Chapter 15 Local Area Networks
... • RTS alerts all stations within range of source that exchange is under way • CTS alerts all stations within range of destination • Stations re ...
... • RTS alerts all stations within range of source that exchange is under way • CTS alerts all stations within range of destination • Stations re ...
1-3_GSM_CDMA_3G4G_08..
... • Multiple BSs can be configured to form a cellular wireless network. The radius of a cell can be 2-40 km while practical one is around 7-8 km with data rate as 70 Mbps per RF channel at a BS • A point-to-point (P2P) or mesh topology also supported by the IEEE 802.16 standard ...
... • Multiple BSs can be configured to form a cellular wireless network. The radius of a cell can be 2-40 km while practical one is around 7-8 km with data rate as 70 Mbps per RF channel at a BS • A point-to-point (P2P) or mesh topology also supported by the IEEE 802.16 standard ...
IP Addresses - Paladin Group LLC
... Do you still have to route between VLANS?* Two different VLAN protocols 802.1Q*, or Cisco ISL* for trunking between switches • Use VLANS for convenience and for creating network security zones. One use is to create “dead” or “restricted” networks unless authentication is done via 802.1x ...
... Do you still have to route between VLANS?* Two different VLAN protocols 802.1Q*, or Cisco ISL* for trunking between switches • Use VLANS for convenience and for creating network security zones. One use is to create “dead” or “restricted” networks unless authentication is done via 802.1x ...
Intelligent Transport Systems
... Standardisation as required by stakeholders and users Automotive industry – Road operators – Public operators Cooperative systems to promote Safety on the roads Cooperative systems to promote Traffic efficiency Achieving environmental improvements – green agenda.. ...
... Standardisation as required by stakeholders and users Automotive industry – Road operators – Public operators Cooperative systems to promote Safety on the roads Cooperative systems to promote Traffic efficiency Achieving environmental improvements – green agenda.. ...
XML Security Standards — Overview for the Non - Events
... Integrity – prevent undetected modification of data Confidentiality – prevent unauthorized reading of data Audit – preserve evidence for accountability Administration – control configuration Others … ...
... Integrity – prevent undetected modification of data Confidentiality – prevent unauthorized reading of data Audit – preserve evidence for accountability Administration – control configuration Others … ...
Harassment Monitoring System Using Android Smartphone
... applications run as Linux users and thus are separated from each other. A security hole in one application does not affect other applications. However, there is also a concept of inter-process communication (IPC) between different applications, or between the Android components of the applications s ...
... applications run as Linux users and thus are separated from each other. A security hole in one application does not affect other applications. However, there is also a concept of inter-process communication (IPC) between different applications, or between the Android components of the applications s ...
GIT 335 Lecture 6 - Arizona State University
... • Problem: internet was begun to foster collaboration among universities and scientists. They trusted each other. No security was built into the internet. • Problem: the internet is open-access and is used by some people who are not trustworthy, who take advantage of the lack of built-in safeguards. ...
... • Problem: internet was begun to foster collaboration among universities and scientists. They trusted each other. No security was built into the internet. • Problem: the internet is open-access and is used by some people who are not trustworthy, who take advantage of the lack of built-in safeguards. ...
ATIS NGN
... Other networks, and upper layer functional entities (FEs) • Session admission, authentication and enforcement of policy are executed via the “Session and Policy” control functions • Value-added and enhanced services are hosted in servers in the “Applications and Service Capability” functions • Servi ...
... Other networks, and upper layer functional entities (FEs) • Session admission, authentication and enforcement of policy are executed via the “Session and Policy” control functions • Value-added and enhanced services are hosted in servers in the “Applications and Service Capability” functions • Servi ...
Not another Perimeter Presentation - ISSA
... Preserve bandwidth, for corporate business Preserve access to unauthenticated but authorized information (e.g. public web site) ...
... Preserve bandwidth, for corporate business Preserve access to unauthenticated but authorized information (e.g. public web site) ...
Undergraduate Research Opportunity
... (1) From the two approaches above, the final results tell us that once we take hidden terminal into account, the transport capacity will be lower. This can be predicted by our intuition since with more restrictions, the wireless network will be less activated. (2) The results deduced from two approa ...
... (1) From the two approaches above, the final results tell us that once we take hidden terminal into account, the transport capacity will be lower. This can be predicted by our intuition since with more restrictions, the wireless network will be less activated. (2) The results deduced from two approa ...
