Wireless Communication
... TCP/IP protocols matured quicker than similar OSI protocols When the need for interoperability across networks ...
... TCP/IP protocols matured quicker than similar OSI protocols When the need for interoperability across networks ...
N4Less17.pps - GEOCITIES.ws
... • Each node uses a special device, called a network interface card (NIC). The card connects to the network media and controls the flow of data. • NICs must use a common network technology to communicate. The most popular network technologies for LANs are Ethernet, Fast Ethernet, and Token Ring. ...
... • Each node uses a special device, called a network interface card (NIC). The card connects to the network media and controls the flow of data. • NICs must use a common network technology to communicate. The most popular network technologies for LANs are Ethernet, Fast Ethernet, and Token Ring. ...
(CISCO) Self-Defending Networks
... • Point of presence on end user systems that enables efficient exchange of valuable network threat information as it occurs • Endpoint system virus, worm detection/protection ...
... • Point of presence on end user systems that enables efficient exchange of valuable network threat information as it occurs • Endpoint system virus, worm detection/protection ...
Word 2000 - UCLA.edu
... The Internet is just a generalization of these interconnected local area networks. The local networks can be Ethernet, fiber optics (FDDI), and so on, but the building blocks are machines that straddle two or more networks. Routing Routing concerns how a packet can reach the destination. If there is ...
... The Internet is just a generalization of these interconnected local area networks. The local networks can be Ethernet, fiber optics (FDDI), and so on, but the building blocks are machines that straddle two or more networks. Routing Routing concerns how a packet can reach the destination. If there is ...
Routing in Peer-to
... •Eavesdropping using the Crawler. •Analyzing the distribution of node-node shortest paths. ...
... •Eavesdropping using the Crawler. •Analyzing the distribution of node-node shortest paths. ...
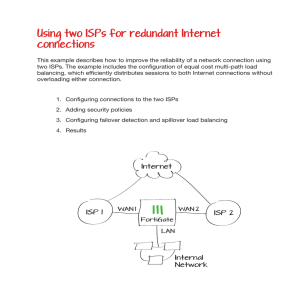
Using two ISPs for redundant Internet connections
... This example describes how to improve the reliability of a network connection using two ISPs. The example includes the configuration of equal cost multi-path load balancing, which efficiently distributes sessions to both Internet connections without overloading either connection. ...
... This example describes how to improve the reliability of a network connection using two ISPs. The example includes the configuration of equal cost multi-path load balancing, which efficiently distributes sessions to both Internet connections without overloading either connection. ...
Chapter 2
... and stored by mail servers. Simple Mail Transfer Protocol (SMTP) is the standard for e-mail client program. Post Office Protocol (POP) is the standard for e-mail server program. The Interactive Mail Access Protocol (IMAP) is a newer e-mail protocol. ...
... and stored by mail servers. Simple Mail Transfer Protocol (SMTP) is the standard for e-mail client program. Post Office Protocol (POP) is the standard for e-mail server program. The Interactive Mail Access Protocol (IMAP) is a newer e-mail protocol. ...
Session2-InternetworkingAndWWW
... These programs apply their routing algorithms to information they have stored in routing tables ...
... These programs apply their routing algorithms to information they have stored in routing tables ...
Powerpoint
... messages would be direct and straightforward. (e.g., the “hotline” between the White House and Kremlin) •Unfortunately, with hundreds, thousands or millions of computers on a network, they cannot all have direct links to each other. ...
... messages would be direct and straightforward. (e.g., the “hotline” between the White House and Kremlin) •Unfortunately, with hundreds, thousands or millions of computers on a network, they cannot all have direct links to each other. ...
Ethernet, IP and TCP
... • A dhcp server will answer and lease an IP address to the host, sending it the network mask and the gateway address as well. • Internet providers work like that to save address space. • Problem: some services require IP addresses to be stable. They can not be run in such a setting. ...
... • A dhcp server will answer and lease an IP address to the host, sending it the network mask and the gateway address as well. • Internet providers work like that to save address space. • Problem: some services require IP addresses to be stable. They can not be run in such a setting. ...
access to all locks
... TOSIBOX Central Lock provides an easy and scalable solution •Hub of the TOSIBOX ecosystem, allowing hundreds of connections from TOSIBOX Keys or Sub Locks. •Over 700 Mbit/s encryption throughput •up to 4000 concurrent VPN connections (TOSIBOX Lock or Key ...
... TOSIBOX Central Lock provides an easy and scalable solution •Hub of the TOSIBOX ecosystem, allowing hundreds of connections from TOSIBOX Keys or Sub Locks. •Over 700 Mbit/s encryption throughput •up to 4000 concurrent VPN connections (TOSIBOX Lock or Key ...
