ppt
... • Allows arbitrary split between network & host part of address • Do not use classes to determine network ID • Use common part of address as network number • E.g., addresses 192.4.16 - 192.4.31 have the first 20 bits in common. Thus, we use these 20 bits as the network number 192.4.16/20 ...
... • Allows arbitrary split between network & host part of address • Do not use classes to determine network ID • Use common part of address as network number • E.g., addresses 192.4.16 - 192.4.31 have the first 20 bits in common. Thus, we use these 20 bits as the network number 192.4.16/20 ...
KO2317681774
... supervisory control of the system and uses it to evade auditing and access control. Initially firewall was used but it could only prevent unauthorized access and cannot monitor network attacks. Intrusion Detection is the possibility of finding the incorrect or inappropriate action. It is considered ...
... supervisory control of the system and uses it to evade auditing and access control. Initially firewall was used but it could only prevent unauthorized access and cannot monitor network attacks. Intrusion Detection is the possibility of finding the incorrect or inappropriate action. It is considered ...
class1
... Call setup required Network resources (bandwidth) are divided into pieces Pieces reserved for the “call” on the path Dedicated resources: no sharing, idle if not used ...
... Call setup required Network resources (bandwidth) are divided into pieces Pieces reserved for the “call” on the path Dedicated resources: no sharing, idle if not used ...
Chapter 4. Network Layer
... Q: how does network get subnet part of IP addr? A: gets allocated portion of its provider ISP’s address ...
... Q: how does network get subnet part of IP addr? A: gets allocated portion of its provider ISP’s address ...
Repeaters and Hubs
... o Communicates using BGP-specific messages o Many factors determine best paths o Configurable to follow policies o Type of EGP (Exterior Gateway Protocol) o Most complex (choice for Internet traffic) Network+ Guide to Networks, 6th Edition ...
... o Communicates using BGP-specific messages o Many factors determine best paths o Configurable to follow policies o Type of EGP (Exterior Gateway Protocol) o Most complex (choice for Internet traffic) Network+ Guide to Networks, 6th Edition ...
A Comparative Study of Wireless Technologies: Zigbee, Bluetooth
... years Zigbee was the promising technology for home automation. But, nowadays there are some other standards which give their best for controlling home devices. This paper presents an overview of different wireless communication standards by comparing their main features in terms of various metrics s ...
... years Zigbee was the promising technology for home automation. But, nowadays there are some other standards which give their best for controlling home devices. This paper presents an overview of different wireless communication standards by comparing their main features in terms of various metrics s ...
Factors that influence TCP performance
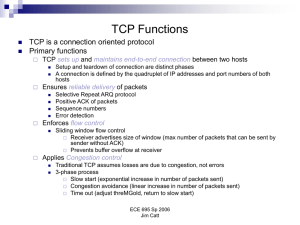
... Slow start (exponential increase in number of packets sent) Congestion avoidance (linear increase in number of packets sent) Time out (adjust threMGold, return to slow start) ECE 695 Sp 2006 Jim Catt ...
... Slow start (exponential increase in number of packets sent) Congestion avoidance (linear increase in number of packets sent) Time out (adjust threMGold, return to slow start) ECE 695 Sp 2006 Jim Catt ...
Chapter 8 Slides (Modified) File
... • A Personal Area Network (PAN) consists of devices that directly connect to a single computer. • You might connect your notebook PC to the projector in the room. • You might also form a PAN by connecting your smartphone to your computer. • A Local Area Network (LAN) is a network in which all the de ...
... • A Personal Area Network (PAN) consists of devices that directly connect to a single computer. • You might connect your notebook PC to the projector in the room. • You might also form a PAN by connecting your smartphone to your computer. • A Local Area Network (LAN) is a network in which all the de ...
Chapter 10 Circuit and Packet Switching
... —Packets are forwarded more quickly • No routing decisions to make ...
... —Packets are forwarded more quickly • No routing decisions to make ...
Network Topologies
... data still to be passed around the loop – if not whole network can be fail as traffic only in one direction, Each device will re-broadcast the data packet so signal is stronger and can cover larger area than some topologies, No hubs / switches required to connect the devices together, If a cable sto ...
... data still to be passed around the loop – if not whole network can be fail as traffic only in one direction, Each device will re-broadcast the data packet so signal is stronger and can cover larger area than some topologies, No hubs / switches required to connect the devices together, If a cable sto ...
2007z
... Interestingly, since the data was retrieved from the way to disseminate campaigned messages, the listed alumni are also reflecting the institutional aspirations and programs campaigners or respective candidate should bring if they were elected to manage the silaturahmi institution. Thi ...
... Interestingly, since the data was retrieved from the way to disseminate campaigned messages, the listed alumni are also reflecting the institutional aspirations and programs campaigners or respective candidate should bring if they were elected to manage the silaturahmi institution. Thi ...
Power Point Slides for Chap. 5
... – Examine all nodes connected to A (adjacent) relabeling them with distance to A – Also label adjacent nodes to a with the tag A so that we can construct a final path later. (In this case B, G are labeled with distance and A) – Examine tentatively labeled nodes & make the one with the smallest label ...
