VPN et IPSec
... which is openly accessible, and is managed within the terms and constraints of a common public resource, often via a public administrative entity. By contrast, a “private” facility is one where access is restricted to a defined set of entities, and third parties cannot gain access. Typically, the pr ...
... which is openly accessible, and is managed within the terms and constraints of a common public resource, often via a public administrative entity. By contrast, a “private” facility is one where access is restricted to a defined set of entities, and third parties cannot gain access. Typically, the pr ...
convrey-bh-us-02-layer2
... • All attacks and mitigation techniques assume a switched Ethernet network running IP If shared Ethernet access is used (WLAN, Hub, etc.) most of these attacks get much easier If you aren’t using Ethernet as your L2 protocol, some of these attacks may not work, but you may be vulnerable to different ...
... • All attacks and mitigation techniques assume a switched Ethernet network running IP If shared Ethernet access is used (WLAN, Hub, etc.) most of these attacks get much easier If you aren’t using Ethernet as your L2 protocol, some of these attacks may not work, but you may be vulnerable to different ...
About the Presentations
... One-Time Password Software • Two types of one-time passwords are available: – Challenge-response passwords • Authenticating computer or firewall generates a random number (the challenge) and sends it to the user, who enters a secret PIN or password (the ...
... One-Time Password Software • Two types of one-time passwords are available: – Challenge-response passwords • Authenticating computer or firewall generates a random number (the challenge) and sends it to the user, who enters a secret PIN or password (the ...
CCNP 2 Version 5 Module 5 - Cisco Device Hardening Module 5
... range of tools and techniques, an attacker can discover the company domain names; network blocks; IP addresses of systems, ports, and services used; and many other details pertaining to the company security posture as related to the Internet, an intranet, remote access, and an extranet. In a simple ...
... range of tools and techniques, an attacker can discover the company domain names; network blocks; IP addresses of systems, ports, and services used; and many other details pertaining to the company security posture as related to the Internet, an intranet, remote access, and an extranet. In a simple ...
Session 7-12. Modern IT Architecture
... • Communicating information VIA electronic means over some distance • Service provided by telecom companies: telephone, mobile phone, wireless transmission, data communication, Cable TV, satellite, ………….. ...
... • Communicating information VIA electronic means over some distance • Service provided by telecom companies: telephone, mobile phone, wireless transmission, data communication, Cable TV, satellite, ………….. ...
Bob Benson - Lewis University Department of Computer
... The VMWare server software may be downloaded from the VMware web site after registering for a free license [2]. The vendor provides online documentation for this software [4]. This software installs on either a Linux or Windows operating systems. VMWare Server version 1.0 released 7/10/06 with a bui ...
... The VMWare server software may be downloaded from the VMware web site after registering for a free license [2]. The vendor provides online documentation for this software [4]. This software installs on either a Linux or Windows operating systems. VMWare Server version 1.0 released 7/10/06 with a bui ...
MIS9eXLME
... The amount of information that can be transferred in a given amount of time Usually expressed as bits per second (bps) Higher bandwidths expressed as ...
... The amount of information that can be transferred in a given amount of time Usually expressed as bits per second (bps) Higher bandwidths expressed as ...
Communication-and-Security-in-M2M
... identifier, transparent of the underlying communication tech. • As in the current Internet architecture, security will remain of prime important and will in fact represent a fundamental enabling factor of most of the current applications of M2M communication. ...
... identifier, transparent of the underlying communication tech. • As in the current Internet architecture, security will remain of prime important and will in fact represent a fundamental enabling factor of most of the current applications of M2M communication. ...
Content centric networking
... Global entities /parc.com/people/presentations (name of some data) Local entities /thisRoom/projector (name of a projector) While global entities utilise the DNS global naming structure, local entities can point to different objects depending on location or other contexts ...
... Global entities /parc.com/people/presentations (name of some data) Local entities /thisRoom/projector (name of a projector) While global entities utilise the DNS global naming structure, local entities can point to different objects depending on location or other contexts ...
FIREWALL DEPLOYMENT AND CONFIGURATION
... weak or unchanged password. There are many methods hackers could break your passwords. For example, some programs like Crack are freely available on the Internet for hackers to crack insecure passwords. Therefore, changing passwords after a certain time is essential. [3] Some TCP (Transmission Contr ...
... weak or unchanged password. There are many methods hackers could break your passwords. For example, some programs like Crack are freely available on the Internet for hackers to crack insecure passwords. Therefore, changing passwords after a certain time is essential. [3] Some TCP (Transmission Contr ...
McAfee Wireless Home Network Security Suite
... Some software programs that are licensed (or sublicensed) to the user under the GNU General Public License (GPL) or other similar Free Software licenses which, among other rights, permit the user to copy, modify and redistribute certain programs, or portions thereof, and have access to the source co ...
