Solution to hw4
... 2. (20 pts) (Problem 10 from sec 2.5 ) Let f (y) = y(1 − y 2 ). So f (y) = 0 if y = 0 or y = ±1. We have f (−2) = (−2)(1−(−2)2 ) > 0,f (−0.5) = (−0.5)(1− (−0.5)2 ) < 0, f (0.5) = (0.5)(1 − (0.5)2 ) > 0 and f (2) = (2)(1 − (2)2 ) < 0 The equilibrium points are y = 0 , y = 1 and y = −1. We also have f ...
... 2. (20 pts) (Problem 10 from sec 2.5 ) Let f (y) = y(1 − y 2 ). So f (y) = 0 if y = 0 or y = ±1. We have f (−2) = (−2)(1−(−2)2 ) > 0,f (−0.5) = (−0.5)(1− (−0.5)2 ) < 0, f (0.5) = (0.5)(1 − (0.5)2 ) > 0 and f (2) = (2)(1 − (2)2 ) < 0 The equilibrium points are y = 0 , y = 1 and y = −1. We also have f ...
slides
... Randomized Quicksort Always output correct answer Takes O(N log N) time on average Likelihood of running O(N log N) time? ...
... Randomized Quicksort Always output correct answer Takes O(N log N) time on average Likelihood of running O(N log N) time? ...
Determining Optimal Parameters in Magnetic
... initial conditions. Such worst initial conditions are not defined in general, but they in turn depend on the adopted design parameters. Therefore, we formulate a min-max problem, whose solutions are robust optimal values for the design parameters. This problem is quite difficult, since the solution ...
... initial conditions. Such worst initial conditions are not defined in general, but they in turn depend on the adopted design parameters. Therefore, we formulate a min-max problem, whose solutions are robust optimal values for the design parameters. This problem is quite difficult, since the solution ...
Problem Sheet 3
... might not a closure operator (in particular c(c(A)) 6= c(A) in general). (d) Suppose now that → is a relation between filters on X and points of X satisfying all the conditions of the part above. Show that τ = {U ⊆ X : ∀x ∈ U ∀ filter F → x U ∈ F} is a topology on X. Show that if → is the convergenc ...
... might not a closure operator (in particular c(c(A)) 6= c(A) in general). (d) Suppose now that → is a relation between filters on X and points of X satisfying all the conditions of the part above. Show that τ = {U ⊆ X : ∀x ∈ U ∀ filter F → x U ∈ F} is a topology on X. Show that if → is the convergenc ...
pdf
... Nonetheless if we consider stronger consistency, such as domain consistency, the improvement is twofold: it provides better accuracy since the variable biases rely only on supports that are domain consistent (rather than arc consistent for EMBP-a) and it is easily implementable for any constraint fo ...
... Nonetheless if we consider stronger consistency, such as domain consistency, the improvement is twofold: it provides better accuracy since the variable biases rely only on supports that are domain consistent (rather than arc consistent for EMBP-a) and it is easily implementable for any constraint fo ...
ppt - Ricam
... A full row rank matrix is zero prime if all its maximal order minors generate the unit ideal. Lin-Bose propose the following problem: Given F, full row rank of size lxm, if all the reduced minors generate the unit ideal, then whether or not F can be factorized as F=GxF1, with det(G)=d, d the gcd, an ...
... A full row rank matrix is zero prime if all its maximal order minors generate the unit ideal. Lin-Bose propose the following problem: Given F, full row rank of size lxm, if all the reduced minors generate the unit ideal, then whether or not F can be factorized as F=GxF1, with det(G)=d, d the gcd, an ...
S225-50-31 Voltage Regulators Polymer Position Indicator Main Cover Replacement Kit Number 5742305B01
... competent technicians, who are familiar with this equipment should install, operate and service it. A competent technician has these qualifications: ■ Is thoroughly familiar with these instructions. ■ Is trained in industry-accepted high- and low-voltage safe operating practices and procedures. ■ Is ...
... competent technicians, who are familiar with this equipment should install, operate and service it. A competent technician has these qualifications: ■ Is thoroughly familiar with these instructions. ■ Is trained in industry-accepted high- and low-voltage safe operating practices and procedures. ■ Is ...
