Slajd 1 - CONFidence 2016
... Malwr is a free malware analysis service and community launched in January 2011. You can submit files to it and receive the results of a complete dynamic analysis back. ...
... Malwr is a free malware analysis service and community launched in January 2011. You can submit files to it and receive the results of a complete dynamic analysis back. ...
BLUETOOTH TECHNOLOGY/SECURITY Prepared By: Lo`ai Hattar
... A piconet • is an ad-hoc computer network of devices using Bluetooth technology protocols to allow one master device to interconnect with up to seven active slave devices • Up to 255 further slave devices can be inactive, or parked, which the master device can bring into active status at any time. ...
... A piconet • is an ad-hoc computer network of devices using Bluetooth technology protocols to allow one master device to interconnect with up to seven active slave devices • Up to 255 further slave devices can be inactive, or parked, which the master device can bring into active status at any time. ...
IPv6 in Greek School Network (GSN) - seeren-2
... Upgrade IOS in routers ONLY (not in switches) ...
... Upgrade IOS in routers ONLY (not in switches) ...
Why you still need an MPLS VPN White Paper Executive Summary
... applications that are collaborative in nature. These apps need the ability to run directly between any two sites, rather than through a hub site before jumping off to the receiving site, to achieve the low latency required for real-time communications to work properly. Vulnerable to DDOS Even if you ...
... applications that are collaborative in nature. These apps need the ability to run directly between any two sites, rather than through a hub site before jumping off to the receiving site, to achieve the low latency required for real-time communications to work properly. Vulnerable to DDOS Even if you ...
SmartRE: An Architecture for Coordinated Network
... Processing constraints MemOps & DRAM speed 2GB cache per RE device ...
... Processing constraints MemOps & DRAM speed 2GB cache per RE device ...
Easy Steps to Cisco Extended Access List
... based on source and destination IP address, port numbers and upper-layer protocols. Standard access list can deny or permit packets by source address only and permit or deny entire TCP/IP protocol suite. Therefore by extended, it means greater functionality and flexibility. Extended access list is a ...
... based on source and destination IP address, port numbers and upper-layer protocols. Standard access list can deny or permit packets by source address only and permit or deny entire TCP/IP protocol suite. Therefore by extended, it means greater functionality and flexibility. Extended access list is a ...
Wireless Access Point Router with 4-Port Switch
... other device on the network. Since a static IP address remains valid until you disable it, static IP addressing insures that the device assigned it will have that same IP address until you change it. Static IP addresses are commonly used with network devices such as server PCs or print servers. If y ...
... other device on the network. Since a static IP address remains valid until you disable it, static IP addressing insures that the device assigned it will have that same IP address until you change it. Static IP addresses are commonly used with network devices such as server PCs or print servers. If y ...
the osi model
... certain amount of time the sending PC would resend the Data. Waiting for an acknowledgement of receipt of data takes extra time but is critical in making sure that all the information makes it to its destination. There are other Protocols that don’t require acknowledgement (UDP) but the transmission ...
... certain amount of time the sending PC would resend the Data. Waiting for an acknowledgement of receipt of data takes extra time but is critical in making sure that all the information makes it to its destination. There are other Protocols that don’t require acknowledgement (UDP) but the transmission ...
Heterogeneous wireless network management
... to determine what network interface is most suitable for the application needs and how to manage its power and performance states. When an application starts on a portable device, PPM pre-selects those WNICs for data communication whose average throughput is greater than the data consumption rate of ...
... to determine what network interface is most suitable for the application needs and how to manage its power and performance states. When an application starts on a portable device, PPM pre-selects those WNICs for data communication whose average throughput is greater than the data consumption rate of ...
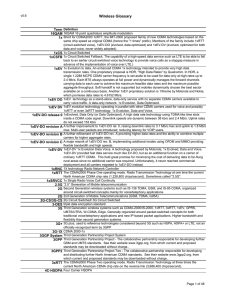
Computer Information Systems (Forensics Classes) Objectives for
... Demonstrate an understanding of a code of ethics and conduct related to the information security and digital forensics professions. • Identify standards of professionalism an ethical behavior for information security and digital forensics professional and apply these standards successfully to ethica ...
