History of Unix OS
... improved and distributed often Many users can spot bugs in the operating system or application if source code is “open” ...
... improved and distributed often Many users can spot bugs in the operating system or application if source code is “open” ...
7 Operating Systems
... Batch systems Batch operating systems were designed in the 1950s to control mainframe computers. At that time, computers were large machines that used punched cards for input, line printers for output and tape drives for secondary storage media. Each program to be executed was called a job. A progra ...
... Batch systems Batch operating systems were designed in the 1950s to control mainframe computers. At that time, computers were large machines that used punched cards for input, line printers for output and tape drives for secondary storage media. Each program to be executed was called a job. A progra ...
History of Unix OS - Seneca
... improved and distributed often Many users can spot bugs in the operating system or application if source code is “open” ...
... improved and distributed often Many users can spot bugs in the operating system or application if source code is “open” ...
Introduction
... Swapping of a process – Process table entry System calls to create and terminate processes System calls to allocate/deallocate memory System calls for communication - signals ...
... Swapping of a process – Process table entry System calls to create and terminate processes System calls to allocate/deallocate memory System calls for communication - signals ...
Operating Systems Operating Systems Operating Systems
... All instructions that access shared resources are made to be privileged instructions. Privileged instructions may only be executed when the processor is in kernel mode. Any attempt to execute a privileged instruction in user mode results in an interrupt. The ISR in the OS will then termi ...
... All instructions that access shared resources are made to be privileged instructions. Privileged instructions may only be executed when the processor is in kernel mode. Any attempt to execute a privileged instruction in user mode results in an interrupt. The ISR in the OS will then termi ...
Lecture 3
... I/O operations - A running program may require I/O, which may involve a file or an I/O device. File-system manipulation - The file system is of particular interest. Obviously, programs need to read and write files and directories, create and delete them, search them, list file ...
... I/O operations - A running program may require I/O, which may involve a file or an I/O device. File-system manipulation - The file system is of particular interest. Obviously, programs need to read and write files and directories, create and delete them, search them, list file ...
Operating Systems: Basic Concepts and Challenges against
... virtualization in OS. We use an operating system entirely when we use “any” sort of system that has some interface or not, has user interaction or not, has a properly built UI or not. An OS interacts on our behalf with the hardware which is of utmost importance when we’re working with various device ...
... virtualization in OS. We use an operating system entirely when we use “any” sort of system that has some interface or not, has user interaction or not, has a properly built UI or not. An OS interacts on our behalf with the hardware which is of utmost importance when we’re working with various device ...
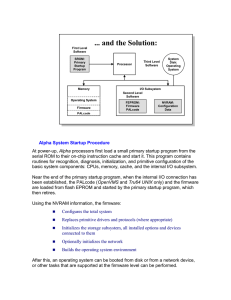
Alpha System Startup Procedure
... either automatically by the firmware or manually by the user. Additional drivers or protocols are installed at the operating system level rather than at the firmware level. Test routines and exercisers are useful tools for checking the hardware to find or exclude hardware errors in case of trouble. ...
... either automatically by the firmware or manually by the user. Additional drivers or protocols are installed at the operating system level rather than at the firmware level. Test routines and exercisers are useful tools for checking the hardware to find or exclude hardware errors in case of trouble. ...
Windows XP Boot Process
... • An x86-based computer first starts in real mode. In real mode, the processor disables certain features to allow compatibility with software designed to run on 8-bit and 16-bit processors. Ntldr then switches the processor to 32-bit mode, which allows access to large amounts of memory and enables W ...
... • An x86-based computer first starts in real mode. In real mode, the processor disables certain features to allow compatibility with software designed to run on 8-bit and 16-bit processors. Ntldr then switches the processor to 32-bit mode, which allows access to large amounts of memory and enables W ...
Chapter 3 System Software Objectives: In this chapter we will
... You're probably familiar with the most popular operating system that uses a graphical user interface, Microsoft Windows. Windows uses a graphical user interface to try and make it easier for people to use their computers and utilize their time. Currently, Windows XP and Windows Vista dominate the ma ...
... You're probably familiar with the most popular operating system that uses a graphical user interface, Microsoft Windows. Windows uses a graphical user interface to try and make it easier for people to use their computers and utilize their time. Currently, Windows XP and Windows Vista dominate the ma ...
Operating System Functions and History
... 5. Stacked job systems necessitated the development of the first protection mechanisms to protect against such problems as a program reading the program just after it as data, or going into an infinite loop and stopping other programs from being run. 6. Although stacked job systems are a thing of th ...
... 5. Stacked job systems necessitated the development of the first protection mechanisms to protect against such problems as a program reading the program just after it as data, or going into an infinite loop and stopping other programs from being run. 6. Although stacked job systems are a thing of th ...
Volume 1 2.8
... allow different family members to use their own desktops and personal sets of files There are two versions: (i) Home Edition version (ii)Professional version Volume 1 2.8 ...
... allow different family members to use their own desktops and personal sets of files There are two versions: (i) Home Edition version (ii)Professional version Volume 1 2.8 ...
How do all these components work together - Metal
... acts as the _________device. The electronic messages travel to and from the CPU across the _________ to the other parts of the computer by the _________. ...