... – Examine all nodes connected to A (adjacent) relabeling them with distance to A – Also label adjacent nodes to a with the tag A so that we can construct a final path later. (In this case B, G are labeled with distance and A) – Examine tentatively labeled nodes & make the one with the smallest label ...
Circuit Switching, Packet Switching, The Network Layer
... Network service model Q: What service model for “channel” transporting datagrams from sender to rcvr? Example services for individual datagrams: ...
... Network service model Q: What service model for “channel” transporting datagrams from sender to rcvr? Example services for individual datagrams: ...
A DoS-limiting Network Architecture
... Security based on inability of attacker to gain capabilities for routers along path to destination. Hashing scheme uses a sufficiently small key that changes every 128 sec. Breaking the key is practically impossible. Attacker may observe pre-capabilities in requests by routers. Stolen capabi ...
... Security based on inability of attacker to gain capabilities for routers along path to destination. Hashing scheme uses a sufficiently small key that changes every 128 sec. Breaking the key is practically impossible. Attacker may observe pre-capabilities in requests by routers. Stolen capabi ...
Week_Four_Network_MIMIC
... A user community is a group of workers who use a particular application. They can exist in a department or group of departments. A User Communities chart should be utilized to record this type of information in. A data store is an area in a network where application layer data resides. A data store ...
... A user community is a group of workers who use a particular application. They can exist in a department or group of departments. A User Communities chart should be utilized to record this type of information in. A data store is an area in a network where application layer data resides. A data store ...
ping - SLAC
... • May not be able to sniff/trace traffic due to privacy/security concerns • Don’t know route details between points, may change, not under your control, may be able to deduce some of it ...
... • May not be able to sniff/trace traffic due to privacy/security concerns • Don’t know route details between points, may change, not under your control, may be able to deduce some of it ...
IP Internet Protocol Based on notes from D. Hollinger Netprog 2002 TCP/IP
... • Includes a network ID and a host ID. • Every host must have a unique IP address. • IP addresses are assigned by a central authority (Internet Corporation for Assigned Names and Numbers -- ICANN) Netprog 2002 TCP/IP ...
... • Includes a network ID and a host ID. • Every host must have a unique IP address. • IP addresses are assigned by a central authority (Internet Corporation for Assigned Names and Numbers -- ICANN) Netprog 2002 TCP/IP ...
Secure Threshold Sensitive Energy Efficient Sensor Network Protocol
... tell that nodes in the Sec-TEEN tend to consume their energy at a slower rate if compared to the SecLEACH nodes. Consequently, as can be seen from the Fig. 3, a WSN of 100 nodes using Sec-TEEN have consumed all of their energy at time 246. However, the nodes have consumed the energy at time 224 for ...
... tell that nodes in the Sec-TEEN tend to consume their energy at a slower rate if compared to the SecLEACH nodes. Consequently, as can be seen from the Fig. 3, a WSN of 100 nodes using Sec-TEEN have consumed all of their energy at time 246. However, the nodes have consumed the energy at time 224 for ...
Long Term Evolution: Simplify the Migration to 4G Networks
... In 2G and 3G networks, diverse schemes were used for mobility management within and across the access technology boundary. So, an operator choosing to deploy 2G access technology of one kind and 3G access technology of a different kind had to deploy two divergent mobility management schemes in the s ...
... In 2G and 3G networks, diverse schemes were used for mobility management within and across the access technology boundary. So, an operator choosing to deploy 2G access technology of one kind and 3G access technology of a different kind had to deploy two divergent mobility management schemes in the s ...
COE 308: Computer Architecture (T032) Dr. Marwan Abu
... Once connection is established, devices appear as if connected directly through a dedicated link Disadvantage: Inefficient utilization with computer type data communication ...
... Once connection is established, devices appear as if connected directly through a dedicated link Disadvantage: Inefficient utilization with computer type data communication ...
Social network analysis in business and economics
... • a software company • 93 employees in three geographical units • 81 employees participated in the study • 59 from Ljubljana (Slovenia), 11 in Zagreb (Croatia) and another 11 in Belgrade (Serbia) ...
... • a software company • 93 employees in three geographical units • 81 employees participated in the study • 59 from Ljubljana (Slovenia), 11 in Zagreb (Croatia) and another 11 in Belgrade (Serbia) ...
OldSmartRunningTrackRakocevicCrnjin
... All devices start symmetric inquiry procedure of all BT devices within range When every device detects all other devices within range, they will inform their neighbors about detected devices All devices can now form tables of all devices and their possible connections in the the future piconet All n ...
... All devices start symmetric inquiry procedure of all BT devices within range When every device detects all other devices within range, they will inform their neighbors about detected devices All devices can now form tables of all devices and their possible connections in the the future piconet All n ...
here - Wettengel
... to support and enhance teaching and learning to prepare all students for success in lifelong learning. All GDOE students shall use the District’s technology (network, telecommunications, video, hardware, and software) in a responsible, efficient, ethical and legal manner in accordance with the visio ...
... to support and enhance teaching and learning to prepare all students for success in lifelong learning. All GDOE students shall use the District’s technology (network, telecommunications, video, hardware, and software) in a responsible, efficient, ethical and legal manner in accordance with the visio ...