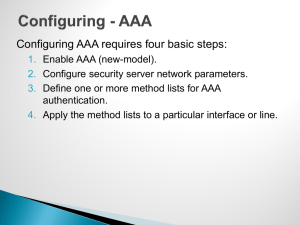
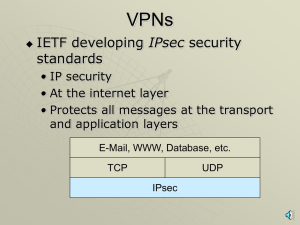
Security
... to encrypt and decrypt e-mail over the Internet. It can also be used to send an encrypted digital signature that lets the receiver verify the sender's identity and know that the message was not changed en route. Available both as freeware and in a low-cost commercial version, PGP is the most widely ...
... to encrypt and decrypt e-mail over the Internet. It can also be used to send an encrypted digital signature that lets the receiver verify the sender's identity and know that the message was not changed en route. Available both as freeware and in a low-cost commercial version, PGP is the most widely ...
Router/Switch Security
... This ensures that the device on the remote end of the connection is still accessible and that half−open or orphaned connections are removed from the local Cisco device. ...
... This ensures that the device on the remote end of the connection is still accessible and that half−open or orphaned connections are removed from the local Cisco device. ...
Copyright Infringement Policies and Sanctions
... policies of the affiliated networks and systems. Each person requesting service from a PQC Telecommunications and Networking technician for equipment owned by a person or entity other than PQC must acknowledge and accept the following liability release before the technician provides the requested se ...
... policies of the affiliated networks and systems. Each person requesting service from a PQC Telecommunications and Networking technician for equipment owned by a person or entity other than PQC must acknowledge and accept the following liability release before the technician provides the requested se ...
Chapter 5 Protection of Information Assets
... • Verify user authorization within the application • Verify user authorization at the field level for changes within a database • Verify subsystem authorization for the user at the file level • Log database / data communications access activities for monitoring access violations ...
... • Verify user authorization within the application • Verify user authorization at the field level for changes within a database • Verify subsystem authorization for the user at the file level • Log database / data communications access activities for monitoring access violations ...
ISi-L - BSI
... between computers, though. Language (e.g. voice over IP) and multi-media contents (e.g. internet TV) are increasingly being transmitted using a standardised IP infrastructure. Another basic protocol is the Internet Control Message ICMP that provides functions for controlling the flow of data. For ex ...
... between computers, though. Language (e.g. voice over IP) and multi-media contents (e.g. internet TV) are increasingly being transmitted using a standardised IP infrastructure. Another basic protocol is the Internet Control Message ICMP that provides functions for controlling the flow of data. For ex ...
Why Study Computers and Digital Technologies?
... Special-purpose computers are designed primarily for one particular function ...
... Special-purpose computers are designed primarily for one particular function ...
Guide to Firewalls and Network Security with Intrusion Detection and
... NAT Hides TCP/IP information of hosts in the network being protected ...
... NAT Hides TCP/IP information of hosts in the network being protected ...
Lecture X ISA & IPSecurity
... Confidentiality: confidentiality services prevent unauthorized access to sensitive data as it passes between parties Data origin authentication and integrity—Data origin authentication and integrity is provided by a hashed message authentication code (HMAC) value, which is included in every packet. ...
... Confidentiality: confidentiality services prevent unauthorized access to sensitive data as it passes between parties Data origin authentication and integrity—Data origin authentication and integrity is provided by a hashed message authentication code (HMAC) value, which is included in every packet. ...
Privacy
... numbers/characters) is used with an algorithm to encrypt/decrypt messages • Important for Internet commerce where people send critical data such as credit card numbers Bordoloi ...
... numbers/characters) is used with an algorithm to encrypt/decrypt messages • Important for Internet commerce where people send critical data such as credit card numbers Bordoloi ...
Cyberespionage campaign hits energy companies
... that supports bidirectional reading/writing of process variables, but does not provide more advanced capabilities like device con guration and rmware updates. OPC is a standard way for process control systems, applications and devices to interact with each other. It is important to note that not al ...
... that supports bidirectional reading/writing of process variables, but does not provide more advanced capabilities like device con guration and rmware updates. OPC is a standard way for process control systems, applications and devices to interact with each other. It is important to note that not al ...
Chapter 7 Review
... Your organization hosts a web site within a DMZ and the web site accesses a database server in the internal network. ACLs on firewalls prevent any connections to the database server except from the web server. Database fields holding customer data are encrypted and all data in transit between the w ...
... Your organization hosts a web site within a DMZ and the web site accesses a database server in the internal network. ACLs on firewalls prevent any connections to the database server except from the web server. Database fields holding customer data are encrypted and all data in transit between the w ...
VPNs, PKIs, ISSs, SSLs with narration
... Another Security System for VPNs is the Point-to-Point Tunneling Protocol (PPTP) ...
... Another Security System for VPNs is the Point-to-Point Tunneling Protocol (PPTP) ...
