1) • Morris Worm (1988) [1] – First active worm; took down several thousand UNIX machines on Internet ...
... Instances of Active Worms (1) • Morris Worm (1988) [1] – First active worm; took down several thousand UNIX machines on Internet ...
An Introduction to SSH Secure Shell
... unsuspecting host but instead contain code designed to break into a system. SSH authentication happens on both ends of a connection and therefore, for practical purposes, eliminating unauthorized connections. • DNS spoofing. “DNS spoofi ng is a term used when a DNS server accepts and uses incorrect ...
... unsuspecting host but instead contain code designed to break into a system. SSH authentication happens on both ends of a connection and therefore, for practical purposes, eliminating unauthorized connections. • DNS spoofing. “DNS spoofi ng is a term used when a DNS server accepts and uses incorrect ...
cisco ws sup720 3b
... for example), and security services. The MSFC builds the Cisco Express Forwarding information Base (FIB) table in software and then downloads this table to the hardware Application-specific-integrated circuits (ASICs) on the PFC3 and Distributed forwarding engine (if present) that make the forwardin ...
... for example), and security services. The MSFC builds the Cisco Express Forwarding information Base (FIB) table in software and then downloads this table to the hardware Application-specific-integrated circuits (ASICs) on the PFC3 and Distributed forwarding engine (if present) that make the forwardin ...
Cisco uBR900 Series Cable Access Router
... Cisco uBR900 Series Cable Access Routers allow cable service providers to deliver feature-rich, business-class Virtual Private Network (VPN) and Voice-over-IP (VoIP) services to small businesses, branch offices, and corporate telecommuters. The products integrate a DOCSIS 1.1-based cable modem and C ...
... Cisco uBR900 Series Cable Access Routers allow cable service providers to deliver feature-rich, business-class Virtual Private Network (VPN) and Voice-over-IP (VoIP) services to small businesses, branch offices, and corporate telecommuters. The products integrate a DOCSIS 1.1-based cable modem and C ...
Diapositiva 1 - SI6 Networks
... are kept in the socket send buffer for their possible retransmission. TCP will retransmit those data until they either get acknowledged or the connection times out. In the mean time, system memory is tied to those data. Easy to exploit for memory exhaustion: establish lots of TCP connections, send a ...
... are kept in the socket send buffer for their possible retransmission. TCP will retransmit those data until they either get acknowledged or the connection times out. In the mean time, system memory is tied to those data. Easy to exploit for memory exhaustion: establish lots of TCP connections, send a ...
CISSP Guide to Security Essentials, Ch4
... – Devices can authenticate through a process called “pairing”, during which two devices can exchange a cryptographic secret key that the two devices can later use ...
... – Devices can authenticate through a process called “pairing”, during which two devices can exchange a cryptographic secret key that the two devices can later use ...
SSG140 Secure Services Gateway
... compliance. The SSG140 is a modular platform that delivers more than 350 Mbps of stateful firewall traffic and 100 Mbps of IPsec VPN traffic. Security: Protection against worms, viruses, trojans, spam, and emerging malware is delivered by proven unified threat management (UTM) security features that ...
... compliance. The SSG140 is a modular platform that delivers more than 350 Mbps of stateful firewall traffic and 100 Mbps of IPsec VPN traffic. Security: Protection against worms, viruses, trojans, spam, and emerging malware is delivered by proven unified threat management (UTM) security features that ...
Secured VPN Models for LTE Backhaul Networks
... As a result, there is a possibility of several breaches and IP based attacks to the backhaul. For instance, an IP based attack which initiates in access network could affect the core gateways directly. However, such risks were never seen in previous non IP mobile backhauls. Second, LTE backhaul netw ...
... As a result, there is a possibility of several breaches and IP based attacks to the backhaul. For instance, an IP based attack which initiates in access network could affect the core gateways directly. However, such risks were never seen in previous non IP mobile backhauls. Second, LTE backhaul netw ...