CSCI6268L10 - Computer Science
... • Our local routing table (on host of user1) is not going to have a route to IP of user2 – Routing table will therefore send our packet to the gateway – Gateway is the machine/router on the “edge” of the network responsible for processing all incoming/outgoing traffic from/to the LAN • NAT boxing, f ...
... • Our local routing table (on host of user1) is not going to have a route to IP of user2 – Routing table will therefore send our packet to the gateway – Gateway is the machine/router on the “edge” of the network responsible for processing all incoming/outgoing traffic from/to the LAN • NAT boxing, f ...
Reliable network solutions enabling Smart Grid Applications
... • TT/MSR – All time transfer signaling in control plane and un-accessible to users (DoS on the IP trunk level must still be considered) Security issues especially important since much of the driving forces for implementing fiber based time transport instead of using GPS/GLONASS is just – security… ...
... • TT/MSR – All time transfer signaling in control plane and un-accessible to users (DoS on the IP trunk level must still be considered) Security issues especially important since much of the driving forces for implementing fiber based time transport instead of using GPS/GLONASS is just – security… ...
CSCI6268L10 - Computer Science
... • Our local routing table (on host of user1) is not going to have a route to IP of user2 – Routing table will therefore send our packet to the gateway – Gateway is the machine/router on the “edge” of the network responsible for processing all incoming/outgoing traffic from/to the LAN • NAT boxing, f ...
... • Our local routing table (on host of user1) is not going to have a route to IP of user2 – Routing table will therefore send our packet to the gateway – Gateway is the machine/router on the “edge” of the network responsible for processing all incoming/outgoing traffic from/to the LAN • NAT boxing, f ...
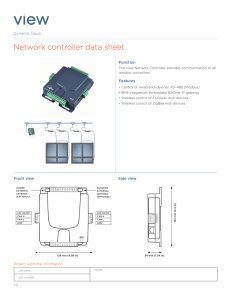
network controller data sheet
... • Operating Temperature: 0°C (32°F) to 60°C (140°F) • Storage Temperature: –20°C (–4°F) to 60°C (140°F) • Relative Humidity: 0 to 90% non–condensing ...
... • Operating Temperature: 0°C (32°F) to 60°C (140°F) • Storage Temperature: –20°C (–4°F) to 60°C (140°F) • Relative Humidity: 0 to 90% non–condensing ...
Wi-Fi Service Delivery Platform
... • DHCP / NAT Server: supports DHCP, static IP addresses, and PPPoE on the Internet side and performs network address translation • Built-in Web Server: provides secure registration and login, walled garden support and customized branding for location • Multiple SSIDs: enables multiple service provid ...
... • DHCP / NAT Server: supports DHCP, static IP addresses, and PPPoE on the Internet side and performs network address translation • Built-in Web Server: provides secure registration and login, walled garden support and customized branding for location • Multiple SSIDs: enables multiple service provid ...
DHCP snooping
... IP Source Guard IP Source Guard is enabled on a DHCP snooping untrusted Layer 2 port For each untrusted Layer 2 port, there are two levels of IP traffic security filtering: Source IP address filter: IP traffic is filtered based on its source IP address. Only IP traffic with a source IP addres ...
... IP Source Guard IP Source Guard is enabled on a DHCP snooping untrusted Layer 2 port For each untrusted Layer 2 port, there are two levels of IP traffic security filtering: Source IP address filter: IP traffic is filtered based on its source IP address. Only IP traffic with a source IP addres ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... Secure lock administration is possible by combining personal verification tools such as fingerprint ID or other biometric in the mobile terminal. ...
... Secure lock administration is possible by combining personal verification tools such as fingerprint ID or other biometric in the mobile terminal. ...
practice_assignment_networking
... 20. What is the difference between video streaming and video download? 21. What is the difference between file upload and file download? Name the devices that get involved in uploading or downloading of files. 22. What is meant by a protocol? Why do you need to have protocols? 23. What would you wan ...
... 20. What is the difference between video streaming and video download? 21. What is the difference between file upload and file download? Name the devices that get involved in uploading or downloading of files. 22. What is meant by a protocol? Why do you need to have protocols? 23. What would you wan ...
