Aprisa SR
... With the move to IP based RTUs, the traffic over the air is significantly increasing, reducing the number of Ethernet RTUs that can be supported in a single network, This is turn means more base station sites, which translates to increased costs for customers to add new points of presence, It is not ...
... With the move to IP based RTUs, the traffic over the air is significantly increasing, reducing the number of Ethernet RTUs that can be supported in a single network, This is turn means more base station sites, which translates to increased costs for customers to add new points of presence, It is not ...
Attacking 802.11 Networks
... • “Crunchy on the outside, soft and chewy on the inside” – Mentos Network Design – Common to many organizations with few security resources to manage client devices – Attacker uses stepping-stone attacks ...
... • “Crunchy on the outside, soft and chewy on the inside” – Mentos Network Design – Common to many organizations with few security resources to manage client devices – Attacker uses stepping-stone attacks ...
C. Wireless Communications Security
... protocols have emerged, Ethernet has become popular in the electric power industry. With more systems connected by networks, operators must take special care to ensure that these systems are not vulnerable. Online threats to SCADA pose as much risk as physical attacks. As cybercriminals become more ...
... protocols have emerged, Ethernet has become popular in the electric power industry. With more systems connected by networks, operators must take special care to ensure that these systems are not vulnerable. Online threats to SCADA pose as much risk as physical attacks. As cybercriminals become more ...
Network Services for Authentication For Wireless LAN
... appliances, ID grid technology, and the Infoblox replication agent, software that runs on the Microsoft domain controller and securely replicates user credentials (user names and passwords) from the domain controller to the grid master and stores them in the built-in Infoblox bloxSDB™ database. The ...
... appliances, ID grid technology, and the Infoblox replication agent, software that runs on the Microsoft domain controller and securely replicates user credentials (user names and passwords) from the domain controller to the grid master and stores them in the built-in Infoblox bloxSDB™ database. The ...
What is a VPN
... frames, which in turn encapsulate IP, IPX, or NetBEUI protocols With L2TP, the computer performs all security checks and validations, and enables data encryption, which makes it much safer to send information over nonsecure networks by using the new Internet Protocol security (IPSec) In this case da ...
... frames, which in turn encapsulate IP, IPX, or NetBEUI protocols With L2TP, the computer performs all security checks and validations, and enables data encryption, which makes it much safer to send information over nonsecure networks by using the new Internet Protocol security (IPSec) In this case da ...
What is a VPN
... frames, which in turn encapsulate IP, IPX, or NetBEUI protocols With L2TP, the computer performs all security checks and validations, and enables data encryption, which makes it much safer to send information over nonsecure networks by using the new Internet Protocol security (IPSec) In this case da ...
... frames, which in turn encapsulate IP, IPX, or NetBEUI protocols With L2TP, the computer performs all security checks and validations, and enables data encryption, which makes it much safer to send information over nonsecure networks by using the new Internet Protocol security (IPSec) In this case da ...
Slide 1
... other Nodes that can then be displayed on a website. Service Clients: submit retrieval data from a Node using a simple client. Integrate Applications: where a local application (webpage, model or report) retrieves information from one or more Nodes as needed. Provide Node Services: use a “hosted” No ...
... other Nodes that can then be displayed on a website. Service Clients: submit retrieval data from a Node using a simple client. Integrate Applications: where a local application (webpage, model or report) retrieves information from one or more Nodes as needed. Provide Node Services: use a “hosted” No ...
Computer networking devices are units that mediate data in a
... at a time. Depending on the network topology, the hub provides a basic level 1 OSI model connection among the network objects (workstations, servers, etc). It provides bandwidth which is shared among all the objects, compared to switches, which provide a dedicated connection between individual nodes ...
... at a time. Depending on the network topology, the hub provides a basic level 1 OSI model connection among the network objects (workstations, servers, etc). It provides bandwidth which is shared among all the objects, compared to switches, which provide a dedicated connection between individual nodes ...
You Can`t Protect What You Can`t See
... All these activities are common and severe enough to warrant consistent monitoring regardless of your industry or location. If you cannot detect these activities, then you are giving threats a place to hide on your network. ...
... All these activities are common and severe enough to warrant consistent monitoring regardless of your industry or location. If you cannot detect these activities, then you are giving threats a place to hide on your network. ...
arubaos xsec module - SecureWirelessWorks.com
... Traditionally, encryption has been performed at Layer 3 (Network Layer) in the form of IPsec. IPsec uses 3DES or AES encryption and can encrypt the IP packet including the source and destination IP addresses in the header. IPsec provides a commonly accepted, secure method of communication over untru ...
