ExtremeFabric - Extreme Forum 2017
... A Fabric wide LAG is dynamically formed to each host that attaches to the ExtremeFabric network with LACP ensbled. All ExtremeFabric nodes use the same chassis MAC so hosts running LACP will form a single LAG with the entire Fabric, as each host views the network of ExtremeFabric nodes as a single ...
... A Fabric wide LAG is dynamically formed to each host that attaches to the ExtremeFabric network with LACP ensbled. All ExtremeFabric nodes use the same chassis MAC so hosts running LACP will form a single LAG with the entire Fabric, as each host views the network of ExtremeFabric nodes as a single ...
IoT in Future Internet2
... to the AAID node, or vice versa – Mobility/Multi-homing bit (M): This tells the AAID gateway to check with the other AAID gateways, through the back end or the overlay, that this node does not have pending sessions from another location. – IP source format (IP S): These bits indicate the IP source a ...
... to the AAID node, or vice versa – Mobility/Multi-homing bit (M): This tells the AAID gateway to check with the other AAID gateways, through the back end or the overlay, that this node does not have pending sessions from another location. – IP source format (IP S): These bits indicate the IP source a ...
PowerPoint - The Exchange Network
... • Also available is a C# client library (.zip file). This allows you to change the requestor library above. If you don't want to change the API, you should download the .NET Sample Client. Requires the .NET Framework 1.X and 1sp1. ...
... • Also available is a C# client library (.zip file). This allows you to change the requestor library above. If you don't want to change the API, you should download the .NET Sample Client. Requires the .NET Framework 1.X and 1sp1. ...
SNMP Simple Network Management Protocol
... •Two major versions SNMPv1, SNMPv2 •SNMPv1 is the recommended standard •SNMPv2 has become split into: •SNMPv2u - SNMPv2 with user-based security •SNMPv2* - SNMPv2 with user-based security and additional features •SNMPv2c - SNMPv2 without security ...
... •Two major versions SNMPv1, SNMPv2 •SNMPv1 is the recommended standard •SNMPv2 has become split into: •SNMPv2u - SNMPv2 with user-based security •SNMPv2* - SNMPv2 with user-based security and additional features •SNMPv2c - SNMPv2 without security ...
IP connectivity access network
... to inter-domain roaming between IMS and CS when a user is not registered or reachable in one domain a session can be routed to the other domain both the CS CN domain and the IMS domain have their own services and cannot be used from another domain some services are similar and available in bot ...
... to inter-domain roaming between IMS and CS when a user is not registered or reachable in one domain a session can be routed to the other domain both the CS CN domain and the IMS domain have their own services and cannot be used from another domain some services are similar and available in bot ...
Reassembling
... Answer: False. There is one instance in which a proxy server should be directly accessible to the Internet: if it is a reverse proxy acting on behalf of one or more Web servers. In this case the reverse proxy receives HTTP requests from external clients and forwards them to the actual Web server(s). ...
... Answer: False. There is one instance in which a proxy server should be directly accessible to the Internet: if it is a reverse proxy acting on behalf of one or more Web servers. In this case the reverse proxy receives HTTP requests from external clients and forwards them to the actual Web server(s). ...
PPT Version
... • Link Down, Packets Discarded too scary – Because notifications aren’t authenticated ...
... • Link Down, Packets Discarded too scary – Because notifications aren’t authenticated ...
ICN`13 ~ NLSR: Named-Data Link State Routing Protocol
... it advertises name prefixes from both static configuration and dynamic registration by local content producers. Whenever any name prefix is added or deleted, it also disseminates a new LSA. The latest version of the LSAs are stored in a Link State Database (LSDB) at each node. Such topology and reac ...
... it advertises name prefixes from both static configuration and dynamic registration by local content producers. Whenever any name prefix is added or deleted, it also disseminates a new LSA. The latest version of the LSAs are stored in a Link State Database (LSDB) at each node. Such topology and reac ...
Chapter 15. Recent advances
... the FEC, often enabling a receiver to reconstruct the original packet. In the event that such information is not enough, an ARQ is sent to the multicast source which in turn, multicasts the requested packet to all receivers. ...
... the FEC, often enabling a receiver to reconstruct the original packet. In the event that such information is not enough, an ARQ is sent to the multicast source which in turn, multicasts the requested packet to all receivers. ...
IEEE C80216m-08/880r3 Project Title
... When transmitting RNG-RSP, BS can further ensure confidentiality in either one of two ways. One, would be for BS to transmit the hashed MAC address in RNG-RSP message. It is then up to the SS/MS to verify the hashed MAC address upon receiving the RNG-RSP. The other method would be for the BS to not ...
... When transmitting RNG-RSP, BS can further ensure confidentiality in either one of two ways. One, would be for BS to transmit the hashed MAC address in RNG-RSP message. It is then up to the SS/MS to verify the hashed MAC address upon receiving the RNG-RSP. The other method would be for the BS to not ...
