B1-802-11-Presentation
... transparency concerning applications and higher layer protocols location awareness if necessary ...
... transparency concerning applications and higher layer protocols location awareness if necessary ...
5G radio network architecture
... Nowadays base stations consume a constant power, regardless of the traffic load. During offpeak traffic hours, small cells are switched off while coverage is maintained by macrocells. For active base stations serving a single user, following Shannon’s theorem, the most energyefficient situation w ...
... Nowadays base stations consume a constant power, regardless of the traffic load. During offpeak traffic hours, small cells are switched off while coverage is maintained by macrocells. For active base stations serving a single user, following Shannon’s theorem, the most energyefficient situation w ...
Lecture 01
... UDP: DNS, RTP (voice & multimedia) TCP & UDP incorporated into computer operating systems Any application designed to operate over TCP or UDP will run over the Internet ...
... UDP: DNS, RTP (voice & multimedia) TCP & UDP incorporated into computer operating systems Any application designed to operate over TCP or UDP will run over the Internet ...
C01-Overview
... Wireless networks in comparison to fixed networks Higher loss-rates due to interference ...
... Wireless networks in comparison to fixed networks Higher loss-rates due to interference ...
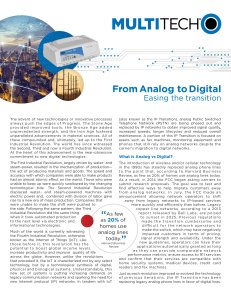
From Analog to Digital - Multi
... Although implementing any type of new service or process co mpan ies in dat a t ra nsm i ssi on. Ana l og l i n e s , a l s o comes with a price tag, the price of passivity is much steeper referred to as “Plain Old Telephone Service” (POTS), than moving forward with new technology. For instance, tra ...
... Although implementing any type of new service or process co mpan ies in dat a t ra nsm i ssi on. Ana l og l i n e s , a l s o comes with a price tag, the price of passivity is much steeper referred to as “Plain Old Telephone Service” (POTS), than moving forward with new technology. For instance, tra ...
Pascal Thubert Thomas Watteyne
... • Choice 2, the ID is allocated to IETF via IANA. There is a defined process to obtain a Payload Group ID (http://www.ieee802.org/15/ANA.html), it basically starts with a formal request from an IANA officer. The issue I have with this choice is that we have only 8 addresses left before going onto ex ...
... • Choice 2, the ID is allocated to IETF via IANA. There is a defined process to obtain a Payload Group ID (http://www.ieee802.org/15/ANA.html), it basically starts with a formal request from an IANA officer. The issue I have with this choice is that we have only 8 addresses left before going onto ex ...
Speaker 7.2
... • CSC_RAU (Conversion Separation Combination –RAU). Performs the signal conversions between the optical and electrical. • CSC_CU (Conversion Separation Combination –CU). • JPU (Joint Processing Unit). Unit where the joint processing of the RF signals for a set of RAU’s is performed. ...
... • CSC_RAU (Conversion Separation Combination –RAU). Performs the signal conversions between the optical and electrical. • CSC_CU (Conversion Separation Combination –CU). • JPU (Joint Processing Unit). Unit where the joint processing of the RF signals for a set of RAU’s is performed. ...
SYSTRA Course
... – Instant access, no further log-on – Flat rate (about $30/mo in the LA area) – User perceived performance: fluctuates (as GPRS users defer to voice users) to a max of 50Kbps ...
... – Instant access, no further log-on – Flat rate (about $30/mo in the LA area) – User perceived performance: fluctuates (as GPRS users defer to voice users) to a max of 50Kbps ...
title of projects - 123SeminarsOnly.com
... Transmitting Section consists of just mobile which has inbuilt GSM modem for wireless data transfer through GSM. GSM (Global System for Mobile communications: originally from Group Special Mobile) is the most popular standard for mobile phones in the world. ...
... Transmitting Section consists of just mobile which has inbuilt GSM modem for wireless data transfer through GSM. GSM (Global System for Mobile communications: originally from Group Special Mobile) is the most popular standard for mobile phones in the world. ...
ReviewSheet Midterm2 Last modified January 7
... 10. In an ad hoc network, the stations can form a network without the need of access points. 11. In wireless LAN, a collision will always be heard by all stations in the network. 12. An autonomous system is a group of networks and routers under the authority of more than one administration bodies. 1 ...
... 10. In an ad hoc network, the stations can form a network without the need of access points. 11. In wireless LAN, a collision will always be heard by all stations in the network. 12. An autonomous system is a group of networks and routers under the authority of more than one administration bodies. 1 ...
C03-Wireless_LANs
... security (no one should be able to read my data), privacy (no one should be able to collect user profiles), safety (low radiation) transparency concerning applications and higher layer protocols, but also location awareness if necessary ...
... security (no one should be able to read my data), privacy (no one should be able to collect user profiles), safety (low radiation) transparency concerning applications and higher layer protocols, but also location awareness if necessary ...
Wireless Mesh Network (WMN)
... • BAC net (Building automation & control) – Elec. Devices power – Light – Elevators – A/C ...
... • BAC net (Building automation & control) – Elec. Devices power – Light – Elevators – A/C ...
MAC Protocols
... Random Access Protocols When node has packet to send transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes -> “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delay ...
... Random Access Protocols When node has packet to send transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes -> “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delay ...
