Lecture 11
... – Usually stored on the computer using the wireless network – 24 bit IV also used • Used checksum for integrity CS 136, Fall 2012 ...
... – Usually stored on the computer using the wireless network – 24 bit IV also used • Used checksum for integrity CS 136, Fall 2012 ...
Development of Network Interface Card (NIC) RT
... diskless and let the board find one on the network. The procedure for building both is same - the difference is in where to put and how to find them using kernel. BusyBox was configured and installed by downloading it from the figure 8. The first step is configuration of the BusyBox [6]. 3.10 Proced ...
... diskless and let the board find one on the network. The procedure for building both is same - the difference is in where to put and how to find them using kernel. BusyBox was configured and installed by downloading it from the figure 8. The first step is configuration of the BusyBox [6]. 3.10 Proced ...
PART II: Multi-layer TE in Metropolitan Area Networks
... coordination signals between layers is required. It is also simple from the operational point of view. The most important drawback is that multiple layers can start the recovery action contemporarily leading in such a way to potential networks instability (above all at the higher network layers) and ...
... coordination signals between layers is required. It is also simple from the operational point of view. The most important drawback is that multiple layers can start the recovery action contemporarily leading in such a way to potential networks instability (above all at the higher network layers) and ...
IP MULTICAST
... source S to group G, it first checks in the standard unicast routing table that the incoming interface is the one that is used for sending unicast packets toward S. If this is not the case, it drops the packets and sends back a “prune (S,G)” message on the incoming interface. • The router will then ...
... source S to group G, it first checks in the standard unicast routing table that the incoming interface is the one that is used for sending unicast packets toward S. If this is not the case, it drops the packets and sends back a “prune (S,G)” message on the incoming interface. • The router will then ...
Fulltext - Brunel University Research Archive
... the events. When the flows are monitored the entire event, whether they occur only frequently or periodically, are stored in the database to be used in the ANN learning system, and consequently the data which are collected from the ANN learning system is considered as being an efficient input to the ...
... the events. When the flows are monitored the entire event, whether they occur only frequently or periodically, are stored in the database to be used in the ANN learning system, and consequently the data which are collected from the ANN learning system is considered as being an efficient input to the ...
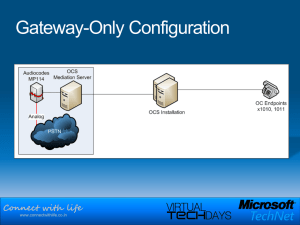
Connect with life
... © 2007 Microsoft Corporation. All rights reserved. Microsoft, Windows, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U.S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microso ...
... © 2007 Microsoft Corporation. All rights reserved. Microsoft, Windows, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U.S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microso ...
Ethernet - Mt. Hood Community College
... PC sends packet to server Packet header has PC IP address and source and server IP address as destination. Frame header has PC MAC address as source and router MAC address as destination. ...
... PC sends packet to server Packet header has PC IP address and source and server IP address as destination. Frame header has PC MAC address as source and router MAC address as destination. ...
Chapter 5 part 2 - Distributed Computing Group
... + Bridge tables are self learning – All traffic confined to spanning tree, even when alternative bandwidth is available – Bridges do not offer protection from broadcast storms ...
... + Bridge tables are self learning – All traffic confined to spanning tree, even when alternative bandwidth is available – Bridges do not offer protection from broadcast storms ...
Transport Layer, Congestion Control
... Use probes to estimate level of congestion Speed up when congestion is low Slow down when congestion increases ...
... Use probes to estimate level of congestion Speed up when congestion is low Slow down when congestion increases ...
Effects on TCP of Routing Strategies in Satellite Constellations
... congestion, and the congestion window is reduced, the return to the previous high rate of throughput is slowed by the large RTT. In both cases, increasing the congestion window takes a number of slow 0.5-s roundtrips, and the capacity of an expensive satellite link will not be fully used as a result ...
... congestion, and the congestion window is reduced, the return to the previous high rate of throughput is slowed by the large RTT. In both cases, increasing the congestion window takes a number of slow 0.5-s roundtrips, and the capacity of an expensive satellite link will not be fully used as a result ...
DWG875/DWG875T - Wireless Voice Gateway User manual CABLE SATELLITE
... and recycling system for which producers' are responsible. This appliance has been designed and manufactured with high quality materials and components that can be recycled and reused. Electrical and electronic appliances are liable to contain parts that are necessary in order for the system to work ...