... Traditionally, encryption has been performed at Layer 3 (Network Layer) in the form of IPsec. IPsec uses 3DES or AES encryption and can encrypt the IP packet including the source and destination IP addresses in the header. IPsec provides a commonly accepted, secure method of communication over untru ...
Other Malware Threats To Data 30
... 30 Threats To Data Phishing • Means when criminals use fake emails or fake websites • They trick people into clicking links and then entering their personal data, such as bank passwords • The cyber-criminals then obtain money by fraud and identify theft. ...
... 30 Threats To Data Phishing • Means when criminals use fake emails or fake websites • They trick people into clicking links and then entering their personal data, such as bank passwords • The cyber-criminals then obtain money by fraud and identify theft. ...
Distributed Systems
... Differences in data representation of interface types on different processors (of different vendors) have to be resolved. ...
... Differences in data representation of interface types on different processors (of different vendors) have to be resolved. ...
Design and Implementation of Security Operating System based on
... Analyzes and reviews relative work of security ...
... Analyzes and reviews relative work of security ...
Speech Title Here
... Laptop theft Financial fraud Abuse of wireless networks Insider abuse of Net access Theft of proprietary information Denial of service ...
... Laptop theft Financial fraud Abuse of wireless networks Insider abuse of Net access Theft of proprietary information Denial of service ...
Cutting Edge VoIP Security Issues Color
... Average losses due to security breaches are up, but down significantly from 2001 and 2002 (*) The number of incidents is down (*) Incidents are being reported at a greater rate (*) ...
... Average losses due to security breaches are up, but down significantly from 2001 and 2002 (*) The number of incidents is down (*) Incidents are being reported at a greater rate (*) ...
Mid-term Presentation
... - Google File System (Distributed File System Storage) - HDFS (Distributed File System Storage) - Microsoft SQL Azure (Relational Database Storage) ...
... - Google File System (Distributed File System Storage) - HDFS (Distributed File System Storage) - Microsoft SQL Azure (Relational Database Storage) ...
For all scenarios, assume you are employed by Dell Computer
... supervisor gives away the refurbished computers to the local elementary school. No specific records are kept of this type of transaction and Emma really needs a computer for her son who is in college. Her supervisor asks her to deliver 12 computer systems to the school. CASE 3: Mario is the secretar ...
... supervisor gives away the refurbished computers to the local elementary school. No specific records are kept of this type of transaction and Emma really needs a computer for her son who is in college. Her supervisor asks her to deliver 12 computer systems to the school. CASE 3: Mario is the secretar ...
Introduction to Information Security - Cs Team Site | courses.cs.tau.ac.il
... Spear-phishing or human error. Social engineering Pure hacking. ...
... Spear-phishing or human error. Social engineering Pure hacking. ...
Introduction
... how bad guys can attack computer networks how we can defend networks against attacks how to design architectures that are immune to attacks Internet not originally designed with ...
... how bad guys can attack computer networks how we can defend networks against attacks how to design architectures that are immune to attacks Internet not originally designed with ...
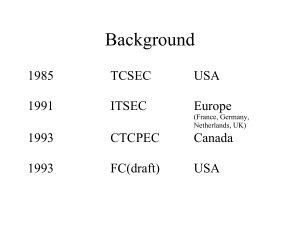
Common Criteria
... Title 10, U.S.C., Section 2223 (reference (a)) •All DoD and Intelligence Community Computers ...
... Title 10, U.S.C., Section 2223 (reference (a)) •All DoD and Intelligence Community Computers ...
CMPE 155 - University of California, Santa Cruz
... Protect organization’s network from attacks originating outside network. ...
... Protect organization’s network from attacks originating outside network. ...
network - CCIT131
... WLAN is more secure compared to LAN (true – false) The Internet is an example of PAN (true – false) Bluetooth is an example of LAN (true – false) ...
... WLAN is more secure compared to LAN (true – false) The Internet is an example of PAN (true – false) Bluetooth is an example of LAN (true – false) ...
83_SURYA NARAYAN CHALAN
... configuration, maintenance, disaster recovery, technical support and troubleshooting. Possess expertise in handling installation of Windows, application software and network drives / cabling; adept at Routing, IP Addressing and Sub netting. Focused and hardworking professional equipped with thorough ...
... configuration, maintenance, disaster recovery, technical support and troubleshooting. Possess expertise in handling installation of Windows, application software and network drives / cabling; adept at Routing, IP Addressing and Sub netting. Focused and hardworking professional equipped with thorough ...