Access Point
... Short for Access Point, a hardware device or a computer's software that acts as a communication hub for users of a wireless device to connect to a wired LAN. ...
... Short for Access Point, a hardware device or a computer's software that acts as a communication hub for users of a wireless device to connect to a wired LAN. ...
Presentation - UWC Computer Science
... A wireless network integrated with wireless fidelity (Wi-Fi) ...
... A wireless network integrated with wireless fidelity (Wi-Fi) ...
WLAN and IEEE 802.11 Security
... – Access Control: Prevent inappropriate use of 802.11 network, such as facilitate dropping of not-authorized packets – Data Integrity: Ensure that messages are not altered or tampered with in transit ...
... – Access Control: Prevent inappropriate use of 802.11 network, such as facilitate dropping of not-authorized packets – Data Integrity: Ensure that messages are not altered or tampered with in transit ...
Home Networking
... Wireless Access Point (WAP) Transfers data received over wireless through wired network to Internet and back Default configuration works on most networks Best to enable security features ...
... Wireless Access Point (WAP) Transfers data received over wireless through wired network to Internet and back Default configuration works on most networks Best to enable security features ...
Chapter 3 E-business infrastructure
... The Internet refers to the physical network that links computers across the globe. It consists of the infrastructure of network servers and communication links between them that are used to hold and transport information between the client PCs and web servers. World Wide Web (WWW) The most common te ...
... The Internet refers to the physical network that links computers across the globe. It consists of the infrastructure of network servers and communication links between them that are used to hold and transport information between the client PCs and web servers. World Wide Web (WWW) The most common te ...
LAB 1 Basic Networking Commands
... Port address: every host has 65,535 ports each of which can be connected to a specific application that sends and receives data packets from the network. Gateway address: every host needs to know the address of the router which connects a network to other networks and the Internet. Domain name: host ...
... Port address: every host has 65,535 ports each of which can be connected to a specific application that sends and receives data packets from the network. Gateway address: every host needs to know the address of the router which connects a network to other networks and the Internet. Domain name: host ...
Sensor Networks
... some standard mechanism for communication! – Requires compatible wireless technology – Standardization a common theme • TCP/IP for the Internet • Java for Internet programming • Jini, SLP, etc. for 802.11 wireless devices ...
... some standard mechanism for communication! – Requires compatible wireless technology – Standardization a common theme • TCP/IP for the Internet • Java for Internet programming • Jini, SLP, etc. for 802.11 wireless devices ...
eHealth Network Monitoring
... Purpose of Monitoring Network monitoring is a method of efficiently ...
... Purpose of Monitoring Network monitoring is a method of efficiently ...
Network Initiated Handovers
... Performing network initiated handover has the main implication that the network has first to assess the terminal view of the network. Signal level evaluation is a important matter when coming down to user mobility. ...
... Performing network initiated handover has the main implication that the network has first to assess the terminal view of the network. Signal level evaluation is a important matter when coming down to user mobility. ...
Wireless Networks
... How are computer networks classified? Networks can be classified according to their size and geographic scope. A PAN.---- (personal area network) refers to the interconnection of personal digital devices within a range of about 30 feel and without the use of wires or ...
... How are computer networks classified? Networks can be classified according to their size and geographic scope. A PAN.---- (personal area network) refers to the interconnection of personal digital devices within a range of about 30 feel and without the use of wires or ...
Slides
... performance on both sides of the network. You might say that the bridge is like a traffic cop at a busy intersection during rush hour. It keeps information flowing on both sides of the network, but it does not allow unnecessary traffic through. Bridges can be used to connect different types of cabli ...
... performance on both sides of the network. You might say that the bridge is like a traffic cop at a busy intersection during rush hour. It keeps information flowing on both sides of the network, but it does not allow unnecessary traffic through. Bridges can be used to connect different types of cabli ...
Firewalls
... • Everything possible is done to hide the identy if the internal user – e-mail addresses in the http headers are not propigated through the proxy10 ...
... • Everything possible is done to hide the identy if the internal user – e-mail addresses in the http headers are not propigated through the proxy10 ...
