Lab 11.6.1: Basic OSPF Configuration Lab (Instructor Version)
... Step 1: Configure interfaces on R1, R2, and R3. Configure the interfaces on the R1, R2, and R3 routers with the IP addresses from the table under the Topology Diagram. Step 2: Verify IP addressing and interfaces. Use the show ip interface brief command to verify that the IP addressing is correct and ...
... Step 1: Configure interfaces on R1, R2, and R3. Configure the interfaces on the R1, R2, and R3 routers with the IP addresses from the table under the Topology Diagram. Step 2: Verify IP addressing and interfaces. Use the show ip interface brief command to verify that the IP addressing is correct and ...
WHO Global Measles and Rubella Laboratory Network
... The boundaries and names shown and the designations used on this map do not imply the expression of any opinion whatsoever on the part of the World Health Organization concerning the legal status of any country, territory, city or area or of its authorities, or concerning the delimitation of its fro ...
... The boundaries and names shown and the designations used on this map do not imply the expression of any opinion whatsoever on the part of the World Health Organization concerning the legal status of any country, territory, city or area or of its authorities, or concerning the delimitation of its fro ...
Lab Additions/Suggestions previously done
... • Scan of the Month Challenge • Using SNORT to act as an Intrusion Detection System • Advanced uses of Ethereal • Introduction to Advanced Intrusion Detection Environment • Snare for Windows • Forensics Investigation the Penguin Sleuth Kit Appendix A: Review of how to set up and run imapd exploit Ap ...
... • Scan of the Month Challenge • Using SNORT to act as an Intrusion Detection System • Advanced uses of Ethereal • Introduction to Advanced Intrusion Detection Environment • Snare for Windows • Forensics Investigation the Penguin Sleuth Kit Appendix A: Review of how to set up and run imapd exploit Ap ...
Application Notes for Configuring QuesCom 400 IP/GSM Gateway
... be routed to the QuesCom 400 IP/GSM gateway. The QuesCom 400 IP/GSM can also receive calls from the GSM network and route the calls to Avaya Communications Manager. The QuesCom 400 IP/GSM can provide a backup route for the PSTN and also be backed up by the PSTN. This can be configured in Avaya Commu ...
... be routed to the QuesCom 400 IP/GSM gateway. The QuesCom 400 IP/GSM can also receive calls from the GSM network and route the calls to Avaya Communications Manager. The QuesCom 400 IP/GSM can provide a backup route for the PSTN and also be backed up by the PSTN. This can be configured in Avaya Commu ...
Packet Switching
... space and time division elements Use digital time division techniques to set up and maintain virtual circuits Partition low speed bit stream into pieces that share higher speed stream Individual pieces manipulated by control logic to flow from input to output ...
... space and time division elements Use digital time division techniques to set up and maintain virtual circuits Partition low speed bit stream into pieces that share higher speed stream Individual pieces manipulated by control logic to flow from input to output ...
Webinar Title - Websense Knowledge Bases
... This completely depends on your company policy and how you would like to configure your policies. However this will mean that you will have to apply different policies on them when 29. Is the basic auth on http or https protocol? Basic auth for any requests coming from roaming users that are coming ...
... This completely depends on your company policy and how you would like to configure your policies. However this will mean that you will have to apply different policies on them when 29. Is the basic auth on http or https protocol? Basic auth for any requests coming from roaming users that are coming ...
Autonomic Computing - DPNM Lab
... management tools seem to be inadequate for handling the scale, complexity, dynamism and heterogeneity of emerging future network and systems Biological systems have evolved strategies to cope with dynamic, complex, highly uncertain constraints Recently, some research area of IT is applying biolo ...
... management tools seem to be inadequate for handling the scale, complexity, dynamism and heterogeneity of emerging future network and systems Biological systems have evolved strategies to cope with dynamic, complex, highly uncertain constraints Recently, some research area of IT is applying biolo ...
Security of Cookies in a computer lab setting
... – High security, cleans up cookies when the user shuts down the web browser – Mischievous user may “disable” the program in some fashion – Program may crash ...
... – High security, cleans up cookies when the user shuts down the web browser – Mischievous user may “disable” the program in some fashion – Program may crash ...