... Some software programs that are licensed (or sublicensed) to the user under the GNU General Public License (GPL) or other similar Free Software licenses which, among other rights, permit the user to copy, modify and redistribute certain programs, or portions thereof, and have access to the source co ...
PDF
... traffic, including worms, spyware, adware, network viruses, and application abuse, before they affect business resiliency. Networks have evolved into complicated architectures, involving multiple segments, branches, ingress and egress points. Due to this constantly changing landscape, network securi ...
... traffic, including worms, spyware, adware, network viruses, and application abuse, before they affect business resiliency. Networks have evolved into complicated architectures, involving multiple segments, branches, ingress and egress points. Due to this constantly changing landscape, network securi ...
EC-Council Course Catalogs
... associated mitigations or remediation's available through the use of appropriate technical security applications and/or use of security resources. ...
... associated mitigations or remediation's available through the use of appropriate technical security applications and/or use of security resources. ...
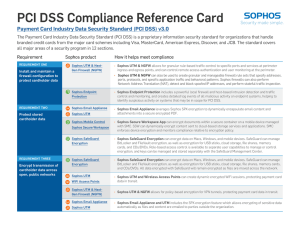
PCI DSS Compliance Reference Card
... ÌÌ Sophos Mobile Security for Android can protect users from malicious applications or potential threats within potentially unwanted applications (PUAs) downloaded by users. ...
... ÌÌ Sophos Mobile Security for Android can protect users from malicious applications or potential threats within potentially unwanted applications (PUAs) downloaded by users. ...
Security Guide - A Guide to Securing Fedora Linux
... Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL® is a reg ...
... Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL® is a reg ...
Security Guide - A Guide to Securing Fedora Linux
... Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL® is a reg ...
... Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL® is a reg ...
The Expanding Role of Service Providers in DDoS Mitigation
... centers to block the attack traffic. From there, they re-inject the “good” traffic back into the provider network. Arbor Networks provides the vast majority of service provider DDoS mitigation equipment, including to nearly all Tier 1 service providers, powering more than 50 Internet service provide ...
... centers to block the attack traffic. From there, they re-inject the “good” traffic back into the provider network. Arbor Networks provides the vast majority of service provider DDoS mitigation equipment, including to nearly all Tier 1 service providers, powering more than 50 Internet service provide ...
BGP
... An AS refuses to act as transit, Limit path advertise An AS can become transit for some AS’s ...
... An AS refuses to act as transit, Limit path advertise An AS can become transit for some AS’s ...
BGP
... Christian Huitema: “Routing in the Internet”, chapters 8 and 9. John Stewart III: “BGP4 - Inter-domain routing in the Univ. of Tehran Computer Network ...
... Christian Huitema: “Routing in the Internet”, chapters 8 and 9. John Stewart III: “BGP4 - Inter-domain routing in the Univ. of Tehran Computer Network ...
Attacks to the IDS
... Gateway Intrusion Detection System – A network intrusion detection system which acts as a network gateway – Designed to stop malicious traffic and generate alerts on suspicious traffic – An “ideal” gateway IDS is able to stop all ...
... Gateway Intrusion Detection System – A network intrusion detection system which acts as a network gateway – Designed to stop malicious traffic and generate alerts on suspicious traffic – An “ideal” gateway IDS is able to stop all ...
Protection in General-Purpose Operating Systems
... Code 1 for Challenge; 2 for Response. Identifier The Identifier field is one octet.(A unit of data that consists of exactly 8 bits) The Identifier field MUST be changed each time a Challenge is sent. The Response Identifier MUST be copied from the Identifier field of the Challenge which caused the R ...
... Code 1 for Challenge; 2 for Response. Identifier The Identifier field is one octet.(A unit of data that consists of exactly 8 bits) The Identifier field MUST be changed each time a Challenge is sent. The Response Identifier MUST be copied from the Identifier field of the Challenge which caused the R ...
SweetBait: Zero-Hour Worm Detection and Containment Using Honeypots
... meta-information. Such data include the timestamp to indicate the time of generation, the source of the signature (e.g., the IP of the honeypot), and various flags to indicate whether it has been verified by an expert to be a valid or a false signature. The latter is essential information that perm ...
... meta-information. Such data include the timestamp to indicate the time of generation, the source of the signature (e.g., the IP of the honeypot), and various flags to indicate whether it has been verified by an expert to be a valid or a false signature. The latter is essential information that perm ...
feb05_eap_usage
... – Problem to solve is “bootstrapping” – This is about how to (a) find a home agent and (b) set up a security association with it so that the mobile node can use the home agent’s services – Want to avoid deployment problem of yet another configuration and secret just because you want to be mobile – O ...
... – Problem to solve is “bootstrapping” – This is about how to (a) find a home agent and (b) set up a security association with it so that the mobile node can use the home agent’s services – Want to avoid deployment problem of yet another configuration and secret just because you want to be mobile – O ...