Network Interface Card Specifications
... Add Ethernet IP-addressability to any TMS/LC2000 System Available as a factory-shipped option or as a field upgrade for any TMS/LC2000 Installs within the locked TMS/LC2000 enclosure for secure, tamperproof connectivity Easy, user-programmable IP Address, Subnet Mask and Gateway Address programming ...
... Add Ethernet IP-addressability to any TMS/LC2000 System Available as a factory-shipped option or as a field upgrade for any TMS/LC2000 Installs within the locked TMS/LC2000 enclosure for secure, tamperproof connectivity Easy, user-programmable IP Address, Subnet Mask and Gateway Address programming ...
9 Simple steps to secure your Wi-Fi Network.
... WEP (Wired Equivalent Privacy) keys can be cracked with relative ease, so opt for WPA (Wi-Fi Protected Access), which uses 64-bit or 128-bit encryption. PSKs are Pre-Shared Keys, which provide stronger security than WEP or WPA. The encrypted keys are shared by the router and your Wi-Fi devices. The ...
... WEP (Wired Equivalent Privacy) keys can be cracked with relative ease, so opt for WPA (Wi-Fi Protected Access), which uses 64-bit or 128-bit encryption. PSKs are Pre-Shared Keys, which provide stronger security than WEP or WPA. The encrypted keys are shared by the router and your Wi-Fi devices. The ...
Senior Systems Administrator - Texarkana Independent School District
... 13. Conduct research on network products, services, protocols, and standards in support of network procurement and development efforts. 14. Develop, implement and maintain policies, procedures and plans for network resource administration, appropriate use, and disaster recovery. SUPERVISORY RESPONSI ...
... 13. Conduct research on network products, services, protocols, and standards in support of network procurement and development efforts. 14. Develop, implement and maintain policies, procedures and plans for network resource administration, appropriate use, and disaster recovery. SUPERVISORY RESPONSI ...
1 Gerd Keiser, Local Area Networks, 2nd ed., McGraw
... 11.11 ThresholdManager from Cisco (see http://www.cisco.com for details). Thresholds define the range in which one expects a network to perform. If these thresholds exceed or go below the expected bounds, these areas can be examined for potential problems. A network manager can create thresholds fo ...
... 11.11 ThresholdManager from Cisco (see http://www.cisco.com for details). Thresholds define the range in which one expects a network to perform. If these thresholds exceed or go below the expected bounds, these areas can be examined for potential problems. A network manager can create thresholds fo ...
fm fluidity
... Your passengers expect wireless high speed connectivity everywhere and FLUIDITY delivers. With our traffic optimization transmission protocol, Wi-Fi connectivity and content can now be offered to passengers more efficiently. Internet connectivity, traffic information to and from the train ...
... Your passengers expect wireless high speed connectivity everywhere and FLUIDITY delivers. With our traffic optimization transmission protocol, Wi-Fi connectivity and content can now be offered to passengers more efficiently. Internet connectivity, traffic information to and from the train ...
Assignment3-LeonardEhalt
... interface FastEthernet0/1 interface FastEthernet0/2 interface FastEthernet0/3 interface FastEthernet0/4 ...
... interface FastEthernet0/1 interface FastEthernet0/2 interface FastEthernet0/3 interface FastEthernet0/4 ...
ABET - Regis University: Academic Web Server for Faculty
... that prevents unauthorized users from accessing private networks • Technologies include: ▫ Static packet filtering ▫ Stateful inspection ▫ Network address translation (NAT) ▫ Application proxy filtering ...
... that prevents unauthorized users from accessing private networks • Technologies include: ▫ Static packet filtering ▫ Stateful inspection ▫ Network address translation (NAT) ▫ Application proxy filtering ...
FireWall-1 - Evolution Security Systems Ltd
... as well as consolidates multiple security policies in an architecture that scales to support thousands of policies. SmartMap™ allows security managers to validate the integrity of their security policy prior to deployment by providing a detailed, graphical map of an organization’s security deploymen ...
... as well as consolidates multiple security policies in an architecture that scales to support thousands of policies. SmartMap™ allows security managers to validate the integrity of their security policy prior to deployment by providing a detailed, graphical map of an organization’s security deploymen ...
