Wireless Communications and Networks
... wired network r relay - responsible for sending packets between wired network and wireless host(s) in its “area” m e.g., cell towers, 802.11 access points ...
... wired network r relay - responsible for sending packets between wired network and wireless host(s) in its “area” m e.g., cell towers, 802.11 access points ...
Network Management
... Management costs are too high Solution costs are too high Lack of one-stop shopping from vendors ...
... Management costs are too high Solution costs are too high Lack of one-stop shopping from vendors ...
IOSR Journal of Electronics and Communication Engineering (IOSRJECE)
... and connect all computers to the Internet without having to pay a full broadband subscription service to their ISP for each computer on the network. In many instances, an ISP will allow you to use a router and connect multiple computers to a single Internet connection and pay a nominal fee for each ...
... and connect all computers to the Internet without having to pay a full broadband subscription service to their ISP for each computer on the network. In many instances, an ISP will allow you to use a router and connect multiple computers to a single Internet connection and pay a nominal fee for each ...
Internet PowerPoint - University at Albany
... Syntax of the various message types, such as, fields in the messages and how they are delineated Semantics of the fields i.e. meaning of information in each field Rules for determining when and how a process sends messages and responds to messages ...
... Syntax of the various message types, such as, fields in the messages and how they are delineated Semantics of the fields i.e. meaning of information in each field Rules for determining when and how a process sends messages and responds to messages ...
ppt
... router will forward packet to a router on the next network over and so on… until packet arrives at router on same network as destination; then, router sends packet directly to destination host Requirements every host needs to know IP address of the router on its LAN every router needs a ro ...
... router will forward packet to a router on the next network over and so on… until packet arrives at router on same network as destination; then, router sends packet directly to destination host Requirements every host needs to know IP address of the router on its LAN every router needs a ro ...
RIP V2
... RIP routes (routes for networks within the RIP routing domain) from "external" RIP routes, which may have been imported from an EGP or another IGP Routers supporting protocols other than RIP should be configurable to allow the Route Tag to be configured for routes imported from ...
... RIP routes (routes for networks within the RIP routing domain) from "external" RIP routes, which may have been imported from an EGP or another IGP Routers supporting protocols other than RIP should be configurable to allow the Route Tag to be configured for routes imported from ...
Towards a Fail-Operational Intrusion Detection System for In
... of a Tesla Model S covered on Wired.com. The automotive industry has slowly replaced much of the mechanical couplings between car components with electronics and software, because electronics are cheaper and lighter than their mechanical counter parts. In conjunction with the hardware, an automobile ...
... of a Tesla Model S covered on Wired.com. The automotive industry has slowly replaced much of the mechanical couplings between car components with electronics and software, because electronics are cheaper and lighter than their mechanical counter parts. In conjunction with the hardware, an automobile ...
Network Topologies
... Is self-healing and can still operate when one node breaks down or a connection goes bad ...
... Is self-healing and can still operate when one node breaks down or a connection goes bad ...
Traffic Measurement - Computer Science & Engineering
... • Measurement tools can also be classified as active or passive • Active: the monitoring tool generates traffic of its own during data collection (e.g., ping, pchar) • Passive: the monitoring tool is passive, observing and recording traffic info, while generating none of its own (e.g., ...
... • Measurement tools can also be classified as active or passive • Active: the monitoring tool generates traffic of its own during data collection (e.g., ping, pchar) • Passive: the monitoring tool is passive, observing and recording traffic info, while generating none of its own (e.g., ...
Security Trends Overview
... More Microsoft products being added over the next months Enterprise solutions, however, will still benefit from a fully-managed software distribution system, such as SMS (Systems Management Server) ...
... More Microsoft products being added over the next months Enterprise solutions, however, will still benefit from a fully-managed software distribution system, such as SMS (Systems Management Server) ...
networks: communicating and sharing resources
... size, called packets. Each packet is numbered and addressed to the destination computer. The sending computer pushes the packets onto the network, where routers examine the packets. Routers are devices that examine each packet they detect. After reading the packet’s address, the router consults a ta ...
... size, called packets. Each packet is numbered and addressed to the destination computer. The sending computer pushes the packets onto the network, where routers examine the packets. Routers are devices that examine each packet they detect. After reading the packet’s address, the router consults a ta ...
