Data Security - Devi Ahilya Vishwavidyalaya
... Introduction Impact of information Need of Information Security. Objectives of Information Security. Areas of Information Security. Types of attackers ...
... Introduction Impact of information Need of Information Security. Objectives of Information Security. Areas of Information Security. Types of attackers ...
Document
... • Mobility: Allows locating them in the best place for receiving a more powerful signal. • May be used in any host. Only a USB port is needed. • If it is neccessary, they may pass from a host to another (only driver installation is needed) Disadvantages • Much more unstable than Wi-Fi PCI Cards. • ...
... • Mobility: Allows locating them in the best place for receiving a more powerful signal. • May be used in any host. Only a USB port is needed. • If it is neccessary, they may pass from a host to another (only driver installation is needed) Disadvantages • Much more unstable than Wi-Fi PCI Cards. • ...
Basic Networking Hardware
... A local area network that transmits over the air typically in an unlicensed frequency such as the 2.4GHz band. A wireless LAN does not require lining up devices for line of sight transmission. Wireless access points (base stations) are connected to an Ethernet hub or server and transmit a radio freq ...
... A local area network that transmits over the air typically in an unlicensed frequency such as the 2.4GHz band. A wireless LAN does not require lining up devices for line of sight transmission. Wireless access points (base stations) are connected to an Ethernet hub or server and transmit a radio freq ...
Spec Sheet - NetComm Wireless
... Enjoy extended WiFi coverage with high-speed WiFi N, or connect up to four wired devices via the Gigabit Ethernet ports. The device also features a USB 2.0 port for external hard drive storage or an alternate Internet source with a compatible 3G/4G USB modem. The VoIP phone port allows users to make ...
... Enjoy extended WiFi coverage with high-speed WiFi N, or connect up to four wired devices via the Gigabit Ethernet ports. The device also features a USB 2.0 port for external hard drive storage or an alternate Internet source with a compatible 3G/4G USB modem. The VoIP phone port allows users to make ...
Security Devices and Practices
... – It is vitally important that the security manager be able to see the organization’s systems and networks from the viewpoint of potential attackers – The security manager should develop a program using in-house resources, contractors, or an outsourced service provider to periodically scan his or he ...
... – It is vitally important that the security manager be able to see the organization’s systems and networks from the viewpoint of potential attackers – The security manager should develop a program using in-house resources, contractors, or an outsourced service provider to periodically scan his or he ...
ComView SM
... modem, a 10/100 Ethernet port, a suite of networking security features, and user-definable access control management software in a small, standalone hardware device. ComView SM is designed to give you complete control in managing dial-up access to your equipment. It does this by allowing you to use ...
... modem, a 10/100 Ethernet port, a suite of networking security features, and user-definable access control management software in a small, standalone hardware device. ComView SM is designed to give you complete control in managing dial-up access to your equipment. It does this by allowing you to use ...
Firewalls
... prevent denial of service attacks: SYN flooding: attacker establishes many bogus TCP connections, no resources left for “real” connections prevent illegal modification/access of internal data. e.g., attacker replaces CIA’s homepage with something else allow only authorized access to inside netwo ...
... prevent denial of service attacks: SYN flooding: attacker establishes many bogus TCP connections, no resources left for “real” connections prevent illegal modification/access of internal data. e.g., attacker replaces CIA’s homepage with something else allow only authorized access to inside netwo ...
IST101 - Test 6 – Ch 7,12 Test 6 consists of 50 questions drawn from
... What is done if a computer technician cannot solve a problem? A. The problem is moved to the end of the priority list and the technician moves on to the next problem on the priority list. B. The problem is shelved for the technician to look at the next day. C. The problem is referred to another tech ...
... What is done if a computer technician cannot solve a problem? A. The problem is moved to the end of the priority list and the technician moves on to the next problem on the priority list. B. The problem is shelved for the technician to look at the next day. C. The problem is referred to another tech ...
Slide 1
... that have a fast connection to the Internet via cable, satellite or DSL, the router can function as a hardware firewall. ...
... that have a fast connection to the Internet via cable, satellite or DSL, the router can function as a hardware firewall. ...
Linux+ Guide to Linux Certification
... – Link manager: Software that helps identify other Bluetooth devices, creates links between devices, and sends and ...
... – Link manager: Software that helps identify other Bluetooth devices, creates links between devices, and sends and ...
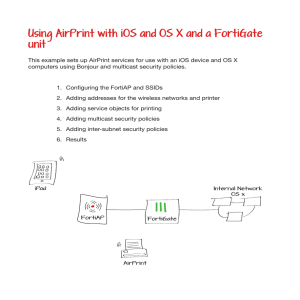
Using AirPrint with iOS and OS X and a FortiGate unit
... AirPrint printer and enable DHCP Server. ...
... AirPrint printer and enable DHCP Server. ...
Lecture19 - The University of Texas at Dallas
... – Layer 2 devices that filter traffic between segments based on MAC ...
... – Layer 2 devices that filter traffic between segments based on MAC ...
Document
... manufacturers designed hardware & software so each could communicate with each other. Originally only large computers had the ability to ...
... manufacturers designed hardware & software so each could communicate with each other. Originally only large computers had the ability to ...
