Read more - Broadband Internet Technical Advisory Group
... services allow users to make calls between IP-based endpoints and to interconnect with the traditional public switched telephone network. VoIP applications use a variety of methods and protocols to manage connections and exchange media (i.e., the content of voice or video communications) over IP-bas ...
... services allow users to make calls between IP-based endpoints and to interconnect with the traditional public switched telephone network. VoIP applications use a variety of methods and protocols to manage connections and exchange media (i.e., the content of voice or video communications) over IP-bas ...
ICN`12 ~ Coexist: A Hybrid Approach for Content Oriented Publish
... 20, 13, 5] has gained the attention as a new networking paradigm that fills the gap between the content-centric needs of a customer and the current location-centric network architecture. Named Data Networking (NDN) [20] is a popular example of CCN, aiming to transform content as a first-class entity ...
... 20, 13, 5] has gained the attention as a new networking paradigm that fills the gap between the content-centric needs of a customer and the current location-centric network architecture. Named Data Networking (NDN) [20] is a popular example of CCN, aiming to transform content as a first-class entity ...
An Overlay MAC Layer for 802.11 Networks Ananth Rao Ion Stoica UC Berkeley
... were far away (e.g., nodes 1 and 5 in Figure 1) did not carrier sense each other and were able to simultaneously send at about 5.1 Mbps. When the nodes are close to each other (e.g., nodes 2 and 3), they carrier sense each others transmissions, and hence share the channel capacity to send at about 2 ...
... were far away (e.g., nodes 1 and 5 in Figure 1) did not carrier sense each other and were able to simultaneously send at about 5.1 Mbps. When the nodes are close to each other (e.g., nodes 2 and 3), they carrier sense each others transmissions, and hence share the channel capacity to send at about 2 ...
IP-MPLS - E-Photon One +
... Each sub-problem is represented by a sequence of pairs where xi is a condition
variable and value is 0 or 1
A sub-problem is solved after the branching operation has been performed on it
A sub-problem is completed if it is solved and either it is a leaf or both its children are completed ...
... Each sub-problem is represented by a sequence of pairs
Document
... answered in a specific format by the destination node. Echo request and reply: for diagnostic purposes Time-stamp request and reply: to determine the round trip time and also to synchronize the clocks in two machines. Address mask request and reply: Request by a host to know its subnet mask to the r ...
... answered in a specific format by the destination node. Echo request and reply: for diagnostic purposes Time-stamp request and reply: to determine the round trip time and also to synchronize the clocks in two machines. Address mask request and reply: Request by a host to know its subnet mask to the r ...
ppt1
... "Phex is entirely based on William W. Wong´s Furi. As Furi has not been updated for over one year I decided to continue it´s development. But in case Wong is currently working on a new version of Furi i decided to rename my branch of the client to Phex. FURI is a Gnutella protocol-compatible Java pr ...
... "Phex is entirely based on William W. Wong´s Furi. As Furi has not been updated for over one year I decided to continue it´s development. But in case Wong is currently working on a new version of Furi i decided to rename my branch of the client to Phex. FURI is a Gnutella protocol-compatible Java pr ...
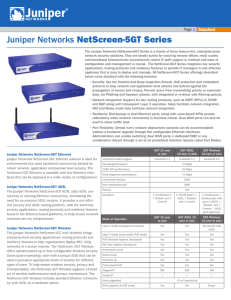
Juniper Networks NetScreen-5GT Series
... The Juniper Networks NetScreen-5GT with Wireless brings enterprise-level security applications, routing protocols and resiliency features to help organizations deploy 802.11b/g networks in a secure manner. The NetScreen- 5GT Wireless offers administrators up to four configurable Wireless Security Zon ...
... The Juniper Networks NetScreen-5GT with Wireless brings enterprise-level security applications, routing protocols and resiliency features to help organizations deploy 802.11b/g networks in a secure manner. The NetScreen- 5GT Wireless offers administrators up to four configurable Wireless Security Zon ...
21-06-0664-00-0000-QoS_considerations_in_NIHO_v3
... This document has been prepared to assist the IEEE 802.21 Working Group. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) res ...
... This document has been prepared to assist the IEEE 802.21 Working Group. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) res ...
A Novel Power Efficient Location-Based Cooperative Routing with
... terminals, it is theoretically possible to better adapt to the common WSNs where the node power is relatively low. Transmit or receive diversity in cooperative routing is realized through the virtual multi-antenna array which is formed by several or all single-antennas in a network sharing each othe ...
