AR G3 Series Enterprise Routers
... The ARs provide the highest port density in the industry and include flexible service interface card (SIC) slots, allowing enterprise customers to connect to LAN, WAN, or wireless networks. The ARs provide the most economical enterprise network solutions. ...
... The ARs provide the highest port density in the industry and include flexible service interface card (SIC) slots, allowing enterprise customers to connect to LAN, WAN, or wireless networks. The ARs provide the most economical enterprise network solutions. ...
Computer Networks
... • Determine where one frame/chunk of data starts and ends (be able to distinguish 000 from a transmission line gone dead) ...
... • Determine where one frame/chunk of data starts and ends (be able to distinguish 000 from a transmission line gone dead) ...
Introduction to Networking
... We use many different types of networks. For example, schools and businesses usually have their own private networks that can only be accessed while in the building. This type of network, known as a LAN (Local Area Network) is sometimes referred to as an Intranet, but most people just call them “The ...
... We use many different types of networks. For example, schools and businesses usually have their own private networks that can only be accessed while in the building. This type of network, known as a LAN (Local Area Network) is sometimes referred to as an Intranet, but most people just call them “The ...
Current Issues in Maintaining a Secure System
... firewalls and spyware to help protect your computer from hackers. • To explain other terms frequently used with system security and examples of how they fit into the big picture. ...
... firewalls and spyware to help protect your computer from hackers. • To explain other terms frequently used with system security and examples of how they fit into the big picture. ...
Data Communication Network
... If the network in question is the Internet or an Intranet, many physical network nodes are host computers, also known as Internet nodes, identified by an IP address, and all hosts are physical network nodes. However, some datalink layer devices such as switches, bridges and WLAN access points do not ...
... If the network in question is the Internet or an Intranet, many physical network nodes are host computers, also known as Internet nodes, identified by an IP address, and all hosts are physical network nodes. However, some datalink layer devices such as switches, bridges and WLAN access points do not ...
MAN Metropolitan Area Network = A metropolitan
... WAN Wide Area Network = A wide area network is a telecommunicationsnetwork or computer networ that extends over a large geographical distance. Wide area networks are often established with leased telecommunication circuits. CAN. Controller Area Network = Bosch originally developed the Controller Are ...
... WAN Wide Area Network = A wide area network is a telecommunicationsnetwork or computer networ that extends over a large geographical distance. Wide area networks are often established with leased telecommunication circuits. CAN. Controller Area Network = Bosch originally developed the Controller Are ...
Class Notes #1
... exchange information with each other in a meaningful way. – Computer networks may link computers that are all of the same type (homogeneous networks), or they may link computers of several different types (heterogeneous networks) – Size of the network: same room, same floor, same building, same camp ...
... exchange information with each other in a meaningful way. – Computer networks may link computers that are all of the same type (homogeneous networks), or they may link computers of several different types (heterogeneous networks) – Size of the network: same room, same floor, same building, same camp ...
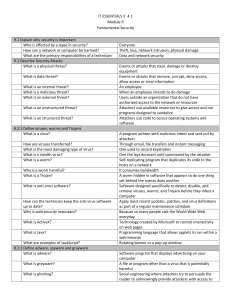
IT ESSENTIALS V. 4.1 Module 9 Fundamental Security 9.1 Explain
... Escort all visitors Lock your computer when you leave your desk Do not let anyone follow you through a door that requires an access card Randomly opens TCP ports, typing up network equipment with large amount of false requests, causing sessions to be denied to others Gains access to resources on dev ...
... Escort all visitors Lock your computer when you leave your desk Do not let anyone follow you through a door that requires an access card Randomly opens TCP ports, typing up network equipment with large amount of false requests, causing sessions to be denied to others Gains access to resources on dev ...
CryptoPro - Applied Security GmbH
... established authentication methods like user-ID/password, smartcard/PIN and biometry for multi-user operation. The encryption of the hard disk as well as its recovery mechanisms will be performed by BitLocker, while the authentication of different users including the required helpdesk methods are ha ...
... established authentication methods like user-ID/password, smartcard/PIN and biometry for multi-user operation. The encryption of the hard disk as well as its recovery mechanisms will be performed by BitLocker, while the authentication of different users including the required helpdesk methods are ha ...
Lecture 9 - USC`s Center for Computer Systems Security
... – Pushback only works in contiguous deployment – Collateral damage is inflicted by response, whenever attack is not clearly separable – Requires modification of existing core routers ...
... – Pushback only works in contiguous deployment – Collateral damage is inflicted by response, whenever attack is not clearly separable – Requires modification of existing core routers ...
