SDN and Security
... • A security enforcement kernel for OpenFlow networks by Philip Porras, Seungwon Shin, Vinod Yegneswaran, Martin Fong, Mabry Tyson, and Guofei Gu, ACM ...
... • A security enforcement kernel for OpenFlow networks by Philip Porras, Seungwon Shin, Vinod Yegneswaran, Martin Fong, Mabry Tyson, and Guofei Gu, ACM ...
Chapter 4 – Database management SystemsApplied Computer
... b. MAC address c. IP address d. USB address 17. Which of the following is used to select a wireless home network from a PC? a. SSID b. MAC address c. IP address d. USB address 18. Which of the following is used to access a router’s control panel from a PC? a. SSID b. MAC address c. IP address d. USB ...
... b. MAC address c. IP address d. USB address 17. Which of the following is used to select a wireless home network from a PC? a. SSID b. MAC address c. IP address d. USB address 18. Which of the following is used to access a router’s control panel from a PC? a. SSID b. MAC address c. IP address d. USB ...
Unit A: Computer and Internet Basics
... needs of a person. It typically provides access to a wide variety of computing applications, such word processing, photo editing, e-mail, etc. There are four types: desktop, notebook computers, workstations, and video game console. Workstations are usually powerful desktop computers for special purp ...
... needs of a person. It typically provides access to a wide variety of computing applications, such word processing, photo editing, e-mail, etc. There are four types: desktop, notebook computers, workstations, and video game console. Workstations are usually powerful desktop computers for special purp ...
Storage Devices and Media Study Guide
... Malware and Other Issues with Information Found on the Internet Try to keep Cloning and Imaging safe from Malware and viruses when transferring files or complete drives. 'Malware' refers to a variety of forms of hostile or intrusive software, including computer viruses, worms, Trojan Horses, ransomw ...
... Malware and Other Issues with Information Found on the Internet Try to keep Cloning and Imaging safe from Malware and viruses when transferring files or complete drives. 'Malware' refers to a variety of forms of hostile or intrusive software, including computer viruses, worms, Trojan Horses, ransomw ...
Collaboration Bus - UNC Computer Science
... Start/stop recording images from all cameras Switch off all lights in the room Switch of all appliances except the refrigerator ...
... Start/stop recording images from all cameras Switch off all lights in the room Switch of all appliances except the refrigerator ...
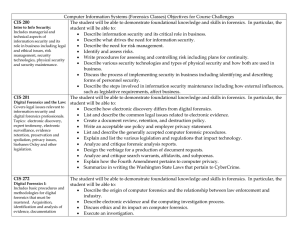
Computer Information Systems (Forensics Classes) Objectives for
... various protocols, responding to attacks on FTP, HTTP, DNS, HTTPS and SSH with advanced attack detection ...
... various protocols, responding to attacks on FTP, HTTP, DNS, HTTPS and SSH with advanced attack detection ...
Absolute Software Overview Brochure
... Gather hundreds of hardware and software data points from devices over the network. Display data with custom views, searches and reports – and export this data into various file formats. Asset information can be integrated into third party applications such as Microsoft SCCM. ...
... Gather hundreds of hardware and software data points from devices over the network. Display data with custom views, searches and reports – and export this data into various file formats. Asset information can be integrated into third party applications such as Microsoft SCCM. ...
Access Security Requirements
... 5.3 Administrative access to firewalls and servers must be performed through a secure internal wired connection only. 5.4 Any stand-alone computers that directly access the Internet must have a desktop firewall deployed that is installed and configured to block unnecessary/unused ports, services, an ...
... 5.3 Administrative access to firewalls and servers must be performed through a secure internal wired connection only. 5.4 Any stand-alone computers that directly access the Internet must have a desktop firewall deployed that is installed and configured to block unnecessary/unused ports, services, an ...
Accounting Information Systems: Essential Concepts
... Databases may be distributed by replication or partition. Replication: Copies of files from the main data base are stored at remote locations Partition: Segments of files are allocated to various locations within the network This avoids data redundancy, but increases the complexity of transmitt ...
... Databases may be distributed by replication or partition. Replication: Copies of files from the main data base are stored at remote locations Partition: Segments of files are allocated to various locations within the network This avoids data redundancy, but increases the complexity of transmitt ...