Chapter 1
... • Thanks must go out to Rick Graziani of Cabrillo College. His material and additional information was used as a reference in their creation. • If anyone finds any errors or omissions, please let me know at: • [email protected]. ...
... • Thanks must go out to Rick Graziani of Cabrillo College. His material and additional information was used as a reference in their creation. • If anyone finds any errors or omissions, please let me know at: • [email protected]. ...
Common meeting of CERN DAQ teams
... sub-detectors in LHCb Up to 48 optical / copper analogue input links from the detector @ 1.6 GBit/s Preprocessing, zerosuppression and dataformatting in large FPGAs Data are sent directly to the Event Filter Farm via a 4channel Gigabit Ethernet plugin-card (developed by ...
... sub-detectors in LHCb Up to 48 optical / copper analogue input links from the detector @ 1.6 GBit/s Preprocessing, zerosuppression and dataformatting in large FPGAs Data are sent directly to the Event Filter Farm via a 4channel Gigabit Ethernet plugin-card (developed by ...
Introduction to Computers
... Connect computers together so that they can communicate, exchange information, and pool resources. Are connected by nodes Categories ...
... Connect computers together so that they can communicate, exchange information, and pool resources. Are connected by nodes Categories ...
evesecures9
... ◦ New Jan ’08 Federal Law requires that all data related to lawsuits (like a hiring discrimination lawsuit) must physically be put into secure locations ...
... ◦ New Jan ’08 Federal Law requires that all data related to lawsuits (like a hiring discrimination lawsuit) must physically be put into secure locations ...
Network File System (NFS)
... protocol is ubiquitous and supported generally by every UNIX-like variant, as well as being supported by operating systems by Microsoft and Apple. The system provides a system for permission management, as well as user and role-based access controls. The protocol dates itself to the 1980’s, with the ...
... protocol is ubiquitous and supported generally by every UNIX-like variant, as well as being supported by operating systems by Microsoft and Apple. The system provides a system for permission management, as well as user and role-based access controls. The protocol dates itself to the 1980’s, with the ...
E1 Protection Fail
... User configurable. May be used for a single E1 link and scaled upto 4 E1 links though user configuration ...
... User configurable. May be used for a single E1 link and scaled upto 4 E1 links though user configuration ...
3rd Edition, Chapter 5
... VC transport: cells carried on VC from source to dest call setup, teardown for each call before data can flow each packet carries VC identifier (not destination ID) every switch on source-dest path maintain “state” for each ...
... VC transport: cells carried on VC from source to dest call setup, teardown for each call before data can flow each packet carries VC identifier (not destination ID) every switch on source-dest path maintain “state” for each ...
RuggedBackbone™ RX1500/1501
... OSPF is a routing protocol that determines the best path for routing IP traffic over a TCP/IP network based on link states between nodes and several quality parameters. OSPF is an interior gateway protocol (IGP), which is designed to work within an autonomous system. It is also a link state protocol ...
... OSPF is a routing protocol that determines the best path for routing IP traffic over a TCP/IP network based on link states between nodes and several quality parameters. OSPF is an interior gateway protocol (IGP), which is designed to work within an autonomous system. It is also a link state protocol ...
II. Background on ad-hoc networking protocols used
... For OLSR, the implementation developed by Tønnesen [11] was used. This implementation is commonly called olsr.org and is now part of the largest open source ad hoc networking development. Version 0.4.10 is used in the massive mesh version. This implementation is RFC3626 compliant and is capable of u ...
... For OLSR, the implementation developed by Tønnesen [11] was used. This implementation is commonly called olsr.org and is now part of the largest open source ad hoc networking development. Version 0.4.10 is used in the massive mesh version. This implementation is RFC3626 compliant and is capable of u ...
Chapter 4 Network Layer CMPT 371 Data Communications
... call setup, teardown for each call before data can flow each packet carries VC identifier (not destination host ID) every router on source-dest path maintains “state” for ...
... call setup, teardown for each call before data can flow each packet carries VC identifier (not destination host ID) every router on source-dest path maintains “state” for ...
oneM2M High Level Overview
... confidentiality, integrity, availability, credential/key management, encryption, privacy, authentication, authorization ...
... confidentiality, integrity, availability, credential/key management, encryption, privacy, authentication, authorization ...
3rd Edition: Chapter 4
... A: ICANN: Internet Corporation for Assigned Names and Numbers allocates addresses manages DNS assigns domain names, resolves disputes ...
... A: ICANN: Internet Corporation for Assigned Names and Numbers allocates addresses manages DNS assigns domain names, resolves disputes ...
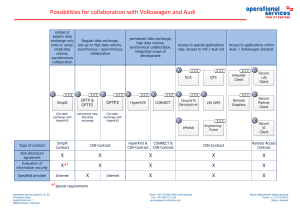
Possibilities for collaboration with Volkswagen
... Preconditions: · valid non-disclosure agreement · proof of an adequate level of information security ...
... Preconditions: · valid non-disclosure agreement · proof of an adequate level of information security ...