Data security based on multipath routing.
... Routing Protocol Security Protocols based on multi path routing SPREAD (Security Protocol for Reliable data delivery) – uses threshold secret sharing system. Provides maximum security along with reliability of some extent. Split multi path routing - uses the source routing. The message parts ...
... Routing Protocol Security Protocols based on multi path routing SPREAD (Security Protocol for Reliable data delivery) – uses threshold secret sharing system. Provides maximum security along with reliability of some extent. Split multi path routing - uses the source routing. The message parts ...
Network - Moodle
... ordinary homes • Access to information and services • Later generations of applications focussed less on letting users access information, more on letting users create their own • Blogs, wikis, social networks, ... • The read/write web ...
... ordinary homes • Access to information and services • Later generations of applications focussed less on letting users access information, more on letting users create their own • Blogs, wikis, social networks, ... • The read/write web ...
CSC 335 Data Communications and Networking I
... informed • Multicast is more demanding • May be reduced – Some members of group may not require delivery from particular source over given time • e.g. selection of one from a number of “channels” ...
... informed • Multicast is more demanding • May be reduced – Some members of group may not require delivery from particular source over given time • e.g. selection of one from a number of “channels” ...
Network+ Guide to Networks, Fourth Edition
... – Used for supplying HTTP-accessible documents, e-mail, file sharing, document management, and collaboration – Defined by its security policies ...
... – Used for supplying HTTP-accessible documents, e-mail, file sharing, document management, and collaboration – Defined by its security policies ...
Fault Level Constraint – Example 1 - UK Power Networks
... Fault Level Constraint – Network Design • Fault level is not readily measured in the same way as current and voltage • Fault levels calculated using off-line analysis tools • Effects of different network configuration considered with fault level analysis due to resultant change in network impedance ...
... Fault Level Constraint – Network Design • Fault level is not readily measured in the same way as current and voltage • Fault levels calculated using off-line analysis tools • Effects of different network configuration considered with fault level analysis due to resultant change in network impedance ...
EDS-405A/408A Series
... The EDS-405A/408A are entry-level 5 and 8-port managed Ethernet switches designed especially for industrial applications. The switches support a variety of useful management functions, such as Turbo Ring, Turbo Chain, ring coupling, IGMP snooping, IEEE 802.1Q VLAN, port- ...
... The EDS-405A/408A are entry-level 5 and 8-port managed Ethernet switches designed especially for industrial applications. The switches support a variety of useful management functions, such as Turbo Ring, Turbo Chain, ring coupling, IGMP snooping, IEEE 802.1Q VLAN, port- ...
group6
... Vector Table is being used which efficiently calculates the shortest path to the host which has the required contents Scalability: The method employed can be extended by using the unused bits of the IP address making the system scalable Latency: The method employs bread crumbs to send data back to t ...
... Vector Table is being used which efficiently calculates the shortest path to the host which has the required contents Scalability: The method employed can be extended by using the unused bits of the IP address making the system scalable Latency: The method employs bread crumbs to send data back to t ...
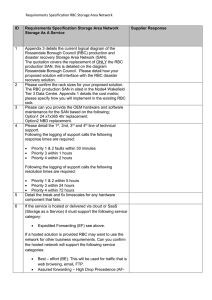
Appendix 2. Requirements Specification RBC Storage Area Network
... to perform the complete set up of any on premise solution. A build plan, configuration list and testing plan including timescales will be required. Disaster Recovery / Business Continuity Management ...
... to perform the complete set up of any on premise solution. A build plan, configuration list and testing plan including timescales will be required. Disaster Recovery / Business Continuity Management ...
part 2 - Computer Science Division
... LIS looks like a LAN ATM net divided into multiple LIS ...
... LIS looks like a LAN ATM net divided into multiple LIS ...
Formal Foundations for Networking - DROPS
... while the one with low Q is not. We provide three results based on empirical data which show that community structure of real-world industrial instances is a better predictor of the running time of CDCL solvers than other commonly considered factors such as variables and clauses. First, we show that ...
... while the one with low Q is not. We provide three results based on empirical data which show that community structure of real-world industrial instances is a better predictor of the running time of CDCL solvers than other commonly considered factors such as variables and clauses. First, we show that ...
Cisco 646-203
... C. a large ISP that has been targeted by a denial of service attack that disables Internet access for several thousand customers D. a mortgage-lending company that opens several branch offices that require secure access to underwriting information on the corporate extranet Answer: B,D QUESTION 11 An ...
... C. a large ISP that has been targeted by a denial of service attack that disables Internet access for several thousand customers D. a mortgage-lending company that opens several branch offices that require secure access to underwriting information on the corporate extranet Answer: B,D QUESTION 11 An ...
Some Network Commands - Texas Tech University
... Some useful network commands – ping – finger – nslookup – tracert – ipconfig ...
... Some useful network commands – ping – finger – nslookup – tracert – ipconfig ...
Network
... • Twisted-Pair Cable – Network cable of eight copper wires twisted into four pairs to prevent crosstalk. – UTP (Unshielded Twisted-Pair) – Most common network cable that comes in different categories for different uses. Categories 3 (voice-grade), 4, and 5 (data). It is unshielded and more susceptib ...
