PPT - ManageEngine
... Secure Platform Authorization: Role based access control Authentication: Strong Encryption & secure key management High Availability for robustness & scalability Ease of Use and Faster Learning curve ...
... Secure Platform Authorization: Role based access control Authentication: Strong Encryption & secure key management High Availability for robustness & scalability Ease of Use and Faster Learning curve ...
Document
... – Provides the benefit of enabling use of “sparing” or standby link when both interfaces are operating normally ...
... – Provides the benefit of enabling use of “sparing” or standby link when both interfaces are operating normally ...
Optimal Resume at KAPLAN UNIVERSITY
... Datagram Protocol (UDP)/ connectionless delivery of packets. IP moves the data from point A to point B and is known as the best-effort transmission because it does not exchange information to establish an end-to-end connection before starting a transmission. Address Resolution Protocol (ARP) is a TC ...
... Datagram Protocol (UDP)/ connectionless delivery of packets. IP moves the data from point A to point B and is known as the best-effort transmission because it does not exchange information to establish an end-to-end connection before starting a transmission. Address Resolution Protocol (ARP) is a TC ...
Document
... 6. Presentation Layer Example application program: redirector (NT), SSL • Translate data from Application Layer to the format suitable for session layer (the network) • Provide data encryption, compression ...
... 6. Presentation Layer Example application program: redirector (NT), SSL • Translate data from Application Layer to the format suitable for session layer (the network) • Provide data encryption, compression ...
The Internet and Its Uses
... A complete communication process includes these steps: 1. _____________ at the application layer of the __________ device 2. __________________________________ of data as it passes down the protocol stack in the source end device 3. Generation of the data _______________________ at the network acces ...
... A complete communication process includes these steps: 1. _____________ at the application layer of the __________ device 2. __________________________________ of data as it passes down the protocol stack in the source end device 3. Generation of the data _______________________ at the network acces ...
Week 3 - IP addressing
... How do IP addresses incorporate network addresses? Every IP address has two parts. These are known as the network number and the host number. ...
... How do IP addresses incorporate network addresses? Every IP address has two parts. These are known as the network number and the host number. ...
Windows Server
... security update. Distributes policy and security updates. Defines enforcement ...
... security update. Distributes policy and security updates. Defines enforcement ...
Mobile Wireless Ad Hoc Network (MANET)
... The big topic in many research projects Far more than 50 different proposals exist The most simplest one: Flooding! Flooding is a simple routing technique in computer networks where a source or node sends packets through every outgoing link. Flooding, which is similar to broadcasting, occu ...
... The big topic in many research projects Far more than 50 different proposals exist The most simplest one: Flooding! Flooding is a simple routing technique in computer networks where a source or node sends packets through every outgoing link. Flooding, which is similar to broadcasting, occu ...
ADM5100 - Vislink
... BUC ■■Software enabled internal 24VDC support, up to 85W on IDU F-connector (typical 6-8W K u) ...
... BUC ■■Software enabled internal 24VDC support, up to 85W on IDU F-connector (typical 6-8W K u) ...
Presentation
... These new concepts in customer empowered networking are starting in the same place as the Internet started – the university and research community. Customers will start with dark fiber but will eventually extend further outwards with customer control and ownership of wavelengths ...
... These new concepts in customer empowered networking are starting in the same place as the Internet started – the university and research community. Customers will start with dark fiber but will eventually extend further outwards with customer control and ownership of wavelengths ...
PDF
... Company 1 has a /20 allocation and has given out sub portions of it to other companies University has a full class B address Company 2 has a /23 allocation from some other class B ALL use the same upstream ISP – that ISP must advertise routes to all these blocks that cannot be described with a simpl ...
... Company 1 has a /20 allocation and has given out sub portions of it to other companies University has a full class B address Company 2 has a /23 allocation from some other class B ALL use the same upstream ISP – that ISP must advertise routes to all these blocks that cannot be described with a simpl ...
Communication-Centric Design
... • Latencies on-chip are much lower than in previous parallel machines. This should make programming easier + new oppurtinities • Easy to increase number of cores as underlying fabrication technology scales • Simply an engineering problem? ...
... • Latencies on-chip are much lower than in previous parallel machines. This should make programming easier + new oppurtinities • Easy to increase number of cores as underlying fabrication technology scales • Simply an engineering problem? ...
TCP/IP for Security Administrators
... ARP conversations Normal: B saves A’s ARP info in cache, ready for replies Other machines on same subnet also save A’s ARP 00:80:c8:f8:4a:51 ff:ff:ff:ff:ff:ff: arp who-has 192.168.99.254 tell 192.168.99.35 00:80:c8:f8:5c:73 00:80:c8:f8:4a:51: arp reply 192.168.99.254 is-at 00:80:c8:f8:5c:73 ...
