Preliminary Works
... Students will utilize basic command-line syntax to gather information about their network. This lab is intended to show that even basic CLI commands can yield valuable network information for a technician or to a potential hacker. ...
... Students will utilize basic command-line syntax to gather information about their network. This lab is intended to show that even basic CLI commands can yield valuable network information for a technician or to a potential hacker. ...
The Network Topology of the Interbank Market
... about 1.5 are email networks (1.5) [25] and co-autorships (1.2) [26]. For the left part of the distribution (small degrees) we find γsmall (Al ) = 0.69, γsmall (Aa ) = 1.01, and γsmall (A) = 0.62. These exponents are small compared to other real world networks. Compare e.g. with foodwebs (1) [27]. W ...
... about 1.5 are email networks (1.5) [25] and co-autorships (1.2) [26]. For the left part of the distribution (small degrees) we find γsmall (Al ) = 0.69, γsmall (Aa ) = 1.01, and γsmall (A) = 0.62. These exponents are small compared to other real world networks. Compare e.g. with foodwebs (1) [27]. W ...
BSNL_MNS
... Pune, Nashik and Aurangabad of Mahrashtra Telecom Circle. All India Requirements of the customers of these cities will be taken care of. ...
... Pune, Nashik and Aurangabad of Mahrashtra Telecom Circle. All India Requirements of the customers of these cities will be taken care of. ...
Network Automation and Orchestration
... provisioning the network is not only time-consuming, but also error-prone. This initial process can clearly benefit from automation where switches are able to download the correct image and configuration as soon as they are racked, stacked and powered on. • Management: Once a switch is provisioned, ...
... provisioning the network is not only time-consuming, but also error-prone. This initial process can clearly benefit from automation where switches are able to download the correct image and configuration as soon as they are racked, stacked and powered on. • Management: Once a switch is provisioned, ...
SINET3: NII?s new Network
... Virtual dedicated lines over shared platform form VPN among specified sites. Users can obtain protocol-free and completely exclusive environment. National Astronomical Observatory of Japan (NAOJ) utilizes L1VPN to transfer constantly-flowing ATM cells from remote telescopes through STM-16 inte ...
... Virtual dedicated lines over shared platform form VPN among specified sites. Users can obtain protocol-free and completely exclusive environment. National Astronomical Observatory of Japan (NAOJ) utilizes L1VPN to transfer constantly-flowing ATM cells from remote telescopes through STM-16 inte ...
PDF
... the destination address of the packet matches the port address, then switch drives the packet to the output port, Length of the data is of 8 bits and from 0 to 63. Length is measured in terms of bytes. Data should be in terms of bytes and can take anything. Frame check sequence contains the security ...
... the destination address of the packet matches the port address, then switch drives the packet to the output port, Length of the data is of 8 bits and from 0 to 63. Length is measured in terms of bytes. Data should be in terms of bytes and can take anything. Frame check sequence contains the security ...
Internet - DePaul University
... Network Address Translation (NAT) • NAT lets router represent entire local area network to Internet as single IP address – Thus, all traffic leaving LAN appears as originating from global IP address – All traffic coming into this LAN uses this global IP address ...
... Network Address Translation (NAT) • NAT lets router represent entire local area network to Internet as single IP address – Thus, all traffic leaving LAN appears as originating from global IP address – All traffic coming into this LAN uses this global IP address ...
P2P
... In the peer-to-peer paradigm, the participating processes play equal roles, with equivalent capabilities and responsibilities (hence the term “peer”). Each participant may issue a request to another participant and receive a response. ...
... In the peer-to-peer paradigm, the participating processes play equal roles, with equivalent capabilities and responsibilities (hence the term “peer”). Each participant may issue a request to another participant and receive a response. ...
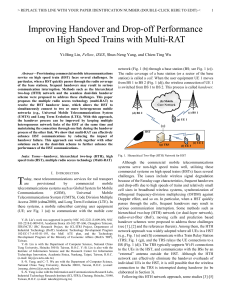
Improving Handover and Drop-off Performance - Jason Yi
... Fig. 1. Hierarchical Two-Hop (HTH) Network for HST ...
... Fig. 1. Hierarchical Two-Hop (HTH) Network for HST ...
Network Routing - Yale University
... shortest path from x back to S A packet is replicated to all but the incoming ...
... shortest path from x back to S A packet is replicated to all but the incoming ...
Topic 12 – Wide Area Networks
... – An important characteristic of a circuit-switching device is whether it is blocking or non blocking – Blocking occurs when the network is unable to connect two stations because all possible paths between them are already in use • A blocking network is one in which such blocking is possible ...
... – An important characteristic of a circuit-switching device is whether it is blocking or non blocking – Blocking occurs when the network is unable to connect two stations because all possible paths between them are already in use • A blocking network is one in which such blocking is possible ...
Revision topics for year 11 Computer Science
... (e) describe the differences between a local area network and a wide area network such as the internet (f) explain the terms IP addressing, MAC addressing, packet and protocols (g) explain the need for security measures in networks, such as user access levels, suitable passwords and encryption techn ...
