Firewalking
... • All the work of first gen firewalls but now with more transport layer • Examine each packet as well as its position in the data stream • Records the “state” of the connection ...
... • All the work of first gen firewalls but now with more transport layer • Examine each packet as well as its position in the data stream • Records the “state” of the connection ...
Electronic Commerce
... One advantage of the bus network is that if one node goes down the network still functions One disadvantage of the bus network is it can not travel as long a distance as say a ring network due to the diminishing signal strength Ethernet 10Base-2 and 10Base-5 use the bus ...
... One advantage of the bus network is that if one node goes down the network still functions One disadvantage of the bus network is it can not travel as long a distance as say a ring network due to the diminishing signal strength Ethernet 10Base-2 and 10Base-5 use the bus ...
Chapter Answers to end-of
... 2. Explain the difference between peer-to-peer and client/server networks. In a peer-to-peer network, all the computers on the network are equals, and there is no file server. Each computer user decides which, if any, files will be accessible to other users on the network. Although peer-topeer netwo ...
... 2. Explain the difference between peer-to-peer and client/server networks. In a peer-to-peer network, all the computers on the network are equals, and there is no file server. Each computer user decides which, if any, files will be accessible to other users on the network. Although peer-topeer netwo ...
Wireless Communications: Networking and - Assets
... Data Units layer by layer is given in Figure 1.6. In the message exchange between two end-systems represented by Application X (sender) and Application Y (receiver), User Data is encapsulated by the Application Header (AH) to create an Application PDU (A-PDU). Similarly, operations take place at the ...
... Data Units layer by layer is given in Figure 1.6. In the message exchange between two end-systems represented by Application X (sender) and Application Y (receiver), User Data is encapsulated by the Application Header (AH) to create an Application PDU (A-PDU). Similarly, operations take place at the ...
Wireless Communications: Networking and Management - Beck-Shop
... Data Units layer by layer is given in Figure 1.6. In the message exchange between two end-systems represented by Application X (sender) and Application Y (receiver), User Data is encapsulated by the Application Header (AH) to create an Application PDU (A-PDU). Similarly, operations take place at the ...
... Data Units layer by layer is given in Figure 1.6. In the message exchange between two end-systems represented by Application X (sender) and Application Y (receiver), User Data is encapsulated by the Application Header (AH) to create an Application PDU (A-PDU). Similarly, operations take place at the ...
Presentazione di PowerPoint - Micrel Lab @ DEIS
... • 79 carriers spaced 1 MHz, in the band 2400-2483,5 MHz • the channel is divided into time slots (625us slot 1600 hop/sec) • a TDD scheme is used where master and slave alternatively transmit. • all Bluetooth units participating in the piconet are time- and hopsynchronized to the channel • Automat ...
... • 79 carriers spaced 1 MHz, in the band 2400-2483,5 MHz • the channel is divided into time slots (625us slot 1600 hop/sec) • a TDD scheme is used where master and slave alternatively transmit. • all Bluetooth units participating in the piconet are time- and hopsynchronized to the channel • Automat ...
abstract - Chennaisunday.com
... the Internet. To accommodate the scale of transactions across the Internet, some of ...
... the Internet. To accommodate the scale of transactions across the Internet, some of ...
Bilkent University - Networking and Systems Research Group
... 1. Introduction.........................................................................................................................................2 2. Research Conducted……………………………………………………………………………………………………………………….2 2.1. Setting Up an Ad-Hoc Network............................................ ...
... 1. Introduction.........................................................................................................................................2 2. Research Conducted……………………………………………………………………………………………………………………….2 2.1. Setting Up an Ad-Hoc Network............................................ ...
CWSA_Session1_Nita-Rotaru - The Center for Wireless Systems
... of access control can translate into degradation of service. Confidentiality: medium is open, vulnerable to eavesdropping. Trust: multi-hop networks, nodes rely on un-trusted nodes to transport data. Physical security: wireless devices are more likely to be stolen, data get compromised or an a ...
... of access control can translate into degradation of service. Confidentiality: medium is open, vulnerable to eavesdropping. Trust: multi-hop networks, nodes rely on un-trusted nodes to transport data. Physical security: wireless devices are more likely to be stolen, data get compromised or an a ...
A Framework for Evaluating the Best Achievable
... resource allocation schemes. Such classes utilize mobility, topology control or cross-layer design in addition to route selection. ...
... resource allocation schemes. Such classes utilize mobility, topology control or cross-layer design in addition to route selection. ...
