FireWxNet: A Multi-Tiered Portable Wireless for Monitoring Weather
... When base station is powered on, it begins sending out control packets (or beacons) for one minute at the rate of one every four ...
... When base station is powered on, it begins sending out control packets (or beacons) for one minute at the rate of one every four ...
Basic Concepts
... Never talk about an innovation “reducing cost,” “increasing speed,” etc. without specifying which element is cheaper or faster. For example, multiplexing only reduces the cost of trunk lines; other costs are not decreased ...
... Never talk about an innovation “reducing cost,” “increasing speed,” etc. without specifying which element is cheaper or faster. For example, multiplexing only reduces the cost of trunk lines; other costs are not decreased ...
Adding Virtual Machines to the GNS3 Topology
... We now want to configure an interface on each VM with settings for the virtual network it is to be connected to. To do this we have to assign an IP Address and Default Gateway to the VM’s network adapter. Below this is shown for both Linux and Windows VMs. ...
... We now want to configure an interface on each VM with settings for the virtual network it is to be connected to. To do this we have to assign an IP Address and Default Gateway to the VM’s network adapter. Below this is shown for both Linux and Windows VMs. ...
Thus, based on the data communications network that is sending
... The rise of internet user already become part of our daily life. This is because the use of information in cyberspace will be important in everyday life. These characteristics are one of the effects of globalization in Indonesia. We often do a good interaction with other people in the exchange of in ...
... The rise of internet user already become part of our daily life. This is because the use of information in cyberspace will be important in everyday life. These characteristics are one of the effects of globalization in Indonesia. We often do a good interaction with other people in the exchange of in ...
Case Study - Korea Opportunities for BB Connectivity in APAC Ki-young, Ko |
... Domestic Traffic Trend 66.5% of households in Korea have smart devices Market share ...
... Domestic Traffic Trend 66.5% of households in Korea have smart devices Market share ...
internet connectivity between mobile adhoc network using mobile ip
... MIPMANET. Ad hoc networking enables IP mobility within a network whereas Mobile IP enables IP mobility between networks. By combining these two, MIPMANET allows mobile nodes to enjoy extended IP mobility. The simulation study has evaluated what is the energy level of one node in the network while it ...
... MIPMANET. Ad hoc networking enables IP mobility within a network whereas Mobile IP enables IP mobility between networks. By combining these two, MIPMANET allows mobile nodes to enjoy extended IP mobility. The simulation study has evaluated what is the energy level of one node in the network while it ...
Advanced Networks Course Topics
... packet-based network both at the user-network interface and within the network itself Today ATM is found in the following applications: » Public network infrastructure: ATM enables public teleco’s to support telephony, cable TV etc. » ATM LAN: ATM can be used for Backbone LANs and as Switching Hub f ...
... packet-based network both at the user-network interface and within the network itself Today ATM is found in the following applications: » Public network infrastructure: ATM enables public teleco’s to support telephony, cable TV etc. » ATM LAN: ATM can be used for Backbone LANs and as Switching Hub f ...
Chapter 06
... 20. Output from analog devices must be converted into digital form in order to input it into a computer. True False 21. Today, ordinary telephone wire is the least used medium for telecommunications. True False 22. Newly developed optical routers will be able to send optical signals up to 2,500 mile ...
... 20. Output from analog devices must be converted into digital form in order to input it into a computer. True False 21. Today, ordinary telephone wire is the least used medium for telecommunications. True False 22. Newly developed optical routers will be able to send optical signals up to 2,500 mile ...
投影片 1
... Packet scheduling policy in CFP 1) The PBS first scans the token buffers of voice sources according to the preset priority order. If a token is found, it removes one token from this token buffer and transmits a packet for this voice source. Then, the PBS generates next token for this voice source a ...
... Packet scheduling policy in CFP 1) The PBS first scans the token buffers of voice sources according to the preset priority order. If a token is found, it removes one token from this token buffer and transmits a packet for this voice source. Then, the PBS generates next token for this voice source a ...
network slicing in 5g
... Context awareness will offer the possibility to optimize the infrastructure and the services ID management will be important not only to address the customer/end-system, it will also address the interconnection to the slice, the service execution environment End-systems become part of the network ...
... Context awareness will offer the possibility to optimize the infrastructure and the services ID management will be important not only to address the customer/end-system, it will also address the interconnection to the slice, the service execution environment End-systems become part of the network ...
Chapter 7
... • Web Portal: Secure, Web-based interface to an application – Places few requirements on client ...
... • Web Portal: Secure, Web-based interface to an application – Places few requirements on client ...
The Future of Computing: Challenges and Opportunities
... UDP (User Datagram Protocol) • From one application to another – multiple destinations ...
... UDP (User Datagram Protocol) • From one application to another – multiple destinations ...
