Network
... – LAN (Local Area Network) – A group of devices sharing resources in a single area such as a room or a building. – WAN (Wide Area Network) – Two or more LANs communicating, often across large distances. The most famous WAN is the Internet. ...
... – LAN (Local Area Network) – A group of devices sharing resources in a single area such as a room or a building. – WAN (Wide Area Network) – Two or more LANs communicating, often across large distances. The most famous WAN is the Internet. ...
Computer Networks Lecture: Kholoud .AE Advantages of Network
... • A MAN ,while larger than LAN is limited to city or group of nearby corporate offices. It uses similar technology of LAN. • The Metropolitan Area Network standards are sponsored by the IEEE,ANSI and the Regional Bell operating companies. • MAN is provides the transfer rates from 34 to 150 Mbps. ...
... • A MAN ,while larger than LAN is limited to city or group of nearby corporate offices. It uses similar technology of LAN. • The Metropolitan Area Network standards are sponsored by the IEEE,ANSI and the Regional Bell operating companies. • MAN is provides the transfer rates from 34 to 150 Mbps. ...
3-4-1_QoS Intro adap..
... – Multihop ad hoc network – Wireless Internet access (from W-LAN or ad hoc net) – Wireless mesh networks • The above scenarios are all challenging: – Channel parameter fluctuations (motion, obstacles, interference) – Change in S/N ratio at receiver – Mobility (path breaks, must be repatched, etc) – ...
... – Multihop ad hoc network – Wireless Internet access (from W-LAN or ad hoc net) – Wireless mesh networks • The above scenarios are all challenging: – Channel parameter fluctuations (motion, obstacles, interference) – Change in S/N ratio at receiver – Mobility (path breaks, must be repatched, etc) – ...
Lesson 07 Bridges, Hub, Switches and Routers
... ‒ Bridges can separate collision domains ↪ join two network segments ‒ Forward traffic between segments ‒ Smarter than repeater ‒ Filter on traffic destination ‒ Messages are: ‒ Read for information ‒ Stored in a queue (of bounded size) ...
... ‒ Bridges can separate collision domains ↪ join two network segments ‒ Forward traffic between segments ‒ Smarter than repeater ‒ Filter on traffic destination ‒ Messages are: ‒ Read for information ‒ Stored in a queue (of bounded size) ...
MPLS, SD-WAN, Internet, and Cloud Network
... With public cloud applications outside the control of IT, organizations can’t rely on optimizations that require a box at both ends of each link. In addition, Cloud infrastructure (servers and storage), introduces a new production environment that has its own connectivity and security requirements. ...
... With public cloud applications outside the control of IT, organizations can’t rely on optimizations that require a box at both ends of each link. In addition, Cloud infrastructure (servers and storage), introduces a new production environment that has its own connectivity and security requirements. ...
Leveraging Internet2 Facilities for the Network Research Community
... • The same basic hierarchies continue today, although in a much more complicated network universe • Moreover, the fact that there is no central authority over the Internet means that networks must work together to provide services – that is especially true in the R&E world. • This begs the need for ...
... • The same basic hierarchies continue today, although in a much more complicated network universe • Moreover, the fact that there is no central authority over the Internet means that networks must work together to provide services – that is especially true in the R&E world. • This begs the need for ...
Wired communication standards solutions
... between e-mail servers and used by e-mail client software to send messages to the server, but never used to retrieve e-mail from a server? A IMAP4 B POP3 C ...
... between e-mail servers and used by e-mail client software to send messages to the server, but never used to retrieve e-mail from a server? A IMAP4 B POP3 C ...
i Net2+ - Argon Audio
... Fixed NAT traversal support that was mistakenly removed from Openswan Openswan is an IPsec implementation for Linux. It has support for NAT Traversal (techniques that establish and maintain Internet protocol connections traversing network address translation (NAT) gateways). Upgraded PPP to version ...
... Fixed NAT traversal support that was mistakenly removed from Openswan Openswan is an IPsec implementation for Linux. It has support for NAT Traversal (techniques that establish and maintain Internet protocol connections traversing network address translation (NAT) gateways). Upgraded PPP to version ...
ETSI Broadband Access including Fixed Wireless Access
... • Broadband Fixed Wireless Access (FWA) – 2-11 GHz – up to 75 Mbit/s @ 20 MHz channelization – FWA services to SMEs and residential users • Interoperable standard – Defines only one PHY mode: OFDM, FFT 256 points • Main Features – Using the basic MAC (DLC and CLs) of the IEEE 802.16-2001 standard as ...
... • Broadband Fixed Wireless Access (FWA) – 2-11 GHz – up to 75 Mbit/s @ 20 MHz channelization – FWA services to SMEs and residential users • Interoperable standard – Defines only one PHY mode: OFDM, FFT 256 points • Main Features – Using the basic MAC (DLC and CLs) of the IEEE 802.16-2001 standard as ...
DICENTIS Wireless Conference System
... 25 open microphones .......................................................................................................... 5 Redundant WAP .................................................................................................................. 5 Typical DICENTIS Wireless Conference Sys ...
... 25 open microphones .......................................................................................................... 5 Redundant WAP .................................................................................................................. 5 Typical DICENTIS Wireless Conference Sys ...