Eastern Michigan University - Emunix Documentation on the Web
... It may be impossible to make sure that no one uses sniffing packages against you, but it is ...
... It may be impossible to make sure that no one uses sniffing packages against you, but it is ...
SoftwareFreedomDay-S.. - The University of Sydney
... Using the wireless to communicate between nodes is the most costly operation on the SunSPOTs WSN nodes should be deployed once and last a long time without having to be physically altered ...
... Using the wireless to communicate between nodes is the most costly operation on the SunSPOTs WSN nodes should be deployed once and last a long time without having to be physically altered ...
CEN 4007C Computer Networks Fundamentals Instructor
... to scale to millions of users. Routers are aggregated into autonomous systems (ASs). Within an AS, all routers run the same intra-AS routing protocol. Special gateway routers in the various ASs run the inter-autonomous system routing protocol that determines the routing paths among the ASs. The prob ...
... to scale to millions of users. Routers are aggregated into autonomous systems (ASs). Within an AS, all routers run the same intra-AS routing protocol. Special gateway routers in the various ASs run the inter-autonomous system routing protocol that determines the routing paths among the ASs. The prob ...
Wireless Communications and Mobile Computing - MAP-i
... and they aim at offering telecom services through multiple access technologies such as, Ethernet, WLAN, WMAN, UMTS, and DVB. As a result, the user becomes always connected to his operator and to the Internet, most of the times through a high bit rate connection. The access flexibility demands a unif ...
... and they aim at offering telecom services through multiple access technologies such as, Ethernet, WLAN, WMAN, UMTS, and DVB. As a result, the user becomes always connected to his operator and to the Internet, most of the times through a high bit rate connection. The access flexibility demands a unif ...
Your future is Bright Blue!
... • An easy-to-use interface • No need for a dedicated PC or security network It’s just like accessing a website Training takes just minutes When used with Schlage VIP or wireless locks, there’s no need for additional door hardware Flashable firmware means easy upgrades It’s the most cost-effective so ...
... • An easy-to-use interface • No need for a dedicated PC or security network It’s just like accessing a website Training takes just minutes When used with Schlage VIP or wireless locks, there’s no need for additional door hardware Flashable firmware means easy upgrades It’s the most cost-effective so ...
com223-chapter 5
... Minimize number of LAN protocols that must cross each router Decreases the work routers must perform Enables routers to process traffic faster Does not create unnecessary traffic on network ...
... Minimize number of LAN protocols that must cross each router Decreases the work routers must perform Enables routers to process traffic faster Does not create unnecessary traffic on network ...
Introduction - Eastern Illinois University
... get a temporary IP address from an autoconfiguration server. (b) The client computer gets back a temporary IP address to use for communications with other computers on the Internet. ( c) The client may also get the DNS server’s IP address, the default gateway’s (or ...
... get a temporary IP address from an autoconfiguration server. (b) The client computer gets back a temporary IP address to use for communications with other computers on the Internet. ( c) The client may also get the DNS server’s IP address, the default gateway’s (or ...
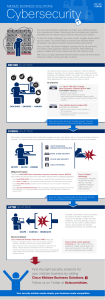
View the graphic
... You face unprecedented challenges to protect your midsize business from cybersecurity threats. New trends such as mobility and cloud are changing how you need to secure devices, data and your network. To deal with these challenges, you need a smart, scalable threat-centric security model. This model ...
... You face unprecedented challenges to protect your midsize business from cybersecurity threats. New trends such as mobility and cloud are changing how you need to secure devices, data and your network. To deal with these challenges, you need a smart, scalable threat-centric security model. This model ...
8[1]. Chapter 9 Norton
... Networking is a group of technologies working together. These technologies include: Media is the wiring that connects the computers 2. Hardware needs to be installed to connect the media 3. Software needs to be written to handle networks ...
... Networking is a group of technologies working together. These technologies include: Media is the wiring that connects the computers 2. Hardware needs to be installed to connect the media 3. Software needs to be written to handle networks ...
Linux Networking
... Name resolution configuration is done in the /etc/resolv.conf file. If the domain search field is set to usu.edu then you can access: cc.usu.edu as just cc. If you want to contact www.cs.usu.edu you would have to use www.cs If the domain search field is usu.edu and cs.usu.edu then you can access www ...
... Name resolution configuration is done in the /etc/resolv.conf file. If the domain search field is set to usu.edu then you can access: cc.usu.edu as just cc. If you want to contact www.cs.usu.edu you would have to use www.cs If the domain search field is usu.edu and cs.usu.edu then you can access www ...
