IP addresses
... is a standard used to define a method of exchanging data over a computer network such as local area network, Internet, Intranet, etc. ...
... is a standard used to define a method of exchanging data over a computer network such as local area network, Internet, Intranet, etc. ...
Networks
... What advantages do networks have? - increase productivity - workers can share information easily without printing, copying, telephoning, or posting. ...
... What advantages do networks have? - increase productivity - workers can share information easily without printing, copying, telephoning, or posting. ...
Overview of Computer Networking
... Overview of Computer Networking Goal of this lecture: get context, overview, “feel” of networking more depth, detail later in course approach: descriptive use Internet as example ...
... Overview of Computer Networking Goal of this lecture: get context, overview, “feel” of networking more depth, detail later in course approach: descriptive use Internet as example ...
Wireless Ethernet ()
... • Wired Equivalent Privacy (WEP) – Lowest level of encrypting data wirelessly with a 64 or 128 bit encryption key. ...
... • Wired Equivalent Privacy (WEP) – Lowest level of encrypting data wirelessly with a 64 or 128 bit encryption key. ...
The Internet and Security
... Discourage, under any circumstances, users giving their passwords to someone via email. ...
... Discourage, under any circumstances, users giving their passwords to someone via email. ...
Introduction - Staffordshire University
... • Computers, telephones, cameras, music systems, printers and game consoles ...
... • Computers, telephones, cameras, music systems, printers and game consoles ...
Introduction to Networking & telecommunications
... Something to which you should pay special attention. ...
... Something to which you should pay special attention. ...
Why the SurfBeam System Should Be Your Internet
... networks just can’t deliver what you need. Our project experience extends to virtually every satellite broadband system in the world. And our production experience includes hundreds of thousands of terminals—climbing towards 1 million—making us far and away the leading technology provider for Ka-ban ...
... networks just can’t deliver what you need. Our project experience extends to virtually every satellite broadband system in the world. And our production experience includes hundreds of thousands of terminals—climbing towards 1 million—making us far and away the leading technology provider for Ka-ban ...
The BT Cardway Service
... The Cardway Delivery Connection uses the X.25 protocol via an interface as described in SIN 57 for the 64 kbit/s Kilostream X.21 interface or via MPLS. For MPLS connection compatible CPE will connect to an IP network which will allow an MPLS VPN to be established. The BT Cardway Network makes no ass ...
... The Cardway Delivery Connection uses the X.25 protocol via an interface as described in SIN 57 for the 64 kbit/s Kilostream X.21 interface or via MPLS. For MPLS connection compatible CPE will connect to an IP network which will allow an MPLS VPN to be established. The BT Cardway Network makes no ass ...
Other Link Layer Protocols and Technologies
... CSMA/CD is not used • The supported modes of operation are: ...
... CSMA/CD is not used • The supported modes of operation are: ...
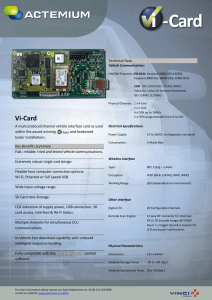
Vi-Card
... LED indication of supply power, USB connection, SD card access, interface & Wi-Fi Status. ...
... LED indication of supply power, USB connection, SD card access, interface & Wi-Fi Status. ...
Selling an Idea or a Product
... – At traffic jam, one strategy is merge closest to the bottleneck » Why people get off at one exit, drive 50 feet, merge back into flow » Ends up slowing everybody else a huge amount ...
... – At traffic jam, one strategy is merge closest to the bottleneck » Why people get off at one exit, drive 50 feet, merge back into flow » Ends up slowing everybody else a huge amount ...
IGERTPoster2009
... neuromodulators in expanding or contracting the set of possible outputs. In the context of the biological functionality of the STG, quantifying the dynamic range of this network will provide insights into how neurons are able to switch between two ongoing rhythms in the network. ...
... neuromodulators in expanding or contracting the set of possible outputs. In the context of the biological functionality of the STG, quantifying the dynamic range of this network will provide insights into how neurons are able to switch between two ongoing rhythms in the network. ...
slides: wireless network topics
... • Adjust the transmit power of devices, such that their SINR meets a certain threshold required for an acceptable performance ...
... • Adjust the transmit power of devices, such that their SINR meets a certain threshold required for an acceptable performance ...
Ericsson`s first ENGINE contract in Colombia
... Ericsson’s first ENGINE contract in Colombia Colombian operator TeleBucaramanga has selected Ericsson’s multiservice network solution ENGINE to migrate its existing network to a multi-service network. The solution will also function as the platform for the introduction of new data services and other ...
... Ericsson’s first ENGINE contract in Colombia Colombian operator TeleBucaramanga has selected Ericsson’s multiservice network solution ENGINE to migrate its existing network to a multi-service network. The solution will also function as the platform for the introduction of new data services and other ...
Advanced TCP/IP Planning and Design
... Supernetting groups networks into larger supernets How: by borrowing bits from the network portion of the address. Why: Say that you want a LAN network to have more than 254 hosts; a class C network is not sufficient. You can group two Class C networks using supernets. Benefits: Provide more IP addr ...
... Supernetting groups networks into larger supernets How: by borrowing bits from the network portion of the address. Why: Say that you want a LAN network to have more than 254 hosts; a class C network is not sufficient. You can group two Class C networks using supernets. Benefits: Provide more IP addr ...
Chapter Answers to end-of
... 2. Explain the difference between peer-to-peer and client/server networks. In a peer-to-peer network, all the computers on the network are equals, and there is no file server. Each computer user decides which, if any, files will be accessible to other users on the network. Although peer-topeer netwo ...
... 2. Explain the difference between peer-to-peer and client/server networks. In a peer-to-peer network, all the computers on the network are equals, and there is no file server. Each computer user decides which, if any, files will be accessible to other users on the network. Although peer-topeer netwo ...
Slide 1
... Choose the path that packets take around the network Packets are given a time to live (TTL) to prevent them travelling for ever ...
... Choose the path that packets take around the network Packets are given a time to live (TTL) to prevent them travelling for ever ...
Network Basics Solutions
... 30 True or false? A star Ethernet might be faster than a bus Ethernet, especially if there are many nodes on the network. False. A star Ethernet might be slower than a bus Ethernet, because the hub generates a lot of data traffic that isn’t used. It replicates all the data it receives from any sourc ...
... 30 True or false? A star Ethernet might be faster than a bus Ethernet, especially if there are many nodes on the network. False. A star Ethernet might be slower than a bus Ethernet, because the hub generates a lot of data traffic that isn’t used. It replicates all the data it receives from any sourc ...
16-Channel monitor w/Interruption
... Technology” that virtually eliminates lightning damage to the system. The Watchdog system communicates with one or more wireless “smart node” sensors and/or interruption controllers at a range up to 300 feet. ...
... Technology” that virtually eliminates lightning damage to the system. The Watchdog system communicates with one or more wireless “smart node” sensors and/or interruption controllers at a range up to 300 feet. ...
Root-Cause Troubleshooting for Your Entire Network
... you when, where, and why VoIP problems occur, and even recommends how to fix them – in plain-English. With TotalView, call troubleshooting has never been easier as all corners of your network and beyond are covered, enabling you to isolate problems even when they occur on your carrier’s network or o ...
... you when, where, and why VoIP problems occur, and even recommends how to fix them – in plain-English. With TotalView, call troubleshooting has never been easier as all corners of your network and beyond are covered, enabling you to isolate problems even when they occur on your carrier’s network or o ...