The Guidelines on Cyber Security onboard Ships - ics
... the worldwide web. This brings the greater risk of unauthorised access or malicious attacks to ships’ systems and networks. Risks may also occur from personnel having access to the systems onboard, for example by introducing malware via removable media. Relevant personnel should have training in ide ...
... the worldwide web. This brings the greater risk of unauthorised access or malicious attacks to ships’ systems and networks. Risks may also occur from personnel having access to the systems onboard, for example by introducing malware via removable media. Relevant personnel should have training in ide ...
GCF Generic Connector Framework Training Session
... Identifying errors and troubleshooting use cases Usage of GCF XML tags Debug process for verifying connector Logging and system verification for GCF connectors Start stop of Generic connector web server Maintenance, Migrations etc. (NOTE: Should we complete the initial sample connector, ...
... Identifying errors and troubleshooting use cases Usage of GCF XML tags Debug process for verifying connector Logging and system verification for GCF connectors Start stop of Generic connector web server Maintenance, Migrations etc. (NOTE: Should we complete the initial sample connector, ...
ECE 467 Network Implementation Lab Manual
... List of Figures Figure 1 OSI layer communication............................................................................................... 12 Figure 2 RJ-48C cross-over .......................................................................................................... 21 Figure 3 RJ-45 ...
... List of Figures Figure 1 OSI layer communication............................................................................................... 12 Figure 2 RJ-48C cross-over .......................................................................................................... 21 Figure 3 RJ-45 ...
Tenable Malware Detection
... DNS entries, database access requests, web based attacks targeting web applications and suspect internet communications. Network sniffing is also an extremely useful tool when looking for botnet infiltration, and for the forensic analysis of what activity the bots in your environment have conducted. ...
... DNS entries, database access requests, web based attacks targeting web applications and suspect internet communications. Network sniffing is also an extremely useful tool when looking for botnet infiltration, and for the forensic analysis of what activity the bots in your environment have conducted. ...
Federated DAFS: Scalable Cluster-based Direct Access File Servers
... Summary of real directory info is generated and exchanged at initialization Cached in memory and updated on directory modifying operations ...
... Summary of real directory info is generated and exchanged at initialization Cached in memory and updated on directory modifying operations ...
Making your Enterprise Cyber Resilient
... to gain access to critical information and secure areas without having to break through firewalls and other technology-based protection layers. Better information sharing is also important. Organizations should share and have access to all threat indicators to help decrease the rate of attacks. Adva ...
... to gain access to critical information and secure areas without having to break through firewalls and other technology-based protection layers. Better information sharing is also important. Organizations should share and have access to all threat indicators to help decrease the rate of attacks. Adva ...
The Inexact Science of Internet Filtering for the K
... • No virus/worm/trojan/malware scanning for web downloads. • No ability to set policies on a per group or user-basis. • No ability to rewrite web requests to enable site-specific safety features, e.g. force Google and Yahoo safe search. • No content caching to improve performance. • Limited ability ...
... • No virus/worm/trojan/malware scanning for web downloads. • No ability to set policies on a per group or user-basis. • No ability to rewrite web requests to enable site-specific safety features, e.g. force Google and Yahoo safe search. • No content caching to improve performance. • Limited ability ...
Basic Ethernet/IP Lab
... Welcome to the “Applying Basic EtherNet/IP Features in Converged Plant-wide Ethernet Architectures” Lab. The Stratix 5700 and Stratix 8000 are Rockwell Automation Managed Ethernet Switches that utilizes Cisco technology. These switches offers the Best of Cisco and the Best of Allen-Bradley. These pr ...
... Welcome to the “Applying Basic EtherNet/IP Features in Converged Plant-wide Ethernet Architectures” Lab. The Stratix 5700 and Stratix 8000 are Rockwell Automation Managed Ethernet Switches that utilizes Cisco technology. These switches offers the Best of Cisco and the Best of Allen-Bradley. These pr ...
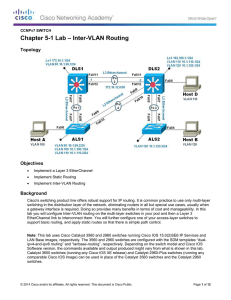
Lab 5-1 Inter-VLAN Routing
... Cisco's switching product line offers robust support for IP routing. It is common practice to use only multi-layer switching in the distribution layer of the network, eliminating routers in all but special use cases, usually when a gateway interface is required. Doing so provides many benefits in te ...