Contents - MAC
... cos2 (x) + 2 cos(x) − 1 = 0 Find the solutions that are in the interval [0, 2π). sin(2t) + sin(t) = 0 ...
... cos2 (x) + 2 cos(x) − 1 = 0 Find the solutions that are in the interval [0, 2π). sin(2t) + sin(t) = 0 ...
Characterization and separation of the Chvatal
... dominant relation in the elementary closure for the knapsack problem. Then, we explicitly describe necessary conditions for an inequality to be a nondominated rank 1 Chvatal-Gomory inequality for the knapsack problem, which we call maximal inequality. Independently, we show that the separation probl ...
... dominant relation in the elementary closure for the knapsack problem. Then, we explicitly describe necessary conditions for an inequality to be a nondominated rank 1 Chvatal-Gomory inequality for the knapsack problem, which we call maximal inequality. Independently, we show that the separation probl ...
Summary of big ideas
... which has larger LP value.) Choose a variable xi which has a noninteger value xi* in the LP solution of the subproblem. Create two new subproblems by adding the respective constraints xi xi* and xi ≥ xi* . 2) Bounding: Solve the new subproblems, record their LP solutions. Based on the LP val ...
... which has larger LP value.) Choose a variable xi which has a noninteger value xi* in the LP solution of the subproblem. Create two new subproblems by adding the respective constraints xi xi* and xi ≥ xi* . 2) Bounding: Solve the new subproblems, record their LP solutions. Based on the LP val ...
The general problem of moist processes in ALADIN-2 J.-F
... To start looking at the problem of the micro-physics time-step-length (algorithmically, not scientifically). To prepare testing of deep-convective ideas in a very wide sense (if one wants compatibility between ALARO-10 and ALARO-5 in methods and between AROME and ALARO-5 for micro-physics, cross-fer ...
... To start looking at the problem of the micro-physics time-step-length (algorithmically, not scientifically). To prepare testing of deep-convective ideas in a very wide sense (if one wants compatibility between ALARO-10 and ALARO-5 in methods and between AROME and ALARO-5 for micro-physics, cross-fer ...
Shortest Path
... Dijkstra’s algorithm finds the length of a shortest path between two vertices in a connected simple undirected weighted graph G=(V,E). The time required by Dijkstra's algorithm is O(|V|2). It will be reduced to O(|E|log|V|) if heap is used to keep {vV\Si : L(v) < }, where Si is the set S after ite ...
... Dijkstra’s algorithm finds the length of a shortest path between two vertices in a connected simple undirected weighted graph G=(V,E). The time required by Dijkstra's algorithm is O(|V|2). It will be reduced to O(|E|log|V|) if heap is used to keep {vV\Si : L(v) < }, where Si is the set S after ite ...
Chem 109 C Fall 2014 Armen Zakarian Office: Chemistry Bldn 2217
... Practice problem 4 A mixture of amino acids that do not separate sufficiently when a single technique is used can often be separated by two-dimensional chromatography. In this technique, the mixture of amino acids is applied to a piece of filter paper and separated by liquid chromatography, then th ...
... Practice problem 4 A mixture of amino acids that do not separate sufficiently when a single technique is used can often be separated by two-dimensional chromatography. In this technique, the mixture of amino acids is applied to a piece of filter paper and separated by liquid chromatography, then th ...
ConArg: Argumentation with Constraints
... use techniques to tackle this inherent complexity, as CP-based ones. Moreover, ConArg can solve different classical hard-problems that concern weighted AFs (where attacks are associated with a “strength” value), as the ones related to weighted grounded extensions presented in [5]. For example, given ...
... use techniques to tackle this inherent complexity, as CP-based ones. Moreover, ConArg can solve different classical hard-problems that concern weighted AFs (where attacks are associated with a “strength” value), as the ones related to weighted grounded extensions presented in [5]. For example, given ...
Say-Ask-Check for Word Problems for the KIDS
... read the problem. I 1. Read the will reread the problem if I don’t problem understand it.” Ask: “Now that I have read the problem, do I fully understand it?” Check: “I understand the problem and will move forward.” 2. Paraphrase Say: “I will restate the problem in my own words.” the problem Ask: “Ca ...
