Manual Linksys phone adapter PAP2T
... Thank you for choosing the Linksys Phone Adapter with 2 Ports for Voice-over-IP. This Phone Adapter will allow you to make phone or fax calls using the your broadband connection. How does the Phone Adapter do this? The Phone Adapter connects your phones or fax machines to your network router or gate ...
... Thank you for choosing the Linksys Phone Adapter with 2 Ports for Voice-over-IP. This Phone Adapter will allow you to make phone or fax calls using the your broadband connection. How does the Phone Adapter do this? The Phone Adapter connects your phones or fax machines to your network router or gate ...
Alcatel-Lucent OmniAccess 5510
... security-first architecture ensures that all newly activated services receive protection from existing security infrastructure. IPSec VPN tunnels and Client VPN allow remote sites and nomadic users to connect to corporate ...
... security-first architecture ensures that all newly activated services receive protection from existing security infrastructure. IPSec VPN tunnels and Client VPN allow remote sites and nomadic users to connect to corporate ...
3 Router Configuration - Cisco Networking Academy
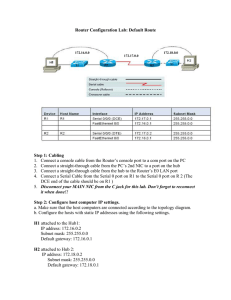
... Step 15 Configure a default route on each router. In order for the routers to talk to each other, they must know how to reach all of the networks connected to each router. A default route will tell each router to send all packets that are not destined for its own LAN to the S0 interface of the other ...
... Step 15 Configure a default route on each router. In order for the routers to talk to each other, they must know how to reach all of the networks connected to each router. A default route will tell each router to send all packets that are not destined for its own LAN to the S0 interface of the other ...
Fastpass: A Centralized “Zero-Queue” Datacenter Network
... In this ideal case, the end-to-end latency of a packet transmission would be the time until the allocated timeslot plus the time needed for the packet to traverse the path to the receiver with empty queues at all egress ports. In moderately-loaded to heavily-loaded networks, ideal allocations will t ...
... In this ideal case, the end-to-end latency of a packet transmission would be the time until the allocated timeslot plus the time needed for the packet to traverse the path to the receiver with empty queues at all egress ports. In moderately-loaded to heavily-loaded networks, ideal allocations will t ...
No Slide Title
... of 0 (zero) - This means that the provider does not guarantee any throughput. In practice, customers usually find that their provider allows them to burst over the 0 (zero) CIR virtually all of the time. If a CIR of 0 (zero) is purchased, carefully monitor performance in order to determine whether o ...
... of 0 (zero) - This means that the provider does not guarantee any throughput. In practice, customers usually find that their provider allows them to burst over the 0 (zero) CIR virtually all of the time. If a CIR of 0 (zero) is purchased, carefully monitor performance in order to determine whether o ...
Cisco ASA 5500 Series SSL/IPsec VPN Edition
... AnyConnect VPN Client, an automatically downloadable network-tunneling client that provides access to virtually any application or resource. Optimized Network Performance: The Cisco AnyConnect VPN Client provides an optimized VPN connection for latencysensitive traffic, such as voice over IP (VoIP) ...
... AnyConnect VPN Client, an automatically downloadable network-tunneling client that provides access to virtually any application or resource. Optimized Network Performance: The Cisco AnyConnect VPN Client provides an optimized VPN connection for latencysensitive traffic, such as voice over IP (VoIP) ...
Cisco 827 Router Cabling and Setup Quick Start Guide
... When you first launch the CD, you will notice a list of books in the left pane of your display that you can use to navigate directly to the book you want to view. When you select the document, Acrobat Reader opens the book in .pdf format and provides a list of topics in the left frame of the Acrobat ...
... When you first launch the CD, you will notice a list of books in the left pane of your display that you can use to navigate directly to the book you want to view. When you select the document, Acrobat Reader opens the book in .pdf format and provides a list of topics in the left frame of the Acrobat ...
Cisco 1700 Series Modular Access Routers
... Cisco IOS Software is the industry’s widely accepted standard for the Internet and private network operations. Based on Cisco IOS security technology, the Cisco 1700 Series routers provide powerful, integrated firewall, VPN, and IDS capabilities. As new security technologies are developed, they oft ...
... Cisco IOS Software is the industry’s widely accepted standard for the Internet and private network operations. Based on Cisco IOS security technology, the Cisco 1700 Series routers provide powerful, integrated firewall, VPN, and IDS capabilities. As new security technologies are developed, they oft ...
Universal Plug and Play - Dead simple or simply
... Apart from some media attention things fizzled out really quick. In January 2008 UPnP hacking code was combined with a Flash bug: local attack became a (limited) remote attack. ...
... Apart from some media attention things fizzled out really quick. In January 2008 UPnP hacking code was combined with a Flash bug: local attack became a (limited) remote attack. ...
“The Tenet Architecture for Tiered Sensor Networks.”
... view of sensor networking, the principle constrains the processing of data received from multiple sensors to be placed at the master tier, regardless of whether that processing is specific to an application or can be expressed as a generic fusion service. (It might, for example, be possible to cast ...
... view of sensor networking, the principle constrains the processing of data received from multiple sensors to be placed at the master tier, regardless of whether that processing is specific to an application or can be expressed as a generic fusion service. (It might, for example, be possible to cast ...
