Snffing_Spoofing_Session Hjacking_Netcat
... Includes a “resync” feature that may allow Trudy out of MiM ...
... Includes a “resync” feature that may allow Trudy out of MiM ...
Internet Security [1] - Distributed Systems Group
... - the traffic can be forced through specific routes (=specific hosts) - if the reverse route is used to reply to traffic, a host on the route can easily impersonate another host - can be used to abuse a trust relationship ...
... - the traffic can be forced through specific routes (=specific hosts) - if the reverse route is used to reply to traffic, a host on the route can easily impersonate another host - can be used to abuse a trust relationship ...
Voice over IP (VoIP)
... VoIP, the actual savings over the long term are still a subject of debate in the industry. Flat rate pricing is available with the Internet and can result in considerable savings for both voice and facsimile (at least currently). It has been estimated that up to 70% of all calls to Asia are to send ...
... VoIP, the actual savings over the long term are still a subject of debate in the industry. Flat rate pricing is available with the Internet and can result in considerable savings for both voice and facsimile (at least currently). It has been estimated that up to 70% of all calls to Asia are to send ...
PDF (Author`s version) - OATAO (Open Archive Toulouse Archive
... I. I NTRODUCTION Wireless Mesh Networks (WMNs) are a flexible, quickly deployable wireless networking solution that benefits from the lack of a rigid infrastructure. They are used to provide rural areas, where broadband infrastructure is not available, with a reliable Internet access based on multih ...
... I. I NTRODUCTION Wireless Mesh Networks (WMNs) are a flexible, quickly deployable wireless networking solution that benefits from the lack of a rigid infrastructure. They are used to provide rural areas, where broadband infrastructure is not available, with a reliable Internet access based on multih ...
Java Security
... Merely annoying, this attack class is the most commonly encountered. Implemented by malicious applets. May require restart of browser. Consequences of these attacks: light to moderate. ...
... Merely annoying, this attack class is the most commonly encountered. Implemented by malicious applets. May require restart of browser. Consequences of these attacks: light to moderate. ...
Document
... When system is sufficiently utilized More peers → more benefits from P2P Large differences among incentive models Build-in model is the best under this setup ...
... When system is sufficiently utilized More peers → more benefits from P2P Large differences among incentive models Build-in model is the best under this setup ...
Testing Bandwidth around the world
... A real time plot of latest RTT & Packet Loss between SLAC and CERN is displayed. ...
... A real time plot of latest RTT & Packet Loss between SLAC and CERN is displayed. ...
Time Server - WordPress.com
... Basically, an Internet Service can be defined as any service that can be accessed through TCP/IP based networks, whether an internal network (Intranet) or external network (Internet). Actually, TCP and IP are two of the protocols that are included in a group of protocols sometimes known as the I ...
... Basically, an Internet Service can be defined as any service that can be accessed through TCP/IP based networks, whether an internal network (Intranet) or external network (Internet). Actually, TCP and IP are two of the protocols that are included in a group of protocols sometimes known as the I ...
ccna1-ch10
... •Is a set of rules that determines how computers communicate with each other. •A protocol describes: •Message format. ...
... •Is a set of rules that determines how computers communicate with each other. •A protocol describes: •Message format. ...
Communications on the Internet are not efficient.
... Data link layer (layer 2) • Data can be sent between local area network devices at layer 2. • Data is broken down into smaller chunks of data called packets. • Different data link transmission protocols can be used. • Ethernet has become the common standard and uses 48-bit (6 bytes) source and dest ...
... Data link layer (layer 2) • Data can be sent between local area network devices at layer 2. • Data is broken down into smaller chunks of data called packets. • Different data link transmission protocols can be used. • Ethernet has become the common standard and uses 48-bit (6 bytes) source and dest ...
English - Senstar
... the Redundant Switcher/Data Converter (RS/DC) . The RS/DC provides media conversion between EIA-232 from the PC and either EIA-422 or multi-mode fiber optic on the sensor side. The RS/DC also provides a fail-over mechanism to enable a sensor network to be polled with a dual-redundant set of RS/ DC u ...
... the Redundant Switcher/Data Converter (RS/DC) . The RS/DC provides media conversion between EIA-232 from the PC and either EIA-422 or multi-mode fiber optic on the sensor side. The RS/DC also provides a fail-over mechanism to enable a sensor network to be polled with a dual-redundant set of RS/ DC u ...
document
... Course Web page: - http://www.cs.berkeley.edu/~istoica/ee122 - check it periodically to get the latest information ...
... Course Web page: - http://www.cs.berkeley.edu/~istoica/ee122 - check it periodically to get the latest information ...
EN 1153742
... • EVM cannot exceed 35%. • Transmission spectral density has to be less than 20dBc relative to carrier and less than -30dBm absolute power, both at +/-3.5MHz offset from highest average spectral power measured within +/1MHz of carrier. Transmission power control range and transmission power step siz ...
... • EVM cannot exceed 35%. • Transmission spectral density has to be less than 20dBc relative to carrier and less than -30dBm absolute power, both at +/-3.5MHz offset from highest average spectral power measured within +/1MHz of carrier. Transmission power control range and transmission power step siz ...