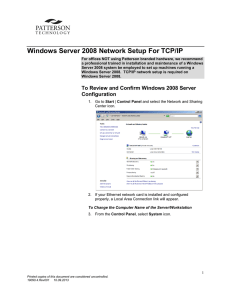
Windows Server 2008 Network Setup For TCP/IP
... Windows Server 2008 Network Setup For TCP/IP For offices NOT using Patterson branded hardware, we recommend a professional trained in installation and maintenance of a Windows Server 2008 system be employed to set up machines running a Windows Server 2008. TCP/IP network setup is required on Windows ...
... Windows Server 2008 Network Setup For TCP/IP For offices NOT using Patterson branded hardware, we recommend a professional trained in installation and maintenance of a Windows Server 2008 system be employed to set up machines running a Windows Server 2008. TCP/IP network setup is required on Windows ...
Chapter 7
... Summary (continued) • T-carrier technology uses TDM to divide a single channel into multiple channels for carrying voice, data, video, or other signals • DSL comes in eight different varieties, each of which is either asymmetrical or symmetrical • Broadband cable is a dedicated service that relies ...
... Summary (continued) • T-carrier technology uses TDM to divide a single channel into multiple channels for carrying voice, data, video, or other signals • DSL comes in eight different varieties, each of which is either asymmetrical or symmetrical • Broadband cable is a dedicated service that relies ...
Solving the Wireless Mesh Multi-Hop Dilemma
... being shared for both ingress and egress traffic. What does this mean? A slight improvement is gained for wireless clients, but overall network performance is still poor for the reason that the backhaul is the bottleneck. The Multi Radio Approach—A Structured Wireless Mesh In the multi-radio—or stru ...
... being shared for both ingress and egress traffic. What does this mean? A slight improvement is gained for wireless clients, but overall network performance is still poor for the reason that the backhaul is the bottleneck. The Multi Radio Approach—A Structured Wireless Mesh In the multi-radio—or stru ...
Internet Overview - Electrical and Computer Engineering
... where its customers and other ISPs connect to it ...
... where its customers and other ISPs connect to it ...
An Analytical Solution to Video Streaming in Mobile Ad hoc Networks
... Like many other network applications, video streaming relies on the layered TCP/IP stack: I ...
... Like many other network applications, video streaming relies on the layered TCP/IP stack: I ...
View File
... agents in the mobile terminal Standard content encoding – defined to allow a WAE user agent to navigate Web content Wireless telephony applications (WTA) – collection of telephony-specific extensions for call and feature ...
... agents in the mobile terminal Standard content encoding – defined to allow a WAE user agent to navigate Web content Wireless telephony applications (WTA) – collection of telephony-specific extensions for call and feature ...
List six access technologies
... R5. Is HFC transmission rate dedicated or shared among users? Are collisions possible in a downstream HFC channel? Why or why not? <4 points> HFC bandwidth is shared among the users. [2 points] On the downstream channel, all packets emanate from a single source, namely, the head end. Thus, there are ...
... R5. Is HFC transmission rate dedicated or shared among users? Are collisions possible in a downstream HFC channel? Why or why not? <4 points> HFC bandwidth is shared among the users. [2 points] On the downstream channel, all packets emanate from a single source, namely, the head end. Thus, there are ...
Vertical optimization of data transmission for mobile wireless terminals
... Consequently, losses in the wireless transmission are incorrectly interpreted as a sign of congestion, leading to a reduction of the data flow by the TCP congestion control mechanism. The fast retransmit mechanism is not able to cope, and data transfer recommences only after a ...
... Consequently, losses in the wireless transmission are incorrectly interpreted as a sign of congestion, leading to a reduction of the data flow by the TCP congestion control mechanism. The fast retransmit mechanism is not able to cope, and data transfer recommences only after a ...
Chapter 3 Physical Components of a Network
... linear bus, all the devices on a bus topology are connected by one single cable, which proceeds from one computer to the next. • This topology is rarely used and would only be suitable for a home office or small business with only a few hosts. ...
... linear bus, all the devices on a bus topology are connected by one single cable, which proceeds from one computer to the next. • This topology is rarely used and would only be suitable for a home office or small business with only a few hosts. ...
Linux+ Guide to Linux Certification
... Summary (continued) • T-carrier technology uses TDM to divide a single channel into multiple channels for carrying voice, data, video, or other signals • DSL comes in eight different varieties, each of which is either asymmetrical or symmetrical • Broadband cable is a dedicated service that relies ...
... Summary (continued) • T-carrier technology uses TDM to divide a single channel into multiple channels for carrying voice, data, video, or other signals • DSL comes in eight different varieties, each of which is either asymmetrical or symmetrical • Broadband cable is a dedicated service that relies ...
Fundamental components of network effects Expectations
... How can we limit this chaos?[2] Network effects •some goods/services create more value when more users consume the same goods and services. •they have little or even no value if they are used in isolation. •utility derived from consumption of these goods/services increases as additional consumers p ...
... How can we limit this chaos?[2] Network effects •some goods/services create more value when more users consume the same goods and services. •they have little or even no value if they are used in isolation. •utility derived from consumption of these goods/services increases as additional consumers p ...