A technical review of some of the options coming from digital
... WiFi and WiMax are typically used to network computers and allow the exchanging of files, sharing peripherals and also sharing a common broadband connection. With the integration of computers with home entertainment centres we see possibilities to broadcast video and audio programming over a Local A ...
... WiFi and WiMax are typically used to network computers and allow the exchanging of files, sharing peripherals and also sharing a common broadband connection. With the integration of computers with home entertainment centres we see possibilities to broadcast video and audio programming over a Local A ...
Dictionary of Networking
... Nothing is more annoying than a dead URL, and link rot is all pervasive. (If you don’t know what link rot is, go look it up.) All the URLs in this book have been individually checked by our Technical Editor; and at the time of writing, they are all active, they all work, and they all contain the inf ...
... Nothing is more annoying than a dead URL, and link rot is all pervasive. (If you don’t know what link rot is, go look it up.) All the URLs in this book have been individually checked by our Technical Editor; and at the time of writing, they are all active, they all work, and they all contain the inf ...
G:\Aethra (Aztech)\Starbridge E
... After every change save the configuration and restart the Modem/Router. During the process of restart, the DSL indicator will go off, followed by the ETH/ACT indicator. Once you see the ETH/ACT indicator lights up and DSL indicator flickers, it meas that the restart process is completed. Please ref ...
... After every change save the configuration and restart the Modem/Router. During the process of restart, the DSL indicator will go off, followed by the ETH/ACT indicator. Once you see the ETH/ACT indicator lights up and DSL indicator flickers, it meas that the restart process is completed. Please ref ...
SNMP In Depth
... Maintains a matrix at the MAC layer that shows the amount of traffic and number of errors between pairs of nodes, one source and one destination pair. A generic filter engine activates all packet capture functions and events. Users can choose to capture packets that are valid or invalid for multilpl ...
... Maintains a matrix at the MAC layer that shows the amount of traffic and number of errors between pairs of nodes, one source and one destination pair. A generic filter engine activates all packet capture functions and events. Users can choose to capture packets that are valid or invalid for multilpl ...
Reference Manual for the Model RP614 Web Safe Router
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiat ...
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiat ...
Chapter5 (IPv4 Address)
... In classful addressing, the first address in the block is called the network address. It defines the network to which an address belongs. The network address is used in routing a packet to its destination network. A network mask or a default mask in classful addressing is a 32-bit number with n ...
... In classful addressing, the first address in the block is called the network address. It defines the network to which an address belongs. The network address is used in routing a packet to its destination network. A network mask or a default mask in classful addressing is a 32-bit number with n ...
Review, Performance Metrics, Cont…
... Near-far problem: if power of multiple users are unequal, strongest received mobile signal will capture demodulator at base station —Power Control to ensure that each mobile within coverage area provides same signal level to base station receiver CDMA is dual mode like TDMA. The system can move a ...
... Near-far problem: if power of multiple users are unequal, strongest received mobile signal will capture demodulator at base station —Power Control to ensure that each mobile within coverage area provides same signal level to base station receiver CDMA is dual mode like TDMA. The system can move a ...
EdgeRouter Lite User Guide
... Ports and Status Information The Ports image displays the active connections. An amber port indicates 10/100 Mbps, and a green port indicates 1000 Mbps. The Status bar graphs display the following: CPU The percentage of processing power that the EdgeRouter is using is displayed. RAM The percentage ...
... Ports and Status Information The Ports image displays the active connections. An amber port indicates 10/100 Mbps, and a green port indicates 1000 Mbps. The Status bar graphs display the following: CPU The percentage of processing power that the EdgeRouter is using is displayed. RAM The percentage ...
ICE600-Computer Networks-SARAH
... original one When the network does not support IP multicast When incoming MH already participates in unicast RSVP session ...
... original one When the network does not support IP multicast When incoming MH already participates in unicast RSVP session ...
CIS Cisco IOS 15 Benchmark
... products or applications that are directly and specifically dependent on such SB Product or any component for any part of their functionality; (8) represent or claim a particular level of compliance or consistency with any SB Product; or (9) facilitate or otherwise aid other individuals or entities ...
... products or applications that are directly and specifically dependent on such SB Product or any component for any part of their functionality; (8) represent or claim a particular level of compliance or consistency with any SB Product; or (9) facilitate or otherwise aid other individuals or entities ...
Multicast monitoring and visualization tools
... MUVI features – Routers connections and availability monitoring • Decorates router’s icon according to router’s status • Automatically marks unavailable connections • Map can be filtered in order to show one multicast group only ...
... MUVI features – Routers connections and availability monitoring • Decorates router’s icon according to router’s status • Automatically marks unavailable connections • Map can be filtered in order to show one multicast group only ...
2014-06 WLAN 9100 Learning_Bytes
... and ongoing changes fast, easy, and error proof It enhances the performance and resiliency of ...
... and ongoing changes fast, easy, and error proof It enhances the performance and resiliency of ...
The Tenet Architecture for Tiered Sensor Networks
... view of sensor networking, the principle constrains the processing of data received from multiple sensors to be placed at the master tier, regardless of whether that processing is specific to an application or can be expressed as a generic fusion service. (It might, for example, be possible to cast ...
... view of sensor networking, the principle constrains the processing of data received from multiple sensors to be placed at the master tier, regardless of whether that processing is specific to an application or can be expressed as a generic fusion service. (It might, for example, be possible to cast ...