... • Twisted-Pair Cable – Network cable of eight copper wires twisted into four pairs to prevent crosstalk. – UTP (Unshielded Twisted-Pair) – Most common network cable that comes in different categories for different uses. Categories 3 (voice-grade), 4, and 5 (data). It is unshielded and more susceptib ...
ch13
... as virtual byte streams, in both directions. UDP transmits packets independently, with no guarantee of delivery and minimal error checking. UDP also limits packet size to the size of a UDP packet, since each packet is independent with no method for sequencing multiple packets that fcontain an extend ...
... as virtual byte streams, in both directions. UDP transmits packets independently, with no guarantee of delivery and minimal error checking. UDP also limits packet size to the size of a UDP packet, since each packet is independent with no method for sequencing multiple packets that fcontain an extend ...
Remote+Monitoring+and+DMI
... SNMP network management tools can support the monitoring of individual devices. However, it is difficult to learn about traffic on a particular network using SNMP. ...
... SNMP network management tools can support the monitoring of individual devices. However, it is difficult to learn about traffic on a particular network using SNMP. ...
Voice over Mobile IP
... (4) umass proxy sends INVITE to eurecom registrar. (5) eurecom registrar forwards INVITE to 197.87.54.21, which is running keith’s SIP client. (6-8) SIP response sent back (9) media sent directly between clients. Note: also a SIP ack message, which is not shown. ...
... (4) umass proxy sends INVITE to eurecom registrar. (5) eurecom registrar forwards INVITE to 197.87.54.21, which is running keith’s SIP client. (6-8) SIP response sent back (9) media sent directly between clients. Note: also a SIP ack message, which is not shown. ...
An Overview of MANET: History, Challenges and Applications
... MANET is a infrastructure less network, there is no central administration. Each device can communicate with every other device, hence it becomes difficult to detect and manage the faults. In MANET, the mobile devices can move randomly. The use of this dynamic topology results in route changes, freq ...
... MANET is a infrastructure less network, there is no central administration. Each device can communicate with every other device, hence it becomes difficult to detect and manage the faults. In MANET, the mobile devices can move randomly. The use of this dynamic topology results in route changes, freq ...
Ch – 1 Introduction
... • Two entities are considered peers if they implement the same protocol in different systems (e.g., two TCP modules in two communicating systems). • Peer entity authentication is provided for use at the establishment of or during the data transfer phase of a connection. ...
... • Two entities are considered peers if they implement the same protocol in different systems (e.g., two TCP modules in two communicating systems). • Peer entity authentication is provided for use at the establishment of or during the data transfer phase of a connection. ...
Public-Private Partnerships In Support of C@ribNET
... Supports the Integration process through working within a single space Reduces costs of ICT services through aggregation Providing access to Tertiary education to a significant number of Caribbean citizens who otherwise would not have the opportunity Extend the reach and access to education assets a ...
... Supports the Integration process through working within a single space Reduces costs of ICT services through aggregation Providing access to Tertiary education to a significant number of Caribbean citizens who otherwise would not have the opportunity Extend the reach and access to education assets a ...
DNS - Department of Computer Science
... Given an IP packet, routers determine the block it belongs to and send the packet to the ISP who are responsible for this block The ISP needs to know how to reach each of its own separate networks ...
... Given an IP packet, routers determine the block it belongs to and send the packet to the ISP who are responsible for this block The ISP needs to know how to reach each of its own separate networks ...
Improving Security in Anonymizing Networks using a Privacy Enhancing System
... blacklisting, backward unlinkability, fast authentication speeds, rate-limited anonymous connections, revocation auditability and also addresses sybil attack[10][11]. Servers can blacklist anonymous users without the knowledge of their IP addresses while allowing behaving users to connect anonymousl ...
... blacklisting, backward unlinkability, fast authentication speeds, rate-limited anonymous connections, revocation auditability and also addresses sybil attack[10][11]. Servers can blacklist anonymous users without the knowledge of their IP addresses while allowing behaving users to connect anonymousl ...
ITNW 1358 - Network+
... with the instructor PRIOR to exam date. NOTE: There is NO make-up exam for the final. Class rules: In class, students will be expected to abide by the following rules, please: 1. Turn OFF your mobile phones or, at a minimum, put them on vibrate mode! 2. Do not use the Internet during lectures or lab ...
... with the instructor PRIOR to exam date. NOTE: There is NO make-up exam for the final. Class rules: In class, students will be expected to abide by the following rules, please: 1. Turn OFF your mobile phones or, at a minimum, put them on vibrate mode! 2. Do not use the Internet during lectures or lab ...
網路基本觀念 - Yen-Cheng Chen / 陳彥錚
... new message types, standardized multi-protocol support, enhanced security, new MIB objects, and a way to co-exist with SNMPv1. SNMPv2C is useful for the retrieval of large amounts of management information using fewer network resources. ...
... new message types, standardized multi-protocol support, enhanced security, new MIB objects, and a way to co-exist with SNMPv1. SNMPv2C is useful for the retrieval of large amounts of management information using fewer network resources. ...
Low-Intensity DoS attack on BGP Infrastructure
... Communication channels not overloaded but have significant droppage of the request/acknowledgement packets. ...
... Communication channels not overloaded but have significant droppage of the request/acknowledgement packets. ...