P2P Local Mesh Communications Network for
... communicating to another node. In this case, if there is heavy attenuation between two such nodes, no communication will ever be established. To overcome this, we decided to implement a mesh network topology for all communication. ...
... communicating to another node. In this case, if there is heavy attenuation between two such nodes, no communication will ever be established. To overcome this, we decided to implement a mesh network topology for all communication. ...
practice
... designed to protect computers, networks and data from unauthorized access, vulnerabilities and attacks delivered via the Internet by cyber criminals. KEY ISSUES Technologies designed to protect computers, networks and data Processes designed to protect computers, network and data ; Vulnerabili ...
... designed to protect computers, networks and data from unauthorized access, vulnerabilities and attacks delivered via the Internet by cyber criminals. KEY ISSUES Technologies designed to protect computers, networks and data Processes designed to protect computers, network and data ; Vulnerabili ...
1993 - abuad lms
... NIC connects to the computer through expansion slots, which are special slots located on a computer’s motherboard that allow peripherals to be plugged directly into it. In some notebook, NIC adapters can be connected to the printer port or through a PC card slot. NIC cards generally all have one or ...
... NIC connects to the computer through expansion slots, which are special slots located on a computer’s motherboard that allow peripherals to be plugged directly into it. In some notebook, NIC adapters can be connected to the printer port or through a PC card slot. NIC cards generally all have one or ...
Communication and network concepts
... Foundation namely-NSFNET. But NSFNET allowed didn’t allow any private business so private companies built their own networks later joined with ARPANET & NSFNET to form internet. ...
... Foundation namely-NSFNET. But NSFNET allowed didn’t allow any private business so private companies built their own networks later joined with ARPANET & NSFNET to form internet. ...
AUROREAN™ POLICY SERVER 7000 AND 3000 SERIES Data Sheet
... configuration and SNMP monitoring agents allow for centralized management of distributed nodes. Detailed reports and analysis tools enable the network administrator to optimize VPN use by monitoring tunnel performance, availability, utilization and cost. Administrators can drill down to the individu ...
... configuration and SNMP monitoring agents allow for centralized management of distributed nodes. Detailed reports and analysis tools enable the network administrator to optimize VPN use by monitoring tunnel performance, availability, utilization and cost. Administrators can drill down to the individu ...
Mobile Communications
... 1999 Standardization of additional wireless LANs IEEE standard 802.11b, 2.4-2.5GHz, 11Mbit/s Bluetooth for piconets, 2.4Ghz, <1Mbit/s ...
... 1999 Standardization of additional wireless LANs IEEE standard 802.11b, 2.4-2.5GHz, 11Mbit/s Bluetooth for piconets, 2.4Ghz, <1Mbit/s ...
Five steps to peak application performance
... Our network team have identified five simple stages in the delivery of peak application performance. Separately, each can deliver results. But it’s when all five work together that you can achieve superior application performance. 1. Help ensure network availability It doesn’t matter how much bandwi ...
... Our network team have identified five simple stages in the delivery of peak application performance. Separately, each can deliver results. But it’s when all five work together that you can achieve superior application performance. 1. Help ensure network availability It doesn’t matter how much bandwi ...
ppt - EECS: www-inst.eecs.berkeley.edu
... maximize performance (smallest AS path length) minimize use of my network bandwidth (“hot potato”) ...
... maximize performance (smallest AS path length) minimize use of my network bandwidth (“hot potato”) ...
Things we didn`t get to talk about
... – Dynamic: easy for administrators to make spontaneous changes ...
... – Dynamic: easy for administrators to make spontaneous changes ...
A Guide to Windows 2000 Server
... If network performance is slow and your network uses a combination of protocols, tune the binding order on Windows NT and Windows 2000 clients which can be an inexpensive way to immediately relieve network congestion ...
... If network performance is slow and your network uses a combination of protocols, tune the binding order on Windows NT and Windows 2000 clients which can be an inexpensive way to immediately relieve network congestion ...
CCNA2 3.0-09 Basic Router Troubleshooting
... • Remember that the IP source and destination do not change in the packet, but the MAC addresses do change. • The packet is forwarded based on the MAC address of the next hop. • Layer 3 address is always used in routing, but the MAC address has to change because the data is framed as it moves out on ...
... • Remember that the IP source and destination do not change in the packet, but the MAC addresses do change. • The packet is forwarded based on the MAC address of the next hop. • Layer 3 address is always used in routing, but the MAC address has to change because the data is framed as it moves out on ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... transfer the encrypted packets between the source and destination. There are four types of control packets RREQ, REER, HELLO and RREP. The first three are sent by broad cast, while RREP is sent by unicast. It discovers the route based on local routing table. The algorithm enables dynamic, self start ...
... transfer the encrypted packets between the source and destination. There are four types of control packets RREQ, REER, HELLO and RREP. The first three are sent by broad cast, while RREP is sent by unicast. It discovers the route based on local routing table. The algorithm enables dynamic, self start ...