Presentation2.8
... The system should be designed so that long delays are not in the middle of interaction and so that the user gets some idea of how the job is progressing. ...
... The system should be designed so that long delays are not in the middle of interaction and so that the user gets some idea of how the job is progressing. ...
English
... TOSIBOX Central Lock provides an easy and scalable solution •Hub of the TOSIBOX ecosystem, allowing hundreds of connections from TOSIBOX Keys or Sub Locks. •Over 700 Mbit/s encryption throughput •up to 4000 concurrent VPN connections (TOSIBOX Lock or Key ...
... TOSIBOX Central Lock provides an easy and scalable solution •Hub of the TOSIBOX ecosystem, allowing hundreds of connections from TOSIBOX Keys or Sub Locks. •Over 700 Mbit/s encryption throughput •up to 4000 concurrent VPN connections (TOSIBOX Lock or Key ...
How to config 7228APn7416APn as Repeater
... Third Step: Change the IP address of EW-7416APn/EW-7228APn to fit in IP addresses of your network. This step is optional but recommended. You may want to change the IP address of EW-7416APn/EW-7228APn to a new IP address so it can be in the same subnet with your network. This is done under “System ...
... Third Step: Change the IP address of EW-7416APn/EW-7228APn to fit in IP addresses of your network. This step is optional but recommended. You may want to change the IP address of EW-7416APn/EW-7228APn to a new IP address so it can be in the same subnet with your network. This is done under “System ...
Courseware Outline
... certification, and have around 9-12 months' experience of networking support or IT administration. It is not necessary that you pass the A+ exams before completing Network+ certification, but it is recommended. Regardless of whether you have passed A+, it is recommended that you have the following s ...
... certification, and have around 9-12 months' experience of networking support or IT administration. It is not necessary that you pass the A+ exams before completing Network+ certification, but it is recommended. Regardless of whether you have passed A+, it is recommended that you have the following s ...
Corporate Design PowerPoint Basic Templates
... Commissioning LAN Preconditions The controller is set up (bus address, power supply, ….) OZS164 basic settings have been made (language, date, time, user accounts, device list) DSL broadband router is set up and has Internet access OZS164 is connected to PC via USB (also see „commissioning“ ...
... Commissioning LAN Preconditions The controller is set up (bus address, power supply, ….) OZS164 basic settings have been made (language, date, time, user accounts, device list) DSL broadband router is set up and has Internet access OZS164 is connected to PC via USB (also see „commissioning“ ...
WI-FI TECHNOLOGY: SECURITY ISSUES
... The typical Wi-Fi setup contains one or more Access Points (APs) and one or more clients. An AP broadcasts its SSID (Service Set Identifier) via packets that are called beacons, which are broadcasted every 100 ms. The beacons are transmitted at 1 Mbit/s, and are relatively short and therefore are no ...
... The typical Wi-Fi setup contains one or more Access Points (APs) and one or more clients. An AP broadcasts its SSID (Service Set Identifier) via packets that are called beacons, which are broadcasted every 100 ms. The beacons are transmitted at 1 Mbit/s, and are relatively short and therefore are no ...
Reaver
... GNU/Linux on your Android device. The application creates a disk image on the flash card, mount it and install there OS distribution. Applications of the new system are run in a chroot environment and working in parallel with platform Android. All changes made on the device are reversible, ie the ap ...
... GNU/Linux on your Android device. The application creates a disk image on the flash card, mount it and install there OS distribution. Applications of the new system are run in a chroot environment and working in parallel with platform Android. All changes made on the device are reversible, ie the ap ...
Wireless Networks
... Allows many devices to share same area Makes efficient use of bandwidth ...
... Allows many devices to share same area Makes efficient use of bandwidth ...
Kuliah Komunikasi Data
... defines the way in which computers, printers, and other devices are connected. A network topology describes the layout of the wire and devices as well as the paths used by data transmissions. ...
... defines the way in which computers, printers, and other devices are connected. A network topology describes the layout of the wire and devices as well as the paths used by data transmissions. ...
Slide 1
... Apply the algorithms behind some current network security protocols. Understand firewalls and their applications.. Demonstrate detailed knowledge of TCP/IP. ...
... Apply the algorithms behind some current network security protocols. Understand firewalls and their applications.. Demonstrate detailed knowledge of TCP/IP. ...
Memory
... The system should be designed so that long delays are not in the middle of interaction and so that the user gets some idea of how the job is progressing. ...
... The system should be designed so that long delays are not in the middle of interaction and so that the user gets some idea of how the job is progressing. ...