... Demonstrate an understanding of a code of ethics and conduct related to the information security and digital forensics professions. • Identify standards of professionalism an ethical behavior for information security and digital forensics professional and apply these standards successfully to ethica ...
media access control - Faculty
... The Layer 2 protocol used for a particular network topology is determined by - the technology used to implement that topology. - the size of the network – -the number of hosts -the geographic scope - the services to be provided over the network. ...
... The Layer 2 protocol used for a particular network topology is determined by - the technology used to implement that topology. - the size of the network – -the number of hosts -the geographic scope - the services to be provided over the network. ...
lecture24
... node and distance and next-hop values for each destination node in the system A node must transmit large amounts of information ...
... node and distance and next-hop values for each destination node in the system A node must transmit large amounts of information ...
Switching Techniques: Circuit Switching Message Switching packet
... Data rate conversion is possible. ...
... Data rate conversion is possible. ...
Intel® Ethernet Server Adapters I350
... traveling to the same destination (or virtual machine) get grouped together in a single queue. The packets are then sent to the hypervisor, which directs them to their respective virtual machines. Relieving the hypervisor of packet filtering and sorting improves overall CPU usage and through-put lev ...
... traveling to the same destination (or virtual machine) get grouped together in a single queue. The packets are then sent to the hypervisor, which directs them to their respective virtual machines. Relieving the hypervisor of packet filtering and sorting improves overall CPU usage and through-put lev ...
Slide 1
... • Dynamic host configuration protocol (DHCP) allows a host to obtain an IP address dynamically without the network administrator having to set up an individual profile for each device. • All that is required when using DHCP is a defined range of IP addresses on a DHCP server. • The major advantage t ...
... • Dynamic host configuration protocol (DHCP) allows a host to obtain an IP address dynamically without the network administrator having to set up an individual profile for each device. • All that is required when using DHCP is a defined range of IP addresses on a DHCP server. • The major advantage t ...
To Transmit or Not to Transmit? Distributed Queueing Games in
... interference to each other. The resulting (time-varying, frequency- and location-dependent) coupling in the transmission strategies makes the formulation and analysis of the distributed queueing resource allocation problem a complicated and, to the best of our knowledge, unexplored design. This pape ...
... interference to each other. The resulting (time-varying, frequency- and location-dependent) coupling in the transmission strategies makes the formulation and analysis of the distributed queueing resource allocation problem a complicated and, to the best of our knowledge, unexplored design. This pape ...
Note
... inet_aton() converts the Internet host address cp from the standard numbers-and-dots notation into binary data and stores it in the structure that inp points to. inet_aton() returns non-zero if the address is valid, zero if not. The inet_addr() function converts the Internet host address cp from num ...
... inet_aton() converts the Internet host address cp from the standard numbers-and-dots notation into binary data and stores it in the structure that inp points to. inet_aton() returns non-zero if the address is valid, zero if not. The inet_addr() function converts the Internet host address cp from num ...
Slide 1
... Internet peers organize themselves into an overlay tree on top of the Internet. Packet replication and forwarding are performed by peers in the application layer by using IP unicast service. ...
... Internet peers organize themselves into an overlay tree on top of the Internet. Packet replication and forwarding are performed by peers in the application layer by using IP unicast service. ...
Project Summary
... At the conclusion of the final phase, NKN shall have presence in more than 500 districts of India with connectivity to major research and education institutions. ...
... At the conclusion of the final phase, NKN shall have presence in more than 500 districts of India with connectivity to major research and education institutions. ...
Saimaa University of Applied Sciences Technology, Lappeenranta Mechanical Engineering and Production Technology
... - Direct and simultaneous access to resources (including valuable information) a great number of users of various categories; - Varity of different hardware and software; - Absence of special protection utilities that could be used in specific computer network. Generally computer network system cons ...
... - Direct and simultaneous access to resources (including valuable information) a great number of users of various categories; - Varity of different hardware and software; - Absence of special protection utilities that could be used in specific computer network. Generally computer network system cons ...