Network Traffic Monitoring and Analysis
... Importance of Network Monitoring and Analysis: • Network monitoring is a difficult and demanding task that is a vital part of a Network Administrators job. • Network Administrators are constantly striving to maintain smooth operation of their networks. If a network were to be down even for a small ...
... Importance of Network Monitoring and Analysis: • Network monitoring is a difficult and demanding task that is a vital part of a Network Administrators job. • Network Administrators are constantly striving to maintain smooth operation of their networks. If a network were to be down even for a small ...
Security
... – Private key – kept secret by owner – Public key – distributed freely to all who wish to send – Generated by computer algorithm, so a mathematical relation exists between them ... however ... – It is computationally difficult to determine the private key from the public key, even with knowledge of ...
... – Private key – kept secret by owner – Public key – distributed freely to all who wish to send – Generated by computer algorithm, so a mathematical relation exists between them ... however ... – It is computationally difficult to determine the private key from the public key, even with knowledge of ...
Corporate Overview - Network Instruments
... 85% are involved with security investigations Engaged in multiple facets of security • 65% implementing preventative measures • 58% investigating attacks • 50% validating security tool configurations 50% indicated correlating security issues with network performance to be their top challenge 44% cit ...
... 85% are involved with security investigations Engaged in multiple facets of security • 65% implementing preventative measures • 58% investigating attacks • 50% validating security tool configurations 50% indicated correlating security issues with network performance to be their top challenge 44% cit ...
Secure your remote access with VASCO and
... while remaining easy-to-use When employees use their PC, they want to read e-mail, use software and documents, access files on the corporate network, work with applications and access websites. With the workforce becoming more mobile, the employees want to do all this anywhere and any time. SSL VPN ...
... while remaining easy-to-use When employees use their PC, they want to read e-mail, use software and documents, access files on the corporate network, work with applications and access websites. With the workforce becoming more mobile, the employees want to do all this anywhere and any time. SSL VPN ...
Local Area Networks
... • Shared data and programs can be stored on a central network server. A server that stores data files may be called a file server. • Managers may assign access rights to users. Some users may only be able to read data, others may be able to make changes to existing files. ...
... • Shared data and programs can be stored on a central network server. A server that stores data files may be called a file server. • Managers may assign access rights to users. Some users may only be able to read data, others may be able to make changes to existing files. ...
Document
... even controls it entirely. • It is made up of many smaller networks. • These smaller networks are often owned and managed by a person or organization. • The Internet, then, is really defined by how connections can be made between these networks. ...
... even controls it entirely. • It is made up of many smaller networks. • These smaller networks are often owned and managed by a person or organization. • The Internet, then, is really defined by how connections can be made between these networks. ...
N4Less17.pps - GEOCITIES.ws
... • Shared data and programs can be stored on a central network server. A server that stores data files may be called a file server. • Managers may assign access rights to users. Some users may only be able to read data, others may be able to make changes to existing files. ...
... • Shared data and programs can be stored on a central network server. A server that stores data files may be called a file server. • Managers may assign access rights to users. Some users may only be able to read data, others may be able to make changes to existing files. ...
Lecture #1 Introduction to Mobile Communication
... simulated, thus attracting calls from mobile phones ...
... simulated, thus attracting calls from mobile phones ...
Document
... Users may have multiple identities: work and private in same equipment Users may have multiple terminals with different capabilities ...
... Users may have multiple identities: work and private in same equipment Users may have multiple terminals with different capabilities ...
Symbian - T-Dose
... User (power user) • Wants full access to the system • Wants powerful apps • (Gets f##ed most of the time) ...
... User (power user) • Wants full access to the system • Wants powerful apps • (Gets f##ed most of the time) ...
Wireless security
.jpg?width=300)
Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is a notoriously weak security standard. The password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP is an old IEEE 802.11 standard from 1999, which was outdated in 2003 by WPA, or Wi-Fi Protected Access. WPA was a quick alternative to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device that encrypts the network with a 256-bit key; the longer key length improves security over WEP.Many laptop computers have wireless cards pre-installed. The ability to enter a network while mobile has great benefits. However, wireless networking is prone to some security issues. Hackers have found wireless networks relatively easy to break into, and even use wireless technology to hack into wired networks. As a result, it is very important that enterprises define effective wireless security policies that guard against unauthorized access to important resources. Wireless Intrusion Prevention Systems (WIPS) or Wireless Intrusion Detection Systems (WIDS) are commonly used to enforce wireless security policies.The risks to users of wireless technology have increased as the service has become more popular. There were relatively few dangers when wireless technology was first introduced. Hackers had not yet had time to latch on to the new technology, and wireless networks were not commonly found in the work place. However, there are many security risks associated with the current wireless protocols and encryption methods, and in the carelessness and ignorance that exists at the user and corporate IT level. Hacking methods have become much more sophisticated and innovative with wireless access. Hacking has also become much easier and more accessible with easy-to-use Windows- or Linux-based tools being made available on the web at no charge.Some organizations that have no wireless access points installed do not feel that they need to address wireless security concerns. In-Stat MDR and META Group have estimated that 95% of all corporate laptop computers that were planned to be purchased in 2005 were equipped with wireless cards. Issues can arise in a supposedly non-wireless organization when a wireless laptop is plugged into the corporate network. A hacker could sit out in the parking lot and gather information from it through laptops and/or other devices, or even break in through this wireless card–equipped laptop and gain access to the wired network.