Slide 1
... Changing Threat Landscape Evolution of NAC to Security Automation Intro to Bradford Networks Leveraging Integration and Correlation Rapid Threat Response Business Impact ...
... Changing Threat Landscape Evolution of NAC to Security Automation Intro to Bradford Networks Leveraging Integration and Correlation Rapid Threat Response Business Impact ...
9_13_35_JanResume
... To learn the minutest aspect of the work given and to implement it in the best possible way so as to enhance my skills and give better performance to the Organization. And not only to be a part of a successful organization but also to be reason of its success. Professional Strenght ...
... To learn the minutest aspect of the work given and to implement it in the best possible way so as to enhance my skills and give better performance to the Organization. And not only to be a part of a successful organization but also to be reason of its success. Professional Strenght ...
PowerPoint-05
... connected to the WLAN • Discovery is a twofold process: the AP or other wireless devices must transmit an appropriate frame (beaconing), and the wireless device must be looking for those frames (scanning) • Once a wireless device has discovered the WLAN, it requests to join the network; This is a tw ...
... connected to the WLAN • Discovery is a twofold process: the AP or other wireless devices must transmit an appropriate frame (beaconing), and the wireless device must be looking for those frames (scanning) • Once a wireless device has discovered the WLAN, it requests to join the network; This is a tw ...
Covert channel
... Covert channel • In computer security, a covert channel is a type of computer security attack that creates a capability to transfer information objects between processes that are not supposed to be allowed to communicate by the computer security policy. ...
... Covert channel • In computer security, a covert channel is a type of computer security attack that creates a capability to transfer information objects between processes that are not supposed to be allowed to communicate by the computer security policy. ...
wireless
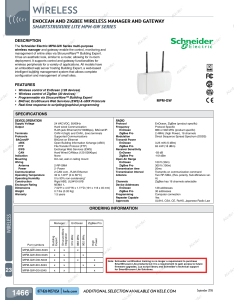
... ENOCEAN AND ZIGBEE WIRELESS MANAGER AND GATEWAY SMARTSTRUXURE LITE MPM-GW SERIES DESCRIPTION The Schneider Electric MPM-GW Series multi-purpose wireless manager and gateway enable the control, monitoring and management of entire sites via StruxureWare™ Building Expert. It has an aesthetic look, simi ...
... ENOCEAN AND ZIGBEE WIRELESS MANAGER AND GATEWAY SMARTSTRUXURE LITE MPM-GW SERIES DESCRIPTION The Schneider Electric MPM-GW Series multi-purpose wireless manager and gateway enable the control, monitoring and management of entire sites via StruxureWare™ Building Expert. It has an aesthetic look, simi ...
Local-area network
... Internet Connections • There are various technologies available that you can use to connect a home computer to the Internet – A phone modem converts computer data into an analog audio signal for transfer over a telephone line, and then a modem at the destination converts it back again into data – A ...
... Internet Connections • There are various technologies available that you can use to connect a home computer to the Internet – A phone modem converts computer data into an analog audio signal for transfer over a telephone line, and then a modem at the destination converts it back again into data – A ...
SkyPilot Network Overview
... • Provides high-gain, improved penetration, and greater reach (up to 10 miles / 16 km between nodes) • NLOS via OFDM’s intrinsic multipath capabilities ...
... • Provides high-gain, improved penetration, and greater reach (up to 10 miles / 16 km between nodes) • NLOS via OFDM’s intrinsic multipath capabilities ...
Secure Mobile IP Communication - Department of Computer Science
... • Describes a solution called Secure Mobile IP (SecMIP) to provide mobile IP users secure access to their company's firewall protected virtual private network. • The solution requires neither introducing new protocols nor to insert or modify network components. It only requires a slight adaptation o ...
... • Describes a solution called Secure Mobile IP (SecMIP) to provide mobile IP users secure access to their company's firewall protected virtual private network. • The solution requires neither introducing new protocols nor to insert or modify network components. It only requires a slight adaptation o ...
Aprisa SR
... With the move to IP based RTUs, the traffic over the air is significantly increasing, reducing the number of Ethernet RTUs that can be supported in a single network, This is turn means more base station sites, which translates to increased costs for customers to add new points of presence, It is not ...
... With the move to IP based RTUs, the traffic over the air is significantly increasing, reducing the number of Ethernet RTUs that can be supported in a single network, This is turn means more base station sites, which translates to increased costs for customers to add new points of presence, It is not ...
Mobile Experience Your Way
... Pre-validated, pre-tested architecture for faster deployment, risk mitigation ...
... Pre-validated, pre-tested architecture for faster deployment, risk mitigation ...
Visualization
... Correlation uses software technology to analyze aggregated data, in real-time, to determine if specific patterns exist. These patterns of similar security events often correspond to specific securityattacks – whether denial of service,anti virus, or some other form of attack. Visualization, the fina ...
... Correlation uses software technology to analyze aggregated data, in real-time, to determine if specific patterns exist. These patterns of similar security events often correspond to specific securityattacks – whether denial of service,anti virus, or some other form of attack. Visualization, the fina ...
Chapter 8 Intro
... • Ethernet Standard (IEEE 802.3) systems use a Star physical topology • But their logical topology is actually a bus topology ...