... and recycling system for which producers' are responsible. This appliance has been designed and manufactured with high quality materials and components that can be recycled and reused. Electrical and electronic appliances are liable to contain parts that are necessary in order for the system to work ...
A Distributed Reputation Approach to Cooperative Internet Routing Protection
... initiate queries in the form of a boolean bit-string, also called a proposition. For example, a node can broadcast the simple proposition “Is AS3 → AS7 a spoofed edge?” and solicit responses from other peers in the network. A response is simply a vote cast in ternary fashion (−1, 0, +1): -1 indicate ...
... initiate queries in the form of a boolean bit-string, also called a proposition. For example, a node can broadcast the simple proposition “Is AS3 → AS7 a spoofed edge?” and solicit responses from other peers in the network. A response is simply a vote cast in ternary fashion (−1, 0, +1): -1 indicate ...
VERA: An Extensible Router Architecture Scott Karlin and Larry Peterson
... support beyond the traditional forwarding service. For example, routers are programmed to filter packets, translate addresses, make level-n routing decisions, broker quality of service (QoS) reservations, thin data streams, run proxies, support computationally-weak home electronic devices, serve as ...
... support beyond the traditional forwarding service. For example, routers are programmed to filter packets, translate addresses, make level-n routing decisions, broker quality of service (QoS) reservations, thin data streams, run proxies, support computationally-weak home electronic devices, serve as ...
FAQ Sprint 3G/4G USB Modem U300
... • If a message that you must restart your computer is displayed, click Yes to restart you computer. Wait until your computer restarts to launch Sprint SmartView. Q: Where can I get the latest version of the Sprint SmartView software for my U300 USB modem? A: Users can initiate an update to the lates ...
... • If a message that you must restart your computer is displayed, click Yes to restart you computer. Wait until your computer restarts to launch Sprint SmartView. Q: Where can I get the latest version of the Sprint SmartView software for my U300 USB modem? A: Users can initiate an update to the lates ...
Multilayer Networks: An Architecture Framework
... and processes that are responsible for providing services to users and maintaining state on those services. The ServicePlane will generally rely on the functions of the ControlPlane and/or ManagementPlane to effect actual changes on the DataPlane. In addition, the ServicePlane will typically maintai ...
... and processes that are responsible for providing services to users and maintaining state on those services. The ServicePlane will generally rely on the functions of the ControlPlane and/or ManagementPlane to effect actual changes on the DataPlane. In addition, the ServicePlane will typically maintai ...
Router Design for Scalable and Efficient Regional Registration
... should move with the roaming user. Per-user integrated location and service management in PCS networks A per-user service proxy is created to serve as a gateway between the mobile user and all client-server applications The service proxy co-located with location database. When there is a loc ...
... should move with the roaming user. Per-user integrated location and service management in PCS networks A per-user service proxy is created to serve as a gateway between the mobile user and all client-server applications The service proxy co-located with location database. When there is a loc ...
Broadband Access Systems, Inc. Cuda 12000 IP
... test common IP traffic. Furthermore, engineers tested 108- and 200-byte packets to test the capability of the Cuda 12000 IP Access Switch when forwarding packet sizes commonly found in packetized voice solutions. Testing was performed in May 2000. ...
... test common IP traffic. Furthermore, engineers tested 108- and 200-byte packets to test the capability of the Cuda 12000 IP Access Switch when forwarding packet sizes commonly found in packetized voice solutions. Testing was performed in May 2000. ...
2014 - Bhulabhai Vanmalibhai Patel Institute of Business
... In broadcasting only one can send and more than one can receive. Print server allow user to share fax services over a network. Wide area network are connected across a distance of less than 30 miles. Networks cannot extend beyond the boundaries of a building. LANs typically connect separate offices ...
... In broadcasting only one can send and more than one can receive. Print server allow user to share fax services over a network. Wide area network are connected across a distance of less than 30 miles. Networks cannot extend beyond the boundaries of a building. LANs typically connect separate offices ...
Internet - Heartland Community College
... addresses of all packets transmitted to it to determine the best next path for the data to take to its destination. The router stores information in a routing table about the other routers and networks to which it is connected and about any nearby networks. This information is compared to the de ...
... addresses of all packets transmitted to it to determine the best next path for the data to take to its destination. The router stores information in a routing table about the other routers and networks to which it is connected and about any nearby networks. This information is compared to the de ...
Set Title in 40pt. No more than 2 lines
... you can run multiple copies of the package Using the baseline of the package, you can now calculate how many scale servers you will need ...
... you can run multiple copies of the package Using the baseline of the package, you can now calculate how many scale servers you will need ...