... ARP conversations Normal: B saves A’s ARP info in cache, ready for replies Other machines on same subnet also save A’s ARP 00:80:c8:f8:4a:51 ff:ff:ff:ff:ff:ff: arp who-has 192.168.99.254 tell 192.168.99.35 00:80:c8:f8:5c:73 00:80:c8:f8:4a:51: arp reply 192.168.99.254 is-at 00:80:c8:f8:5c:73 ...
Chapter_4_Sec3 - ODU Computer Science
... advanced design: fragmenting datagram into fixed length cells, switch cells through the fabric. Cisco 12000: switches 60 Gbps through the interconnection network ...
... advanced design: fragmenting datagram into fixed length cells, switch cells through the fabric. Cisco 12000: switches 60 Gbps through the interconnection network ...
tia4_ppt_ch12
... – Handles communications between networks including the Internet – Often the only device on the network directly connected to the Internet ...
... – Handles communications between networks including the Internet – Often the only device on the network directly connected to the Internet ...
lect04
... limited only by your imagination. And a couple of laws of physics. TCP/IP, HTTP How, Why, What, When? ...
... limited only by your imagination. And a couple of laws of physics. TCP/IP, HTTP How, Why, What, When? ...
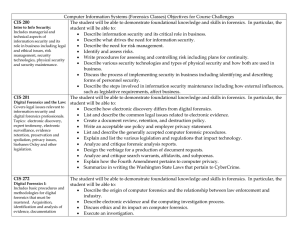
Computer Information Systems (Forensics Classes) Objectives for
... • Describe authentication, integrity and confidentiality and how they relate to security systems. • Describe the use of public key technology in networks and the issues associated with key management. • Compare and contrast the various mechanisms that provide authentication services, authentication, ...
... • Describe authentication, integrity and confidentiality and how they relate to security systems. • Describe the use of public key technology in networks and the issues associated with key management. • Compare and contrast the various mechanisms that provide authentication services, authentication, ...
white paper - Nuage Networks
... The VSP solution is designed to enable communication only through established network policies (which ensure restricting access to only authorized networks/ services). ...
... The VSP solution is designed to enable communication only through established network policies (which ensure restricting access to only authorized networks/ services). ...
Chapter 4. - Amoud University
... most important protocol in this layer. It is a connectionless protocol that does not assume reliability from lower layers. IP does not provide reliability, flow control, or error recovery. These functions must be provided at a higher level. IP provides a routing function that attempts to deliver tra ...
... most important protocol in this layer. It is a connectionless protocol that does not assume reliability from lower layers. IP does not provide reliability, flow control, or error recovery. These functions must be provided at a higher level. IP provides a routing function that attempts to deliver tra ...
Securing Your Wireless Network - Homes and Lifestyles of Colorado
... Going wireless generally requires a broadband Internet connection into your home, called an "access point," like a cable or DSL line that runs into a modem. To set up the wireless network, you connect the access point to a wireless router that broadcasts a signal through the air, sometimes as far a ...
... Going wireless generally requires a broadband Internet connection into your home, called an "access point," like a cable or DSL line that runs into a modem. To set up the wireless network, you connect the access point to a wireless router that broadcasts a signal through the air, sometimes as far a ...
Cross layer design for Wireless networks
... Application, transport and physical layer can be separated if : ...
... Application, transport and physical layer can be separated if : ...
Chapter8R_backup
... If no reply by T2, host broadcasts DHCP Request to any server If no reply by T, host must relinquish IP address and start from the beginning ...
... If no reply by T2, host broadcasts DHCP Request to any server If no reply by T, host must relinquish IP address and start from the beginning ...
A Survey on Denial of Service Attacks
... by the website those no longer for clients of that website. Distributed Denial of Service (DDOS) attacks are based on traffic volume based attacks from huge number of compromised hosts. These hosts or resources, known as ‘zombies’, form a widely distributed attack network called as ‘botnet’ [3].The ...
... by the website those no longer for clients of that website. Distributed Denial of Service (DDOS) attacks are based on traffic volume based attacks from huge number of compromised hosts. These hosts or resources, known as ‘zombies’, form a widely distributed attack network called as ‘botnet’ [3].The ...
LinkProof Data Sheet
... Integrated Application-Level Security Rampant virus or Denial of Service (DoS) attacks can impact the availability and performance of your business in the exact same way that a down link can, damaging your reputation and your bottom line. LinkProof provides a secure, single point of entry to your n ...
... Integrated Application-Level Security Rampant virus or Denial of Service (DoS) attacks can impact the availability and performance of your business in the exact same way that a down link can, damaging your reputation and your bottom line. LinkProof provides a secure, single point of entry to your n ...
tutorial13
... possibility to distribute the networking load on them between a group of servers – Candidate applications could be: Web browsers, remote login, file transfer, mail applications ...
... possibility to distribute the networking load on them between a group of servers – Candidate applications could be: Web browsers, remote login, file transfer, mail applications ...