General Assembly 1 Background Guide
... and attacks. Sensitive government information is also often stored online and past leaks have put numerous individuals, including informants and military operatives, in great danger. Millions of cyber attacks take place each day and combatting this growing threat will necessitate a multilateral and ...
... and attacks. Sensitive government information is also often stored online and past leaks have put numerous individuals, including informants and military operatives, in great danger. Millions of cyber attacks take place each day and combatting this growing threat will necessitate a multilateral and ...
Weitere Entwicklung und Konvergenz der CDISC
... ODM team would like to publish the CDASH forms as ODM 1.3 metadata files, for use in (e)CRFs Currently in discussion with CDISC Technical Leadership Committee Issues: ...
... ODM team would like to publish the CDASH forms as ODM 1.3 metadata files, for use in (e)CRFs Currently in discussion with CDISC Technical Leadership Committee Issues: ...
Internet Vulnerabilities & Criminal Activity
... Know the law enforcement difficulties working internationally Use several proxies in different counties to route connections Know which countries are weak on cyber enforcement ...
... Know the law enforcement difficulties working internationally Use several proxies in different counties to route connections Know which countries are weak on cyber enforcement ...
Captain James Mills â Cyber Operations
... Develop and deliver enhanced cyber situational awareness tools Tune operations to cyber “attack” risk Key terrain analysis Continuity of Operations Vital information protection ...
... Develop and deliver enhanced cyber situational awareness tools Tune operations to cyber “attack” risk Key terrain analysis Continuity of Operations Vital information protection ...
Babu Madhav Institute of Information Technology, UTU 2017
... 10. Looking into the trash for information is known as _________________. 11. _________________ is equivalent to dumpster diving. 12. Botnets are also called as ___________ networks. MULTIPLE CHOICE QUESTIONS:1) Gathering information about a target without his/her knowledge is known as a) Attack b) ...
... 10. Looking into the trash for information is known as _________________. 11. _________________ is equivalent to dumpster diving. 12. Botnets are also called as ___________ networks. MULTIPLE CHOICE QUESTIONS:1) Gathering information about a target without his/her knowledge is known as a) Attack b) ...
Babu Madhav Institute of Information Technology, UTU 2015
... 8. What is social engineering? Explain an example of any one type of social engineering. 9. Explain human based social engineering in depth. 10. Explain computer based social engineering in depth. 11. Differentiate between shoulder surfing and dumpster diving. 12. Justify how pop-up windows can be s ...
... 8. What is social engineering? Explain an example of any one type of social engineering. 9. Explain human based social engineering in depth. 10. Explain computer based social engineering in depth. 11. Differentiate between shoulder surfing and dumpster diving. 12. Justify how pop-up windows can be s ...
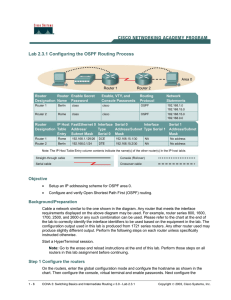
Lab 2.3.1 Configuring the OSPF Routing Process Objective
... FastEthernet 0/1 (FA0/1) Serial 0/0 (S0/0) Serial 0/1 (S0/1) (FA0/0) In order to find out exactly how the router is configured, look at the interfaces. This will identify what type and how many interfaces the router has. There is no way to effectively list all of the combinations of configurations f ...
... FastEthernet 0/1 (FA0/1) Serial 0/0 (S0/0) Serial 0/1 (S0/1) (FA0/0) In order to find out exactly how the router is configured, look at the interfaces. This will identify what type and how many interfaces the router has. There is no way to effectively list all of the combinations of configurations f ...
Document
... Introduction to Cyber Network Defense • Cyber Network Defense (CND) is continuously improving process for defending IT assets • The CND approach in this Chapter includes: – Lightweight process for CND – Set of open source scripts for network monitoring and Advanced Log Analysis (ALA) on Backtrack – ...
... Introduction to Cyber Network Defense • Cyber Network Defense (CND) is continuously improving process for defending IT assets • The CND approach in this Chapter includes: – Lightweight process for CND – Set of open source scripts for network monitoring and Advanced Log Analysis (ALA) on Backtrack – ...
Silicon OS for Large.. - Index of
... space-time sharing will be a major step forward towards attaining exa-flop computing. Some positives of SMAPP are: ...
... space-time sharing will be a major step forward towards attaining exa-flop computing. Some positives of SMAPP are: ...
GPRS
... PDP context identifier, PDP type, PDP address, and PDP state Access point name to the external data network Subscribed, requested and negotiated QoS profiles IP address of the GGSN currently used by the activated PDP context Identifier of the charging records generated by SGSN and GGSN ...
... PDP context identifier, PDP type, PDP address, and PDP state Access point name to the external data network Subscribed, requested and negotiated QoS profiles IP address of the GGSN currently used by the activated PDP context Identifier of the charging records generated by SGSN and GGSN ...
MMN-lec20-MultimediaApplications
... network, increasing staff access to news and company information. The same infrastructure can be used no matter how many channels or viewing devices are attached to the network. No special wiring or video distribution design is required. ...
... network, increasing staff access to news and company information. The same infrastructure can be used no matter how many channels or viewing devices are attached to the network. No special wiring or video distribution design is required. ...
