View File - University of Engineering and Technology, Taxila
... to access to the outside world The host network provides support for the ad-hoc by providing access to specific domain services and agreements ...
... to access to the outside world The host network provides support for the ad-hoc by providing access to specific domain services and agreements ...
Secure Routing and Intrusion Detection in Ad
... Ad Hoc networks • Nikander at Helsinki discusses the authentication, authorization, and accounting in Ad Hoc networks • Bhargavan at UIUC presents the method to enhance security by dynamic virtual infrastructure • Vaidya at UIUC presents the idea of securing Ad Hoc networks with directional antennas ...
... Ad Hoc networks • Nikander at Helsinki discusses the authentication, authorization, and accounting in Ad Hoc networks • Bhargavan at UIUC presents the method to enhance security by dynamic virtual infrastructure • Vaidya at UIUC presents the idea of securing Ad Hoc networks with directional antennas ...
Lab 9.2.4 IP Addressing Basics
... unique IP address. This address is referred to as its host address. TCP/IP is the most widely used protocol in the world. The Internet or World Wide Web only uses IP addressing. In order for a host to access the Internet, it must have an IP address. In its basic form, the IP address has two parts: ...
... unique IP address. This address is referred to as its host address. TCP/IP is the most widely used protocol in the world. The Internet or World Wide Web only uses IP addressing. In order for a host to access the Internet, it must have an IP address. In its basic form, the IP address has two parts: ...
ex1-10 - wmmhicks.com
... They produce 4 subnets each with 510 addresses. This is impossible. It will be corrected. You can do it if you start with 172.16.0.0/21 ...
... They produce 4 subnets each with 510 addresses. This is impossible. It will be corrected. You can do it if you start with 172.16.0.0/21 ...
Lecture 2 Layers of the OSI
... So what is broadcast? If you address a single host, it is called Unicast. Even unicast packets are received by each and every host, but after unpacking it up to the network level, the host sees if it was the intended recipient or not. If not, the packet is simply thrown away. Sometimes you want to r ...
... So what is broadcast? If you address a single host, it is called Unicast. Even unicast packets are received by each and every host, but after unpacking it up to the network level, the host sees if it was the intended recipient or not. If not, the packet is simply thrown away. Sometimes you want to r ...
INS PPT - Home Kalim Puthawala
... Still possible for Outsiders to assess the amount of traffic entering and leaving each end system When input plaintext is not present, random data are encrypted, making it possible for an attacker to distinguish true data flow from padding, and thereby deduce the amount of traffic. End-to-End Encryp ...
... Still possible for Outsiders to assess the amount of traffic entering and leaving each end system When input plaintext is not present, random data are encrypted, making it possible for an attacker to distinguish true data flow from padding, and thereby deduce the amount of traffic. End-to-End Encryp ...
An Immucor Technical Support Solution
... Yes, blud_direct utilizes the Secure Socket Layer (SSL) protocol, commonly used for secure transactions over the web. Additionally, the application uses 256-bit AES encryption to further secure the communication. Is there software loaded on our instrument computer? No. There is no software to load o ...
... Yes, blud_direct utilizes the Secure Socket Layer (SSL) protocol, commonly used for secure transactions over the web. Additionally, the application uses 256-bit AES encryption to further secure the communication. Is there software loaded on our instrument computer? No. There is no software to load o ...
Performance Issues of P2P File Sharing Over Asymmetric and
... performance of TCP based network applications will be interfered by the P2P file sharing operation. These problems are further complicated by the voluntary nature of P2P that peer nodes may be fairly unstable such that the failure rates of download operations are fairly high. We can easily identify ...
... performance of TCP based network applications will be interfered by the P2P file sharing operation. These problems are further complicated by the voluntary nature of P2P that peer nodes may be fairly unstable such that the failure rates of download operations are fairly high. We can easily identify ...
Mobile Network Layer
... COA can be assigned via auto-configuration (DHCPv6 is one candidate), every node has address auto-configuration no need for a separate FA, all routers perform router advertisement which can be used instead of the special agent advertisement; addresses are always co-located MN can signal a sender dir ...
... COA can be assigned via auto-configuration (DHCPv6 is one candidate), every node has address auto-configuration no need for a separate FA, all routers perform router advertisement which can be used instead of the special agent advertisement; addresses are always co-located MN can signal a sender dir ...
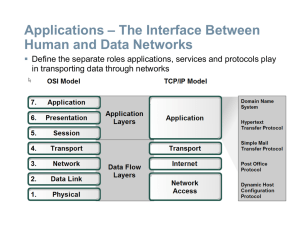
Application Layer Functionality and Protocols
... Describe how a switch can eliminate collisions, backoffs and re- transmissions, the leading factors in reduced throughput on a hub-based Ethernet network ...
... Describe how a switch can eliminate collisions, backoffs and re- transmissions, the leading factors in reduced throughput on a hub-based Ethernet network ...