Introduction
... Answer: In Circuit Switching networks: (1) a dedicated circuit is established between sender and receiver, (2) circuit capacity is reserved during the duration of each communication, at each node (switch) and on each transmission line; (3) no routing decisions are necessary since circuit is ...
... Answer: In Circuit Switching networks: (1) a dedicated circuit is established between sender and receiver, (2) circuit capacity is reserved during the duration of each communication, at each node (switch) and on each transmission line; (3) no routing decisions are necessary since circuit is ...
Network Protocols Designed for Optimizability Jennifer Rexford Computer Science Department Princeton University
... find mutually beneficial ways to direct the traffic [14]. However, this approach depends on having an effective way to satisfy the objectives of both networks, while ensuring that neither domain has an incentive to provide misleading information to the other. Similarly, the difficulties in tuning th ...
... find mutually beneficial ways to direct the traffic [14]. However, this approach depends on having an effective way to satisfy the objectives of both networks, while ensuring that neither domain has an incentive to provide misleading information to the other. Similarly, the difficulties in tuning th ...
Information Technology Unit 2
... difference is low and the added efficiencies of a switch make it a logical choice for many networks. ...
... difference is low and the added efficiencies of a switch make it a logical choice for many networks. ...
Wi-SUN presentation
... help ensure consistency of approach, share relevant experience, and address co-existence issues & potential interoperability, since these solutions will be used in the same markets in complementary ways. ...
... help ensure consistency of approach, share relevant experience, and address co-existence issues & potential interoperability, since these solutions will be used in the same markets in complementary ways. ...
Secure Authentication Mechanism for MANET Barkha Gaur#1, Neha
... Server to save the computation resources of the client. It operates using two different phases. In the first phase known as the Handshake, the client validates itself to the proxy and establishes a secure channel with it. Second phase is called the Service Access, in which the proxy accesses the Ker ...
... Server to save the computation resources of the client. It operates using two different phases. In the first phase known as the Handshake, the client validates itself to the proxy and establishes a secure channel with it. Second phase is called the Service Access, in which the proxy accesses the Ker ...
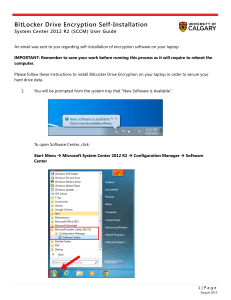
BitLocker Drive Encryption Self
... A prompt will indicate you must restart the computer. Click Restart Now. If you don't restart within 15 minutes, the computer will do so automatically. This is the point where saving your data is critical. ...
... A prompt will indicate you must restart the computer. Click Restart Now. If you don't restart within 15 minutes, the computer will do so automatically. This is the point where saving your data is critical. ...
Multicast and IPv6 - Stanford Secure Computer Systems Group
... Other Tunneling Use: VPN • Virtual Private Networks • Use case: two distance corporate offices - Want to access each other’s internal networks - Make it looks like they’re the actually one network ...
... Other Tunneling Use: VPN • Virtual Private Networks • Use case: two distance corporate offices - Want to access each other’s internal networks - Make it looks like they’re the actually one network ...
CH01-Testbank-NetSec5e
... 8. A __________ attack attempts to learn or make use of information from the system but does not affect system resources. 9. The common technique for masking contents of messages or other information traffic so that opponents, even if they captured the message, could not extract the information fr ...
... 8. A __________ attack attempts to learn or make use of information from the system but does not affect system resources. 9. The common technique for masking contents of messages or other information traffic so that opponents, even if they captured the message, could not extract the information fr ...
Lecture 6: Intra
... • Problem: Find lowest cost path between two nodes - Each node individually computes the cost (some recent research argues against doing this, more on this later) ...
... • Problem: Find lowest cost path between two nodes - Each node individually computes the cost (some recent research argues against doing this, more on this later) ...
Wireless Internet Architectures: Selected Issues Adam Wolisz 1
... Endsystem Access. Extensive research activities are focused on development of TCP modifications [14], however convincing proof of their efficiency is still to be provided. In addition the idea of modifying TCP according to features of the physical link is not really in line with the internet philoso ...
... Endsystem Access. Extensive research activities are focused on development of TCP modifications [14], however convincing proof of their efficiency is still to be provided. In addition the idea of modifying TCP according to features of the physical link is not really in line with the internet philoso ...
Slide 1
... ICMP (Internet Control Message Protocol) When working on a network, it’s important to be able to test the functionality of that network. How would you know if data could be transmitted without knowing you have a complete path from the source to the destination? That being said, how could you 'test' ...
... ICMP (Internet Control Message Protocol) When working on a network, it’s important to be able to test the functionality of that network. How would you know if data could be transmitted without knowing you have a complete path from the source to the destination? That being said, how could you 'test' ...