WT-2 Setup Guide for Infrastructure Networks
... of different access points that you typically connect to. Once a network has been added to this list you can select it and move Remove the CF card from your computer and insert it up and down with respect to it into the camera with the WT-2 attached. Wait the other networks. for the green light to g ...
... of different access points that you typically connect to. Once a network has been added to this list you can select it and move Remove the CF card from your computer and insert it up and down with respect to it into the camera with the WT-2 attached. Wait the other networks. for the green light to g ...
air digital wireless triple play network
... CATV network (the broadcast is similar to Satellite broadcast), upstream consist of IP traffic only (including VoIP) in the direction from the end user to the Main station. The same system can be used in a standard coaxial, analog or digital cable TV network or in a combined network (wireless and ca ...
... CATV network (the broadcast is similar to Satellite broadcast), upstream consist of IP traffic only (including VoIP) in the direction from the end user to the Main station. The same system can be used in a standard coaxial, analog or digital cable TV network or in a combined network (wireless and ca ...
Wireless Mesh Networks Challenges and Opportunities
... Nodes can use a control channel to coordinate and the rest to exchange data. In some conditions can be very efficient. However the control channel can be: an unacceptable ...
... Nodes can use a control channel to coordinate and the rest to exchange data. In some conditions can be very efficient. However the control channel can be: an unacceptable ...
QoS Monitoring and Quality of 4G Services in Latvia
... be measured and the content, form and manner of the information to ...
... be measured and the content, form and manner of the information to ...
Document
... In a Client Server network some computers are clients. People use these to access the network. A server is a computer which controls a resource that is made available to clients on the network. Resources might include applications, data files, printers, email or internet access. Backing storage is ...
... In a Client Server network some computers are clients. People use these to access the network. A server is a computer which controls a resource that is made available to clients on the network. Resources might include applications, data files, printers, email or internet access. Backing storage is ...
Computer communications
... DSL is a very high-speed connection that uses the same wires as a regular telephone line. Provided by an Internet Service Provider (ISP) Here are some advantages of DSL: •You can leave your Internet connection always on and still use the phone line for voice calls. •Doesn't require new wiring. •Prov ...
... DSL is a very high-speed connection that uses the same wires as a regular telephone line. Provided by an Internet Service Provider (ISP) Here are some advantages of DSL: •You can leave your Internet connection always on and still use the phone line for voice calls. •Doesn't require new wiring. •Prov ...
Review() - Personal.psu.edu
... more reliably than the other node – A message, once transmitted, may need to be retransmitted for some reasons ...
... more reliably than the other node – A message, once transmitted, may need to be retransmitted for some reasons ...
Unbuntu Installation
... This paper examines how open source embedded network tools were used to perform persistent internal audits of Ethernet Local Area Network broadcast traffic. The initial requirements to define the project phases were developed based on the analysis of each open source learning stage. Open Source UNIX ...
... This paper examines how open source embedded network tools were used to perform persistent internal audits of Ethernet Local Area Network broadcast traffic. The initial requirements to define the project phases were developed based on the analysis of each open source learning stage. Open Source UNIX ...
EL736 Communications Networks II: Design and Algorithms
... all sources connect to that location ...
... all sources connect to that location ...
Partners Friday Meeting 9th November 2007
... Feedback given was that overall, the inspectors were very impressed with the practices and staff they had met and feedback included ...
... Feedback given was that overall, the inspectors were very impressed with the practices and staff they had met and feedback included ...
... Develops and maintains accurate documentation showing network infrastructure, platform(s), configuration and security; Evaluates the Ministry’s network systems against established industry benchmarks for performance, security, stability etc. and plans and implements the improvements of the systems w ...
Improving Security in Anonymizing Networks using a Privacy Enhancing System
... drawbacks. If the message frequency is very high at a node, the NM forwards only the simple messages. Latency is more and hence the speed gets reduced. In proposed methodology, the credential system is secured by the hashing algorithm. The algorithms used are RSA for confidentiality and MD5 for auth ...
... drawbacks. If the message frequency is very high at a node, the NM forwards only the simple messages. Latency is more and hence the speed gets reduced. In proposed methodology, the credential system is secured by the hashing algorithm. The algorithms used are RSA for confidentiality and MD5 for auth ...
Complex Networks
... Interaction between networks Overlay networks compete with IP networks to provide routing service IP and overlay networks are unaware of key things happening at the other layer Multiple overlay networks co-exist and make independent decisions How does all this affect IP and overlay networks? ...
... Interaction between networks Overlay networks compete with IP networks to provide routing service IP and overlay networks are unaware of key things happening at the other layer Multiple overlay networks co-exist and make independent decisions How does all this affect IP and overlay networks? ...
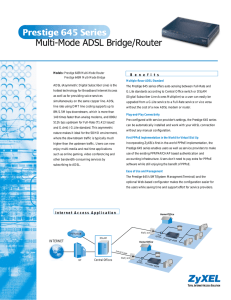
Multi-Mode ADSL Bridge/Router
... upgraded from a G.Lite service to a Full-Rate service or vice versa ...
... upgraded from a G.Lite service to a Full-Rate service or vice versa ...