Firewalls
... • Everything possible is done to hide the identy if the internal user – e-mail addresses in the http headers are not propigated through the proxy10 ...
... • Everything possible is done to hide the identy if the internal user – e-mail addresses in the http headers are not propigated through the proxy10 ...
DHCP Server Configuration - Brookdale Community College
... provided to enable DHCP Server functionality. • Subnet Mask: This field is read-only and reports the Access Point.s current subnet mask. DHCP clients that receive dynamic addresses from the AP will be assigned this same subnet mask. • Gateway IP Address: The AP will assign the specified address to i ...
... provided to enable DHCP Server functionality. • Subnet Mask: This field is read-only and reports the Access Point.s current subnet mask. DHCP clients that receive dynamic addresses from the AP will be assigned this same subnet mask. • Gateway IP Address: The AP will assign the specified address to i ...
tutorial 1 - UniMAP Portal
... in a mailbox to the time the letter is delivered to its destination. What role do names, addresses and mail codes play? How might the letter be routed to its destination? To what extent can the process be automated? 1b. Repeat part (a) for an e-mail message. At this point, you may have to conjecture ...
... in a mailbox to the time the letter is delivered to its destination. What role do names, addresses and mail codes play? How might the letter be routed to its destination? To what extent can the process be automated? 1b. Repeat part (a) for an e-mail message. At this point, you may have to conjecture ...
Document
... Need for networking: Resource sharing (Processing, Peripherals, Information and software) Personal or national or worldwide communication Information discovery and retrieval A brief history of computer networks: The first computer network was jointly designed by the Advanced Research Proje ...
... Need for networking: Resource sharing (Processing, Peripherals, Information and software) Personal or national or worldwide communication Information discovery and retrieval A brief history of computer networks: The first computer network was jointly designed by the Advanced Research Proje ...
Chapter 4 - HFT 3444
... • The manner in which workstations are connected together physically and logically is referred to as a NETWORK ...
... • The manner in which workstations are connected together physically and logically is referred to as a NETWORK ...
International Journal of Advance Research, IJOAR .org
... .Quality of Service enables a network administrator guarantee a minimum bandwidth for certain classes of traffic and limit the maximum bandwidth for certain classes of traffic. It is the integral part of wired and wireless Local Area Network. Quality of Service has been checked for both networks. Va ...
... .Quality of Service enables a network administrator guarantee a minimum bandwidth for certain classes of traffic and limit the maximum bandwidth for certain classes of traffic. It is the integral part of wired and wireless Local Area Network. Quality of Service has been checked for both networks. Va ...
Slide 1
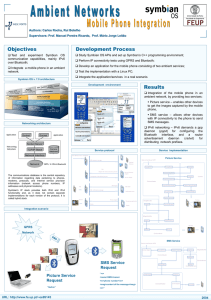
... The communications database is the central repository of information regarding data pertaining to phones, modems, protocols, and Internet service provision information (network access phone numbers, IP addresses and physical locations). Symbian’s IP stack provides both IPv6 and IPv4 functionality an ...
... The communications database is the central repository of information regarding data pertaining to phones, modems, protocols, and Internet service provision information (network access phone numbers, IP addresses and physical locations). Symbian’s IP stack provides both IPv6 and IPv4 functionality an ...
Light-Fidelity (Li-Fi) Revelution and How Radio Waves Can Help Li
... to 5G Visible Light Communication systems using Light Emitting Diodes as a medium to high-speed communication in a similar manner as Wi-Fi [3]. It can help to conserve a large amount of electricity by transmitting data through light bulbs and other such lighting equipments. It can be used in aircraf ...
... to 5G Visible Light Communication systems using Light Emitting Diodes as a medium to high-speed communication in a similar manner as Wi-Fi [3]. It can help to conserve a large amount of electricity by transmitting data through light bulbs and other such lighting equipments. It can be used in aircraf ...
Panel 7 Maritime Transportation Logistics & Security Nov. 17, 2010
... • Operations • Technical Support • Network Security ...
... • Operations • Technical Support • Network Security ...