Aalborg Universitet Bujlow, Tomasz; Riaz, Tahir; Pedersen, Jens Myrup
... is no need to continuously compute delays for all the paths, wasting processor, memory and storage resources [5]. Authors propose a sampling-based heuristic to compute a small set of paths to monitor, reducing monitoring overhead by nearly 50 % comparing to monitoring all the existing paths. Next pr ...
... is no need to continuously compute delays for all the paths, wasting processor, memory and storage resources [5]. Authors propose a sampling-based heuristic to compute a small set of paths to monitor, reducing monitoring overhead by nearly 50 % comparing to monitoring all the existing paths. Next pr ...
GAINING FULL CONTROL OF YOUR NETWORK WITH SERVICE PROVIDER SDN
... To achieve the network automation and optimizing benefits described above, SP SDN relies on four key capabilities: network abstraction, global network visibility, centralized network control, and policy. The network abstraction capabilities of SP SDN simplify how the network (and the services it sup ...
... To achieve the network automation and optimizing benefits described above, SP SDN relies on four key capabilities: network abstraction, global network visibility, centralized network control, and policy. The network abstraction capabilities of SP SDN simplify how the network (and the services it sup ...
Chapter 6
... • Collision Detect (CD): – Declared when any signal other than its own detected – If a collision is detected • To avoid a collision, wait a random amount of time and then resend message Copyright 2007 John Wiley & Sons, Inc ...
... • Collision Detect (CD): – Declared when any signal other than its own detected – If a collision is detected • To avoid a collision, wait a random amount of time and then resend message Copyright 2007 John Wiley & Sons, Inc ...
Converge without Conflation
... – There may be plenty of dark fibre, but it is dark – We are not time travellers and we need to offer bandwidth now ...
... – There may be plenty of dark fibre, but it is dark – We are not time travellers and we need to offer bandwidth now ...
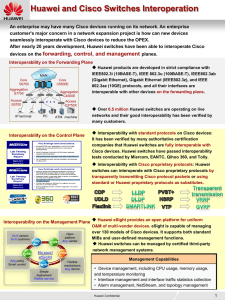
1 - Cisco Support Community
... Huawei &Cisco Interoperation Success Stories Turkey AveA's campus network project: Huawei S9700 interoperated with Cisco C6509E through OSPF and used BFD to speed up OSPF convergence. Huawei S5700 and Cisco 3560 ran VRRP to implement redundancy protection. S5700 and Cisco 2960/3560 ran standard MST ...
... Huawei &Cisco Interoperation Success Stories Turkey AveA's campus network project: Huawei S9700 interoperated with Cisco C6509E through OSPF and used BFD to speed up OSPF convergence. Huawei S5700 and Cisco 3560 ran VRRP to implement redundancy protection. S5700 and Cisco 2960/3560 ran standard MST ...
Lab 02 - IP Addresses
... Hardware address]. The MAC address of a network card indicates the vendor of that card and a unique serial number. 1.3.1 Rules of IPv4 Addressing 1. Format of IP Address: IPv4 is made up of four parts, in the pattern “w.x.y.z”. Each part has 8 binary bits and the values in decimal ranges from 0 to 2 ...
... Hardware address]. The MAC address of a network card indicates the vendor of that card and a unique serial number. 1.3.1 Rules of IPv4 Addressing 1. Format of IP Address: IPv4 is made up of four parts, in the pattern “w.x.y.z”. Each part has 8 binary bits and the values in decimal ranges from 0 to 2 ...
Primary Enabling Infrastructure for Mobile Internet
... are ideal for carrying high-value voice services but are not optimized for high bandwidth data services. • Backhaul links are becoming congested ...
... are ideal for carrying high-value voice services but are not optimized for high bandwidth data services. • Backhaul links are becoming congested ...
CloudWatcher: Network Security Monitoring Using OpenFlow in
... summarized as follows. First, it is a large-scale environment that consists of many physical hosts and virtual machines (VMs). For example, some study showed that Amazon EC2 Cloud runs at least half million physical hosts [1]. This is not the end, because each host will serve multiple virtual machin ...
... summarized as follows. First, it is a large-scale environment that consists of many physical hosts and virtual machines (VMs). For example, some study showed that Amazon EC2 Cloud runs at least half million physical hosts [1]. This is not the end, because each host will serve multiple virtual machin ...
Principals of Information Security, Fourth Edition
... lines or other data channels; these connections are usually secured under requirements of formal service agreement • When individuals seek to connect to organization’s network, more flexible option must be provided • Options such as virtual private networks (VPNs) have become more popular due to spr ...
... lines or other data channels; these connections are usually secured under requirements of formal service agreement • When individuals seek to connect to organization’s network, more flexible option must be provided • Options such as virtual private networks (VPNs) have become more popular due to spr ...
Slide 1
... the temporary IP address is returned to the DHCP server for re-use. Your ISP uses DHCP to assign you a temporary IP address when you connect to the Internet. ...
... the temporary IP address is returned to the DHCP server for re-use. Your ISP uses DHCP to assign you a temporary IP address when you connect to the Internet. ...
![Internet Security [1] - Distributed Systems Group](http://s1.studyres.com/store/data/008042804_1-fef73260079c1aa16dceefbf38249e12-300x300.png)