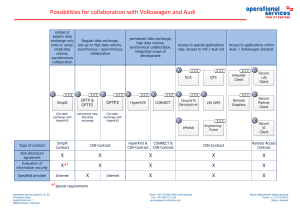
Possibilities for collaboration with Volkswagen
... (PKI card or similar) provided to them for performing their activities from the working environment and from the terminal and personally hold them in safe keeping. The commissioning department and/or corporate security at Volkswagen AG receives unrestricted, authorized access to the premises as well ...
... (PKI card or similar) provided to them for performing their activities from the working environment and from the terminal and personally hold them in safe keeping. The commissioning department and/or corporate security at Volkswagen AG receives unrestricted, authorized access to the premises as well ...
Wide Area Network Approvals Memorandum of Understanding
... ISSM Responsibilities for Connection to WAN All remote participant sites will operate in the PL1 mode accredited by their local DSS office. 1.Notify the Network Security Manager (NSM) of any proposed external connections or system changes effecting security. 2.Notify NSM of any local SSP or protecti ...
... ISSM Responsibilities for Connection to WAN All remote participant sites will operate in the PL1 mode accredited by their local DSS office. 1.Notify the Network Security Manager (NSM) of any proposed external connections or system changes effecting security. 2.Notify NSM of any local SSP or protecti ...
Security Agents for Network Traffic Analysis
... runtime. When an agent needs to execute on the runtime, the runtime creates a new thread which executes the agent’s program. ...
... runtime. When an agent needs to execute on the runtime, the runtime creates a new thread which executes the agent’s program. ...
AVOCENT DATA CENTER SOLUTIONS Secure, Centralized Data Center Management ®
... The Avocent Universal Management Gateway appliance enables secure, remote server management using embedded server management technologies such as IPMI, Dell DRAC, HP iLO, IBM RSA II, Sun ALOM, Sun ILOM, Fujitsu iRMC and IBM BladeCenter. Features • Single console for multiple service processor types ...
... The Avocent Universal Management Gateway appliance enables secure, remote server management using embedded server management technologies such as IPMI, Dell DRAC, HP iLO, IBM RSA II, Sun ALOM, Sun ILOM, Fujitsu iRMC and IBM BladeCenter. Features • Single console for multiple service processor types ...
Under Threat or Compromise - Every Detail Counts
... Just because you’ve reimaged all the hosts the attackers were observed communicating to does not mean the attackers are gone. They may be lying dormant in other areas of the network.5 However, by using network packet data, defenders can be sure of detecting the attackers if they activate dormant bac ...
... Just because you’ve reimaged all the hosts the attackers were observed communicating to does not mean the attackers are gone. They may be lying dormant in other areas of the network.5 However, by using network packet data, defenders can be sure of detecting the attackers if they activate dormant bac ...
What is Trusted Computing and Digital Rights Management
... What are the risks associated with Trusted Computing and Digital Rights Management? DRM can adversely affect the full usability of documents. Information providers can encumber documents with restrictions and conditions imposed by the provider. For example, providers can set a document to become un ...
... What are the risks associated with Trusted Computing and Digital Rights Management? DRM can adversely affect the full usability of documents. Information providers can encumber documents with restrictions and conditions imposed by the provider. For example, providers can set a document to become un ...
Database Security
... simultaneously cannot exceed some limit – Can disallow sets of queries that repeatedly involve the same records ...
... simultaneously cannot exceed some limit – Can disallow sets of queries that repeatedly involve the same records ...
Introduction to IT Security - Virginia Alliance for Secure Computing
... Confidentiality: Ensures that the info in a system and transmitted info are accessible only for reading by authorized parties. (Data Privacy) Integrity: Ensures that only authorized parties are able to modify computer systems assets and transmitted information. (Data has not been altered) Authent ...
... Confidentiality: Ensures that the info in a system and transmitted info are accessible only for reading by authorized parties. (Data Privacy) Integrity: Ensures that only authorized parties are able to modify computer systems assets and transmitted information. (Data has not been altered) Authent ...
Internet Security
... But – good citizenship make it more difficult for hackers A packet filter can reject outbound packets with illegal IP addresses could not have been legally generated inside the network Example 140.192.*.* are DePaul IP addresses if an outbound packet has a source address of ...
... But – good citizenship make it more difficult for hackers A packet filter can reject outbound packets with illegal IP addresses could not have been legally generated inside the network Example 140.192.*.* are DePaul IP addresses if an outbound packet has a source address of ...
Performance-aware Security for Unicast Communication in Hybrid Satellite Networks
... • TCP Performance Enhancing Proxy (PEP) server used to mitigate the negative impact of satellite link propagation delay on TCP performance. • HTTP Proxy server used to reduce the effect of satellite link delay on HTTP protocol/web browsing. • IPSEC disables the functionality of TCP PEP and HTTP ...
... • TCP Performance Enhancing Proxy (PEP) server used to mitigate the negative impact of satellite link propagation delay on TCP performance. • HTTP Proxy server used to reduce the effect of satellite link delay on HTTP protocol/web browsing. • IPSEC disables the functionality of TCP PEP and HTTP ...