Analysis of Attack - FSU Computer Science
... Uses IP spoofing and broadcasting to send a ping to a group of hosts on a network When a host is pinged it sends back ICMP message traffic information indicating status to the originator Once a broadcast is sent to the network, all hosts will answer back to the ping which results in an overload of t ...
... Uses IP spoofing and broadcasting to send a ping to a group of hosts on a network When a host is pinged it sends back ICMP message traffic information indicating status to the originator Once a broadcast is sent to the network, all hosts will answer back to the ping which results in an overload of t ...
Hands-On Ethical Hacking and Network Security
... Wi-Fi Protected Access (WPA) • Specified in the 802.11i standard • It is the replacement for WEP • WPA improves encryption by using Temporal Key Integrity Protocol (TKIP) • TKIP is composed of four enhancements ...
... Wi-Fi Protected Access (WPA) • Specified in the 802.11i standard • It is the replacement for WEP • WPA improves encryption by using Temporal Key Integrity Protocol (TKIP) • TKIP is composed of four enhancements ...
No Slide Title
... • Forward packets based on the Layer 3 header information. • Can limit or secure network traffic based on identifiable attributes within each packet. • Switch packets to the appropriate interface based on the destination IP address. • Can perform bridging and routing. ...
... • Forward packets based on the Layer 3 header information. • Can limit or secure network traffic based on identifiable attributes within each packet. • Switch packets to the appropriate interface based on the destination IP address. • Can perform bridging and routing. ...
Firewalls
... network sends an application request to the firewall and the firewall allows the request through to the outside Internet, a sniffer just outside the firewall may sniff the packet and it will reveal the source IP address. The host then may be a potential victim for attack. In IP address hiding, the f ...
... network sends an application request to the firewall and the firewall allows the request through to the outside Internet, a sniffer just outside the firewall may sniff the packet and it will reveal the source IP address. The host then may be a potential victim for attack. In IP address hiding, the f ...
Secure Ad Hoc Networking
... Mobile hosts collaboratively support the ad hoc network operation without necessarily pursuing a common objective or running the same application. The network membership and connectivity change frequently, as nodes may join and leave the network without prior notice, e.g., due to mobility or because ...
... Mobile hosts collaboratively support the ad hoc network operation without necessarily pursuing a common objective or running the same application. The network membership and connectivity change frequently, as nodes may join and leave the network without prior notice, e.g., due to mobility or because ...
Wireless security
.jpg?width=300)
Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is a notoriously weak security standard. The password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP is an old IEEE 802.11 standard from 1999, which was outdated in 2003 by WPA, or Wi-Fi Protected Access. WPA was a quick alternative to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device that encrypts the network with a 256-bit key; the longer key length improves security over WEP.Many laptop computers have wireless cards pre-installed. The ability to enter a network while mobile has great benefits. However, wireless networking is prone to some security issues. Hackers have found wireless networks relatively easy to break into, and even use wireless technology to hack into wired networks. As a result, it is very important that enterprises define effective wireless security policies that guard against unauthorized access to important resources. Wireless Intrusion Prevention Systems (WIPS) or Wireless Intrusion Detection Systems (WIDS) are commonly used to enforce wireless security policies.The risks to users of wireless technology have increased as the service has become more popular. There were relatively few dangers when wireless technology was first introduced. Hackers had not yet had time to latch on to the new technology, and wireless networks were not commonly found in the work place. However, there are many security risks associated with the current wireless protocols and encryption methods, and in the carelessness and ignorance that exists at the user and corporate IT level. Hacking methods have become much more sophisticated and innovative with wireless access. Hacking has also become much easier and more accessible with easy-to-use Windows- or Linux-based tools being made available on the web at no charge.Some organizations that have no wireless access points installed do not feel that they need to address wireless security concerns. In-Stat MDR and META Group have estimated that 95% of all corporate laptop computers that were planned to be purchased in 2005 were equipped with wireless cards. Issues can arise in a supposedly non-wireless organization when a wireless laptop is plugged into the corporate network. A hacker could sit out in the parking lot and gather information from it through laptops and/or other devices, or even break in through this wireless card–equipped laptop and gain access to the wired network.
















![8[1]. Chapter 9 Norton](http://s1.studyres.com/store/data/008740653_1-fe1d78b3a4d5882ed6aebaaa8846aa3c-300x300.png)