A. LAN models can be configured as either “client / server (domain)”
... performed at the local workstation. In a peer-to-peer network, all workstations perform a dual role of “client” and “server”. The local PC designates what resources (files, printers, etc.) are to be shared and then makes them available to the other PC peers in the network. Because the workstations i ...
... performed at the local workstation. In a peer-to-peer network, all workstations perform a dual role of “client” and “server”. The local PC designates what resources (files, printers, etc.) are to be shared and then makes them available to the other PC peers in the network. Because the workstations i ...
Multiple Processor Systems
... – Link – physically interfacing with communication medium to move a packet over a link; Ethernet, WiFi 802.11 – Network – moving packets over multiple links, from src to destination; IP (Internet Protocol) – Transport – provides a msg service to apps; apps don’t need to care that communication is ...
... – Link – physically interfacing with communication medium to move a packet over a link; Ethernet, WiFi 802.11 – Network – moving packets over multiple links, from src to destination; IP (Internet Protocol) – Transport – provides a msg service to apps; apps don’t need to care that communication is ...
pptx
... Implementing a functionality at a lower level should have minimum performance impact on the applications that do not use the functionality ...
... Implementing a functionality at a lower level should have minimum performance impact on the applications that do not use the functionality ...
Certification Exercise 2
... 8. Which network device provides public to private network security and may use Network Address Translation (NAT)? a) Hub b) Bridge c) Switch d) Firewall 9. Which device connects multiple computers to create a single logical network segment? a) Hub b) NIC c) Router d) Bridge 10. Devices on a Token ...
... 8. Which network device provides public to private network security and may use Network Address Translation (NAT)? a) Hub b) Bridge c) Switch d) Firewall 9. Which device connects multiple computers to create a single logical network segment? a) Hub b) NIC c) Router d) Bridge 10. Devices on a Token ...
Cyber-landmining SCADA Supervisory, Control And Data Acquisition
... hard to remember, leading users to write them down rather than memorizing them. • Digital Rights Management schemes are often used to discourage illegal piracy by preventing copying of content, which also has the effect of reducing its utility to paying customers who want to play their purchased mat ...
... hard to remember, leading users to write them down rather than memorizing them. • Digital Rights Management schemes are often used to discourage illegal piracy by preventing copying of content, which also has the effect of reducing its utility to paying customers who want to play their purchased mat ...
Principals of Information Security, Fourth Edition
... – Frequently installed on a dedicated computer; also known as a proxy server – Since proxy server is often placed in unsecured area of the network (e.g., DMZ), it is exposed to higher levels of risk from less trusted networks – Additional filtering routers can be implemented behind the proxy server, ...
... – Frequently installed on a dedicated computer; also known as a proxy server – Since proxy server is often placed in unsecured area of the network (e.g., DMZ), it is exposed to higher levels of risk from less trusted networks – Additional filtering routers can be implemented behind the proxy server, ...
Network Traffic Monitoring and Analysis
... • The Managed Devices contain the SNMP Agent and can consist of routers, switches, hubs, printers. They are responsible for collecting information and making it available to the NMSs. • The Agents contain software that have knowledge of management information and translates this information into a ...
... • The Managed Devices contain the SNMP Agent and can consist of routers, switches, hubs, printers. They are responsible for collecting information and making it available to the NMSs. • The Agents contain software that have knowledge of management information and translates this information into a ...
How UTM Solutions Provide the Most Complete
... Keeping corporate networks safe is more challenging every year, and network security has become one of the most critical issues facing businesses today. New and ever-changing threats appear with alarming regularity, and no organization is immune from risk. In the early days of the Internet, Internet ...
... Keeping corporate networks safe is more challenging every year, and network security has become one of the most critical issues facing businesses today. New and ever-changing threats appear with alarming regularity, and no organization is immune from risk. In the early days of the Internet, Internet ...
4th Edition: Chapter 1 - United States Naval Academy
... 1.1 what is the Internet? 1.2 network edge end systems, access networks, links 1.3 network core packet switching, circuit switching, network structure ...
... 1.1 what is the Internet? 1.2 network edge end systems, access networks, links 1.3 network core packet switching, circuit switching, network structure ...
Trojan Horse - Communications Systems Center
... Look under keyboard, telephone etc. Look in the Rolodex under “X” and “Z” Call up pretending to from “micro-support,” and ask for it. “Snoop” a network and watch the plaintext passwords go by. Tap a phone line - but this requires a very special modem. Use a “Trojan Horse” program or “key catcher”to ...
... Look under keyboard, telephone etc. Look in the Rolodex under “X” and “Z” Call up pretending to from “micro-support,” and ask for it. “Snoop” a network and watch the plaintext passwords go by. Tap a phone line - but this requires a very special modem. Use a “Trojan Horse” program or “key catcher”to ...