HSARPA Cyber Security R&D
... We still lack large-scale deployment of security technology sufficient to protect our vital infrastructures ...
... We still lack large-scale deployment of security technology sufficient to protect our vital infrastructures ...
Biological Laboratory Safety
... comprehensive and professional health, safety and environmental services to the University community. Protect Rutgers employees, students and visitors. REHS ensures compliance with government regulations ...
... comprehensive and professional health, safety and environmental services to the University community. Protect Rutgers employees, students and visitors. REHS ensures compliance with government regulations ...
Immersive Media Delivery and Access Grid
... Kyushu Nat`l Univ, AIST KISTI, K-JIST, Chonnam U, HYU Description (to be revised) The Access Grid, as a communication channel for users from remote sites, can give researchers and scientists in both Korea and Japan a seamless and immersive collaboration environment. With this project, we want to e ...
... Kyushu Nat`l Univ, AIST KISTI, K-JIST, Chonnam U, HYU Description (to be revised) The Access Grid, as a communication channel for users from remote sites, can give researchers and scientists in both Korea and Japan a seamless and immersive collaboration environment. With this project, we want to e ...
ICS 156: Advanced Computer Networks
... After each lab session, you prepare a lab report that summarizes and analyzes the findings from the lab session. A notepad symbol indicates an assignment for the lab report. The lab reports should be submitted as a typewritten document. ...
... After each lab session, you prepare a lab report that summarizes and analyzes the findings from the lab session. A notepad symbol indicates an assignment for the lab report. The lab reports should be submitted as a typewritten document. ...
CyberShield Command Core
... • CyberShield Command Core is a modular system consisting of four functional units with a common infrastructure to enable the provision of end-to-end protection of critical networks within a rapidly changing cyber domain. The modular system can be tailored to the customer’s cyber defense doctrine a ...
... • CyberShield Command Core is a modular system consisting of four functional units with a common infrastructure to enable the provision of end-to-end protection of critical networks within a rapidly changing cyber domain. The modular system can be tailored to the customer’s cyber defense doctrine a ...
Certified Penetration Testing Specialist
... information on the latest vulnerabilities and defenses. This class also enhances the business skills needed to identify protection opportunities, justify testing activities and optimize security controls appropriate to the business needs in order to reduce business risk. We go far beyond simply teac ...
... information on the latest vulnerabilities and defenses. This class also enhances the business skills needed to identify protection opportunities, justify testing activities and optimize security controls appropriate to the business needs in order to reduce business risk. We go far beyond simply teac ...
Wireless
... the data, the beginnings of these frames would be the same, offering a pattern that can aid hackers in cracking the encryption algorithm. Since the IV is different for most frames, WEP guards against this type of attack. The frequent changing of IVs also improves the ability of WEP to safeguard agai ...
... the data, the beginnings of these frames would be the same, offering a pattern that can aid hackers in cracking the encryption algorithm. Since the IV is different for most frames, WEP guards against this type of attack. The frequent changing of IVs also improves the ability of WEP to safeguard agai ...
S-72.423 Telecommunication Systems
... IN (Intelligent Network) solutions developed first for PSTN but a typical important part of most networks as in PLMNs ...
... IN (Intelligent Network) solutions developed first for PSTN but a typical important part of most networks as in PLMNs ...
S-72.423 Telecommunication Systems
... The PSTN is optimized for fixed speech service, statistically distributed, analog subscribers (by using the circuit switching technology that was made available beginning of this century). Support for data traffic "artificially added" by modems ISDN (integrated into exchanges) xDSL (x digital ...
... The PSTN is optimized for fixed speech service, statistically distributed, analog subscribers (by using the circuit switching technology that was made available beginning of this century). Support for data traffic "artificially added" by modems ISDN (integrated into exchanges) xDSL (x digital ...
S-72.423 Telecommunication Systems
... Most people have observed that a telecommunications network is a system transmitting the messages (even SMS) … In this course we focus on analyzing that it consists of ... ...
... Most people have observed that a telecommunications network is a system transmitting the messages (even SMS) … In this course we focus on analyzing that it consists of ... ...
망관리 기술 발전 방향
... information services to customers and operate them in a way that meets quality and cost objectives • Service creation • Order handling • Customer administration • Marketing • Problem handling • Billing, and so on The key goals are to improve customer service, reduce cost, and shorten time to marke ...
... information services to customers and operate them in a way that meets quality and cost objectives • Service creation • Order handling • Customer administration • Marketing • Problem handling • Billing, and so on The key goals are to improve customer service, reduce cost, and shorten time to marke ...
Teaching Computer Security using Minix
... Existing labs have been updated New labs were added every year Students’ positive feedbacks. Industry recruiters are interested. ...
... Existing labs have been updated New labs were added every year Students’ positive feedbacks. Industry recruiters are interested. ...
Introduction - Tsinghua Future Internet communication Lab
... trade off in the asymptotic regime of dense networks. This tradeoff shows the superiority of the D2D caching network approach and of the coded multicasting approach over the conventional schemes, which can be regarded as today current technology. In order to gain a better understanding of the actual ...
... trade off in the asymptotic regime of dense networks. This tradeoff shows the superiority of the D2D caching network approach and of the coded multicasting approach over the conventional schemes, which can be regarded as today current technology. In order to gain a better understanding of the actual ...