Hands-on Networking Fundamentals, 2ed
... the problems can be quickly located and repaired. You might also emphasize that it is important to keep this information up to date as the network grows. Most intelligent network devices, such as hubs, switches, and routers, will provide network management applications either locally or remotely tha ...
... the problems can be quickly located and repaired. You might also emphasize that it is important to keep this information up to date as the network grows. Most intelligent network devices, such as hubs, switches, and routers, will provide network management applications either locally or remotely tha ...
Access Security Requirements
... 5.3 Administrative access to firewalls and servers must be performed through a secure internal wired connection only. 5.4 Any stand-alone computers that directly access the Internet must have a desktop firewall deployed that is installed and configured to block unnecessary/unused ports, services, an ...
... 5.3 Administrative access to firewalls and servers must be performed through a secure internal wired connection only. 5.4 Any stand-alone computers that directly access the Internet must have a desktop firewall deployed that is installed and configured to block unnecessary/unused ports, services, an ...
CH07-CompSec2e - MCST-CS
... Source Address Spoofing use forged source addresses usually via the raw socket interface on operating systems makes attacking systems harder to identify attacker generates large volumes of packets that have the ...
... Source Address Spoofing use forged source addresses usually via the raw socket interface on operating systems makes attacking systems harder to identify attacker generates large volumes of packets that have the ...
Ch_32 - UCF EECS
... must be discarded (not forwarded). Figure 32.33 shows an example of a filtering table for this kind of a firewall. ...
... must be discarded (not forwarded). Figure 32.33 shows an example of a filtering table for this kind of a firewall. ...
Security in Wireless Networks
... • Weak IVs in form of B+3:FF:N – B Refers to the Byte of the Key – FF is Weak Middle Byte of all 1s – N is any value from 0 to 255 ...
... • Weak IVs in form of B+3:FF:N – B Refers to the Byte of the Key – FF is Weak Middle Byte of all 1s – N is any value from 0 to 255 ...
GK2411581160
... hot research area in recent years, with the objective to achieve as high throughput as possible over the network [2]. As we know while transmitting packets or data in the network, to minimize the number of link layer transmission including retransmission in a wireless mesh network is major issue and ...
... hot research area in recent years, with the objective to achieve as high throughput as possible over the network [2]. As we know while transmitting packets or data in the network, to minimize the number of link layer transmission including retransmission in a wireless mesh network is major issue and ...
Figure 32.33: Packet
... must be discarded (not forwarded). Figure 32.33 shows an example of a filtering table for this kind of a firewall. ...
... must be discarded (not forwarded). Figure 32.33 shows an example of a filtering table for this kind of a firewall. ...
Wireless security
.jpg?width=300)
Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is a notoriously weak security standard. The password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP is an old IEEE 802.11 standard from 1999, which was outdated in 2003 by WPA, or Wi-Fi Protected Access. WPA was a quick alternative to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device that encrypts the network with a 256-bit key; the longer key length improves security over WEP.Many laptop computers have wireless cards pre-installed. The ability to enter a network while mobile has great benefits. However, wireless networking is prone to some security issues. Hackers have found wireless networks relatively easy to break into, and even use wireless technology to hack into wired networks. As a result, it is very important that enterprises define effective wireless security policies that guard against unauthorized access to important resources. Wireless Intrusion Prevention Systems (WIPS) or Wireless Intrusion Detection Systems (WIDS) are commonly used to enforce wireless security policies.The risks to users of wireless technology have increased as the service has become more popular. There were relatively few dangers when wireless technology was first introduced. Hackers had not yet had time to latch on to the new technology, and wireless networks were not commonly found in the work place. However, there are many security risks associated with the current wireless protocols and encryption methods, and in the carelessness and ignorance that exists at the user and corporate IT level. Hacking methods have become much more sophisticated and innovative with wireless access. Hacking has also become much easier and more accessible with easy-to-use Windows- or Linux-based tools being made available on the web at no charge.Some organizations that have no wireless access points installed do not feel that they need to address wireless security concerns. In-Stat MDR and META Group have estimated that 95% of all corporate laptop computers that were planned to be purchased in 2005 were equipped with wireless cards. Issues can arise in a supposedly non-wireless organization when a wireless laptop is plugged into the corporate network. A hacker could sit out in the parking lot and gather information from it through laptops and/or other devices, or even break in through this wireless card–equipped laptop and gain access to the wired network.