... Cisco's switching product line offers robust support for IP routing. It is common practice to use only multi-layer switching in the distribution layer of the network, eliminating routers in all but special use cases, usually when a gateway interface is required. Doing so provides many benefits in te ...
Slide 1
... Do generalized alert correlation analysis. Instead of requiring (certain types of) attribute value match (e.g., the destination IP address of one alert matches the source IP of another) ...
... Do generalized alert correlation analysis. Instead of requiring (certain types of) attribute value match (e.g., the destination IP address of one alert matches the source IP of another) ...
Mobile IP: General Security Issues
... located; that is the link, which has been assigned the same network-prefix as the node’s IP address A foreign link is any link other than a node’s home link – that is, any link whose network-prefix differs from that of the node’s IP address Host-specific route is a routing-table with Prefix-Length o ...
... located; that is the link, which has been assigned the same network-prefix as the node’s IP address A foreign link is any link other than a node’s home link – that is, any link whose network-prefix differs from that of the node’s IP address Host-specific route is a routing-table with Prefix-Length o ...
New Tools on the Bot War Front
... not a bot, per se, because it was not part of a large remote-controlled network. However, this example does show how difficult remote-controlled malware is to detect once it gets inside the network and how easily it can hide command/control and outbound data transfers in HTTP. On an organizational l ...
... not a bot, per se, because it was not part of a large remote-controlled network. However, this example does show how difficult remote-controlled malware is to detect once it gets inside the network and how easily it can hide command/control and outbound data transfers in HTTP. On an organizational l ...
DSU / CSU NETWORK DESIGN LAB INTRODUCTION
... The objective of this lab is to gain an understanding of the functionality of a Channel Service Unit / Data Service Unit (CSU/DSU) system employed within an Internet Protocol (IP) communications network. INTRODUCTION (Students read prior to attending lab session) The CSU is a device that performs pr ...
... The objective of this lab is to gain an understanding of the functionality of a Channel Service Unit / Data Service Unit (CSU/DSU) system employed within an Internet Protocol (IP) communications network. INTRODUCTION (Students read prior to attending lab session) The CSU is a device that performs pr ...
17 September 2015
... knowledge – must improve if insurers are to meet growing demand. In addition, as with any other emerging risk, insurers also face challenges around pricing, untested policy wordings, modelling and risk accumulation. Responding to cyber risk The AGCS report highlights steps companies can take to addr ...
... knowledge – must improve if insurers are to meet growing demand. In addition, as with any other emerging risk, insurers also face challenges around pricing, untested policy wordings, modelling and risk accumulation. Responding to cyber risk The AGCS report highlights steps companies can take to addr ...
Open resource
... collaboration between industry and government, consists of standards, guidelines, and practices to promote the protection of critical infrastructure The prioritized, flexible, repeatable, and cost-effective approach of the Framework helps owners and operators of critical infrastructure to manage c ...
... collaboration between industry and government, consists of standards, guidelines, and practices to promote the protection of critical infrastructure The prioritized, flexible, repeatable, and cost-effective approach of the Framework helps owners and operators of critical infrastructure to manage c ...
HIgh PErformance Radio Local Network (HIPERLAN) – Type 1
... means of a Channel Access Mechanism (CAM) with priorities Easy establishment of wireless ad-hoc LAN, by using distributed topology and routing functions in the MAC layer ...
... means of a Channel Access Mechanism (CAM) with priorities Easy establishment of wireless ad-hoc LAN, by using distributed topology and routing functions in the MAC layer ...
Power Point Slides - Organization of American States
... sector, transportation, press, energy sector, etc. •Carried out in Argentina, Colombia, Guatemala, Panama, Paraguay, Peru, Trinidad, and Uruguay, Washington DC www.oas.org/cyber/ ...
... sector, transportation, press, energy sector, etc. •Carried out in Argentina, Colombia, Guatemala, Panama, Paraguay, Peru, Trinidad, and Uruguay, Washington DC www.oas.org/cyber/ ...