Network Security Overview
... system or application being attacked. Another form of access attacks involves privilege escalation. This is done by legitimate users who have a lower level of access privileges or intruders who have gained lower-privileged access. The intent is to get information or execute procedures that are unaut ...
... system or application being attacked. Another form of access attacks involves privilege escalation. This is done by legitimate users who have a lower level of access privileges or intruders who have gained lower-privileged access. The intent is to get information or execute procedures that are unaut ...
Slide 1 - IITK - Indian Institute of Technology Kanpur
... • Hide the Service Set ID or SSID :Sometimes changing the SSID is also not full proof as hackers have advanced methods to intrude into a wireless network if the SSID is known. To prevent such cases the SSID needs to be hidden. Router configuration softwares allow the SSID to be hidden and the steps ...
... • Hide the Service Set ID or SSID :Sometimes changing the SSID is also not full proof as hackers have advanced methods to intrude into a wireless network if the SSID is known. To prevent such cases the SSID needs to be hidden. Router configuration softwares allow the SSID to be hidden and the steps ...
physcial_sci_networks_part2
... • Need to trade off the strength of security with the practicality of the measures – Users when faced with a complex process may attempt to undermine the system • Sharing of passwords • Not logging out ...
... • Need to trade off the strength of security with the practicality of the measures – Users when faced with a complex process may attempt to undermine the system • Sharing of passwords • Not logging out ...
thesis proposal - uhcl - College of Science and Engineering
... 1. Logical Ports: Since, unlike wired networks, wireless stations are not connected to the network by physical means, they must have some sort of association relation with an Access Point in order to use the WLAN. This association is established b y allowing the clients and Access Point to know each ...
... 1. Logical Ports: Since, unlike wired networks, wireless stations are not connected to the network by physical means, they must have some sort of association relation with an Access Point in order to use the WLAN. This association is established b y allowing the clients and Access Point to know each ...
Review For Exam notes
... SSID frequently broadcasted by the access point for ease of discovery. SSID in frame headers are transmitted in clear text SSID broadcasting could be disabled but it’s a weak security measure Sniffer programs (e.g. Kismet) can find SSIDs easily ...
... SSID frequently broadcasted by the access point for ease of discovery. SSID in frame headers are transmitted in clear text SSID broadcasting could be disabled but it’s a weak security measure Sniffer programs (e.g. Kismet) can find SSIDs easily ...
Complete Wireless Network Upgrade for Flagstaff Campus
... hot spots in hotels, coffee shops, and other public areas. It is becoming common to have broad coverage in University campuses. NAU requires a modern wireless network and an underlying network infrastructure in order to meet student and faculty expectations, stay competitive, and encourage innovatio ...
... hot spots in hotels, coffee shops, and other public areas. It is becoming common to have broad coverage in University campuses. NAU requires a modern wireless network and an underlying network infrastructure in order to meet student and faculty expectations, stay competitive, and encourage innovatio ...
Chapter 1 - William Stallings, Data and Computer Communications
... computer by merely being brought within range. ...
... computer by merely being brought within range. ...
Network interface cards (NIC)
... • A type of communications where a channel or circuit is established for the duration of the call. • That circuit is dedicated to the two end nodes using it. • 1950’s/60’s the networks were analog, circuit switched networks. • Telephony companies invested millions/billions of dollars in equipment ov ...
... • A type of communications where a channel or circuit is established for the duration of the call. • That circuit is dedicated to the two end nodes using it. • 1950’s/60’s the networks were analog, circuit switched networks. • Telephony companies invested millions/billions of dollars in equipment ov ...
Chapter 6 slides, Computer Networking, 3rd edition
... laptop, PDA, IP phone run applications may be stationary (non-mobile) or mobile ...
... laptop, PDA, IP phone run applications may be stationary (non-mobile) or mobile ...
Introduction - start [kondor.etf.rs]
... Servers store various kinds of information for users, for example DNS databases, e-mails, web pages and provide it to the users. Gateways convert data format, and negotiate QoS with the network. ...
... Servers store various kinds of information for users, for example DNS databases, e-mails, web pages and provide it to the users. Gateways convert data format, and negotiate QoS with the network. ...
network topology
... A firewall is a set of related programs, located at a network gateway server that protects the resources of a private network from users from other networks. An enterprise with an intranet that allows its workers access to the wider Internet installs a firewall to prevent outsiders from accessing it ...
... A firewall is a set of related programs, located at a network gateway server that protects the resources of a private network from users from other networks. An enterprise with an intranet that allows its workers access to the wider Internet installs a firewall to prevent outsiders from accessing it ...
WLAN Site Surveys and Security Considerations
... Does not specify MAC level encryption type (I.e. WEP40/104 or other), so independent of it However, 802.1x can be used to set WEP keys – Addresses Key Distribution problem – Permits rapidly changing, individual WEP keys – WEP is still required for encryption eLearning…Wired and Wirelessly! ...
... Does not specify MAC level encryption type (I.e. WEP40/104 or other), so independent of it However, 802.1x can be used to set WEP keys – Addresses Key Distribution problem – Permits rapidly changing, individual WEP keys – WEP is still required for encryption eLearning…Wired and Wirelessly! ...
All-in-one modem and router solution for Internet
... on one computer, and listen to it anywhere in the house. Organize all of your family’s digital pictures in one place, to simplify finding the ones you want, and easing backup to CD-R. Utilize extra free space on one computer when another’s hard drive starts to fill up. The new Wi-Fi Protected Setup ...
... on one computer, and listen to it anywhere in the house. Organize all of your family’s digital pictures in one place, to simplify finding the ones you want, and easing backup to CD-R. Utilize extra free space on one computer when another’s hard drive starts to fill up. The new Wi-Fi Protected Setup ...
