Introduction. The telecommunications service market
... However, an important backbone for other networks! The PSTN will be there for a long time and it seems that it can be used for modern day networking also on quite high data rates by using various extension techniques Modern day networks are constructed thus that the required services can be suppor ...
... However, an important backbone for other networks! The PSTN will be there for a long time and it seems that it can be used for modern day networking also on quite high data rates by using various extension techniques Modern day networks are constructed thus that the required services can be suppor ...
BIO-ELECTRO-INFO TECHNOLOGIES TO COMBAT TERRORISM
... The Internet is the high ground and a first termer in NDA will know that the first lesson that one learns is to occupy high ground and hold it under all costs. ...
... The Internet is the high ground and a first termer in NDA will know that the first lesson that one learns is to occupy high ground and hold it under all costs. ...
投影片 1
... against threats from the other network (the one that is said to be "outside" the firewall). ...
... against threats from the other network (the one that is said to be "outside" the firewall). ...
8_19Counter Hack 6 scanning
... Run the tools against your networks Be careful with DoS(Denial-to-Server) and Password Guessing tests! Be aware of limitations of vulnerability scanning tools. ...
... Run the tools against your networks Be careful with DoS(Denial-to-Server) and Password Guessing tests! Be aware of limitations of vulnerability scanning tools. ...
INTAKE IN-FLIGHT and/or COMMITTED
... Infection Control Application - Needs further clarification (FY15 1.2m) Pyxis MedStation Enterprise Systems Version (ES) Mission Bay APeX Build Out (FY14-15) ...
... Infection Control Application - Needs further clarification (FY15 1.2m) Pyxis MedStation Enterprise Systems Version (ES) Mission Bay APeX Build Out (FY14-15) ...
Online Service Management Algorithm for Cellular/WLAN
... Sungwook Kim Sogang University Department of Computer Science Seoul, South Korea ...
... Sungwook Kim Sogang University Department of Computer Science Seoul, South Korea ...
Power Point - ECE Users Pages - Georgia Institute of Technology
... Vulnerabilities come from: • Default configuration weakness • Configuration errors ...
... Vulnerabilities come from: • Default configuration weakness • Configuration errors ...
Report
... to callee's location, and manage the conversation, the actual voice or video content are carried by other session protocols, typically RTP. Brekeke SIP Server is a commercial software, so we only have its academic version, which turns out to be rather unstable. We have installed a SIP server on Wind ...
... to callee's location, and manage the conversation, the actual voice or video content are carried by other session protocols, typically RTP. Brekeke SIP Server is a commercial software, so we only have its academic version, which turns out to be rather unstable. We have installed a SIP server on Wind ...
File
... Firewalls can be organized into two different categories. One which is a defaultdeny policy, where the firewall system lists down allowed system services, and everything else is rejected. The second category is a default- allow policy, which were the firewall system lists system services that are no ...
... Firewalls can be organized into two different categories. One which is a defaultdeny policy, where the firewall system lists down allowed system services, and everything else is rejected. The second category is a default- allow policy, which were the firewall system lists system services that are no ...
Lecture 1 Installing Linux, VMware, Reconnaissance, Network
... Vulnerabilities come from: • Default configuration weakness • Configuration errors ...
... Vulnerabilities come from: • Default configuration weakness • Configuration errors ...
Traffic Engineering over MPLS
... window flow control, queue management, scheduling, etc) ; (iii) Both ...
... window flow control, queue management, scheduling, etc) ; (iii) Both ...
LAB02-Network_Connectivity
... Posts active connections on TCP, but the number of the port and the addresses are in numerical format and no attempt is made to determine the names. ...
... Posts active connections on TCP, but the number of the port and the addresses are in numerical format and no attempt is made to determine the names. ...
ppt
... When the link is constructed, the link capacity (number of streams that can be delivered) is negotiated and decided The participating users enhance the delivery routing tree The routing tree of the source user is constructed with the shortest ...
... When the link is constructed, the link capacity (number of streams that can be delivered) is negotiated and decided The participating users enhance the delivery routing tree The routing tree of the source user is constructed with the shortest ...
Validation Plan for Cobas Integra 400 for ALT
... Effective (or Post) Date: Date of last review: Reviewed by: ...
... Effective (or Post) Date: Date of last review: Reviewed by: ...
Page PDF - Utah Valley University
... * Prerequisite(s): IT 2700 and University Advanced Standing * Prerequisite(s) or Corequisite(s): INFO 3430 Provides perspective of key issues involved in IT activities across the organizational and technical security landscape. Examines management methodologies, staffing, and operational issues. Tea ...