Packet switched
... As in they are moved beyond there local connection If this is not true – then they are not routing • On this basis a unique address is still needed if there are multiple destinations but you may not need a IP address • A hardware address is used for these communications MAC • Point to point communic ...
... As in they are moved beyond there local connection If this is not true – then they are not routing • On this basis a unique address is still needed if there are multiple destinations but you may not need a IP address • A hardware address is used for these communications MAC • Point to point communic ...
SkyExtender DualBand
... backhaul, Wi-Fi can be deployed in dense coverage patterns, like blanketing the downtown area of a city, as well as being deployed in targeted locations such as hotzones or residences. This allows multiple distinct and separate Wi-Fi networks to connect to a high-capacity, redundant mesh backhaul to ...
... backhaul, Wi-Fi can be deployed in dense coverage patterns, like blanketing the downtown area of a city, as well as being deployed in targeted locations such as hotzones or residences. This allows multiple distinct and separate Wi-Fi networks to connect to a high-capacity, redundant mesh backhaul to ...
Lesson 1
... on the network to access and share information and data. Hardware sharing – one device connected to a network can serve the needs of many users. Software sharing – all users on the network can access a program from one central location. Collaborative environment – enables users to work together on ...
... on the network to access and share information and data. Hardware sharing – one device connected to a network can serve the needs of many users. Software sharing – all users on the network can access a program from one central location. Collaborative environment – enables users to work together on ...
NetDay Cyber Security Kit for Schools
... copies of confidential student and staff data; in fact, local, state and federal laws require that these records be protected from unauthorized release. As districts begin to store confidential data electronically, these same laws apply – so electronic data security should be a top priority for admi ...
... copies of confidential student and staff data; in fact, local, state and federal laws require that these records be protected from unauthorized release. As districts begin to store confidential data electronically, these same laws apply – so electronic data security should be a top priority for admi ...
network - CCIT131
... Networks offer a quick and easy way to share files directly. 2. Resource Sharing: ...
... Networks offer a quick and easy way to share files directly. 2. Resource Sharing: ...
Chapter04
... have not been made available through updates, are the most broad. After installing the current version of the operating system software on the computer the very next step should be to install the service pack (or packs). This will serve to update the software to the fullest extent. The second type i ...
... have not been made available through updates, are the most broad. After installing the current version of the operating system software on the computer the very next step should be to install the service pack (or packs). This will serve to update the software to the fullest extent. The second type i ...
Networks
... The Internet is worldwide and intended to be accessed by anybody. A global network connecting millions of computers. The best “known” network. More than 100 countries are linked into exchanges of data, news and opinions. The World Wide Web, or just "the Web," as ordinary people call it, is a subset ...
... The Internet is worldwide and intended to be accessed by anybody. A global network connecting millions of computers. The best “known” network. More than 100 countries are linked into exchanges of data, news and opinions. The World Wide Web, or just "the Web," as ordinary people call it, is a subset ...
BitLocker - Microsoft
... “After virus infections, businesses report unintended forwarding of e-mails and loss of mobile devices more frequently than they do any other security breach” Jupiter Research Report, 2004 ...
... “After virus infections, businesses report unintended forwarding of e-mails and loss of mobile devices more frequently than they do any other security breach” Jupiter Research Report, 2004 ...
CSIT560 Project Presentation
... multitude of information is obtained by analyzing networking parameters. ...
... multitude of information is obtained by analyzing networking parameters. ...
PPT - pantherFILE
... • Without trust, information systems cannot be built—too complex • Trust abuse – security holes come from what you trust – Trust in a system could be defined as the level of confidence in its integrity. – Nevertheless, just like it is hard to provide computer security with reasonable guarantees, it ...
... • Without trust, information systems cannot be built—too complex • Trust abuse – security holes come from what you trust – Trust in a system could be defined as the level of confidence in its integrity. – Nevertheless, just like it is hard to provide computer security with reasonable guarantees, it ...
Internet-based Research: Perspectives of IT
... • Provide server support, maintenance, and security for dedicated servers at a cost of $100 per server ...
... • Provide server support, maintenance, and security for dedicated servers at a cost of $100 per server ...
