Oracle EBS R12 - Security
... In today’s environment, a properly secured computing infrastructure is critical. When securing the infrastructure, a balance must be struck between risk of exposure, cost of security and value of the information protected. ...
... In today’s environment, a properly secured computing infrastructure is critical. When securing the infrastructure, a balance must be struck between risk of exposure, cost of security and value of the information protected. ...
Introduction to computer networkd #8
... communications logs, data security and privacy, and translation capabilities for networks. ...
... communications logs, data security and privacy, and translation capabilities for networks. ...
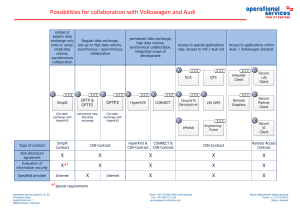
Possibilities for collaboration with Volkswagen
... Preconditions: · valid non-disclosure agreement · proof of an adequate level of information security ...
... Preconditions: · valid non-disclosure agreement · proof of an adequate level of information security ...
Defending Office 365 Against Denial-of-Service Attacks
... Microsoft’s DoS Defense Strategy Microsoft’s strategy for defending against DoS is somewhat unique due to our scale and global footprint. This scale allows Microsoft to utilize strategies and techniques that few organizations (providers or customer organizations) can match. The cornerstone of our Do ...
... Microsoft’s DoS Defense Strategy Microsoft’s strategy for defending against DoS is somewhat unique due to our scale and global footprint. This scale allows Microsoft to utilize strategies and techniques that few organizations (providers or customer organizations) can match. The cornerstone of our Do ...
Chapter 7 Powerpoints
... The internet is operated by the Internet Society, a non-profit, nongovernmental, professional society. This group establishes and enforces network protocol standards. ...
... The internet is operated by the Internet Society, a non-profit, nongovernmental, professional society. This group establishes and enforces network protocol standards. ...
pptx
... PON Passive Optical Network Optical splitters do not need electrical power. Hard to isolate failure Transmission speed may be slower during peak hours. Computer Networks ...
... PON Passive Optical Network Optical splitters do not need electrical power. Hard to isolate failure Transmission speed may be slower during peak hours. Computer Networks ...
PPTX - ME Kabay
... Private address space accessed by internal tables Limits determination of internal network size & topology Restricts access to specific endpoints Static NAT Manual, permanent assignment of IP address to each internal node Dynamic NAT Pool of addresses assigned as required Port Addres ...
... Private address space accessed by internal tables Limits determination of internal network size & topology Restricts access to specific endpoints Static NAT Manual, permanent assignment of IP address to each internal node Dynamic NAT Pool of addresses assigned as required Port Addres ...
Switched Broadcast 2003
... You can also set up your access so users need to use SSH, or other secure methods to authenticate on the trusted host before they can connect to the Console Server ...
... You can also set up your access so users need to use SSH, or other secure methods to authenticate on the trusted host before they can connect to the Console Server ...
Chapter4
... Our routing study thus far - idealization all routers identical network “flat” … not true in practice scale: with 200 million destinations: can’t store all dest’s in ...
... Our routing study thus far - idealization all routers identical network “flat” … not true in practice scale: with 200 million destinations: can’t store all dest’s in ...
Network Layer
... – AS-PATH collects a path to reach the network prefix Path information prevents routing loops from occurring Path information also provides information on the length of a path (By default, a shorter route is preferred) Note: BGP aggregates routes according to CIDR rules ...
... – AS-PATH collects a path to reach the network prefix Path information prevents routing loops from occurring Path information also provides information on the length of a path (By default, a shorter route is preferred) Note: BGP aggregates routes according to CIDR rules ...
The Internet and Its Uses
... The routing process requires the source device to determine if the destination device is local or remote to the local subnet. The source device accomplishes this by comparing the source and destination addresses against the subnet mask. Once the destination address has been determined to be on ...
... The routing process requires the source device to determine if the destination device is local or remote to the local subnet. The source device accomplishes this by comparing the source and destination addresses against the subnet mask. Once the destination address has been determined to be on ...
Palm Connectivity Part 8 - GPRS Setting for
... (Jul 03, 2005 at 11:54 AM) - Contributed by Dr Azmi Mohd Tamil - Last Updated (Oct 29, 2005 at 06:00 PM) ...
... (Jul 03, 2005 at 11:54 AM) - Contributed by Dr Azmi Mohd Tamil - Last Updated (Oct 29, 2005 at 06:00 PM) ...
Chapter 1
... • Used to connect routers to external networks, usually over a larger geographical distance. • The Layer 2 encapsulation can be different types (PPP, Frame Relay, HDLC (High-Level Data Link Control) ). • Similar to LAN interfaces, each WAN interface has its own IP address and subnet mask, making it ...