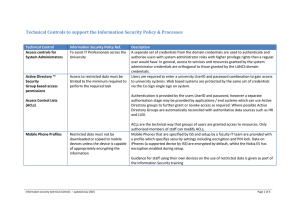
Technical Controls to support the Information
... When sending email; copying data onto, for example, CDs, laptops, phones or USB sticks; or when working outside the confines of the University you must secure information appropriately. When working with restricted information away from the University you must always use a secure mechanism such as V ...
... When sending email; copying data onto, for example, CDs, laptops, phones or USB sticks; or when working outside the confines of the University you must secure information appropriately. When working with restricted information away from the University you must always use a secure mechanism such as V ...
Wireless, Voice, Desktop Video, and BYOD Implications for
... aged devices - 20K Routers, switches, ...
... aged devices - 20K Routers, switches, ...
Cybersecurity - Queen`s Wiki
... ITS will never ask for your NetID password through email or text ...
... ITS will never ask for your NetID password through email or text ...
Broadband Voice IAD
... of packets, and an integrated Denial of Service (DoS) engine monitors a wide range of attack patterns, and logs potential security breaches to a local cache or remote server. The SpeedTouch 706WL/780WL also support powerful wireless security mechanisms, such as Wi-Fi Protected AccessTM (WPA), Wired ...
... of packets, and an integrated Denial of Service (DoS) engine monitors a wide range of attack patterns, and logs potential security breaches to a local cache or remote server. The SpeedTouch 706WL/780WL also support powerful wireless security mechanisms, such as Wi-Fi Protected AccessTM (WPA), Wired ...
Presentation
... whose sole purpose is to sneak through security systems. Whereas crackers sole aim is to break into secure systems, hackers are more interested in gaining knowledge about computer systems and possibly using this knowledge for playful pranks. Although hackers still argue that there's a big difference ...
... whose sole purpose is to sneak through security systems. Whereas crackers sole aim is to break into secure systems, hackers are more interested in gaining knowledge about computer systems and possibly using this knowledge for playful pranks. Although hackers still argue that there's a big difference ...
Sensor Networks
... • Limited input and output options – light/speaker only makes diagnosis and performance evaluation difficult ...
... • Limited input and output options – light/speaker only makes diagnosis and performance evaluation difficult ...
View File - University of Engineering and Technology, Taxila
... Packet-based switching for both voice and data ...
... Packet-based switching for both voice and data ...
Appendix 5 to the TD – Environment Description and the
... Appendix 5 to the TD – Environment Description and the Cooperation of the Contracting Entity and the Bidder a) Cooperation The Contracting Entity shall provide to the Bidder (Supplier) the following at regular pricelist prices: Premises for the placement of the (core) BRS Information System. Cab ...
... Appendix 5 to the TD – Environment Description and the Cooperation of the Contracting Entity and the Bidder a) Cooperation The Contracting Entity shall provide to the Bidder (Supplier) the following at regular pricelist prices: Premises for the placement of the (core) BRS Information System. Cab ...
ppt
... No firewall between local network and the Internet. If using your own private laptop, for your security set your local rules properly ! ...
... No firewall between local network and the Internet. If using your own private laptop, for your security set your local rules properly ! ...
William Stallings Data and Computer Communications
... Wide Area Networks Large geographical area Crossing public rights of way Rely in part on common carrier circuits ...
... Wide Area Networks Large geographical area Crossing public rights of way Rely in part on common carrier circuits ...
What*s inside your network?
... and blocked by web proxy and web application firewalls and network intrusion prevention security controls via deep packet inspection Once outbound packets were encrypted communications were able to traverse the network ...
... and blocked by web proxy and web application firewalls and network intrusion prevention security controls via deep packet inspection Once outbound packets were encrypted communications were able to traverse the network ...
Wireless security
.jpg?width=300)
Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is a notoriously weak security standard. The password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP is an old IEEE 802.11 standard from 1999, which was outdated in 2003 by WPA, or Wi-Fi Protected Access. WPA was a quick alternative to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device that encrypts the network with a 256-bit key; the longer key length improves security over WEP.Many laptop computers have wireless cards pre-installed. The ability to enter a network while mobile has great benefits. However, wireless networking is prone to some security issues. Hackers have found wireless networks relatively easy to break into, and even use wireless technology to hack into wired networks. As a result, it is very important that enterprises define effective wireless security policies that guard against unauthorized access to important resources. Wireless Intrusion Prevention Systems (WIPS) or Wireless Intrusion Detection Systems (WIDS) are commonly used to enforce wireless security policies.The risks to users of wireless technology have increased as the service has become more popular. There were relatively few dangers when wireless technology was first introduced. Hackers had not yet had time to latch on to the new technology, and wireless networks were not commonly found in the work place. However, there are many security risks associated with the current wireless protocols and encryption methods, and in the carelessness and ignorance that exists at the user and corporate IT level. Hacking methods have become much more sophisticated and innovative with wireless access. Hacking has also become much easier and more accessible with easy-to-use Windows- or Linux-based tools being made available on the web at no charge.Some organizations that have no wireless access points installed do not feel that they need to address wireless security concerns. In-Stat MDR and META Group have estimated that 95% of all corporate laptop computers that were planned to be purchased in 2005 were equipped with wireless cards. Issues can arise in a supposedly non-wireless organization when a wireless laptop is plugged into the corporate network. A hacker could sit out in the parking lot and gather information from it through laptops and/or other devices, or even break in through this wireless card–equipped laptop and gain access to the wired network.








![Introduction - start [kondor.etf.rs]](http://s1.studyres.com/store/data/000507900_1-4612cc6372b2ee158f9c52bcf8aea7c5-300x300.png)