Pharmaceutical
... while still remaining HIPAA compliant. The following capabilities are offered: Data Encryption. Fully encrypt data at every touch point, keeping it safe within a data center while ensuring it remains just as safe as it flows in and out of that center. Security Management. Log opt-in and opt-out ...
... while still remaining HIPAA compliant. The following capabilities are offered: Data Encryption. Fully encrypt data at every touch point, keeping it safe within a data center while ensuring it remains just as safe as it flows in and out of that center. Security Management. Log opt-in and opt-out ...
Internet-based Research: Perspectives of IT
... • Monitors server for dell specific hardware issues and writes error to server logs when error occurs ...
... • Monitors server for dell specific hardware issues and writes error to server logs when error occurs ...
information system
... People rely on modern information systems to communicate with each other using a variety of physical devices (hardware), information processing instructions and procedures (software), communications channels (networks), and stored data (data resources). ...
... People rely on modern information systems to communicate with each other using a variety of physical devices (hardware), information processing instructions and procedures (software), communications channels (networks), and stored data (data resources). ...
Unit E - Home - KSU Faculty Member websites
... – Treats every computer as an equal – Workstations transfer data to each other ...
... – Treats every computer as an equal – Workstations transfer data to each other ...
C: Glossary
... To change analog information to a digital format. Once information has been converted to this form, it can be conveniently stored, manipulated, and compressed. It can also be transmitted over a distance with little or no loss in quality. Sound (such as speech or music), still images (such as transpa ...
... To change analog information to a digital format. Once information has been converted to this form, it can be conveniently stored, manipulated, and compressed. It can also be transmitted over a distance with little or no loss in quality. Sound (such as speech or music), still images (such as transpa ...
Guide on Information Technology Security
... Communication is essential for us to achieve our business goals and the Internet is fast becoming one of the essential tools to exchange information. Electronic means to transfer files, such as electronic mail and the World Wide Web, have allowed the development of cooperation between scientists and ...
... Communication is essential for us to achieve our business goals and the Internet is fast becoming one of the essential tools to exchange information. Electronic means to transfer files, such as electronic mail and the World Wide Web, have allowed the development of cooperation between scientists and ...
How to Prevent Unauthorized Access to Laser Beam Printers and
... This guide only describes those features within the application that have some discernible impact to the general network environment, whether it be the overall network, security, or other customer resources. ...
... This guide only describes those features within the application that have some discernible impact to the general network environment, whether it be the overall network, security, or other customer resources. ...
The Cyber-Crime Threat to the UK - Royal United Services Institute
... which can be increased in their scale or reach by use of computers, networks or other forms of ICT). These are some of the most common ways in which criminals can profit from online criminal activity: Online financial fraud: the defrauding of legitimate businesses, using forged or fraudulent credit ...
... which can be increased in their scale or reach by use of computers, networks or other forms of ICT). These are some of the most common ways in which criminals can profit from online criminal activity: Online financial fraud: the defrauding of legitimate businesses, using forged or fraudulent credit ...
Basic DataCommunication
... collaborate, or work online, with other users connected to a server Collaboration software including tools that enable users to share documents via online meetings and communicate with other ...
... collaborate, or work online, with other users connected to a server Collaboration software including tools that enable users to share documents via online meetings and communicate with other ...
Categories of Networks
... • packets passed from node to node between source and destination • used for terminal to computer and computer to computer communications ...
... • packets passed from node to node between source and destination • used for terminal to computer and computer to computer communications ...
Computer Literacy Vocabulary List Input Device
... Hack- to gain unauthorized access to others computers Hacker- one who hacks Hardware- physical components of a computer HTML (hyper-text markup language)- what the web is written in Hyperlink- can be clicked to jump to a different section of the current document Hypertext- texts that links Integer- ...
... Hack- to gain unauthorized access to others computers Hacker- one who hacks Hardware- physical components of a computer HTML (hyper-text markup language)- what the web is written in Hyperlink- can be clicked to jump to a different section of the current document Hypertext- texts that links Integer- ...
Document
... breached in the last 12 months, with 64 percent of the breaches costing $2 million or more.” - csi Of those: 99% used antivirus software 98% used firewalls 91% employed physical security to protect their ...
... breached in the last 12 months, with 64 percent of the breaches costing $2 million or more.” - csi Of those: 99% used antivirus software 98% used firewalls 91% employed physical security to protect their ...