... • Used to connect routers to external networks, usually over a larger geographical distance. • The Layer 2 encapsulation can be different types (PPP, Frame Relay, HDLC (High-Level Data Link Control) ). • Similar to LAN interfaces, each WAN interface has its own IP address and subnet mask, making it ...
3rd Edition: Chapter 4
... A: ICANN: Internet Corporation for Assigned Names and Numbers allocates addresses manages DNS assigns domain names, resolves disputes ...
... A: ICANN: Internet Corporation for Assigned Names and Numbers allocates addresses manages DNS assigns domain names, resolves disputes ...
Managing security risks and vulnerabilities
... resolution to help improve their security posture. These solutions can generate meaningful data from activity associated with people, data, applications and infrastructure, and then pull all of that data into a single repository. What’s more, organizations can apply advanced analytics to that data—w ...
... resolution to help improve their security posture. These solutions can generate meaningful data from activity associated with people, data, applications and infrastructure, and then pull all of that data into a single repository. What’s more, organizations can apply advanced analytics to that data—w ...
an architectural survey
... subcomponents that interact through well-defined abstract interfaces - is often considered as a major success story of computer networking. The OSI layering model, however, relates mostly to the Internet’s data plane which has evolved to offer various useful abstractions [6]. The Internet’s control ...
... subcomponents that interact through well-defined abstract interfaces - is often considered as a major success story of computer networking. The OSI layering model, however, relates mostly to the Internet’s data plane which has evolved to offer various useful abstractions [6]. The Internet’s control ...
Model-T: Rethinking the OS for terabit speeds
... First, we replace the common model of having few coarsegrained tasks with one built from many smaller processing steps. These operations are not independent. Each operation executes a single step in the network stack, such as IP defragmentation, TCP port routing or HTTP gzip decompression. For each ...
... First, we replace the common model of having few coarsegrained tasks with one built from many smaller processing steps. These operations are not independent. Each operation executes a single step in the network stack, such as IP defragmentation, TCP port routing or HTTP gzip decompression. For each ...
Financial Reporting: The Institutional Setting
... Ensure strong password & password management. ...
... Ensure strong password & password management. ...
A Platform for Unobtrusive Measurements on PlanetLab Rob Sherwood Neil Spring Abstract
... should be enabled. Many of the results in Section 4 PlanetLab VNET worked with Sidecar. PlanetLab used connections from one PlanetLab machine to the web implements a connection tracking and traffic isolation sys- server of another PlanetLab machine as the source of extem called VNET [7] to prevent r ...
... should be enabled. Many of the results in Section 4 PlanetLab VNET worked with Sidecar. PlanetLab used connections from one PlanetLab machine to the web implements a connection tracking and traffic isolation sys- server of another PlanetLab machine as the source of extem called VNET [7] to prevent r ...
Metrics for Degree of Reordering in Packet Sequences
... without loss or duplication. Table 1 shows steps in computing displacements for RH. Initially, (see column 1) E, the expected sequence number is 1 and S, the arrived sequence number is also 1. The displacement value thus is 0 and hence frequency corresponding to displacement=0, F[0] becomes 1. For n ...
... without loss or duplication. Table 1 shows steps in computing displacements for RH. Initially, (see column 1) E, the expected sequence number is 1 and S, the arrived sequence number is also 1. The displacement value thus is 0 and hence frequency corresponding to displacement=0, F[0] becomes 1. For n ...
Chapter4_revised
... A: ICANN: Internet Corporation for Assigned Names and Numbers allocates addresses manages DNS assigns domain names, resolves disputes ...
... A: ICANN: Internet Corporation for Assigned Names and Numbers allocates addresses manages DNS assigns domain names, resolves disputes ...
PPT - Suraj @ LUMS
... Performing Link Adaption & ARQ functions Transmission Scheduling Admission Control Link Initialization Fragmentation and Retransmission ...
... Performing Link Adaption & ARQ functions Transmission Scheduling Admission Control Link Initialization Fragmentation and Retransmission ...
2. FSF-1 Sea Fighter - Engineering Informatics Group
... termed firmware, is stored within the microcontroller. The firmware includes two categories of software: first, an operating system (OS) is embedded for the configuration and operation of peripheral components on the sensor, as well as for real-time allocation of processing power. Second, applicatio ...
... termed firmware, is stored within the microcontroller. The firmware includes two categories of software: first, an operating system (OS) is embedded for the configuration and operation of peripheral components on the sensor, as well as for real-time allocation of processing power. Second, applicatio ...