... * Prerequisite(s): IT 2700 and University Advanced Standing * Prerequisite(s) or Corequisite(s): INFO 3430 Provides perspective of key issues involved in IT activities across the organizational and technical security landscape. Examines management methodologies, staffing, and operational issues. Tea ...
01_423intro
... Transportation system differentiated into constant rate, real-time and higher-latency services by Multi-Protocol Label Switching (MPLS) or Differentiated Services (DiffServ) User services can be divided to different groups, depending on QoS requirements. Four traffic classes can been identified: C ...
... Transportation system differentiated into constant rate, real-time and higher-latency services by Multi-Protocol Label Switching (MPLS) or Differentiated Services (DiffServ) User services can be divided to different groups, depending on QoS requirements. Four traffic classes can been identified: C ...
Lab1Overview - ECE Users Pages
... • Security holes in applications and protocols • Failure to implement patches! ECE 4112 - Internetwork Security ...
... • Security holes in applications and protocols • Failure to implement patches! ECE 4112 - Internetwork Security ...
Artificial Intelligence for Cyber Security (AICS)
... systems by the cyber security community. One promising approach to mitigate this problem is to build models of human behavior and enable formal reasoning about how human beings interact with cyber systems. Game theory, in particular, has been used to model human behavior and leveraging game-theoreti ...
... systems by the cyber security community. One promising approach to mitigate this problem is to build models of human behavior and enable formal reasoning about how human beings interact with cyber systems. Game theory, in particular, has been used to model human behavior and leveraging game-theoreti ...
Next Generation Security Operation Center for NCHC
... – Simulating vulnerable systems for network threats – Collecting malware samples and suspicious exploit traffic for further research – Analyzing Malware behavior for potential threats ...
... – Simulating vulnerable systems for network threats – Collecting malware samples and suspicious exploit traffic for further research – Analyzing Malware behavior for potential threats ...
Future of Cyber Security and the Issue of Cyber warfare: A
... political, military, or infrastructural assets of a nation, or its people. Cyber security is therefore a critical part of any governments’ security strategy. Cyber warfare involves nation-states using information technology to penetrate another nation’s networks to cause damage or disruption. In 201 ...
... political, military, or infrastructural assets of a nation, or its people. Cyber security is therefore a critical part of any governments’ security strategy. Cyber warfare involves nation-states using information technology to penetrate another nation’s networks to cause damage or disruption. In 201 ...
Paper - Asee peer logo
... other hosts in the Internet. Students use nslookup to determine the sequence of name servers to contact to resolve a specific domain name of a host in the Internet. COMNET III is presently running on a Windows platform. The department purchased a multi-site license for approximately $3000. COMNET II ...
... other hosts in the Internet. Students use nslookup to determine the sequence of name servers to contact to resolve a specific domain name of a host in the Internet. COMNET III is presently running on a Windows platform. The department purchased a multi-site license for approximately $3000. COMNET II ...
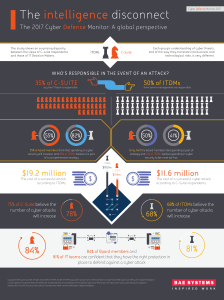
The intelligence disconnect
... The 2017 Cyber Defence Monitor: A global perspective The study shows an surprising disparity between the views of C-suite respondents and those of IT Decision Makers. ...
... The 2017 Cyber Defence Monitor: A global perspective The study shows an surprising disparity between the views of C-suite respondents and those of IT Decision Makers. ...
VoIP - Chetan Vaity
... As the popularity of VoIP grows, and PSTN users switch to VoIP in increasing numbers, governments are becoming more interested in regulating VoIP in a manner similar to legacy PSTN services In some countries, governments fearful for their state owned telephone services, have imposed restrictions ...
... As the popularity of VoIP grows, and PSTN users switch to VoIP in increasing numbers, governments are becoming more interested in regulating VoIP in a manner similar to legacy PSTN services In some countries, governments fearful for their state owned telephone services, have imposed restrictions ...
john p. carlin - AFCEA International
... and cyber and other national security threats. Prior to assuming his role in the NSD, Mr. Carlin served as Chief of Staff and Senior Counsel to Robert S. Mueller, III, former director of the FBI, where he helped lead the FBI’s evolution to meet growing and changing national security threats, includi ...
... and cyber and other national security threats. Prior to assuming his role in the NSD, Mr. Carlin served as Chief of Staff and Senior Counsel to Robert S. Mueller, III, former director of the FBI, where he helped lead the FBI’s evolution to meet growing and changing national security threats, includi ...