Security Overview
... •A security attack is any action that compromises the security of information (i.e. stored or in ...
... •A security attack is any action that compromises the security of information (i.e. stored or in ...
Focus area #6
... Functionality; ipv6, multicast, official IP-adresses, mobility etc. available only on parts of the campus network. Lack of efficient management tools covering all networking and services areas. Innovation by use of NRENs often stops somewhere in the campus organization. The unreleased potential for ...
... Functionality; ipv6, multicast, official IP-adresses, mobility etc. available only on parts of the campus network. Lack of efficient management tools covering all networking and services areas. Innovation by use of NRENs often stops somewhere in the campus organization. The unreleased potential for ...
LevelOne
... This Wi-Fi detector also allows the user to go online wirelessly and is designed to comply with IEEE 802.11g Wireless LAN standard. It is suitable for any laptop or desktop computer. ...
... This Wi-Fi detector also allows the user to go online wirelessly and is designed to comply with IEEE 802.11g Wireless LAN standard. It is suitable for any laptop or desktop computer. ...
System Administration
... and have the following characteristics: – Service to a large and diverse set of users. – Costs that are difficult t allocate to individual users. – Recurring need for new capital expenditures. – Significant operating costs for maintenance. ...
... and have the following characteristics: – Service to a large and diverse set of users. – Costs that are difficult t allocate to individual users. – Recurring need for new capital expenditures. – Significant operating costs for maintenance. ...
EHLANZENI DISTRICT MUNICIPALITY INTRUSION DETECTION
... This policy is designed both to protect the confidentiality of any data that may be stored on the mobile computer and to protect the organizational network from being infected by any hostile software when the mobile computer returns. This policy also considers wireless access. Scope This policy cove ...
... This policy is designed both to protect the confidentiality of any data that may be stored on the mobile computer and to protect the organizational network from being infected by any hostile software when the mobile computer returns. This policy also considers wireless access. Scope This policy cove ...
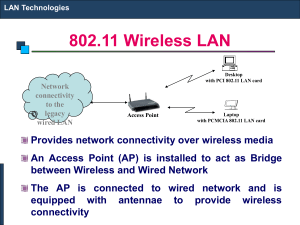
802.11 Wireless LAN
... between Wireless and Wired Network The AP is connected to wired network and is equipped with antennae to provide wireless connectivity ...
... between Wireless and Wired Network The AP is connected to wired network and is equipped with antennae to provide wireless connectivity ...
Wireless security
.jpg?width=300)
Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is a notoriously weak security standard. The password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP is an old IEEE 802.11 standard from 1999, which was outdated in 2003 by WPA, or Wi-Fi Protected Access. WPA was a quick alternative to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device that encrypts the network with a 256-bit key; the longer key length improves security over WEP.Many laptop computers have wireless cards pre-installed. The ability to enter a network while mobile has great benefits. However, wireless networking is prone to some security issues. Hackers have found wireless networks relatively easy to break into, and even use wireless technology to hack into wired networks. As a result, it is very important that enterprises define effective wireless security policies that guard against unauthorized access to important resources. Wireless Intrusion Prevention Systems (WIPS) or Wireless Intrusion Detection Systems (WIDS) are commonly used to enforce wireless security policies.The risks to users of wireless technology have increased as the service has become more popular. There were relatively few dangers when wireless technology was first introduced. Hackers had not yet had time to latch on to the new technology, and wireless networks were not commonly found in the work place. However, there are many security risks associated with the current wireless protocols and encryption methods, and in the carelessness and ignorance that exists at the user and corporate IT level. Hacking methods have become much more sophisticated and innovative with wireless access. Hacking has also become much easier and more accessible with easy-to-use Windows- or Linux-based tools being made available on the web at no charge.Some organizations that have no wireless access points installed do not feel that they need to address wireless security concerns. In-Stat MDR and META Group have estimated that 95% of all corporate laptop computers that were planned to be purchased in 2005 were equipped with wireless cards. Issues can arise in a supposedly non-wireless organization when a wireless laptop is plugged into the corporate network. A hacker could sit out in the parking lot and gather information from it through laptops and/or other devices, or even break in through this wireless card–equipped laptop and gain access to the wired network.