Educause Task Force on Systems Security
... Inventory your critical systems (Virginia Tech Excel) Risk Mgt: Assess/prioritize the risks to these systems Secure critical (and legally mandated systems) by patching/hardening the OS and applications • Move critical systems into data centers where they will be physically and environmentally secure ...
... Inventory your critical systems (Virginia Tech Excel) Risk Mgt: Assess/prioritize the risks to these systems Secure critical (and legally mandated systems) by patching/hardening the OS and applications • Move critical systems into data centers where they will be physically and environmentally secure ...
CAP - MUM - Mikrotik
... Traditionally, administering wireless Access Point is done individually one by one ...
... Traditionally, administering wireless Access Point is done individually one by one ...
The Network Layer
... incoming datagrams: replace (NAT IP address, new port #) in dest fields of every incoming datagram with corresponding (source IP address, port #) stored in NAT table ...
... incoming datagrams: replace (NAT IP address, new port #) in dest fields of every incoming datagram with corresponding (source IP address, port #) stored in NAT table ...
Network architecture, operations, services info sheet
... Software Defined Networking (SDN) over a high performance, geographically distributed facility. ...
... Software Defined Networking (SDN) over a high performance, geographically distributed facility. ...
Hierarchical Organization Unveiled by Functional Connectivity in
... models, such as small-world (SW) and scale-free networks, and analyzed the ability to achieve idealized complete synchronization or coherent collective oscillations. However, many realistic network systems display several levels of topological organization not well accounted for by typical network m ...
... models, such as small-world (SW) and scale-free networks, and analyzed the ability to achieve idealized complete synchronization or coherent collective oscillations. However, many realistic network systems display several levels of topological organization not well accounted for by typical network m ...
Introduction - Department of Computer Engineering
... Network application Program that is designed to run over a network, such as the Internet. A network application has two components, one that runs on the local computer and one that runs on a remote computer. ...
... Network application Program that is designed to run over a network, such as the Internet. A network application has two components, one that runs on the local computer and one that runs on a remote computer. ...
Managing security risks and vulnerabilities
... Fortunately, today’s organizations have a smarter option. The latest integrated security intelligence solutions use advanced labor-saving automation to deliver more value from security budgets—and increase efficiency of IT staff—while simultaneously strengthening their security posture. Organization ...
... Fortunately, today’s organizations have a smarter option. The latest integrated security intelligence solutions use advanced labor-saving automation to deliver more value from security budgets—and increase efficiency of IT staff—while simultaneously strengthening their security posture. Organization ...
Document
... announcing its existance and address. A newly arrived mobile host may wait for one of these messages, but if none arrives quickly enough, the mobile host can broadcast a packet saying: “Are there any foreign agents around?” 2. The mobile host registers with the foreign agent, giving its home address ...
... announcing its existance and address. A newly arrived mobile host may wait for one of these messages, but if none arrives quickly enough, the mobile host can broadcast a packet saying: “Are there any foreign agents around?” 2. The mobile host registers with the foreign agent, giving its home address ...
Module 9 VLAN Trunking Protocol
... • For example, a trunk can connect a switch to another switch, a switch to the inter-VLAN router, or a switch to a server with a special NIC installed that supports trunking. • Remember that when a host on one VLAN wants to communicate with a host on another, a router must be involved. ...
... • For example, a trunk can connect a switch to another switch, a switch to the inter-VLAN router, or a switch to a server with a special NIC installed that supports trunking. • Remember that when a host on one VLAN wants to communicate with a host on another, a router must be involved. ...
CCNP Routing Semester 5 - YSU Computer Science & Information
... providers that provide Internet connectivity • Site topology – The level local to an organization that does not provide connectivity to nodes outside itself • Interface identifier – The level specific to a node’s individual interface ...
... providers that provide Internet connectivity • Site topology – The level local to an organization that does not provide connectivity to nodes outside itself • Interface identifier – The level specific to a node’s individual interface ...
Use of a WDM network
... Issue 1 • IP traffic even in core measured to be bursty – Implication: need traffic shaping at edge routers or gateways if circuit-switched alternatives are used – Is it possible to shape IP (self-similar) traffic to a constant rate? – Is there a problem if the IP traffic delivered at the far-end r ...
... Issue 1 • IP traffic even in core measured to be bursty – Implication: need traffic shaping at edge routers or gateways if circuit-switched alternatives are used – Is it possible to shape IP (self-similar) traffic to a constant rate? – Is there a problem if the IP traffic delivered at the far-end r ...
CELLULAR OVER BROADBAND NETWORKS
... This trend creates a need for high-capacity networks to carry traffic as diverse as phone calls, data look-up, pictures, entertainment and emergency alerts at low cost and without congestion. Different types of applications place different demands on a network The implementation of an efficient prot ...
... This trend creates a need for high-capacity networks to carry traffic as diverse as phone calls, data look-up, pictures, entertainment and emergency alerts at low cost and without congestion. Different types of applications place different demands on a network The implementation of an efficient prot ...