... terminals, it is theoretically possible to better adapt to the common WSNs where the node power is relatively low. Transmit or receive diversity in cooperative routing is realized through the virtual multi-antenna array which is formed by several or all single-antennas in a network sharing each othe ...
show ip route
... Clarifications (This is for IGPs only and not EGPs such as BGP): • The network command does two things: 1. Determines which interfaces will participate in sending and receiving routing updates, as long as the interface IP address falls in the range of the network command. 2. Determines which network ...
... Clarifications (This is for IGPs only and not EGPs such as BGP): • The network command does two things: 1. Determines which interfaces will participate in sending and receiving routing updates, as long as the interface IP address falls in the range of the network command. 2. Determines which network ...
Basic Configuration
... work at a location that is geographically local to the device offering the service. Serial ports at access servers can also be connected to modems, switches and other devices to provide access to services that are available at remote locations or for users who are at remote locations. This is referr ...
... work at a location that is geographically local to the device offering the service. Serial ports at access servers can also be connected to modems, switches and other devices to provide access to services that are available at remote locations or for users who are at remote locations. This is referr ...
Chapter 14
... – Users must be trained to update their antivirus software daily or, at a bare minimum, weekly – Users also must learn how viruses are transmitted between computers – Teach users to scan removable devices with the virus scanning software before using them ...
... – Users must be trained to update their antivirus software daily or, at a bare minimum, weekly – Users also must learn how viruses are transmitted between computers – Teach users to scan removable devices with the virus scanning software before using them ...
EQ-BGP: an efficient inter-domain QoS routing protocol
... independently of the number of ASs. This can be explained by the fact all ASs fixed routing paths on the direct links and than establish the alternative paths. As the QoS level assured on direct links is better then offered on alternative paths, therefore non of the routers would change to alternat ...
... independently of the number of ASs. This can be explained by the fact all ASs fixed routing paths on the direct links and than establish the alternative paths. As the QoS level assured on direct links is better then offered on alternative paths, therefore non of the routers would change to alternat ...
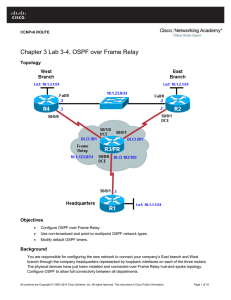
Chapter 3 Lab 3-4, OSPF over Frame Relay
... All contents are Copyright © 1992–2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. ...
... All contents are Copyright © 1992–2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. ...
Slide 1
... physical medium and in what order – Classifier – maps incoming packets into a given class for equal treatment by the packet scheduler – Admission control – determines whether or not a new flow may be established without affecting existing sessions – The ability to mark some packets as eligible for d ...
... physical medium and in what order – Classifier – maps incoming packets into a given class for equal treatment by the packet scheduler – Admission control – determines whether or not a new flow may be established without affecting existing sessions – The ability to mark some packets as eligible for d ...
Aalborg Universitet Morten Videbæk
... helper before it starts transmitting the coded packets (called p). The value of p will determine how much the source and the helper should send, but it also determines the performance of the scheme. The value of p should be large enough to guarantee that the helper transmissions are innovative for t ...
... helper before it starts transmitting the coded packets (called p). The value of p will determine how much the source and the helper should send, but it also determines the performance of the scheme. The value of p should be large enough to guarantee that the helper transmissions are innovative for t ...
About the Presentations
... • Common rules for packet filtering: – Drop all inbound connections except connection requests for configured servers – Eliminate packets bound for all ports that should not be available to the Internet – Filter out any ICMP redirect or echo (ping) messages – Drop all packets that use the IP header ...
... • Common rules for packet filtering: – Drop all inbound connections except connection requests for configured servers – Eliminate packets bound for all ports that should not be available to the Internet – Filter out any ICMP redirect or echo (ping) messages – Drop all packets that use the IP header ...
Distance vector routing protocols
... Distance vector routing protocols typically implement a technique known as split horizon. Prevents information from being sent out the same interface from which it was received. For example, R2 would not send an update out Serial 0/0/0 containing the network 10.1.0.0 because R2 learned about t ...
... Distance vector routing protocols typically implement a technique known as split horizon. Prevents information from being sent out the same interface from which it was received. For example, R2 would not send an update out Serial 0/0/0 containing the network 10.1.0.0 because R2 learned about t ...
ppt
... PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet Upstream satellite communication 802.11 wireless LAN ...
... PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet Upstream satellite communication 802.11 wireless LAN ...
Large-scale Internet measurement
... írta Laki, Sándor Publication date 2015 Szerzői jog © 2015 Laki Sándor ...
... írta Laki, Sándor Publication date 2015 Szerzői jog © 2015 Laki Sándor ...