... read the problem. I 1. Read the will reread the problem if I don’t problem understand it.” Ask: “Now that I have read the problem, do I fully understand it?” Check: “I understand the problem and will move forward.” 2. Paraphrase Say: “I will restate the problem in my own words.” the problem Ask: “Ca ...
Chapter 8: Dynamic Programming
... Rule 1 If an element in row i and column j is 1 in R(k-1), it remains 1 in R(k) Rule 2 If an element in row i and column j is 0 in R(k-1), it has to be changed to 1 in R(k) if and only if the element in its row i and column k and the element in its column j and row k are both 1’s in R(k-1) ...
... Rule 1 If an element in row i and column j is 1 in R(k-1), it remains 1 in R(k) Rule 2 If an element in row i and column j is 0 in R(k-1), it has to be changed to 1 in R(k) if and only if the element in its row i and column k and the element in its column j and row k are both 1’s in R(k-1) ...
Chapter 8: Dynamic Programming
... Rule 1 If an element in row i and column j is 1 in R(k-1), it remains 1 in R(k) Rule 2 If an element in row i and column j is 0 in R(k-1), it has to be changed to 1 in R(k) if and only if the element in its row i and column k and the element in its column j and row k are both 1’s in R(k-1) ...
... Rule 1 If an element in row i and column j is 1 in R(k-1), it remains 1 in R(k) Rule 2 If an element in row i and column j is 0 in R(k-1), it has to be changed to 1 in R(k) if and only if the element in its row i and column k and the element in its column j and row k are both 1’s in R(k-1) ...
Breakfast Bytes
... if number is even then set number to number/2 if number is odd then set number to 3number + 1 ...
... if number is even then set number to number/2 if number is odd then set number to 3number + 1 ...
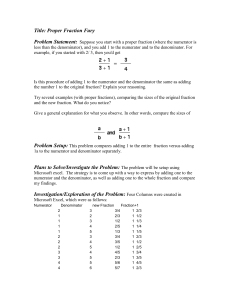
Proper Fraction Fury
... I proceeded to plug in various numerators that were smaller than the denominator. I continued to do this until I could develop a pattern. In working the problem, I discovered that adding one to a problem causes the problem to increase in value by 1 whole number. In adding 1 to the numerator and deno ...
... I proceeded to plug in various numerators that were smaller than the denominator. I continued to do this until I could develop a pattern. In working the problem, I discovered that adding one to a problem causes the problem to increase in value by 1 whole number. In adding 1 to the numerator and deno ...
ASB Presentation - The University of Sheffield
... The mating partner for Pi (where i is the index of the current individual in a population) is selected using of the following rules i.e. rule 1: select a parent from the neighbourhood with a probability of τ and rule 2: select a random parent from the population with a probability of (1−τ ). Method ...
... The mating partner for Pi (where i is the index of the current individual in a population) is selected using of the following rules i.e. rule 1: select a parent from the neighbourhood with a probability of τ and rule 2: select a random parent from the population with a probability of (1−τ ). Method ...
When flow shop scheduling meets dominoes
... There is a set of n jobs available at time zero ; each job j must be processed non-preemptively on two continuously available machines M1 , M2 with known integer processing times aj , bj , respectively. The order of processing is M1 → M2 for all jobs. Each machine can process at most one job at a ti ...
... There is a set of n jobs available at time zero ; each job j must be processed non-preemptively on two continuously available machines M1 , M2 with known integer processing times aj , bj , respectively. The order of processing is M1 → M2 for all jobs. Each machine can process at most one job at a ti ...
This PDF is a selection from an out-of-print volume from... Bureau of Economic Research
... extensions of similar analyses in closed-economy models. In this discussion, I emphasize two important caveats of open-economy optimal policy problems. First, the intertemporal budget constraint of the government is not a necessary restriction that a Ramsey government should consider in its maximiza ...
... extensions of similar analyses in closed-economy models. In this discussion, I emphasize two important caveats of open-economy optimal policy problems. First, the intertemporal budget constraint of the government is not a necessary restriction that a Ramsey government should consider in its maximiza ...