... (e) describe the differences between a local area network and a wide area network such as the internet (f) explain the terms IP addressing, MAC addressing, packet and protocols (g) explain the need for security measures in networks, such as user access levels, suitable passwords and encryption techn ...
Review for Quiz-1 - Georgia Institute of Technology
... – 802.11b/g (WiFi): 11 or 54 Mbps • wider-area wireless access – provided by telco operator – 3G ~ 384 kbps • Will it happen?? – GPRS in Europe/US ...
... – 802.11b/g (WiFi): 11 or 54 Mbps • wider-area wireless access – provided by telco operator – 3G ~ 384 kbps • Will it happen?? – GPRS in Europe/US ...
Network Topology
... when staff members want to share data, the only means available is to copy the data on one computer to a floppy disk and insert the disk in another computer. Recently, problems have arisen. The business manager is spending too much time printing other people's documents; and it is frequently unclear ...
... when staff members want to share data, the only means available is to copy the data on one computer to a floppy disk and insert the disk in another computer. Recently, problems have arisen. The business manager is spending too much time printing other people's documents; and it is frequently unclear ...
Chapter 7 Powerpoints
... - It is aware of which nodes are on which side of the lan. - It determines whether a message should be passed on to another network ...
... - It is aware of which nodes are on which side of the lan. - It determines whether a message should be passed on to another network ...
Solutions Brief - Coriant Transcend™ SDN Solution
... SRLG (Shared Risk Link Group), and resilience as well as service status, towards the Packet Controller to allow multi-layer optimized and transport layer aware service routing. This enhances service reliability with the awareness of the shared risks of transport services. To provide pre-integration ...
... SRLG (Shared Risk Link Group), and resilience as well as service status, towards the Packet Controller to allow multi-layer optimized and transport layer aware service routing. This enhances service reliability with the awareness of the shared risks of transport services. To provide pre-integration ...
On the Convexity of Latent Social Network Inference
... show how to obtain a convex program with a l1 -like penalty term that encourages sparsity. We evaluate our approach on synthetic as well as real-world email and viral marketing datasets. Experiments reveal that we can near-perfectly recover the underlying network structure as well as the parameters ...
... show how to obtain a convex program with a l1 -like penalty term that encourages sparsity. We evaluate our approach on synthetic as well as real-world email and viral marketing datasets. Experiments reveal that we can near-perfectly recover the underlying network structure as well as the parameters ...
chapter02-v1.0
... - Many different conversations can be interleaved on the network. The process used to interleave the pieces of separate conversations together on the network is called multiplexing. - Increase the reliability of network communications. The separate pieces of each message need not travel the same pat ...
... - Many different conversations can be interleaved on the network. The process used to interleave the pieces of separate conversations together on the network is called multiplexing. - Increase the reliability of network communications. The separate pieces of each message need not travel the same pat ...
REBOOK
... architecture that overcome the rigid separation (and mistrust) between hosts/applications and the ...
... architecture that overcome the rigid separation (and mistrust) between hosts/applications and the ...
port
... eth0” There “eth0” stands for your first Ethernet interfaces. If you have wlan, you would probably say something like “dhclient wlan0” ...
... eth0” There “eth0” stands for your first Ethernet interfaces. If you have wlan, you would probably say something like “dhclient wlan0” ...
ppt
... • Elements (send/receive) data in terms of Frames. • Unique MAC (Media Access Control) address as an identifier for each element. • NIC within every element uses MAC addresses as an address of a house, determining if a frame carries its own address in the sake of passing it on to upper layers (accep ...
... • Elements (send/receive) data in terms of Frames. • Unique MAC (Media Access Control) address as an identifier for each element. • NIC within every element uses MAC addresses as an address of a house, determining if a frame carries its own address in the sake of passing it on to upper layers (accep ...
CarNet - Disco Lab - Rutgers University
... •Using GLS any node may locate any other whose ID is well-known •Privacy of user’s location and movements is an issue •Nodes can share a pool of IP addresses – opening connections to a node will be impossible as its current ID is unknown •Nodes can employ proxies to prevent contacted nodes from lear ...
... •Using GLS any node may locate any other whose ID is well-known •Privacy of user’s location and movements is an issue •Nodes can share a pool of IP addresses – opening connections to a node will be impossible as its current ID is unknown •Nodes can employ proxies to prevent contacted nodes from lear ...
Communication - Princeton University
... • No need to update the routers – E.g., adding a new host 5.6.7.213 on the right – Doesn’t require adding a new forwarding-table entry ...
... • No need to update the routers – E.g., adding a new host 5.6.7.213 on the right – Doesn’t require adding a new forwarding-table entry ...
Networking Support For Mobile Computing
... stationary users, each user has a fixed address that is used to transfer information to them. Information is transferred by a process called routing, where a route is found to the user for information transfer. Many network protocols are optimized for a wired medium rather than a wireless medium. Th ...
... stationary users, each user has a fixed address that is used to transfer information to them. Information is transferred by a process called routing, where a route is found to the user for information transfer. Many network protocols are optimized for a wired medium rather than a wireless medium. Th ...