New services call for new financial networks TextStart With China`s
... network that consists of three parts: a tier-2 backbone network, a tier-1 branch LAN, and an intra-city access network. It was designed to provide always-on connectivity using efficient, secure, and reliable high-bandwidth bearing capabilities, so as to ensure banks were able to provide quality serv ...
... network that consists of three parts: a tier-2 backbone network, a tier-1 branch LAN, and an intra-city access network. It was designed to provide always-on connectivity using efficient, secure, and reliable high-bandwidth bearing capabilities, so as to ensure banks were able to provide quality serv ...
Improve exploration, production and refining with 'add at will' wireless automation
... 802.11 Wi-Fi access point coverage that would integrate (or “backhaul”) smaller wireless field networks (Fig. 2). Process measurement and control instruments would be added to the field networks and communicate using IEC 62591 (WirelessHART) technology. The plant-wide network development began with ...
... 802.11 Wi-Fi access point coverage that would integrate (or “backhaul”) smaller wireless field networks (Fig. 2). Process measurement and control instruments would be added to the field networks and communicate using IEC 62591 (WirelessHART) technology. The plant-wide network development began with ...
Ch08
... • Fragmentation only allowed at source • No fragmentation at intermediate routers • Node must perform path discovery to find smallest MTU of intermediate networks • Source fragments to match MTU • Otherwise limit to 1280 octets ...
... • Fragmentation only allowed at source • No fragmentation at intermediate routers • Node must perform path discovery to find smallest MTU of intermediate networks • Source fragments to match MTU • Otherwise limit to 1280 octets ...
NCL1135 Configuration
... data from the backhaul and fans it out to multiple CCUs • GUI configured ...
... data from the backhaul and fans it out to multiple CCUs • GUI configured ...
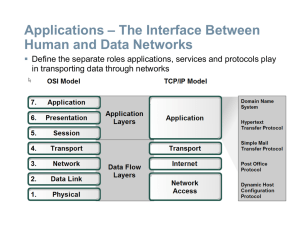
Application Layer Functionality and Protocols
... Identify two media access control methods for shared media and the basic characteristics of each ...
... Identify two media access control methods for shared media and the basic characteristics of each ...
PPT Version
... confining EAP for configuration to network access keys only – Now, IP address information is configured also – What else will drive through that hole? ...
... confining EAP for configuration to network access keys only – Now, IP address information is configured also – What else will drive through that hole? ...
OSPF - Suraj @ LUMS
... A router sends a link state advertisement to the designated router only using 224.0.0.6 “all designated routers” multicast address If advertisement is new, designated router floods the link state on all its interfaces (including the network on which it is received!) using 224.0.0.5 “all OSPF routers ...
... A router sends a link state advertisement to the designated router only using 224.0.0.6 “all designated routers” multicast address If advertisement is new, designated router floods the link state on all its interfaces (including the network on which it is received!) using 224.0.0.5 “all OSPF routers ...
ppt - Suraj @ LUMS
... A router sends a link state advertisement to the designated router only using 224.0.0.6 “all designated routers” multicast address If advertisement is new, designated router floods the link state on all its interfaces (including the network on which it is received!) using 224.0.0.5 “all OSPF routers ...
... A router sends a link state advertisement to the designated router only using 224.0.0.6 “all designated routers” multicast address If advertisement is new, designated router floods the link state on all its interfaces (including the network on which it is received!) using 224.0.0.5 “all OSPF routers ...
cos440-Intro
... • Functions are allocated to specific layers • The set of layers and their definitions is called the network architecture • Set of protocols is called the protocol stack ...
... • Functions are allocated to specific layers • The set of layers and their definitions is called the network architecture • Set of protocols is called the protocol stack ...
common Network Information Service Modelling and interacting with
... NMWG (Network Measurement Working Group) ...
... NMWG (Network Measurement Working Group) ...
Security Attacks
... Framing: Group bits into frames (packets) Arbitration: multiple senders, one resource Addressing: multiple receivers, one wire ...
... Framing: Group bits into frames (packets) Arbitration: multiple senders, one resource Addressing: multiple receivers, one wire ...
Chapter 6 Slides
... – WLANs can have multiple access points • Reassociation: station changes access points ...
... – WLANs can have multiple access points • Reassociation: station changes access points ...