MAC Protocols
... Random Access Protocols When node has packet to send transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes -> “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delay ...
... Random Access Protocols When node has packet to send transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes -> “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delay ...
Usually, the alarm panel in the market will use telephone line
... Auto self check and restart function: It can continuously monitor the system status of its own. When there is a problem with the SIM card or the module is not working properly, it will automatically restart the system. Automatically call to 8 pre-program phone numbers while alarming. The WT-1010C2 a ...
... Auto self check and restart function: It can continuously monitor the system status of its own. When there is a problem with the SIM card or the module is not working properly, it will automatically restart the system. Automatically call to 8 pre-program phone numbers while alarming. The WT-1010C2 a ...
LEDS:Providing Location –Aware End-to-End Data
... • Once a node in a certain area is compromised, the attacker can disrupt any event report from that area from being forwarded to the sink thereafter by simply contributing a wrong MAC to the final report. • Since the en-route filtering allows intermediate nodes to drop packets with false MACs, such ...
... • Once a node in a certain area is compromised, the attacker can disrupt any event report from that area from being forwarded to the sink thereafter by simply contributing a wrong MAC to the final report. • Since the en-route filtering allows intermediate nodes to drop packets with false MACs, such ...
$doc.title
... • But, performance definitely is affected – TCP treats packet loss as a sign of conges5on – TCP tries to es5mate the RTT to drive retransmissions – TCP does not perform well under out‐of‐order packets ...
... • But, performance definitely is affected – TCP treats packet loss as a sign of conges5on – TCP tries to es5mate the RTT to drive retransmissions – TCP does not perform well under out‐of‐order packets ...
Wireless Communications Research Overview
... Energy (transmit and processing) is the driving constraint Data flows to centralized location (joint compression) Low per-node rates but tens to thousands of nodes Intelligence is in the network rather than in the devices ...
... Energy (transmit and processing) is the driving constraint Data flows to centralized location (joint compression) Low per-node rates but tens to thousands of nodes Intelligence is in the network rather than in the devices ...
Lecture note 13
... • The component used to interconnect BSSs is called “distribution system (DS).” • The medium used for the DS can be different from the wireless medium. (Normally most vendors just use Ethernet as the DS.) • The DS can be considered as a layer-2 network. • An access point (AP) is a station that provi ...
... • The component used to interconnect BSSs is called “distribution system (DS).” • The medium used for the DS can be different from the wireless medium. (Normally most vendors just use Ethernet as the DS.) • The DS can be considered as a layer-2 network. • An access point (AP) is a station that provi ...
Networking Security - Northwestern Networks Group
... interference from other sources: standardized wireless network frequencies (e.g., 2.4 GHz) shared by other devices (e.g., phone); multipath propagation: radio signal reflects off objects ground, arriving ad destination at ...
... interference from other sources: standardized wireless network frequencies (e.g., 2.4 GHz) shared by other devices (e.g., phone); multipath propagation: radio signal reflects off objects ground, arriving ad destination at ...
Quiz-3 Review - Communications Systems Center
... Z sends datagrams for X to Y Z advertises "X in 5 hops". Y-X link cost goes to 60 Y thinks Z can route in 5 hops, so Y advertises "X in 6", sends datagrams back to Z. Z sends datagrams back to Y, advertises "X in 7". Y sends datagrams back to Z, advertises "X in 8". ...
... Z sends datagrams for X to Y Z advertises "X in 5 hops". Y-X link cost goes to 60 Y thinks Z can route in 5 hops, so Y advertises "X in 6", sends datagrams back to Z. Z sends datagrams back to Y, advertises "X in 7". Y sends datagrams back to Z, advertises "X in 8". ...
Part I: Introduction - Northwestern University
... interference from other sources: standardized wireless network frequencies (e.g., 2.4 GHz) shared by other devices (e.g., phone); multipath propagation: radio signal reflects off objects ground, arriving ad destination at ...
... interference from other sources: standardized wireless network frequencies (e.g., 2.4 GHz) shared by other devices (e.g., phone); multipath propagation: radio signal reflects off objects ground, arriving ad destination at ...
Cellular network

A cellular network or mobile network is a communications network where the last link is wireless. The network is distributed over land areas called cells, each served by at least one fixed-location transceiver, known as a cell site or base station. In a cellular network, each cell uses a different set of frequencies from neighboring cells, to avoid interference and provide guaranteed bandwidth within each cell.When joined together these cells provide radio coverage over a wide geographic area. This enables a large number of portable transceivers (e.g., mobile phones, pagers, etc.) to communicate with each other and with fixed transceivers and telephones anywhere in the network, via base stations, even if some of the transceivers are moving through more than one cell during transmission.Cellular networks offer a number of desirable features: More capacity than a single large transmitter, since the same frequency can be used for multiple links as long as they are in different cells Mobile devices use less power than with a single transmitter or satellite since the cell towers are closer Larger coverage area than a single terrestrial transmitter, since additional cell towers can be added indefinitely and are not limited by the horizonMajor telecommunications providers have deployed voice and data cellular networks over most of the inhabited land area of the Earth. This allows mobile phones and mobile computing devices to be connected to the public switched telephone network and public Internet. Private cellular networks can be used for research or for large organizations and fleets, such as dispatch for local public safety agencies or a taxicab company.