... • Ethernet Standard (IEEE 802.3) systems use a Star physical topology • But their logical topology is actually a bus topology ...
module4.1
... between a group of N users against eavesdropping. • To ensure confidentiality, a simple scheme is to let all group members share the same secret key, which is used to encrypt and decrypt all messages transmitted between group members. • Because the secret key in this scheme is shared by all members, ...
... between a group of N users against eavesdropping. • To ensure confidentiality, a simple scheme is to let all group members share the same secret key, which is used to encrypt and decrypt all messages transmitted between group members. • Because the secret key in this scheme is shared by all members, ...
Introduction to Information Security - Cs Team Site | courses.cs.tau.ac.il
... passwords: Each 7 bytes of the password is hashed seperately making it easier instead of 256^14 we get 256^7 * 2. Therefore a rainbow table can be easily ...
... passwords: Each 7 bytes of the password is hashed seperately making it easier instead of 256^14 we get 256^7 * 2. Therefore a rainbow table can be easily ...
Set 1 File
... - if one connection fails, the rest of the network will fail. To avoid this a dual ring could be used. IEEE 802.5 ( IBM Token Ring) & FDDI (Fiber Distributed ...
... - if one connection fails, the rest of the network will fail. To avoid this a dual ring could be used. IEEE 802.5 ( IBM Token Ring) & FDDI (Fiber Distributed ...
붙임 3 - CCRG
... multicast have many uses in multimedia applications, data distribution services, and as tools for other communications protocols. More recently, the availability of less expensive sensors has prompted renewed interest in group communication within the context of sensor networks. ...
... multicast have many uses in multimedia applications, data distribution services, and as tools for other communications protocols. More recently, the availability of less expensive sensors has prompted renewed interest in group communication within the context of sensor networks. ...
Simulators for Sensor Networks
... • It should be efficient for large simulations. • There should be technical support. ...
... • It should be efficient for large simulations. • There should be technical support. ...
Target audience
... The secure infrastructure configuration should be the most important line of defense in every organization. Unfortunately, people, the most valuable resource, are not always aware of the level of security in their companies, possible points of entry, how operating systems are attacked, and how to pr ...
... The secure infrastructure configuration should be the most important line of defense in every organization. Unfortunately, people, the most valuable resource, are not always aware of the level of security in their companies, possible points of entry, how operating systems are attacked, and how to pr ...
DHCP Server Configuration - Brookdale Community College
... • Subnet Mask: This field is read-only and reports the Access Point.s current subnet mask. DHCP clients that receive dynamic addresses from the AP will be assigned this same subnet mask. • Gateway IP Address: The AP will assign the specified address to its DHCP clients. • Primary DNS IP Address: The ...
... • Subnet Mask: This field is read-only and reports the Access Point.s current subnet mask. DHCP clients that receive dynamic addresses from the AP will be assigned this same subnet mask. • Gateway IP Address: The AP will assign the specified address to its DHCP clients. • Primary DNS IP Address: The ...
See the dedicated slideshow - VCE IT Lecture Notes by Mark Kelly
... Server farms On smaller networks, network services are performed by software in a single server. On busy LANs, multiple servers share the work… •Login servers – authenticate users •Proxy servers – cache downloads •DHCP servers – allocate IP addresses •Print servers –manage print job queues •Web/FTP ...
... Server farms On smaller networks, network services are performed by software in a single server. On busy LANs, multiple servers share the work… •Login servers – authenticate users •Proxy servers – cache downloads •DHCP servers – allocate IP addresses •Print servers –manage print job queues •Web/FTP ...
ppt
... – The use of the same user-ID on all computers and networks is desirable for the purpose of account maintenance – User account provides accountability ...
... – The use of the same user-ID on all computers and networks is desirable for the purpose of account maintenance – User account provides accountability ...
Wireless security
.jpg?width=300)
Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is a notoriously weak security standard. The password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP is an old IEEE 802.11 standard from 1999, which was outdated in 2003 by WPA, or Wi-Fi Protected Access. WPA was a quick alternative to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device that encrypts the network with a 256-bit key; the longer key length improves security over WEP.Many laptop computers have wireless cards pre-installed. The ability to enter a network while mobile has great benefits. However, wireless networking is prone to some security issues. Hackers have found wireless networks relatively easy to break into, and even use wireless technology to hack into wired networks. As a result, it is very important that enterprises define effective wireless security policies that guard against unauthorized access to important resources. Wireless Intrusion Prevention Systems (WIPS) or Wireless Intrusion Detection Systems (WIDS) are commonly used to enforce wireless security policies.The risks to users of wireless technology have increased as the service has become more popular. There were relatively few dangers when wireless technology was first introduced. Hackers had not yet had time to latch on to the new technology, and wireless networks were not commonly found in the work place. However, there are many security risks associated with the current wireless protocols and encryption methods, and in the carelessness and ignorance that exists at the user and corporate IT level. Hacking methods have become much more sophisticated and innovative with wireless access. Hacking has also become much easier and more accessible with easy-to-use Windows- or Linux-based tools being made available on the web at no charge.Some organizations that have no wireless access points installed do not feel that they need to address wireless security concerns. In-Stat MDR and META Group have estimated that 95% of all corporate laptop computers that were planned to be purchased in 2005 were equipped with wireless cards. Issues can arise in a supposedly non-wireless organization when a wireless laptop is plugged into the corporate network. A hacker could sit out in the parking lot and gather information from it through laptops and/or other devices, or even break in through this wireless card–equipped laptop and gain access to the wired network.