Introduction to Operations Security (OPSEC)
... Do not discuss critical information with anyone who does not have a “need-to-know.” Safeguard sensitive information the same way you would protect classified information. Use common sense and camouflage sensitive information. By providing OPSEC training to all employees, every employee becomes a “se ...
... Do not discuss critical information with anyone who does not have a “need-to-know.” Safeguard sensitive information the same way you would protect classified information. Use common sense and camouflage sensitive information. By providing OPSEC training to all employees, every employee becomes a “se ...
Chap 12
... Establish process for avoiding further exploitations of the same vulnerability Avoid escalation and further incidents Assess impact and damage of the incident Recover from the incident ...
... Establish process for avoiding further exploitations of the same vulnerability Avoid escalation and further incidents Assess impact and damage of the incident Recover from the incident ...
US SAFE WEB Act - Higher Education Compliance Alliance
... only keeping information that is needed and many universities, especially public universities, are subject to statutes which require keeping records for a number of years, so scaling down records may not be feasible. However, a useful tip from this principle is limiting information to only those emp ...
... only keeping information that is needed and many universities, especially public universities, are subject to statutes which require keeping records for a number of years, so scaling down records may not be feasible. However, a useful tip from this principle is limiting information to only those emp ...
Global Information Assurance Certification (GIAC) develops and administers the premier
... (GSE). For good reason. It’s the most prestigious, most demanding certification in the information security industry. The GSE’s performancebased, hands-on nature sets it apart from any other certification in the IT security industry. Those who earn the GSE master the wide variety of skills, across m ...
... (GSE). For good reason. It’s the most prestigious, most demanding certification in the information security industry. The GSE’s performancebased, hands-on nature sets it apart from any other certification in the IT security industry. Those who earn the GSE master the wide variety of skills, across m ...
Unix Network Security - LSU Computer Science
... Security Essentials Security is a very general terminology in computer science environment. Since electronic communication and electronic data has an essential importance in all aspects of business and personal process, leaking information may produce harmful damages for different situation. However ...
... Security Essentials Security is a very general terminology in computer science environment. Since electronic communication and electronic data has an essential importance in all aspects of business and personal process, leaking information may produce harmful damages for different situation. However ...
Vpn Iaun Ac Ir
... Vpn Iaun Ac Ir - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while benefitin ...
... Vpn Iaun Ac Ir - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while benefitin ...
ch02kc
... Mail bombing: also a DoS; attacker routes large quantities of e-mail to target Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network Social engineering: using social skills to convince people ...
... Mail bombing: also a DoS; attacker routes large quantities of e-mail to target Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network Social engineering: using social skills to convince people ...
Slide 1
... US Federal Government after sensitive customer data, including credit card numbers and personal information, allegedly were stolen three times in less than two years. ...
... US Federal Government after sensitive customer data, including credit card numbers and personal information, allegedly were stolen three times in less than two years. ...
document
... be a local leased line (much less expensive than a longdistance one), or it could be a local broadband connection such as DSL service. ...
... be a local leased line (much less expensive than a longdistance one), or it could be a local broadband connection such as DSL service. ...
Literature Review - Rhodes University
... Verifying that users are who they claim to be, these may be a person using a computer, a computer itself or a program on a computer. Oracle allows 4 login trials before the database is blocked and also allows a password to be used only for three months to combat authentication breaches. The database ...
... Verifying that users are who they claim to be, these may be a person using a computer, a computer itself or a program on a computer. Oracle allows 4 login trials before the database is blocked and also allows a password to be used only for three months to combat authentication breaches. The database ...
Chapter 1 - IPFW ETCS
... become what is known as zombie. Then the attacker chooses a victim and sends a signal to all the zombies to launch the attack. It means the victim counters n attacks from the n zombies all acting at once. ...
... become what is known as zombie. Then the attacker chooses a victim and sends a signal to all the zombies to launch the attack. It means the victim counters n attacks from the n zombies all acting at once. ...
spear-phishing attacks
... FireEye protects the most valuable assets in the world from those who have them in their sights. Our combination of technology, intelligence, and expertise—reinforced with the most aggressive incident response team—helps eliminate the impact of security breaches. With FireEye, you’ll detect attacks ...
... FireEye protects the most valuable assets in the world from those who have them in their sights. Our combination of technology, intelligence, and expertise—reinforced with the most aggressive incident response team—helps eliminate the impact of security breaches. With FireEye, you’ll detect attacks ...
Port Scanning
... If the port sends back an ICMP “Port Unreachable” message, the port is closed. Again, not getting that message might imply the port is open, but this isn’t always true. A firewall or packetfiltering device could undermine your assumptions ...
... If the port sends back an ICMP “Port Unreachable” message, the port is closed. Again, not getting that message might imply the port is open, but this isn’t always true. A firewall or packetfiltering device could undermine your assumptions ...
Introduction to CyberWarfare: Offensive and Defensive Software
... begin by discussing the common operational picture that has been used for military situational awareness for many years. They use this foundation as a means to present and discuss the need for similar doctrine and tools in the cyberspace domain. This interesting gap analysis is discussed in the cont ...
... begin by discussing the common operational picture that has been used for military situational awareness for many years. They use this foundation as a means to present and discuss the need for similar doctrine and tools in the cyberspace domain. This interesting gap analysis is discussed in the cont ...