Chapter 11 Outline
... IPSec connection is established, it is possible to tunnel across other networks at lower levels of the OSI model. C. The set of security services provided by IPSec occurs at the network layer of the OSI model, so higher layer protocols, such as TCP, UDP, ICMP, and BGP, are unaffected by the implemen ...
... IPSec connection is established, it is possible to tunnel across other networks at lower levels of the OSI model. C. The set of security services provided by IPSec occurs at the network layer of the OSI model, so higher layer protocols, such as TCP, UDP, ICMP, and BGP, are unaffected by the implemen ...
Lecture12
... items and processes that operate on those data items. The key data type in the Clark-Wilson model is a Constrained Data Item (CDI). An Integrity Verification Procedure (IVP) ensures that all CDIs in the system are valid at a certain state. Transactions that enforce the integrity policy are represent ...
... items and processes that operate on those data items. The key data type in the Clark-Wilson model is a Constrained Data Item (CDI). An Integrity Verification Procedure (IVP) ensures that all CDIs in the system are valid at a certain state. Transactions that enforce the integrity policy are represent ...
module_70
... client connects to a SOCKS proxy server. The proxy server connects to the application server on behalf of the client, and relays data between the client and the application server. For the application server, the proxy server is the ...
... client connects to a SOCKS proxy server. The proxy server connects to the application server on behalf of the client, and relays data between the client and the application server. For the application server, the proxy server is the ...
Cyber ShockWave exposed missing links in US security
... are on the front lines because our personal communications and network systems are the conduits for Internet warfare. This means that the responsibility for cybersecurity must be a joint effort involving not only our government’s national security and homeland security elements and private enterpris ...
... are on the front lines because our personal communications and network systems are the conduits for Internet warfare. This means that the responsibility for cybersecurity must be a joint effort involving not only our government’s national security and homeland security elements and private enterpris ...
WelcometoCISandCybercorps
... Attack Modeling/Visualization • DoJ project developing coherent schemes for monitoring and visualizing Internet attacks in real-time • Java prototype under development • Distributed agents synthesize feedback from IDS into a special language • Subsequently transformed into an integrated graphical r ...
... Attack Modeling/Visualization • DoJ project developing coherent schemes for monitoring and visualizing Internet attacks in real-time • Java prototype under development • Distributed agents synthesize feedback from IDS into a special language • Subsequently transformed into an integrated graphical r ...
Getting Security Right in Wireless Sensor Networks
... The simplest solution to this reverse-engineering problem is to ensure that every communication session (or flow of data between two endpoints) has its own unique keys that are unknown to any other nodes in the network. In this case, even a compromised node in the network cannot snoop, manipulate, o ...
... The simplest solution to this reverse-engineering problem is to ensure that every communication session (or flow of data between two endpoints) has its own unique keys that are unknown to any other nodes in the network. In this case, even a compromised node in the network cannot snoop, manipulate, o ...
Peer Router retains public key on routing table Route discovery
... Imai Lab, IIS, University of Tokyo ...
... Imai Lab, IIS, University of Tokyo ...
Network Flow Analysis in Information Security Strategy
... Support controls to prevent or slow propagation or escalation Flow signatures (Jones/Shimeall, FloCon 2014) • DNS responses without prior requests • DNS responses from non-authoritative source • Email or Web contacts to addresses associated with DNS source ...
... Support controls to prevent or slow propagation or escalation Flow signatures (Jones/Shimeall, FloCon 2014) • DNS responses without prior requests • DNS responses from non-authoritative source • Email or Web contacts to addresses associated with DNS source ...
Course Overview - Cyber Security Lab
... reveal information, such as the location and identity of communication hosts, or the frequency and length of data being exchanged, which might be useful in guessing the nature of the communication that is taking place. Passive attacks are difficult to detect because traffic is still sent and receive ...
... reveal information, such as the location and identity of communication hosts, or the frequency and length of data being exchanged, which might be useful in guessing the nature of the communication that is taking place. Passive attacks are difficult to detect because traffic is still sent and receive ...
Multimedia Application Production
... It becomes a target to millions of various attack Computer’s IP address Registered and known to others Attacks against Internet-connected computers Can come in the form of direct attacks or Through viruses, worms, or spyware ...
... It becomes a target to millions of various attack Computer’s IP address Registered and known to others Attacks against Internet-connected computers Can come in the form of direct attacks or Through viruses, worms, or spyware ...
Speech Title Here
... Stay current with service packs and updates Harden IIS with IISLockdown and URLScan Harden the Web server's TCP/IP stack Run ASP.NET using principle of least privilege ACL resources to prevent unauthorized access Disable unused shares and services Move Web root to drive other than C: ...
... Stay current with service packs and updates Harden IIS with IISLockdown and URLScan Harden the Web server's TCP/IP stack Run ASP.NET using principle of least privilege ACL resources to prevent unauthorized access Disable unused shares and services Move Web root to drive other than C: ...