... acts as the _________device. The electronic messages travel to and from the CPU across the _________ to the other parts of the computer by the _________. ...
Operating system - Department of Computer Science
... z Program loading and execution- Absolute loaders, relocatable loaders, linkage editors, and overlay-loaders, debugging systems for higher-level and machine language z Communications - Provide the mechanism for creating virtual connections among processes, users, and computer systems Allow users t ...
... z Program loading and execution- Absolute loaders, relocatable loaders, linkage editors, and overlay-loaders, debugging systems for higher-level and machine language z Communications - Provide the mechanism for creating virtual connections among processes, users, and computer systems Allow users t ...
Running on Borrowed Time: Why Businesses Must Finally Let Go of
... Unfortunately, Tuesday April 8th, 2014 marked the end of XP as we’ve known it. On this date, Microsoft officially halted all Windows XP support services. A Service Pack 3 (SP3) was introduced to announce that XP users will no longer receive security updates. Additionally, support options such as fre ...
... Unfortunately, Tuesday April 8th, 2014 marked the end of XP as we’ve known it. On this date, Microsoft officially halted all Windows XP support services. A Service Pack 3 (SP3) was introduced to announce that XP users will no longer receive security updates. Additionally, support options such as fre ...
Device Drivers - EMU CMPE Home Page
... Svetlana Sorokina, Andrey Tihonov, Andrey Scherbakov, Drivers Programming and Security Systems, St-Petersburg, BHV-Petersburg, Moscow, Izdatel Molgacheva S.V., 2002, 256 p., ISBN 5-94157-263-8 (in Russian) Device Drivers are special programs which are used for organization of access to external devi ...
... Svetlana Sorokina, Andrey Tihonov, Andrey Scherbakov, Drivers Programming and Security Systems, St-Petersburg, BHV-Petersburg, Moscow, Izdatel Molgacheva S.V., 2002, 256 p., ISBN 5-94157-263-8 (in Russian) Device Drivers are special programs which are used for organization of access to external devi ...
Course Form - Bluegrass Community and Technical College
... Identify, install and configure internal and peripheral computer hardware and select appropriate components to upgrade computer systems. Describe operating system functions and compare characteristics of multiple client operating systems. Diagnose and repair common hardware and software problems. Id ...
... Identify, install and configure internal and peripheral computer hardware and select appropriate components to upgrade computer systems. Describe operating system functions and compare characteristics of multiple client operating systems. Diagnose and repair common hardware and software problems. Id ...
Ch01 - Mathematics and Computer Science
... Answers will vary. The GPL stands for the GNU Public License and allows Open Source Software such as Linux to be freely available and improved for an indefinite period of time. The Open Source business model is different from conventional software; the value of software is based on its use and its u ...
... Answers will vary. The GPL stands for the GNU Public License and allows Open Source Software such as Linux to be freely available and improved for an indefinite period of time. The Open Source business model is different from conventional software; the value of software is based on its use and its u ...
Chapter 2
... • Integrates features from all other versions (SVR3, 4BSD, SunOS, XENIX) • Introduced real-time scheduling • AT&T sold its interest in UNIX to Novell in ...
... • Integrates features from all other versions (SVR3, 4BSD, SunOS, XENIX) • Introduced real-time scheduling • AT&T sold its interest in UNIX to Novell in ...
File
... This is a mechanism behind Windows 3.1 and while not in use to real time application for reasons which will become apparent it has been included for reference. ...
... This is a mechanism behind Windows 3.1 and while not in use to real time application for reasons which will become apparent it has been included for reference. ...
slides
... Memory-Mapped I/O The processor reads and writes data to address in its memory space, which are associated with the registers and control lines of I/O controllers. I/O port ...
... Memory-Mapped I/O The processor reads and writes data to address in its memory space, which are associated with the registers and control lines of I/O controllers. I/O port ...
DOS (“Disk Operating System”)
... – Explicit in Linux – “Hidden” in Windows • ‘C drive’ is NOT always the main drive (mine used to be ‘F drive’) ...
... – Explicit in Linux – “Hidden” in Windows • ‘C drive’ is NOT always the main drive (mine used to be ‘F drive’) ...
LectureNotes - Cabrillo College
... An evolutionary development compared to the earlier Windows operating system in terms of GUI and integrated components New options for customizing the GUI, including tighter integration with Microsoft’s Web browser, Internet Explorer (IE) ...
... An evolutionary development compared to the earlier Windows operating system in terms of GUI and integrated components New options for customizing the GUI, including tighter integration with Microsoft’s Web browser, Internet Explorer (IE) ...
Document
... In the mid-1980s Apple developed the Macintosh with the a successful GUI based on one developed by Rank Xerox. The Macintosh GUI with its WIMP (Windows, Icons, Mouse, Pull-down menus) technology introduced GUIs as the design paradigm of choice Microsoft then replaced MS-DOS by their Windows (GUI-bas ...
... In the mid-1980s Apple developed the Macintosh with the a successful GUI based on one developed by Rank Xerox. The Macintosh GUI with its WIMP (Windows, Icons, Mouse, Pull-down menus) technology introduced GUIs as the design paradigm of choice Microsoft then replaced MS-DOS by their Windows (GUI-bas ...